Data security compliance is the act of applying risk-reducing security controls to match relevant data protection regulations, security frameworks, and security policies. Governments provide the primary data regulations with the largest penalties, yet data security frameworks and policies provide the most tangible guidelines that enable best practices and provide the basis for standardized compliance tools and services.
Major Security Regulations & Laws
Governments pass data security regulations and laws to force organizations of all sizes to better protect customers and consumers through improved cybersecurity practices. Currently, most laws focus on the protection of data, specifically personal identifiable information (PII), but some regulations also cover financial and healthcare information.
The major international laws for data protection include:
- General Data Protection Regulation (GDPR): The European Union (EU) regulation to protect personal data with extremely broad PII definitions and punishing fines.
- California Consumer Privacy Act (CCPA): The first of many US state laws to require protection for personal data and a mechanism to sue over data breaches.
- Personal Information Protection Law (PIPL): The Chinese law to protect the PII associated with citizens within the People’s Republic of China against breach or misuse.
- Health Insurance Portability and Accountability Act (HIPAA): The US federal law that requires the protection of medical records and personal health information.
- Gramm-Leach-Bliley (GLB) Act: The US federal law that requires financial institutions to protect non-public personal financial information.
Some regulations create regulating bodies with broad and less-defined enforcement capabilities. The US Securities Exchange Commission (SEC) and US Federal Trade Commission (FTC) both fall into this category and periodically assess fines and criminal charges related to data breaches.
Security Regulation Requirements
At their core, the data security laws require companies, non-profits, and other entities to prevent leak or misuse of regulated data. In general, regulations define protected data and security requirements broadly, with some details for definitions and reporting requirements. The table below provides a high-level overview of the major regulations:
| International Law | Protected Data | Security Requirements |
|---|---|---|
| GDPR | Personal data of EU citizens or residents, even if not within the EU. | Demonstrate GDPR compliance, handle data securely, notify EU officials within 72 hours of a data breach. |
| CCPA | Personal information of California residents. | Notify any California resident of personal data exposed by a breach; notify state officials of breaches of 500 or more. |
| PIPL | Personal information of people within China. | Identify and exclude data from unnecessary processing (collection, storage, use, processing, transmission, provision, publication, and erasure). |
| HIPAA | Personal health information and medical records. | Safeguard integrity, availability, and security of healthcare data. |
| GLB | Any nonpublic personal information of a financial institution’s consumers. | Safeguard customer information. |
Despite broadly defined requirements, regulations apply specific penalties for violations. For example, the GDPR states a maximum penalty of the greater of 4% of annual global turnover or €20 million. HIPAA civil penalties range from civil fines between $100 and $1.5 million per year to criminal jail sentences up to 10 years.
Companies often settle with regulators on penalty amounts below the maximum penalty, but the amounts can remain high and significantly impact the business. Recent examples of penalties include:
- €1.2 billion fine in 2023 for Meta GDPR violations.
- €746 million fine in 2021 for Amazon GDPR violations.
- €405 million fine in 2022 for Meta GDPR violations.
- $5.1 million fine in 2021 for Lifetime Healthcare Companies HIPAA violations.
The broad and vaguely defined security requirements allow the regulations to survive changing technology landscapes, but as a consequence make the requirements unclear and difficult to satisfy. Most organizations defend themselves by selecting a security standard that offers more concrete guidance for implementing, assessing, and reporting compliance.
Major Security Standards & Frameworks
Security standards are specific requirements for specific IT goals or best practices. Security frameworks consist of collections of security standards, procedures, and best practices. While some frameworks can be developed by governments, private industry groups develop and enforce many of the broadly adopted security standards and frameworks.
Major security standard frameworks include:
- National Institute of Standards and Technology (NIST) Cybersecurity Framework: Develops a common foundation for security applicable to many different organizations.
- Health Information Trust Alliance (HITRUST) Common Security Framework (CSF): Defines a set of security principles specifically designed to protect HIPAA data.
- Payment Card Industry Data Security Standards (PCI DSS): Defines the security standards that must be implemented to maintain the right to process payment cards.
- International Organization for Standardization (ISO): Offers many security standards to standardize security processes and objectives such as ISO-27001 or ISO 27799.
- System and Organization Controls (SOC) 2: Provides a framework to certify an organization’s IT security, availability, integrity, confidentiality, and privacy controls.
Security Framework Requirements
Frameworks provide much more guidance than regulations by breaking down security principles into areas with specific goals, functions, and policies. Once you decide to adopt a framework for your organization, you need to develop security policies to define how the company will enforce each framework requirement, implement the policies, and then test the systems to ensure they fulfill the goals of the policies and the framework.
Some voluntary frameworks allow for self-enforced and self-certified enforcement with no penalties for non-compliance. Others, such as PCI DSS, require mandatory participation to retain card payment privileges and require independent third-party auditors to verify compliance. Such auditors often must be certified by the association that developed the framework in order to perform certification audits.
Although more prescriptive than regulations, frameworks also tend to remain at a relatively high level to avoid technology lock-in or overly prescriptive requirements. For example, consider endpoint protection.
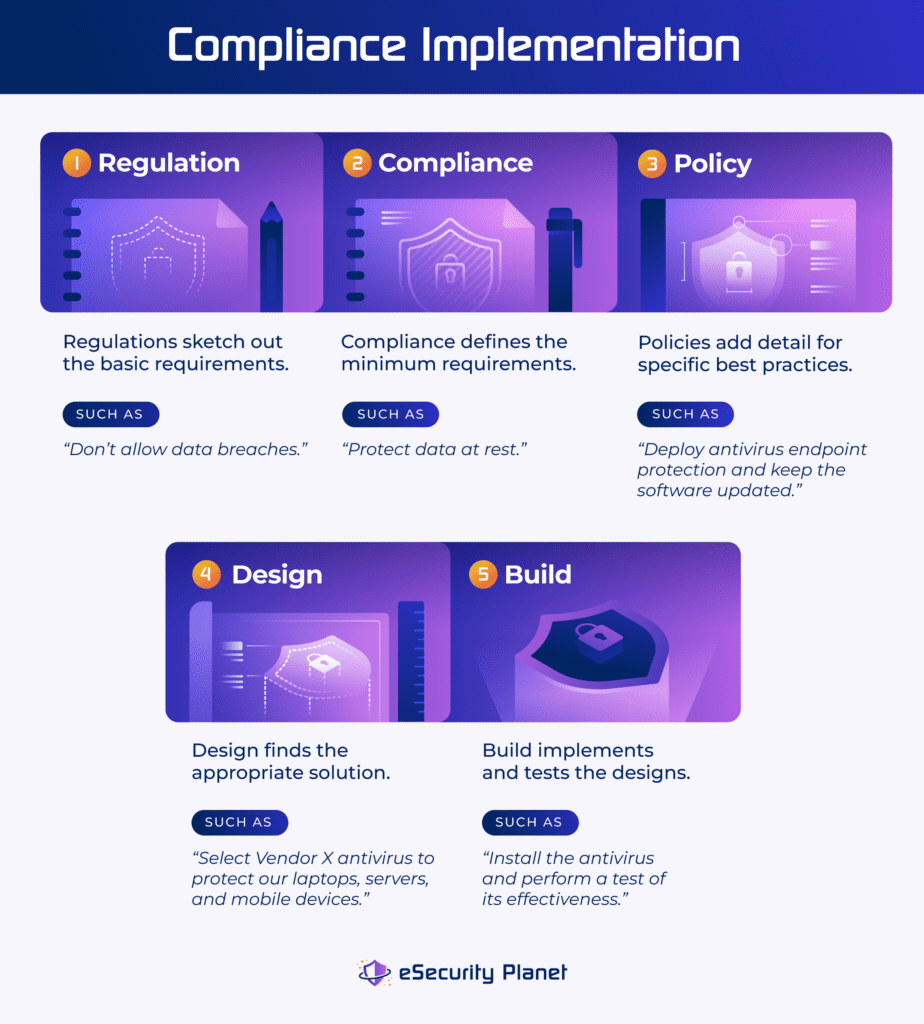
The NIST CSF framework for Data Security (PR.DS-01) expects that “the confidentiality, integrity, and availability of data-at-rest are protected.” PCI DSS endpoint security standard requires organizations to “maintain a vulnerability management program” and to “protect all systems against malware and regularly update anti-virus software or programs.” Neither specifically mentions endpoints and only one specifies a technology (antivirus).
Why Comply with Data Security Laws & Standards
We comply with data security laws, standards, and frameworks for three key reasons: We have to comply to avoid punishment, they make us better, and they help us limit damages.
We Must Comply to Avoid Punishment
We have to abide by laws and regulations or we face penalties and punishments:
- Financial and criminal penalties: Avoid fines, expensive settlements, and even possible jail time that might be triggered by failure to comply with regulations.
- Public embarrassment: Escape mandatory reporting laws for breaches by using compliance to limit the potential scope and magnitude of data breaches.
- Business loss: Retain business contracts and insurance coverage that require specific security standards or frameworks to be maintained such as PCI DSS for card payments.
Recently, many small companies that might otherwise be exempt from compliance began to not receive demands for compliance validations from their large customers. Newer regulations force validation from the supply chain, which widens the requirements beyond the scope of the original regulations.
Compliance Makes Us Better
Compliance with regulations, standards, and frameworks can improve the overall business through security best practices, additional data protection, insurance requirement satisfaction, reputation protection, and new business opportunities.
- Enforces best practices: Informs effective security controls, documentation, monitoring, testing, reporting, and remediation for a broad spectrum of security.
- Protects data: Enforces compliance with regulated data that also potentially adds controls to protect corporate secrets from theft and help enforce good business practices.
- Meets insurance requirements: Delivers controls and reports that naturally improve an organization’s ability to validate existing controls for cybersecurity insurance coverage.
- Protects reputation: Provides security penetration test reports that assure customers, security to minimize breaches, and security system resilience for business continuity.
- Wins new business: Adds opportunities to win new business; for example, a CMMC certification enables bids for DoD contracts or to subcontract to existing DoD vendors.
Although compliance typically will be seen as a cost center, look for opportunities to work with sales to capitalize on verifiable security levels and compliance certifications.
Compliance Limits Damages
Compliance can’t guarantee security, so an incident or data breach may still occur. Fortunately, compliance implementation, testing, and reporting can limit negligence claims, breach scale, and attack-related costs.
- Negligence claims: Eliminates inflated negligence penalties through validated third-party standards for good security and defined-reasonable security safeguards.
- Breach scale: Reduces the attackers’ reach, quantity of data obtainable, and abuse potential of stolen data when protected by effective compliance controls.
- Attack-related costs: Contains attacks to a smaller footprint that reduces the time and expenses for investigation, recovery, and remediation.
A breach still incurs costs, but certified data security compliance tends to decrease the overall costs significantly.
Challenges of Security Compliance
Compliance clearly provides legal and financial protection, if not advantages. Yet the challenges of security compliance that limit adoption include:
Unclear Identification
Many organizations struggle to perform the basics for security, let alone apply compliance, when they lack clear identification of devices, compliance obligations, compliance proof, and data.
- Device awareness: Continues to fall behind as users unexpectedly add bring-your-own-device (BYOD) and internet-of-things (IoT) devices to networks.
- Compliance obligation: Remains vague for vendors, service providers, and small and medium businesses (SMBs) on the edge of complex definitions for regulated entities.
- Compliance proof: Variances in consultant and attorney interpretations of laws and policies lead to dangerous differences in standards of proof for compliance.
- Murky data: Increases in data quantity, expanding storage locations, and widespread usage add difficulty for data classifications and understanding which regulations apply.
Rapid Changes
Regulations, frameworks, standards, and internal policies struggle to keep up with constant and rapid changes such as:
- Evolving networks: Expands the network to include remote worker BYOD, edge computing, software-as-a-service (SaaS), containers, and IoT.
- Increased complexity: Adds additional skill and time demands by shifting to cloud workloads and adding wireless connectivity to operational technologies (OT).
- System users: Challenges compliance definitions of users when artificial intelligence (AI), apps, and application programming interfaces (APIs) access and analyze data.
- Volume increases: Increases compliance challenges constantly with more users, added systems, and ever-increasing data to evaluate, control, and secure.
Managing Conflicts
Compliance introduces natural conflicts between security, finance, human resources, and even external parties to manage issues including:
- Definition ambiguities: Makes legal impose conservative requirements impossible to technically achieve when various laws introduce different and conflicting requirements.
- Older technology: Rejects potentially improved solutions (e.g., endpoint detection and response) because standards still specifically require older tech (e.g., antivirus).
- Regulatory ownership: Applies to one company in a supply chain, but a breach in any other part of the chain still affects every organization and may trigger fines.
- Resource limitations: Leads to dangerous compromises and risk denial to meet budgets and impose compliance minimums that might leave systems vulnerable.
6 NIST Best Practice Categories for Data Security Compliance
Different regulations, policies, and frameworks will apply to different specifics, but generalized best practices apply to all compliance programs. The NIST CSF framework provides a useful organization we can use to discuss the core best practices of compliance (govern, identify, protect, detect, respond, and recover) before we consider additional best practices.
Govern
The NIST governance best practices incorporate compliance into broader corporate data, enterprise risk management (ERM), and operations initiatives and these include:
- Organizational context: Matches compliance objectives with existing organizational objectives such as legal requirements, contractual obligations, and operations goals.
- Risk management strategy: Defines priorities, constraints, risk tolerance, risk appetites, and outlines assumptions to inform and support compliance decisions.
- Roles, responsibilities, and authorities: Assigns the personnel to implement, oversee, and monitor each compliance component’s implementation and maintenance.
- Policy: Places the goals, objectives, principles, roles, and reporting into a written security policy to guide each of the other stages in the compliance process.
- Oversight: Formalizes how compliance results will be used to inform, improve, or adjust the compliance process and related activities such as operations and risk management.
- Supply chain risk management: Extends compliance to supply chain partners through identification, risk assessment, prioritization, and negotiation.
Relevant tools and services to achieve these best practices include compliance and risk management tools and specialized consultants.
Identify
Best practices related to identification, as defined by NIST, seek to understand the true risks to the organization to be addressed in other compliance stages and require performing all of the steps below.
- Asset management: Identifies relevant assets that control, use, or protect compliance assets such as data, hardware, software, systems, services, people, and facilities.
- Risk assessment: Evaluates and assigns risk to each asset to help prioritize assets for protection and identify the types of risks to be mitigated through security controls.
- Improvement: Locates areas for improvement through evaluations, tests (internal or third-party), operations, and incident response after-action plans.
Identification starts within IT operations, but security tools such as identity and access management (IAM), vulnerability scanners, or penetration testing services accelerate the identification process and provide verifiable consistency for reporting.
Protect
NIST protection best practices reduce risks for network security and cloud security to an acceptable threshold as defined by governance best practices and to meet compliance requirements to implement security controls for the following:
- Identity management, authentication, and access control: Controls physical or virtual access to assets by validating identities for defined and authorized access levels.
- Awareness and training: Educates employees to understand their roles in security or compliance and how to safely conduct operations and identify potential attacks.
- Data security: Applies security controls to protect data at rest, data in transit, data integrity, and ongoing availability through protected and maintained backups.
- Platform security: Secures physical and virtual systems and connected infrastructure from attacks that might compromise their confidentiality, integrity, or availability.
- Technology infrastructure resilience: Accounts for the likelihood of failure of other protection best practices to implement redundancies or backup controls.
A huge number of security tools focus on protection from classic endpoint and firewall technologies to modern application security and secure access service edge (SASE) tools.
Detect
NIST best practices for detection locate anomalies, initiated or ongoing attacks, insider threats, and other potential compromises to assets or controls through the implementation of:
- Continuous monitoring: Uses logs, tools, and personnel to monitor systems, internal staff, external services providers, and processes for attack or potential vulnerabilities.
- Adverse event analysis: Examines potential signs of attack and vulnerability to determine risk threat level and segregate true threats from false alarms.
Relevant detection tools include network monitoring tools, log monitoring tools, and security information and event management (SIEM) tools.
Respond
Response best practices under NIST define the management process that must be implemented to respond to attacks or vulnerabilities based upon the threat level and urgency. These include:
- Incident management: Determines triage, categorization, prioritization, escalation, elevation, criteria, and third-party roles for responding to attacks and vulnerabilities.
- Incident analysis: Defines processes for analysis, actions, record taking, evidence collection, and magnitude for all types of incidents.
- Incident response reporting and communication: Establishes notifications and information required for internal and external stakeholders at various incident levels.
- Incident mitigation: Provides processes, tools, and potential service providers for escalation to contain and eliminate attacks and other potential threats.
Incident response tools vary from vulnerability management software to specialized incident response tools. Internal staff will often be complemented by outside consultants or services providing a similar range of services from patch management as a service to managed detection and response (MDR).
Recover
Recovery best practices in the NIST framework implement the processes to plan, execute, and communicate fixes during and after an incident:
- Incident recovery plan execution: Establishes plans, prioritizes actions, verifies backups, restores operations, verifies asset restoration, and creates after-action reports.
- Incident recovery communication: Provides accurate, coordinated, and timely information to internal or external stakeholders, regulators, and the public.
Recovery processes often require disaster recovery solutions but may also involve coordination with non-technical consultants such as attorneys and public relations specialists.
Additional Best Practices
While the NIST framework organizes best practices within security compliance, it doesn’t address best practices about compliance. Improve every data security compliance framework or policy with additional best practices such as:
- Constant improvement: Enables increased security, risk reduction, and potential cost savings through constant improvements in operations and security systems.
- Advanced options: Reduces risk from future negligence claims stemming from vague regulations and standards by going above and beyond minimums when reasonable.
- Scope limitation: Confines risk and highest compliance obligations to limited systems by restricting data access and implementing controls for least-privilege access.
Each compliance regulation, framework, and policy introduces specific requirements. While best practices address the broadest issues, analyze regulations thoroughly to ensure adequate capture of all specific requirements.
Compliance Tools & Services
Many tool vendors and service providers can provide security controls but don’t manage the compliance processes themselves. Select specialized classes of tools for governance and risk management or even service providers to help accelerate and assist with compliance tasks.
Governance, Risk & Compliance Tools
Governance, risk, and compliance (GRC) tools automate and organize the tasks to manage risk, compliance reports, internal policies, and related cybersecurity concerns. The top tool to use depends on the broad or specific needs of the compliance program.
For example, Archer GRC provides the best option for a breadth of features and ServiceNow provides the best automation for GRC solutions. Yet, for specific risk reporting needs, LogicManager may provide the best GRC tool fit.
Third-Party Risk Management
Third-party risk management (TPRM) provides specialized vendor risk management (VRM) tools to manage supply chain risk. These tools focus on assisting with the vendor onboarding processes with respect to compliance requirements and risk assessments.
In the eSecurity Planet assessment of best TPRM tools, OneTrust performed the best overall in our evaluation. Other tools to consider would be Venminder for the best customer support category or the Prevalent TPRM Platform for the best VRM assessments.
Service Provider & Consultants
Consultants, managed service providers (MSPs), and managed security service providers (MSSPs) can supply services to manage or validate compliance. The variety of service providers equals the spectrum of consulting needs from specialized assistance to fully-outsourced turn-key processes.
The largest corporations and governments will seek equally large consulting service providers such as Accenture or NTT. However, smaller organizations may seek a specialized fit from smaller local service providers or specialty service providers such as penetration testing services from vendors like Intruder.
When to Use Tools or Services
Which tool or what type of service provider to use depends on available resources and risk maturity. New compliance initiatives need more help and will lean on the guidance of experienced consultants that apply an established understanding of requirements to quickly implement relevant controls.
More advanced programs can switch to internal programs run by internal compliance teams and boosted by GRC or TPRM tools. However, even the most advanced program must still turn to outside consultants for audits and effective pentests.
Potential Future Regulations
The best compliance frameworks provide insurance against future regulations, but they also help to keep an eye out for oncoming laws to avoid unpleasant surprises. Anticipated regulations include additional US privacy laws, new international privacy regulations, AI regulations, expanded or new breach reporting laws, and enforcement details added for US government and DOD contractor compliance requirements.
Additional US Privacy Regulations
US states continue to enact personal information protection laws, with 22 laws, 15 of them comprehensive, enacted by 2024. Expect additional states to pass laws, but hopefully also a US federal legislation to provide standardized protection and eliminate discrepancies, gaps, and conflicts between state laws.
Additional International Privacy Regulations
In addition to the EU and China, the United Arab Emirates and South Africa passed laws to protect personal information and consumer data. Expect others to follow suit to protect their citizens and to generate revenue from fines and settlements.
AI Regulations
The European Union just passed the AI Act that will become enforced later in 2024. The act imposes rules to address AI risks, practices, applications, obligations, assessments, and governance. Best practices for how the law affects AI use will become possible after sufficient attorney evaluation and legal testing of the rules in the months to come.
Breach Reporting Laws Expand
The 2022 Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) instructs the US Cybersecurity and Infrastructure Security Agency (CISA) to develop regulation similar to current SEC rules for reporting cyber incidents and ransomware payments. Enforcement potentially begins in 2025 pending definitions of the entities covered, disclosure requirements, disclosure thresholds, and penalties. Expect overall regulations to increase and expand in scope.
Enforcement of US Government Contractor Compliance
The US Department of Defense (DOD) will shortly propose version 2.0 of the Cybersecurity Maturity Model Certification (CMMC) that is required to maintain a DoD contract. The release date for the fully-fledged model and enforcement date remain pending. The Federal Acquisition Regulation (FAR) Council will also require incident reporting and compliance for unclassified federal information systems applicable to all government contractors.
Bottom Line: Compliance Provides Security Opportunities
The most common fears regarding compliance involve increased time, resources, and hassles. Yet, compliance can provide opportunities to rigorously examine security, risk, and operations to determine weak spots in the security stack. Compliance not only helps uncover vulnerabilities, but it also helps to define reasonable security practices, which can protect against potential breaches and lower overall costs associated with security incidents.
Compliance initiatives only define controls and systems. Read more about the types of penetration testing that verify and validate implemented security controls.




