Endpoint detection and response (EDR) platforms help IT teams identify threats on devices and limit cyber attacks by remediating potential threats. The best solutions offer features like threat hunting, behavioral analytics, and incident containment. I analyzed many of the top EDR products in the cybersecurity industry and scored them based on features and capabilities, selecting the highest-scoring solutions for my final list.
Here are my picks for the eight best EDR solutions:
- Microsoft Defender for Endpoint & XDR: Best overall for features and administration
- Palo Alto Networks Cortex XDR: Best for experienced IT and security teams
- Trend Micro Vision One: Best for supporting junior cybersecurity teams
- FortiEDR: Best for integrations with FortiGate firewalls
- SentinelOne Singularity: Best for dedicated forensics and third-party integrations
- CrowdStrike Falcon Insight: Best for advanced threat response capabilities
- ESET Protect: Best for basic EDR functionality
- Cybereason Defense Platform: Best for advanced threat visualization
Top EDR Solutions Compared
The following table briefly compares our top picks, including features like threat hunting, custom detection rules, and trial details.
| Automated Remediation | Threat Hunting | Custom Detection Rules | Free Trial | |
|---|---|---|---|---|
| Microsoft Defender XDR | ✔️ | ✔️ | ✔️ | 30 days |
| Palo Alto Cortex XDR | ✔️ | ➕ | ✔️ | ❌ |
| Trend Micro Vision One | ✔️ | ✔️ | ✔️ | 30 days |
| FortiEDR | ✔️ | ✔️ | ✔️ | ❌ |
| SentinelOne Singularity | ✔️ | ✔️ | ❌ | 30 days |
| CrowdStrike Falcon Insight | ✔️ | ✔️ | ❌ | 15 days |
| ESET Protect | ✔️ | ✔️ | Unclear | 30 days |
| Cybereason | Unclear | ✔️ | ✔️ | ❌ |
✔️=Yes ❌=No/Unclear ➕=Add-On
Based on my analysis, Microsoft Defender for Endpoint and Defender XDR are your business’s best endpoint protection options. However, all of my picks are robust solutions depending on your organization’s needs. Continue reading to learn more, or skip down to see how I evaluated the best EDR products.

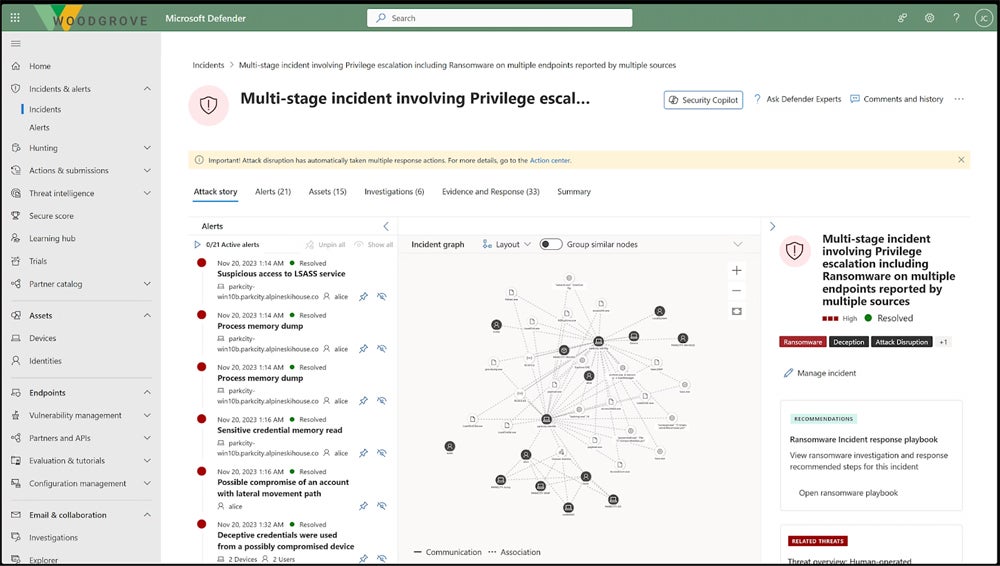
Microsoft Defender for Endpoint & Defender XDR – Best Overall for Features & Administration
Overall Rating
4.2/5
Pricing
3.6/5
Features
4.1/5
Usability
5/5
Administration
4.8/5
MITRE scores
5/5
Customer support
3.2/5
Microsoft Defender for Endpoint and Defender XDR are detection and response solutions for endpoints, cloud apps, collaboration software, and identity management. Microsoft has built a surprisingly strong security business, and a selection of advanced protective features — and consistently high MITRE scores — show that. Consider Defender for Endpoint or XDR if you’re looking for a product with administrative capabilities like dashboards and policy creation.
Pros
Cons
- Contact for quote: Custom pricing available
- Free trial: 30 days
- Automated remediation: Automatic incident response helps security teams prioritize threats.
- Sandboxing: Partner products include Splunk and Bitdefender GravityZone.
- Third-party integrations: Defender XDR helps teams locate unprotected devices on their network.

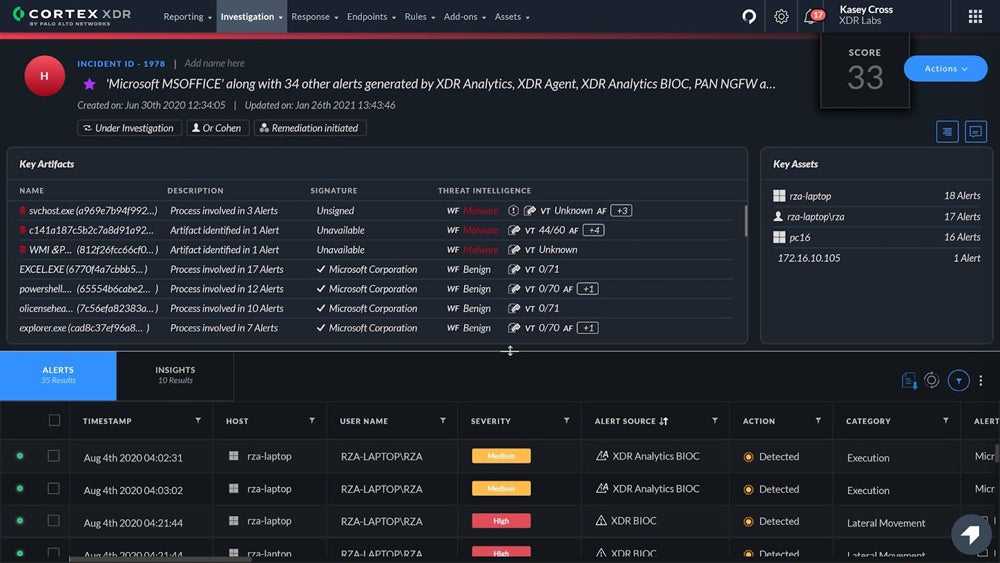
Palo Alto Cortex XDR – Best for Experienced IT & Security Teams
Overall Rating
4.1/5
Pricing
2.3/5
Features
4.2/5
Usability
4.7/5
Administration
4/5
MITRE scores
5/5
Customer support
4.7/5
Palo Alto Networks’ Cortex XDR is a sophisticated platform for advanced security teams that want features like sandboxing and forensics tools. Palo Alto topped the 2023 MITRE test results with perfect scores; it’s one of the market’s most established and secure endpoint protection vendors. If you’re a large enterprise with a built-out IT or security team, consider Cortex XDR — if you have the budget for it, it could be one of the best security investments you ever make.
Pros
Cons
- Contact for quote: Custom pricing available
- Free demo: Contact to schedule
- Root cause analysis: Automated discovery of threats’ root causes helps security teams focus on other tasks.
- Forensic investigations: Administrators and analysts can perform detailed analysis on endpoint behavior.
- Detection rules: Teams can use Palo Alto’s out-of-the-box and custom rules.
- Incident triage: Cortex XDR filters threats using incident fields and prioritizes them for remediation.

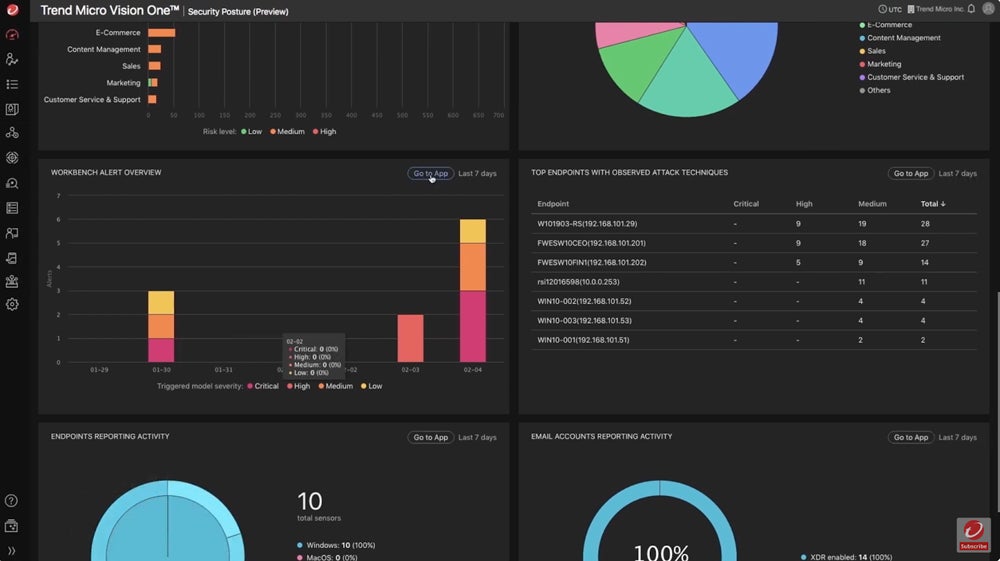
Trend Micro Vision One – Best for Supporting Junior Security Teams
Overall Rating
4/5
Pricing
3.6/5
Features
4.1/5
Usability
4.7/5
Administration
3.8/5
MITRE scores
4/5
Customer support
4.3/5
Trend Micro’s Vision One platform is an XDR and attack surface management solution, also referred to as Trend Micro XDR. Another vendor now vying for the XDR space, Trend Micro’s range of security offerings is impressive, spanning cloud, containers, network security, and endpoints. Its managed XDR services are a good choice for smaller organizations that don’t have an extensive IT team.
Pros
Cons
- Contact for quote: Custom pricing available
- Free trial: 30 days
- Free demo: Contact to schedule
- Guided investigation: Guided threat exploration helps teams identify the best remediation strategies.
- Detection rules: Rules designed to locate and identify threats are added based on discoveries from threat experts.
- Policy adjustments: You can change policies based on recent insights that Vision One discovers.
- Customized dashboards: The boards are relevant to team members’ specific organizational roles, like SecOps or CIOs.
EDR isn’t just a solution you should set and forget (and often, you can’t). Read our guide to tuning your EDR product to learn more about tailoring it to your business’s needs so you’re not just using the default configurations and so hackers don’t have an easy in.

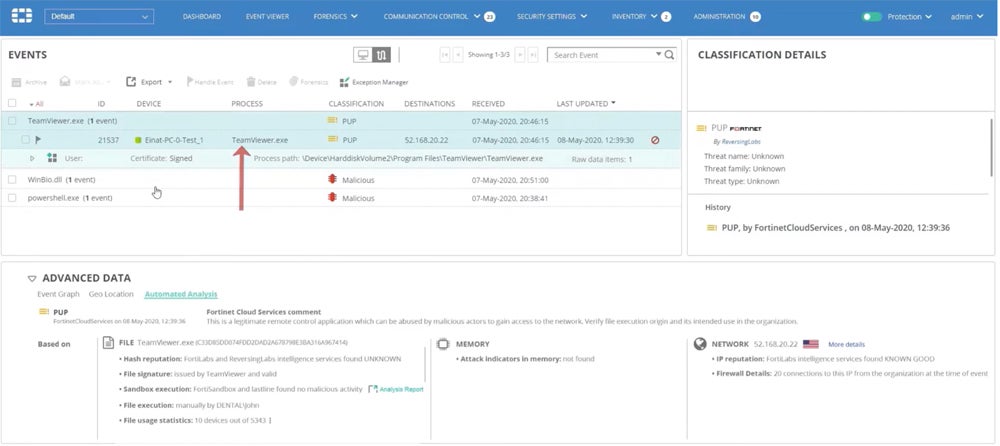
FortiEDR – Best for Integrations With FortiGate Firewalls
Overall Rating
4/5
Pricing
2.7/5
Features
3.1/5
Usability
4.7/5
Administration
5/5
MITRE scores
4.3/5
Customer support
4.7/5
FortiEDR is a network security provider for Fortinet’s endpoint detection and response solution. While Fortinet is best known for its firewalls, its EDR solution is an excellent choice for existing customers and users outside the Fortinet ecosystem. Features include threat intelligence, USB device control, threat hunting, and detection rules. If you already have FortiGate firewalls installed, consider expanding to other products in Fortinet’s Security Fabric.
Pros
Cons
- Contact for quote: Custom pricing available
- Free demo: Contact to schedule
- Role-based access: Admins can set RBAC to help reduce misconfigurations and restrict access to sensitive controls.
- Security policies: FortiEDR comes with out-of-the-box policies and allows admins to define additional policies as well.
- Incident classification: FortiEDR automatically classifies security incidents so you can prioritize responses.
- Code-tracing: One of the product’s threat-hunting features helps detect the cause of a threat even when the endpoint is offline.

SentinelOne Singularity – Best for Dedicated Forensics & Third-Party Integrations
Overall Rating
3.9/5
Pricing
3.4/5
Features
3.8/5
Usability
3.7/5
Administration
4/5
MITRE scores
4/5
Customer support
4.7/5
SentinelOne Singularity is a comprehensive security platform with multiple plans ranging from essential endpoint protection to full XDR. Singularity offers RemoteOps Forensics as part of its platform, allowing teams to focus more intensely on endpoint and threat data. Singularity Marketplace’s third-party integrations include Splunk, ServiceNow, and Zscaler. SentinelOne is a good choice for teams that want to explore forensics and also need plenty of integrations.
Pros
Cons
- Singularity Core: $69.99 per endpoint; unspecified period of time
- Singularity Control: $79.99 per endpoint
- Singularity Complete: $159.99 per endpoint
- Singularity Commercial: $209.99 per endpoint
- Singularity Enterprise: Contact for quote
- Free trial of Singularity Control: 30 days
- Free demo: Contact to schedule
- Advanced endpoint controls: Singularity Control helps you manage USB and Bluetooth devices, set firewall controls, and discover rogue devices.
- Managed threat hunting: SentinelOne’s WatchTower service is a 24/7 solution for threat hunting and detailed attack surface assessments.
- Data retention: Singularity’s Commercial and Enterprise plans both retain data for 90 days.
- Identity threat detection and response: Protect your Active Directory and Azure AD environments with tools like misdirection and hiding credentials.

CrowdStrike Falcon – Best for Advanced Threat Response Capabilities
Overall Rating
3.9/5
Pricing
3.5/5
Features
3.7/5
Usability
3.5/5
Administration
3.5/5
MITRE scores
5/5
Customer support
4.7/5
CrowdStrike Falcon Insight is a solution for teams needing advanced EDR features. CrowdStrike offers robust security, as evidenced by its nearly-perfect MITRE scores, but its management and response capabilities are where the vendor shines. Features include threat hunting, prioritization, and security posture assessments. Consider Falcon Insight if your IT team wants advanced response features and plenty of opportunities to grow in their expertise.
Pros
Cons
- Contact for quote: Custom pricing available for Falcon Insight XDR, which falls under the Falcon Elite plan
- Free trial: 15 days
- Free demo: Contact to schedule
- Posture assessments: Falcon’s assessments help teams identify unsafe or outdated sensors and settings.
- Threat context: Falcon Insight offers threat attribution to give details about vulnerabilities.
- Falcon Sandbox: Users can analyze unknown malware and other threats in more detail with the sandbox.
- MITRE mapping: Compare threats to the MITRE ATT&CK framework to better understand specific detections.

ESET Protect – Best for Basic EDR Functionality
Overall Rating
3.9/5
Pricing
4/5
Features
3.5/5
Usability
4.5/5
Administration
4.3/5
MITRE scores
1.3/5
Customer support
5/5
ESET Protect is a platform for antivirus, endpoint protection, and device control, leading to managed detection and response if your business needs it. It also offers protection for your team’s mobile devices. With essential features like anti-phishing and advanced capabilities such as XDR network protection, ESET is a great choice if you’re just starting EDR but will want to expand those features over time.
Pros
Cons
- ESET Protect Entry: $211 annually for 5 endpoints
- ESET Protect Advanced: $275 annually for 5 endpoints
- ESET Protect Complete: $287.72 annually for 5 endpoints
- ESET Protect MDR: Contact for quote
- Free trial: 30 days
- Free demo: Contact to schedule
- Vulnerability and patch management: ESET automatically scans your operating systems and applications, reports gaps, and patches issues as needed.
- Mobile threat defense add-on: This extra product includes mobile device management for iOS, lateral movement prevention, and app blocking.
- Cloud Office Security: ESET protects Microsoft 365 and Google Workspace apps from threats like phishing and malware.
- Mail security: Microsoft Exchange and IBM email servers receive host server protection and anti-phishing coverage.
Read more about different approaches to network protection, including EDR and MDR, in our guide to the types of network security solutions.

Cybereason – Best for Advanced Threat Visualization
Overall Rating
3.8/5
Pricing
2.2/5
Features
3.8/5
Usability
4.3/5
Administration
4.3/5
MITRE scores
5/5
Customer support
3.9/5
Cybereason’s Defense Platform is a detection and response solution with strong features and extensive documentation. Cybereason’s Defense Platform takes a comprehensive approach to threats, known as malicious operations (MalOps). By analyzing threat data and creating a comprehensive attack story, Cybereason aims to provide more context to malicious behavior. Consider Cybereason if your team is looking for detailed threat visualizations.
Pros
Cons
- Contact for quote: Enterprise, Enterprise Advanced, and Enterprise Complete bundles available
- Free demo: Contact to schedule
- Cloud integrations: Cybereason supports significant cloud providers such as Google, AWS, and Microsoft Azure.
- Cloud workload analysis: XDR for cloud also helps your team protect container environments.
- Digital forensics capabilities: Root cause analysis helps businesses investigate incidents in greater detail.
- Visualizations: MalOps centralizes data to give you a comprehensive view of each threat.
5 Key Features of EDR Solutions
Important EDR features include behavioral analytics, automated remediation, vulnerability management, device monitoring and control, and threat intelligence integrations. Use this list of EDR features to narrow down a good fit for your business based on platform capabilities.
Behavioral Detection
Behavioral analytics use machine learning technology, which studies thousands to millions of user and device behaviors to identify abnormal patterns. These patterns could indicate a malicious user or a downloaded strain of malware. Behavioral detection is a crucial EDR feature because it uses an immense amount of data to automatically locate potential threats that would take more time to detect manually. It can be helpful in zero-day attacks, too.
Automated Remediation
Security teams can configure automatic threat remediation by setting remediation rules in advance or using prebuilt ones. A particular action on an endpoint triggers a predefined remediation policy, and without any human interaction, the EDR tool sets remediation in motion. Automation is helpful because it reduces manual remediation work for security admins. It’s a particularly good feature for small or overwhelmed security teams.
Vulnerability Monitoring & Management
EDR solutions consistently monitor endpoints, alerting security teams when the software unearths vulnerabilities that could be exploited. These can include outdated operating systems, backdoors, and misconfigurations. Automated searches for vulnerabilities are more efficient, allowing IT and security teams to catch them quickly and spend time on other tasks.
Device Control
EDR solutions monitor USB devices and other direct-attached storage for malicious behavior. Threat actors use USB and flash drives to infect systems with malware, and employees often plug unfamiliar storage devices into computers without knowing what’s on them. EDR tools allow admins to set strict policies for device use and determine when to give remote access permissions to USB devices.
Threat Intelligence Feed Integration
Threat intelligence integrations are essential because they compile threats and indicators of compromise (IoC) so your team can look for a wide range of behaviors and threats. Many EDR tools integrate with third-party threat intel solutions, so your team has more information to keep the business on top of vulnerabilities.
How I Evaluated the Best EDR Solutions
I evaluated a broad selection of EDR products using a product scoring rubric with six main categories. Each category was weighted based on importance and contained subcriteria with their own weighting, which all factored into the product’s overall score out of five. The eight highest-scoring products made our list, and the scores helped us determine the products’ use cases.
Evaluation Criteria
My most important criteria included major EDR features, like threat intelligence and remediation suggestions, and administration, which looked at features like security policies and APIs. Then I considered customer support, including channels like phone and email, and pricing, which evaluated vendors’ transparency and free trials. I also looked at usability, including documentation and MITRE scores, which evaluate practical detection and protection abilities.
- Core features (25%): I scored products based on the availability of core EDR capabilities like behavioral analytics, device controls, and remediation recommendations.
- Criterion winner: Palo Alto Networks Cortex XDR
- Administration (20%): I considered options to create security policies, set role-based access controls, and useful tools like APIs and dashboards.
- Criterion winner: FortiEDR
- Pricing (15%): I evaluated vendors’ pricing availability, free trials, and information provided about licensing or plan length.
- Criterion winner: ESET Protect
- Customer support (15%): I looked at the availability of support channels like phone and chat. I also reviewed the duration of vendor assistance with implementation, review scores, and demo availability.
- Criterion winner: ESET Protect
- Usability (15%): I measured products based on documentation, training videos, and the option to use managed services.
- Criterion winner: Multiple winners
- MITRE scores (10%): The MITRE ATT&CK corporation performs stringent evaluations that test vendors’ detection and protection abilities. I scored products based on their MITRE detection and protection scores. scores, and demo availability.
- Criterion winner: Multiple winners
Frequently Asked Questions (FAQs)
Why Do I Need an EDR Solution?
Endpoint detection and response products help IT and security teams manage hundreds to thousands of devices they would be unable to secure otherwise. Because threats have developed such sophisticated tactics, you’ll need to be able to respond as quickly as possible to advanced threats. EDR solutions automate much of that response, which could otherwise overwhelm you and your teammates over time.
How Long Do EDR Products Retain Data?
Vendors will have different data retention and storage systems, but 30-60 days is a common time frame for storing threat data. Vendors offer more or fewer; for example, CrowdStrike Falcon Insight stores data for up to 90 days. Some vendors store certain types of data for 180 days.
What’s the Difference Between EDR & XDR?
EDR mainly focuses on endpoints like devices and users. Extended detection and response (XDR) is broader, covering networks, cloud applications, and other technologies. XDR is designed to protect the entire tech ecosystem, but whether individual products accomplish this goal is an industry question. Your enterprise should look for solutions that have strong detection and response capabilities — look at user reviews and independent testing results.
What’s the Difference Between Antivirus, Endpoint Protection Platforms, & EDR?
Antivirus products find and eradicate malware and viruses from computer systems, but many are limited in scope. While endpoint protection platforms serve a similar purpose to EDR, they mainly identify vulnerabilities and protect systems from threats. EDR platforms respond more actively and hunt threats, giving businesses more comprehensive protection. Read more about the differences between antivirus, EPP, and EDR to choose one of the three best.
Bottom Line: EDR Solutions Help Protect Your Devices & Systems
EDR is a foundational enterprise cybersecurity technology as important as firewalls and SIEM. Choosing the EDR system that best meets your organization’s needs and budget is important. These tools are useful for many organizations but especially critical for enterprises with many endpoint devices, including but not limited to servers, desktops, and laptops.
Don’t rely on your EDR to fix everything for you immediately. Learning, implementing, and tuning any endpoint platform takes time, but the long-term benefits are worthwhile, including the experience security staff will gain from using any EDR software. As your IT and security teams learn to recognize behavioral and threat patterns, your enterprise will be more prepared to secure your endpoints and broader infrastructure.
Considering a broader range of security solutions? Read more about the best cybersecurity software for businesses, including cloud access security brokers and next-generation firewalls.
Paul Shread contributed to this article.