The cybersecurity market is booming, offering many options — but not all solutions are created equal.
To help you cut through the noise, we’ve curated a list of 20 top cybersecurity technology providers that stand out for their innovation, impact, and effectiveness. Our selections are backed by expert analysis, user reviews, independent security tests, and real-world performance, ensuring you have the best defense against today’s ever-changing threats.
Top Cybersecurity Companies
The following table compares our top 20 providers, including the times they’ve appeared in one of our buyer’s guides.

1. Palo Alto Networks
Best protection against network, endpoint, and remote asset attacks
Headquarters: Santa Clara, California
Founded: 2005
Annual Revenue: $7.52 billion
Employees count: 11,000-15,000
Appearances on eSecurity Planet‘s Top Vendors lists: 14
Palo Alto Networks (NASDAQ: PANW) delivers a broad portfolio of security products and a long history of top scores in rigorous independent security tests. Known for strong next-generation firewalls (NGFW) and endpoint detection and response (EDR) products, it also ranks for network security tools, zero trust, extended detection and response (XDR), IoT security, software-defined wide area network (SD-WAN), and secure access service edge (SASE).
While known primarily for its comprehensive cybersecurity solutions, Palo Alto managed a top-four finish in the first MITRE managed security tests, showing no slouch in security services either. Its security product tests have been consistently excellent, including in the latest MITRE endpoint security tests and CyberRatings firewall tests. Analysts predict that the 19-year-old firm will grow its annual revenue at 18% over the next five years.

2. Fortinet
Best for network security perimeter protection
Headquarters: Sunnyvale, California
Founded: 2000
Annual Revenue: $5.3 billion
Employee count: 13,000-14,000
Appearances on eSecurity Planet‘s Top Vendors lists: 15
Fortinet (NASDAQ: FTNT) turned its firewall expertise into leadership positions in NGFW, web application firewalls (WAF), unified threat management (UTM), and adjacent markets like software-defined wide area networks (SD-WAN) and enterprise virtual private networks (VPNs). Analysts project a 14.6% annual growth rate for the next five years.
The network security vendor doesn’t shy away from rigorous testing, and customer satisfaction ratings are high in key areas like product capabilities, value, ease of use, and support. This also helps Fortinet make inroads into small business markets.

3. Bitdefender
Best for endpoint security and ransomware protection
Headquarters: Bucharest, Romania
Founded: 2001
Annual Revenue: ~$392 million (2023)
Employees count: 1,400-1,600
Appearances on eSecurity Planet‘s Top Vendors lists: 3
Bitdefender is widely regarded as a cybersecurity leader with a global footprint, protecting over 500 million users in more than 150 countries. It offers the GravityZone platform, a unified solution for enterprise security that includes advanced endpoint protection, EDR, XDR, and cloud workload security.
Bitdefender’s consumer and business products consistently earn top rankings in independent security tests, reflecting exceptional malware detection and overall protection.

4. Cisco
Best for integrated network security
Headquarters: San Jose, California
Founded: 1984
Annual Revenue: $57.2 billion
Employees count: 80,000-94,000
Appearances on eSecurity Planet‘s Top Vendors lists: 16
Cisco (NASDAQ: CSCO) pioneered networking and developed its network security offerings through internal development and acquisition. Through strategic acquisitions such as Splunk (2023), Isovalent, Lightspin, Oort, and Working Group Two, Cisco has expanded its capabilities in network detection and response (NDR), cloud security, and zero-trust architectures.
Cisco’s existing networking customers primarily drive the adoption of its security solutions for built-in compatibility with existing infrastructure. Still, Cisco earned a spot on our top security product lists, including network detection and response and zero trust.

5. CrowdStrike
Best for endpoint security and services
Headquarters: Sunnyvale, California
Founded: 2011
Annual Revenue: $3.4 billion
Employees count: 7,900-8,400
Appearances on eSecurity Planet‘s Top Vendors lists: 8
CrowdStrike (NASDAQ: CRWD) builds off of its strength in endpoint protection to offer solutions for XDR, MDR, vulnerability management as a service (VMaaS), and cloud security posture management (CSPM).
CrowdStrike consistently earns top rankings in MITRE ATT&CK and MSSP evaluations, validating its effectiveness in real-world threat detection. Analysts predict a five-year revenue growth rate of 31.8%, making it one of the fastest-growing cybersecurity companies.

6. IBM
Best for advanced encryption
Headquarters: Armonk, New York
Founded: 1911
Annual Revenue: $61.9 billion
Employees count: 270,000-280,000
Appearances on eSecurity Planet‘s Top Vendors lists: 13
IBM’s biggest strength might be its research depth, which drives advances in areas like homomorphic encryption. Big Blue (NYSE: IBM) earns mention for unified endpoint management (UEM), SOAR, SIEM, encryption, database security, threat intelligence platform, single sign-on, and managed security service providers (MSSPs).

7. Trend Micro
Best for small businesses
Headquarters: Tokyo, Japan
Founded: 1988
Annual Revenue: $1.3 billion
Employees count: ~7,500
Appearances on eSecurity Planet‘s Top Vendors lists: 14
Trend Micro (OTC: TMICY) customers cite high value and ease of use across a portfolio of tools such as antivirus, full disk encryption, cloud workload protection platforms (CWPP), and intrusion detection and prevention systems (IDPSs). With $1.3 billion in revenue, Trend Micro continues growing steadily past its first-gen antivirus vendor status.

8. Tenable
Best for vulnerability management
Headquarters: Columbia, Maryland
Founded: 2002
Annual Revenue: $0.8 billion
Employees count: ~1,500
Appearances on eSecurity Planet‘s Top Vendors lists: 9
Tenable (NASDAQ: TENB) seeks to reduce the attack surface through a portfolio of solutions that includes vulnerability management, vulnerability scanning, patch management, cloud security, Active Directory security, pen testing, and breach and attack simulation.
Focusing on enabling critical yet difficult-to-achieve security processes earns Tenable strong positive reviews across its portfolio.

9. KnowBe4
Best for security awareness training
Headquarters: Clearwater, Florida
Founded: 2010
Annual Revenue: $0.2 billion
Employees count: 2,000-3,000
Appearances on eSecurity Planet‘s Top Vendors lists: 2
KnowBe4 (private) gained first mover advantage in cybersecurity training — a critically important practice for reducing the source of most cyberattacks. The training enjoys positive customer reviews, which drives success and motivated the $4.6 billion take-private acquisition by Vista Equity Partners in February 2023.
KnowBe4 continues to innovate in behavior-driven security training, reinforcing its position as the go-to provider for enterprises looking to strengthen their human-layer security.

10. Darktrace
Best for AI-powered security
Headquarters: Cambridge, U.K.
Founded: 2013
Annual Revenue: $0.5 billion
Employees count: 2,200-2,400
Appearances on eSecurity Planet‘s Top Vendors lists: 1
Darktrace (LSE: DARK), a U.K.-based venture, pioneers AI-based security. Their quality earns a top spot for NDR tools, but the product often challenges categorization with security and operations features for prevention, detection, incident response, and automated healing.
Darktrace’s innovative approach and technological advancements have earned it recognition as a leader in AI-driven cybersecurity solutions, trusted by organizations worldwide to safeguard their digital assets.

11. Check Point
Best for firewalls
Headquarters: Tel Aviv, Israel, and San Carlos, California
Founded: 1993
Annual Revenue: $2.4 billion
Employees count: 5,000-6,000
Appearances on eSecurity Planet‘s Top Vendors lists: 11
Check Point (NASDAQ: CHKP), the 30-year-old firewall pioneer, offers a complete security portfolio that ranks highly on independent security tests (MITRE, etc.). It offers strong security and value through traditional solutions such as firewalls, gateways, UTM, DLP, and encryption and a strong service portfolio.
In addition to incident response and threat intelligence services, Check Point continues to invest in software-as-a-service (SaaS) providers and recently acquired both Atmosec and Perimeter81.

12. Sophos
Best for home and small office security
Headquarters: Abingdon, U.K.
Founded: 1985
Annual Revenue: $0.6 billion
Employees count: 3,600-4,500
Appearances on eSecurity Planet‘s Top Vendors lists: 10
Sophos (private), founded in the 1980s, provides consumer antivirus and enterprise solutions for WAF, NGFW, UTM, EDR, cloud workload protection platform (CWPP), encryption, XDR, MDR, and ransomware removal. Thoma Bravo took the company private in 2020, with services being a major focus area under the new ownership.
Customer reviews have been among the best on this list, showing plenty of demand for products that offer good security, value, and ease of use.

13. Zscaler
Best for cloud security
Headquarters: San Jose, CA
Founded: 2007
Annual Revenue: $1.9 billion
Employees count: ~7,400
Appearances on eSecurity Planet‘s Top Vendors lists: 5
Zscaler (NASDAQ: ZS) delivers cloud and edge security through a cloud-native platform that transforms IT infrastructure from castle-and-moat networks to distributed, zero-trust environments. Analysts see promise in this model and forecast a five-year growth rate of 38.2%. Other top solutions Zscaler provides include secure web gateways (SWGs) and deception tools.

14. OneTrust
Best for privacy and compliance
Headquarters: Atlanta, Georgia
Founded: 2016
Annual Revenue: $0.4 billion
Employees count: ~200
Appearances on eSecurity Planet‘s Top Vendors lists: 2
OneTrust (private) is an eight-year-old privacy compliance technology startup that has ridden data privacy laws like GDPR and CCPA to rapid growth. The company provides solutions to quantify and assess the risks associated with data exposure and earns places on our risk management, third-party risk management, and hot cybersecurity startups lists.

15. Rapid7
Best for integrated vulnerability and threat management
Headquarters: Boston, Massachusetts
Founded: 2000
Annual Revenue: $0.8 billion
Employees count: ~2,500
Appearances on eSecurity Planet‘s Top Vendors lists: 10
The Rapid7 (NASDAQ: RPD) security portfolio builds on a strong vulnerability detection and management base and adds SIEM and threat detection capabilities. An emphasis on pricing transparency, value, and ease of use drives growth analysts project to reach 52% over the next five years. That combination has landed Rapid7 on 10 of our top product lists, with vulnerability management being a major highlight.

16. Proofpoint
Best for end user data security
Headquarters: Sunnyvale, California
Founded: 2002
Annual Revenue: $1.1 billion
Employees count: ~3,600
Appearances on eSecurity Planet‘s Top Vendors lists: 7
Proofpoint (private) focuses on securing end users with a product portfolio that includes cloud access security broker (CASB), data loss prevention (DLP), zero trust, threat intelligence, email security, and email gateways. The company cleared the $1 billion revenue mark before Thoma Bravo took it private in 2021.

17. Broadcom
Best for endpoint management
Headquarters: San Jose, California
Founded: 1991
Annual Revenue: $35.8 billion
Employees count: ~37,000
Appearances on eSecurity Planet‘s Top Vendors lists: 12
Broadcom (NASDAQ: AVGO) offers a robust portfolio of security solutions such as CASB, DLP, SASE, SD-WAN, and zero trust. However, their product and service mix continues to shift as they attempt to digest acquisition brands such as Symantec’s enterprise security tools and VMware’s portfolio, which also includes Carbon Black.

18. Trellix
Best for combined XDR & cloud needs
Headquarters: San Jose, California
Founded: 2022 (Trellix), 1987 (McAfee), 2004 (FireEye)
Annual Revenue: Privately held
Employees count: 1,000-5,000
Appearances on eSecurity Planet‘s Top Vendors lists: 6
Trellix focuses on its core network security market and related technology that protects against network threats, such as IDPS, SOAR, and encryption. The company was formed in 2022 when the private equity group Symphony Technology Group (STG) merged technologies and products from FireEye and McAfee Enterprise.

19. Barracuda Networks
Best for remote worker protection
Headquarters: Campbell, California
Founded: 2003
Annual Revenue: Private
Employees count: 2,000-2,500
Appearances on eSecurity Planet‘s Top Vendors lists: 11
Barracuda Networks builds on its pioneering email security products to deliver solutions for WAF, UTM, SASE, and zero trust. The reliable products perform well in testing and customer satisfaction rankings, which also helps place Barracuda in our list of top tools and software for SMBs.

20. Okta
Best for access management
Headquarters: San Francisco
Founded: 2009
Annual Revenue: $2.3 billion
Employees count: 8,000-9,000
Appearances on eSecurity Planet‘s Top Vendors lists: 3
Okta (NASDAQ: OKTA) delivers leading identity and access management (IAM) and zero-trust solutions. With easy-to-use, deploy, and manage products, Okta continues to attract security buyers, and analysts project a long-term expected growth rate of 25% despite several highly publicized breaches.
Other cybersecurity market leaders
The cybersecurity industry is loaded with great companies. The following didn’t make our top 20 cybersecurity companies, but that doesn’t mean they don’t have great products and services. Some continue to gain traction; in other cases, mergers and private equity takeovers have limited our visibility. But all these vendors make our top product lists and meet the needs of many users.
| Honorable Mentions | ||||
| Vendor | # of eSecurity Planet Top Product lists | Market Capitalization | Overall Gartner Peer Insights Score | Overall Glassdoor Score |
| OpenText (DevSecOps, encryption, SSO) | 8 | $6.86 B | 4.3 | 3.4 |
| Ivanti (patch management, VMaaS, ITAM) | 8 | No current valuation | 4.3 | 3.6 |
| Illumio (zero trust, CWPP) | 3 | No current valuation | 4.7 | 4 |
| SkyHigh (CASB, cloud security) | 4 | No current valuation | 4.6 | 3.2 |
| Tanium (zero trust, patch management) | 2 | No current valuation | 4.7 | 4.1 |
Methodology
To compile our list, we started with innovation and market leadership, hence our focus on our rigorously researched top security product lists, or buyer’s guides.
Consistent performance, revenue, and growth were ranking factors, as were strong independent security test results in a market starved for information. User reviews, product features, benefits and use cases, and analyst reports also played a role in our analysis.
Specialization can be a good thing in cybersecurity, with CrowdStrike, Okta, and OneTrust high on our list.
The vendors at the top of the list shouldn’t surprise longtime readers — Palo Alto Networks and Fortinet continue to impress us — and a number of other vendors have also withstood the test of time.
Frequently Asked Questions (FAQs)
What are the main types of cybersecurity?
The security industry is broad, complex, and nuanced — with a brief illustration in the image below:
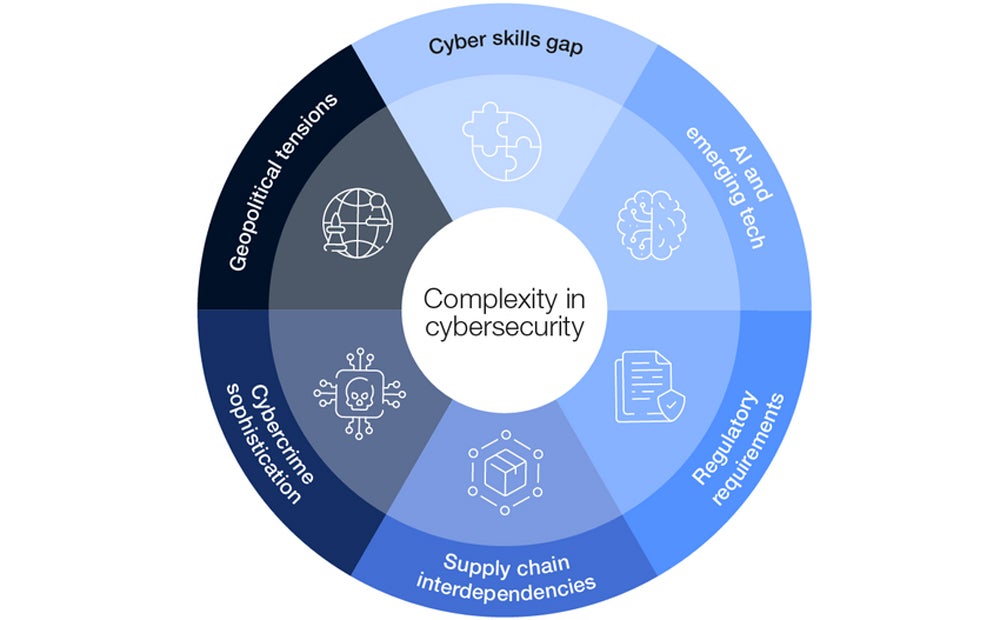
With these numerous complexities come different categories to cater for. The few widely recognized categories of security are:
- Network security: Protects the connections between networks, including data transfers to and from the internet and hardware like routers and switches.
- Endpoint security: Defends devices like laptops, phones, and servers.
- Application security: Adds software, data, and access protection at the individual application level.
- Cloud security: Protects cloud environments and data from vulnerabilities and threat actors.
Note that some security solutions cover multiple categories. For example, extended detection and response (XDR) pulls alerts from endpoints, networks, and applications into a single console for centralized management.
How do you choose a cybersecurity company?
Choosing a cybersecurity vendor involves multiple factors, including company focus, integration issues, customer support needs, your team’s skill level, and your budget. Consider the following questions when choosing a cybersecurity vendor:
- What is the company’s overall focus? If you’re searching for a container security solution, consider a vendor specializing in cloud and application security.
- How many of their solutions will you use? If you have software or hardware from another security vendor, do they integrate well? And look at support for other applications.
- What are your customer support needs? Signs that a vendor has good technical service include 24/7 support in multiple channels and high praise for the support team in reviews.
- Can your business afford it? Some smaller businesses might not have the budget for vendors like Palo Alto and CrowdStrike, and that’s okay. There are plenty of providers that have security solutions designed for small companies.
Will cybersecurity jobs become obsolete?
If you’re a job seeker in the security industry or considering a career change, know that cybersecurity careers aren’t going anywhere.
These positions might continue to change as the industry evolves, but the demand for cybersecurity skills and training remains strong. Today’s IT climate requires knowledge of large security platforms, detection and response technologies, and sometimes distributed systems.
Job seekers must research the field and curate the most useful skills for potential employers. Organizations like EC-Council and CompTIA+ have certifications that provide a springboard for individuals wanting to start a security career. Continued education is critical for staying on top of threats—never stop learning.
What are the top cybersecurity companies to work for?
The following companies are a sample of highly rated enterprises with strong security solutions. If you’re looking for a career change, consider open roles with these tech organizations.
- SentinelOne offers good benefits and receives 4.4 out of 5 stars on Glassdoor. It is also comparatively small in the security industry, with fewer than a thousand employees. The company boasts some pretty stellar cybersecurity products.
- Netskope offers its personnel flexible spending accounts, a 401(k), and employee stock purchase plans. Its Glassdoor employee reviews earn it 4.2 stars. Netskope specializes in SASE, CASB, and SD-WAN technology.
- Palo Alto Networks has employee benefits like stock purchase plans, development courses, and a 401(k). It earns 4 stars on Glassdoor. Palo Alto has some of the best and broadest security in the entire industry, so there’s lots of opportunity to experience different facets of security.
- Fortinet offers employees unlimited PTO, a health savings account, and a 401(k). It, too, has 4 stars on Glassdoor. Fortinet is known for its firewalls but excels elsewhere, including in SIEM and EDR.
- And don’t forget big IT vendors with a security presence. Cisco (4.3 stars from Glassdoor) and Akamai Technologies (4.4) are two standouts.
- Lastly, CyberArk offers an investment, employee recognition, and tuition reimbursement program. The IAM leader receives 4.3 stars on Glassdoor.
Bottom Line: Top Cybersecurity Companies
The enterprise security market is wide, covering a range of technologies and systems that must be protected. Some vendors offer a variety of products, while others specialize in just one or two.
Consider your needs before choosing a potential provider for your business. While all the vendors listed above offer strong solutions, researching and demoing products is worthwhile until you find one well-suited to your organization’s cybersecurity needs.
Crave more insight into the cybersecurity companies in the market? Read about the top cybersecurity startups.




