Security information and event management (SIEM) is a critical enterprise technology that pulls data from IT and cybersecurity systems to assess threats and manage risks. SIEM facilitates real-time monitoring, compliance adherence, and identification of anomalous activities. To help you choose the best SIEM tool tailored for your needs, we’ve evaluated the leading SIEM solutions in the marketplace, their best features, and limitations.
Here are the six best SIEM tools and software to consider:
- Splunk Enterprise Security: Best for IT observability
- IBM Security QRadar SIEM: Best overall SIEM tool
- Securonix Unified Defense: Best SOAR integration
- Exabeam Fusion: Best option for UEBA capabilities
- LogRhythm SIEM Platform: Best on-premise SIEM
- Rapid7 InsightIDR: Best intruder trapping technology
Featured PartnersFeatured Partners: Security Information and Event Management (SIEM) Tools
eSecurity Planet may receive a commission from merchants for referrals from this website
Comparing the Top SIEM Software & Tools
Examine the pricing structures, distinct features, and capabilities of each tool below:
| MITRE ATT&CK Mapping & Support | Advanced Analytics Features | Starting Price | Free Trial | |
|---|---|---|---|---|
| Splunk Enterprise Security | Yes | Yes | Legacy ingest: $150+/month | Available for 60 days via Splunk Enterprise |
| IBM Security QRadar | Limited | Yes | QRadar Community Edition: Free Software: $320+/month SaaS: $2,340+/month | Available through certain MSSPs |
| Securonix Unified Defense SIEM | Limited | Yes | Contact for pricing info | Available for SaaS offering |
| Exabeam Fusion | Yes | Yes | Contact for pricing info | Available for SaaS cloud offering |
| LogRhythm SIEM Platform | Limited | No | Contact for pricing info | No |
| Rapid7 InsightIDR | Yes | Yes | InsightIDR Essential: $3.82+/asset/month InsightIDR Advanced: $6.36+/asset/month InsightIDR Ultimate: $8.21+/asset/month | Available for 30 days |
Note: All prices are commitment-free and usage-based unless otherwise noted.

Splunk Enterprise Security
Best for IT Observability
Overall Rating: 4.2/5
- Core Features: 4.7/5
- Cost: 3.7/5
- Advanced Features: 4.5/5
- Ease of Use & Setup: 3.9/5
- Customer Support: 4.3/5
Splunk Enterprise Security is an analytics-first solution that’s scalable to on-premises or multi-cloud environments and has powerful threat detection capabilities. Notably, it provides powerful SIEM capabilities while demonstrating scalability via a platform that hosts over 2,800 apps and seamlessly connects data and workflows. Splunk, known for its IT observability, is one of the best options for comprehensive insights into IT landscapes.
Splunk ES is a scalable solution, but the pricing model is more complex than others. For a more transparent and accessible pricing structure, try IBM Security QRadar SIEM.
Pricing
- Vendor price: Contact Splunk
- Marketplace price: $150+ per month per 1 GB data
- Free trial: Available for 60 days via Splunk Enterprise
| Pros | Cons |
|---|---|
| ✔️ Comprehensive SIEM and security approach | ❌ Resource challenges for smaller teams |
| ✔️ Flexible infrastructure and deployment | ❌ Complex and potentially expensive pricing |
| ✔️ Wide device integration | ❌ Limited presence outside North American market |
Key Features
- Risk classification: Categorizes risks based on user and system compliance with various security frameworks, following established standards.
- Scalable ingestion: Scalability is available for both structured and unstructured data ingestion, leading to efficient processing of a wide range of data kinds and quantities.
- Built-in threat intelligence: Incorporates a threat intelligence management tool, which improves its ability to analyze and respond to developing cyberthreats effectively.
- Versatile deployment: Deployable across cloud, IaaS, software, hardware appliances, or hybrid setups, providing flexibility for organizations with a wide range of needs.
- 700+ detections: Provides access to over 700 detections, in line with frameworks such as MITRE, NIST, Kill Chain, and CIS 20 for complete threat identification and mitigation.
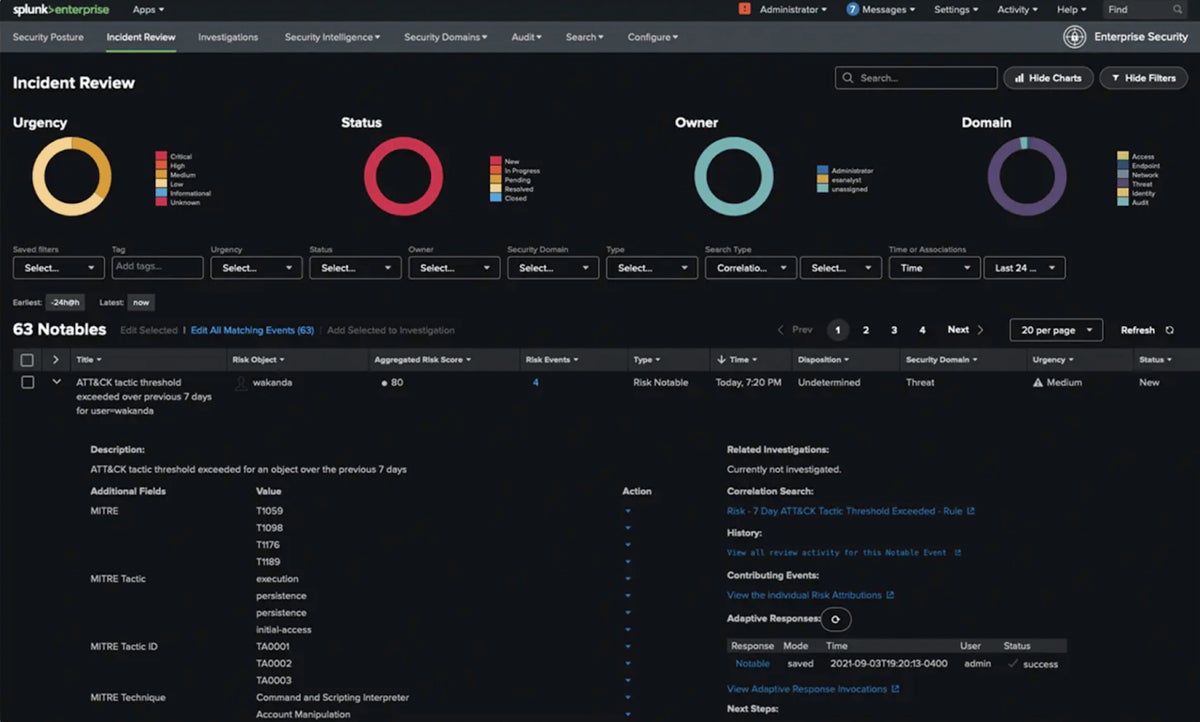

IBM Security QRadar SIEM
Best Overall SIEM Tool
Overall Rating: 4.3/5
- Core Features: 4.8/5
- Cost: 4.5/5
- Advanced Features: 4.1/5
- Ease of Use & Setup: 3.9/5
- Customer Support: 4.3/5
IBM Security QRadar SIEM is an enterprise favorite that’s adapted alongside the evolution of the SIEM market. IBM launched the IBM Security QRadar Suite to more effectively combine threat detection, investigation and response, SOAR, SIEM, EDR, and XDR in one platform service for hybrid cloud users. Its global presence offers localized support, regional regulatory expertise, and expansive channels, making it a reliable choice across regions around the world.
IBM consistently improves its security orchestration, automation, and response (SOAR) capabilities. However, deficiencies change based on upgrades and releases. If you’re looking for a tool with excellent SOAR integration capabilities, check out Securonix Unified Defense SIEM.
Pricing
- Free version: Available but limited via QRadar Community Edition
- IBM QRadar SIEM (Software): $320 to $26,540 per month
- IBM QRadar SIEM (SaaS): $2,340 to $25,922 per month
- Custom plans: Contact IBM for quote
- Free trial: Available through certain MSSPs
| Pros | Cons |
|---|---|
| ✔️ AI-driven with user behavior analytics and network flow insights | ❌ Challenging onboarding and implementation |
| ✔️ Extensive global security portfolio and expertise | ❌ Outdated, complex user interface |
| ✔️ Broad security ecosystem and seamless QRadar SIEM integration | ❌ Concerns about product support and platform developments |
Key Features
- Continuous monitoring: Maintains continuous surveillance across on-premises and cloud settings, providing full visibility along the kill chain.
- Threat intelligence: Powered by IBM’s Security X-Force and STIX/TAXII feeds, which provide comprehensive threat information to enhance security measures.
- Compliance resources: Offers comprehensive compliance support, including materials for HIPAA, SOX, ISO, PCI, NIST, GLBA, GDPR, and CCPA.
- Versatile deployment: Offers deployment options, including hardware appliances, software, SaaS, and virtual machines, catering to on-premises and IaaS environments.
- Integration access: Allows seamless integration with multiple security ecosystems by providing access to over 450 interfaces, APIs, and an SDK.

Read the full product review: IBM QRadar SIEM Product Overview

Securonix Unified Defense SIEM
Best SOAR Integration
Overall Rating: 3.6/5
- Core Features: 4.2/5
- Cost: 2/5
- Advanced Features: 3.7/5
- Ease of Use & Setup: 3.8/5
- Customer Support: 4.4/5
Securonix, recognized for its innovative approach, also stands out for its SOAR integration capabilities. Its Unified Defense SIEM integrates seamlessly with SIEM, threat detection, investigation, and response. The Autonomous Threat Sweeper for threat detection capitalizes on the Snowflake Data Cloud for improved data searchability. Its Threat Coverage Analyzer assesses security gaps aligned with industry standards such as MITRE ATT&CK and US-CERT.
Securonix Unified Defense’s combined SIEM-SOAR-TDIR approach offers accelerated incident response, but it requires a steeper learning curve for setup, especially for new users. If you’re looking for easier installation and setup, see Rapid7 InsightIDR.
Pricing
- Vendor price: Contact Securonix Security Operations and Analytics Platform
- Marketplace price: $67,331+ per year for basic SIEM subscription
- Free trial: Available for SaaS offering
| Pros | Cons |
|---|---|
| ✔️ Integrated SOAR for accelerated incident response | ❌ Limited role-based access control (RBAC) |
| ✔️ Playbooks and workflow guide reduce response time | ❌ Steep platform learning curve |
| ✔️ Built-in threat intelligence at no additional cost | ❌ Basic SIEM subscription is more expensive than others |
Key Features
- Multi-environment ingestion: Has centralized ingestion for cloud, on-premises, and hybrid environments, with a uniform console to streamline data collection.
- Long-term search: Enables extended analysis by providing comprehensive historical data search capabilities for detecting and managing slow-burning threats.
- Cloud-native platform: Is designed for on-demand scaling, with a SaaS subscription model to provide flexibility and efficiency in cloud-based security operations.
- Extensive cloud connectors: Access to 350+ connectors and API-based interfaces enables broad data collection from different cloud sources.
- Use case content: With an investigative workbench, users can develop cases based on industry examples, which improves practical application and analysis.
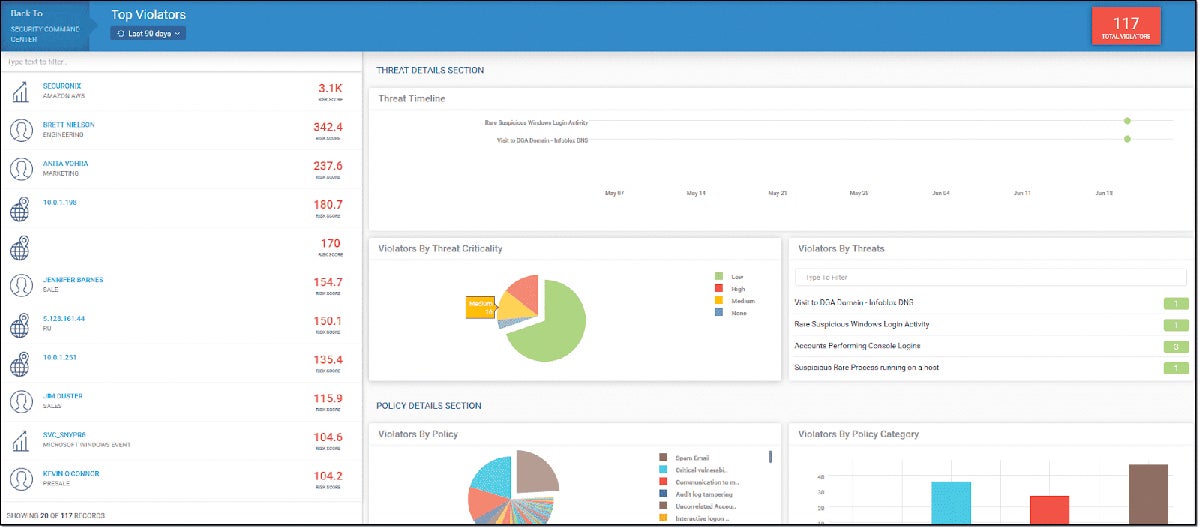

Exabeam Fusion
Best Option for UEBA Capabilities
Overall Rating: 3.9/5
- Core Features: 4.7/5
- Cost: 2/5
- Advanced Features: 4.5/5
- Ease of Use & Setup: 3.9/5
- Customer Support: 4.5/5
Exabeam Fusion is a threat detection, investigation, and response (TDIR) solution that brings together automated, next-generation SIEM capabilities. It provides user and entity behavior analytics (UEBA) through powerful machine learning, behavioral analytics, and contextual information. Fusion combines SIEM and XDR capabilities for a comprehensive approach to security incidents, including a suite of tools for advanced threat defense and integration.
While Exabeam Fusion offers a good cloud-native SIEM, LogRhythm SIEM is better suited for those seeking on-premise SIEM solutions.
Pricing
- Vendor price: Contact Exabeam’s sales team
- Free trial: Available for SaaS cloud offering
| Pros | Cons |
|---|---|
| ✔️ Simple interface and user-friendly experience | ❌ Limited transparency in pricing model |
| ✔️ Top-tier UEBA capabilities in the SIEM market | ❌ Third-party alerts delay in Fusion |
| ✔️ 10-year retention for searchable log storage | ❌ Limited built-in detection and response capabilities in Fusion |
Key Features
- UEBA for threats: Detects insider and zero-day threats using advanced analytics, improving the discovery and mitigation of potential security concerns.
- Full indexing: Ingests logs comprehensively. Enables advanced search capabilities for efficient data retrieval, analysis, and threat detection.
- Smart timelines: Gathers and presents evidence intelligently. Creates cohesive incident timelines that streamline investigation processes for effective incident response.
- Playbooks & dashboards: Provides access to hundreds of playbooks and dashboards, streamlining reporting with established templates for regulatory compliance.
- Integration options: Integrates with over 500 security and IT technologies in the TDIR space to create a coherent ecosystem for better threat detection and response.


LogRhythm SIEM Platform
Best On-Premise SIEM
Overall Rating: 3.8/5
- Core Features: 4.8/5
- Cost: 1.4/5
- Advanced Features: 4/5
- Ease of Use & Setup: 4.3/5
- Customer Support: 4.3/5
LogRhythm is a noteworthy on-premise SIEM solution, known for its log management, threat detection, and response capabilities. Its on-premise deployment secures data ownership and compliance, providing a scalable solution adapted to specific security requirements. Beyond SIEM, LogRhythm excels in SOAR, UEBA, and NDR, offering hardware, software, cloud, and hybrid formats for business scalability.
LogRhythm excels as an on-premise SIEM solution, but it has limitations in API key integration for LogRhythm apps. Splunk might be considered a more flexible option in this regard.
Read the full comparative review here: LogRhythm vs Splunk
Pricing
- Vendor price: Contact LogRhythm’s sales team
- Free trial: Not available
| Pros | Cons |
|---|---|
| ✔️ A longtime, established provider of on-premises SIEM | ❌ Challenges in adapting to the cloud and SaaS market |
| ✔️ A strong network of MSPs and reselling partners | ❌ Limited API key integration for LogRhythm apps |
| ✔️ User-friendly product interface and administration features | ❌ Infrequent product updates; vendor committed to quarterly releases |
Key Features
- Advanced analytics: Detects malicious activities by evaluating patterns in compliance and security contexts, which improves proactive threat detection.
- Prebuilt playbooks: Include alert triage, threat context, and case categorization to streamline incident response through preset, efficient workflows.
- Accelerated detection: The automated workflows optimize threat detection and response, ensuring rapid remediation for effective incident resolution.
- Threat intelligence: LogRhythm Labs offers useful insights, giving access to current and comprehensive threat intelligence for proactive defense.
- Access to data: Provides wide access to over 950 third-party data sources as well as 1,100 pre-configured correlation rule sets for richer and efficient threat analysis.
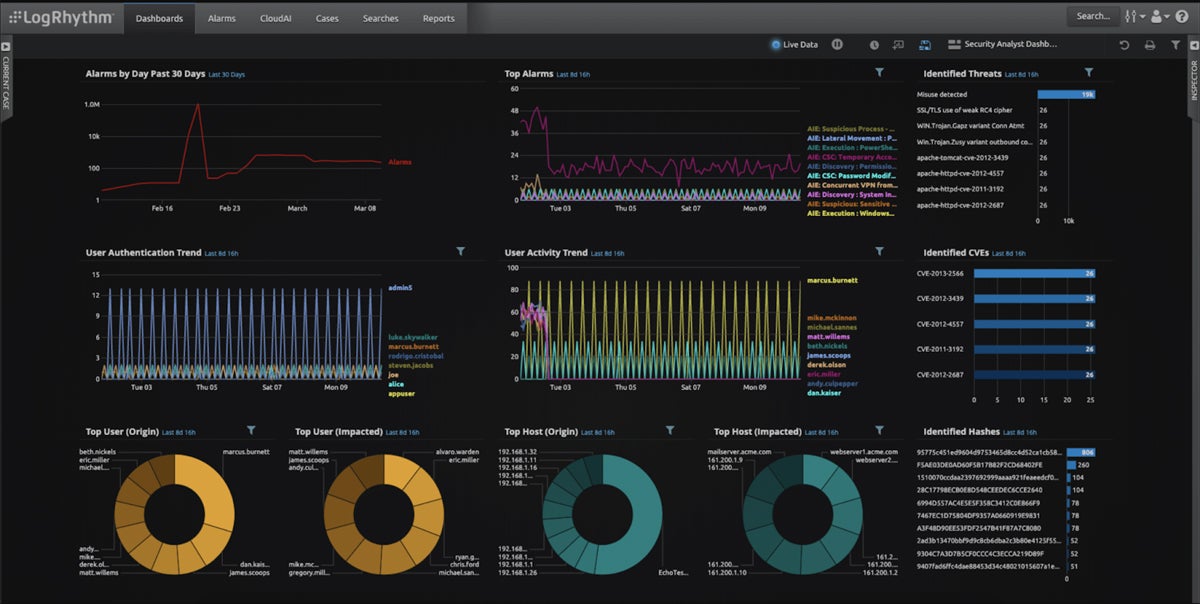

Rapid7 InsightIDR
Best Intruder Trapping Technology
Overall Rating: 3.6/5
- Core Features: 4.5/5
- Cost: 3.5/5
- Advanced Features: 2.4/5
- Ease of Use & Setup: 3.9/5
- Customer Support: 3.9/5
Rapid7 offers a comprehensive SIEM platform with its flagship SIEM-XDR hybrid solution, InsightIDR. It solves the issues of over-indexing on endpoints or using only a restricted number of event sources. Its deception suite, which includes honeypots, honey users, credentials, and files, improves threat detection throughout the attack chain. These traps use continuous attacker research to provide real-time, file-level visibility for effective security against breaches.
While Rapid7 InsightIDR has a good 13 months data retention, Exabeam’s log storage extends searchable log retention to 10 years.
Read the full review: Rapid7 InsightIDR Testing & Review
Pricing
- InsightIDR Essential: $3.82+ per asset per month
- InsightIDR Advanced: $6.36+ per asset per month
- InsightIDR Ultimate: $8.21+ per asset per month
- Custom plans: Contact Rapid7 for quote
- Free trial: Available for 30 days
| Pros | Cons |
|---|---|
| ✔️ Relatively easy to install | ❌ Limited automation |
| ✔️ 13 months of searchable data retention by default | ❌ High false positives |
| ✔️ Has pre-built compliance content | ❌ Bandwidth-heavy system scans |
Key Features
- Network traffic analysis: The curated intrusion detection system (IDS) focuses on actual threats. You can view extra network metadata to gauge the extent of activity.
- UEBA: Automatically correlates network activities to specific individuals and entities.
- Embedded threat intelligence: Detection library combines machine learning, enhanced attack surface mapping, and threat intelligence from the open-source community.
- MITRE ATT&CK alignment: Uses MITRE framework to map attacker and UEBA detections. Reveals tactics, methods, and procedures most used by threat actors.
- Deception technology: Provides four types of intruder traps and injects bogus honey credentials into your endpoints to deceive hackers.
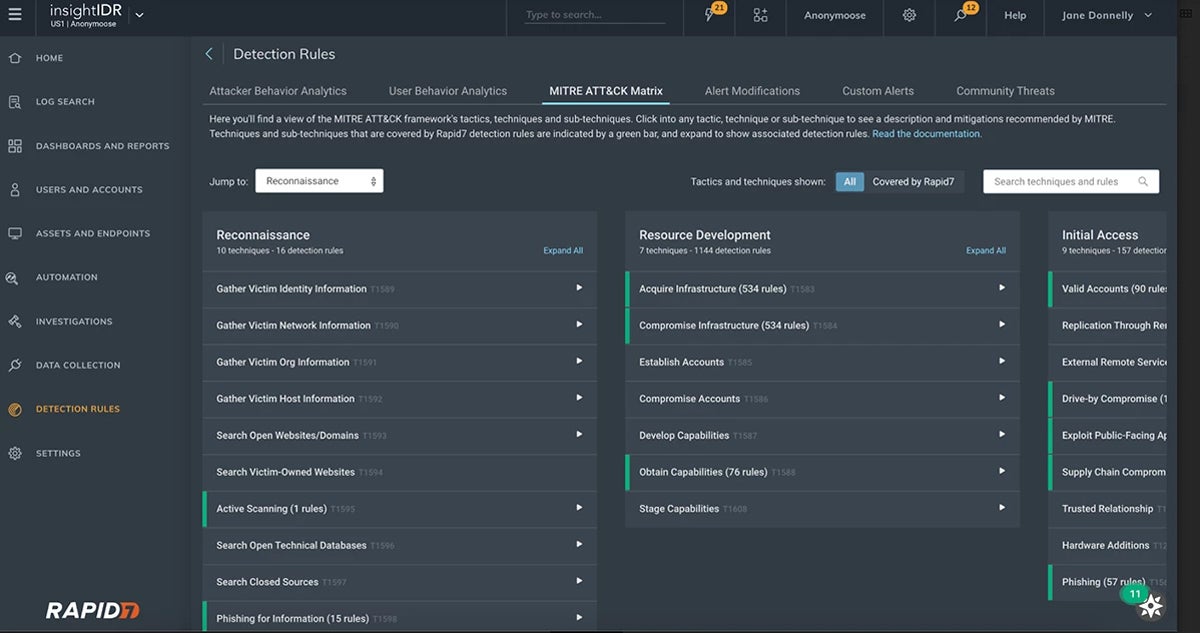
Top 7 Features of SIEM Tools
SIEM tools often incorporate the best factors of other network security tools, such as advanced threat detection, endpoint/extended detection response (EDR/XDR) integration, MITRE ATT&CK mapping and support, and UEBA, to thoroughly detect vulnerabilities and threats.
When selecting a SIEM tool, consider the following top features and capabilities:
- Advanced threat detection: Uses advanced algorithms and analysis techniques to detect and neutralize complex and developing cyberthreats.
- EDR/XDR integration: Integrates capabilities for real-time monitoring, detection, and response to security issues on endpoints or across multiple environments.
- Flexible infrastructure and deployability: Supports deployment flexibility across several environments, allowing enterprises to select on-premises, cloud, hybrid, or virtual configurations based on their individual needs and preferences.
- Integration with threat intelligence platforms: Combines enterprise resource planning (ERP), big data, identity and access management (IAM), and threat intelligence platforms to improve overall security intelligence and context.
- MITRE ATT&CK mapping and support: Aligns with the MITRE ATT&CK framework by providing a standardized mapping of adversary tactics, techniques, and procedures, facilitating threat intelligence analysis and improving detection capabilities.
- Unified management, asset discovery, and compliance reporting: Provides a consolidated platform for streamlining security processes and ensuring regulatory compliance.
- User and entity behavior analytics (UEBA): Tracks and analyzes patterns of user and entity activity to detect abnormalities to help identify potential insider threats or illegal access based on deviations from normal behavior.
How We Evaluated the Best SIEM Tools
We took a systematic approach to analyzing the top SIEM tools and software. We classified our assessments into five categories: core features, cost, advanced features, ease of use and setup, and customer support – each with subcriteria. In order to provide a fair assessment, we assigned category ratings ranging from one to five for each specific subcriterion on our list.
Core Features – 25%
These are the main security posture capabilities of SIEM like threat hunting, efficient digital forensics, and effective incident response, unified management, compliance reporting, EDR/XDR integration, advanced threat detection, UEBA, and comprehensive integrity monitoring.
- Criterion Winner: Multiple winners
Cost – 20%
Cost examines factors such as the availability of free trials, transparent and accessible pricing structures, scalability-oriented cost per workstation or server, and plan flexibility.
- Criterion Winner: IBM Security QRadar SIEM
Advanced Features – 20%
We considered additional but valuable capabilities such as vulnerability monitoring, SOAR integration, out-of-the-box content availability, and seamless integration with diverse platforms.
- Criterion Winner: Multiple winners
Ease of Use & Setup – 20%
Here, we evaluated high automation, accessible knowledge resources, minimal technical setup requirements, dashboard intuitiveness, and user experience on platforms like G2, Capterra, and TrustRadius.
- Criterion Winner: LogRhythm SIEM Platform
Customer Support – 15%
Reflecting the accessibility and effectiveness of customer service channels, we assessed live chat accessibility, email responsiveness, and the quality of documentation, demos, and training materials. It also reflects the user experience on platforms like G2 and Capterra.
- Criterion Winner: Exabeam Fusion
Bottom Line: Choose SIEM Tools for Advanced Security
To get an idea of how vital a SIEM platform is to enterprise security, consider the scale of security incidents and the data involved. A large enterprise may generate more than 25,000 events per second (EPS) and require 50 TB or more of data storage. SIEM’s efficient data filtering prioritizes critical security issues, enhancing manageability. Choose the right tool to secure your digital operations and leverage free trials or demos for a test run before committing.
SIEM systems often rely on data from various security mechanisms, so knowing the common network security protections could help you interpret and prioritize these events more effectively.




