Every organization needs visibility into the potential threats they face daily. Enterprise risk management software can provide risk monitoring, identification, analysis, assessment, and mitigation, all in one solution.
While a number of solutions focus on the operational and financial risks posed to enterprises, this article focuses on software vendors specializing in cybersecurity risk management. Here are the top picks for risk management software vendors and solutions, followed by what every buyer needs to know and consider before purchasing.
Featured ERM Software
Alyne
Leading enterprise risk management tool powered by AI technology so your team never misses a red flag. From third-party risk management to ESG and information governance, Alyne helps CISOs and risk professionals understand and assess risk, implement compliance requirements, leverage and report on analytics for more risk-aware decisions, and drive 24/7, agile defense against threats. covering regulations: ISO 27001, SOC 2, SS1/22 & SS2/22, COBIT, NIST, CCAR, sr 11-7, DFAST, SOX, TRIM & More
StandardFusion
Simplify Enterprise Risk Management with StandardFusion’s unified platform, integrating risk, compliance, vendor, privacy, policy, and audit management. Overcome complexity with scalable and customizable workflows, tailored for your needs while ensuring compliance amid evolving regulatory challenges including AI and privacy laws. Automate GRC tasks, protect data, and drive collaboration across departments for a seamless, future-proof strategy.
What is Risk Management?
Risk management is the process of identifying threats, monitoring their exploitability status, conducting internal audits, and managing risks to mitigate harm to a company or organization.
Before the IT revolution, brick-and-mortar stores and enterprise offices protected physical assets from threat actors using security guards, alarms, and CCTV. Behind closed doors, a lock safeguarded cash, patents, and more.
Today sensitive user data and proprietary technologies are accessible to hackers without physical access, meaning RM needs to evolve to meet advancing threats of IT environments. With the broad workforce adoption of IT tools, risk assessment and mitigation are more crucial than ever.
Read more: Top Governance, Risk, and Compliance (GRC) Tools & Software
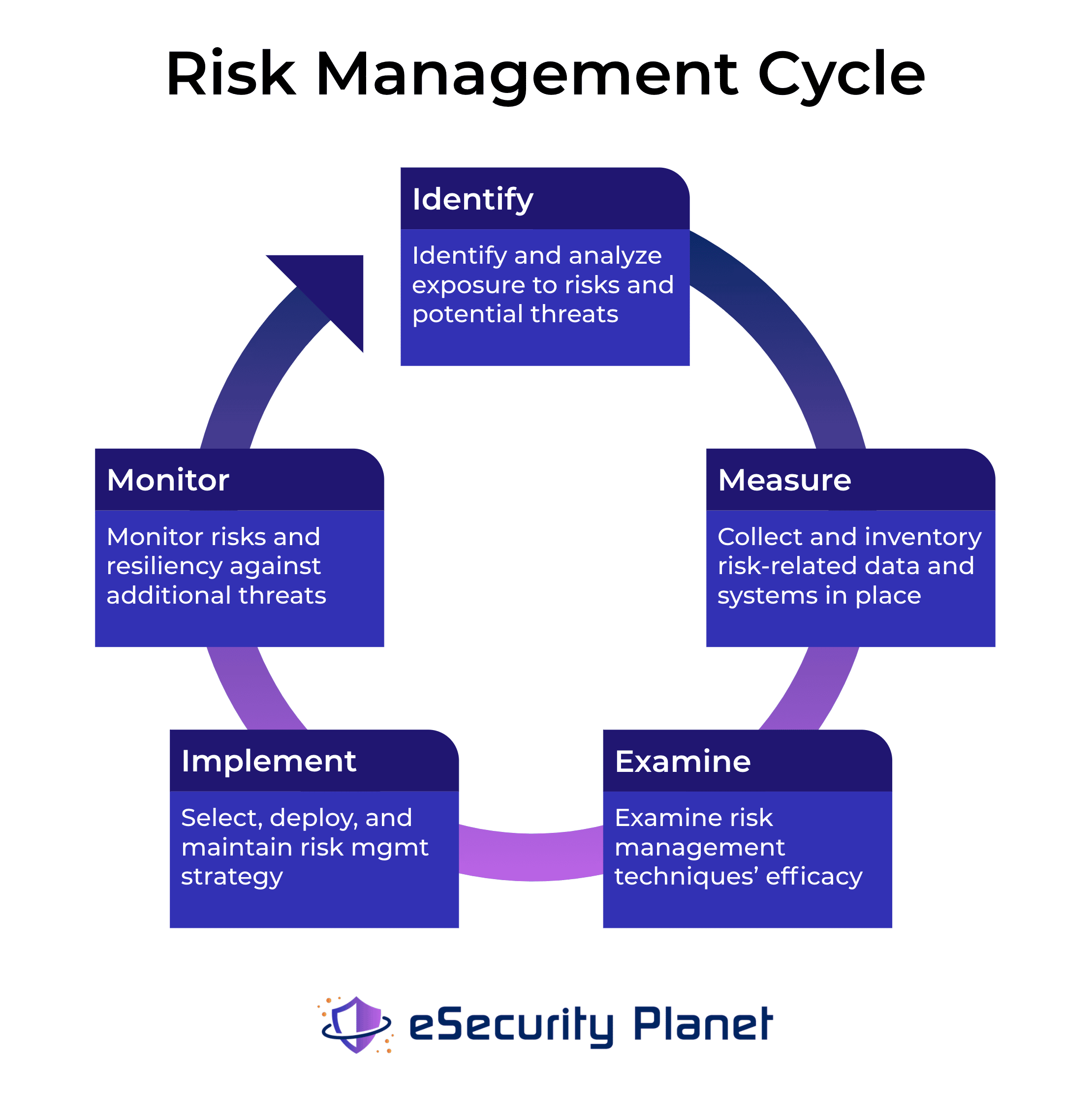
What is Enterprise Risk Management?
Enterprise risk management (ERM) is the methodology for managing risk for organizations with thousands of employees, global networks, and an increasingly complex IT environment. While traditional risk management frameworks empower division managers with risk strategy, ERM is the macro-view and RM process for an organization’s collective risk posture.
Organizations scaling would be wise to hire a chief risk officer (CRO) and accompanying staff to establish an ERM strategy. As a centralized risk owner, a CRO has the cross-environment visibility and influence to preserve business continuity. To meet this demand, vendors also offer ERM software for larger organizations that require a robust and granular risk management process.
Also read: IoT Devices a Huge Risk to Enterprises
Considerations for Risk Management Software
- What risks does this software seek to address, and how?
- Does the solution integrate with existing infrastructure and systems?
- How long does implementation take, and in what form (installed or hosted)?
- What access to support and resources do clients have?
- How does this risk management software compare to alternatives?
- Is the vendor addressing current RM challenges?
Types of IT Risk Management
Information security’s objectives — confidentiality, integrity, and availability — offer an idea of the types of threats that endanger IT environments.
Organizations must keep some extent of client or proprietary data confidential, ensure that data is reliable and available to respective users like staff and clients. Most IT risk falls under one of these objectives, if not some overlap considering the increasingly interconnected and complex nature of managing risk across the enterprise.
Examples of Common Risks
| IT Threat Type | Relates to | Examples |
| Physical | Access to physical systems | Natural disaster, fire, shoulder surfing |
| Technical | System failure | Software bug, crash, loss of data |
| Digital | System compromise | Phishing, malware, ransomware |
| Human Error | Staff of user access | Accidental misconfiguration |
| 3rd Party | External parties | Suppliers, partners, and stakeholders |
Enterprises Today Rely on IT Risk Management
Though the above IT threats directly impact today’s digital infrastructure, failing to manage these risks can have extensive consequences for companies and organizations.
For organizations working with personally identifiable information (PII), obligated to regulatory compliance, a breach can compromise protected user or patient information. On top of remediating the incident, the breach could mean legal liability, financial issues, and uncertainty. Excessive downtime has no legal ramifications, but staff, users, and clients relying on high availability quickly move on if the service isn’t functioning correctly.
To avoid these threats to business continuity, IT risk management planning and tools are necessary for today’s enterprise organizations.
Also read: Top Vulnerability Management Tools
Benefits of Risk Management Software
Maintaining an efficient security infrastructure requires the ability to act fast to stop attackers in their tracks. The benefit of risk management software includes quickly identifying threats, assessing how dangerous they are, and improving risk mitigation efforts.
The ability to prioritize what risks take priority first ensures the proper allocation of resources. Organizations, in turn, can avoid the financial and operational risks presented by breaches or downtime altogether. With the rapid pace of IT adoption and the economy’s reliance on its continued functionality, managing these risks becomes more costly by the day, considering legal and compliance consequences.
Risk Management Software Features
- Risk Identification: Scans networks and identifies risks and vulnerabilities as they arise
- Alert System: Identifies and alerts specific team members of potential threats
- Risk Assessment: Analysis of risks and vulnerabilities to determine how severe the threat is and what resources it would affect
- Risk Prioritization: Prioritize what risks will cause the most damage and alert operators to the appropriate task
- Centralized Dashboard: All logs of threats and vulnerabilities visible in a single dashboard with automatic patching and mitigation capabilities
- Reporting and Audits: Generate reports on risks and save historical data on past incidents to help inform future responses
- Regulatory Compliance: Risk management software should help maintain GRC and internal standards
Read more: Cloud Bucket Vulnerability Management
How to Choose a Risk Management Solution
Organization Needs
First, you should identify your essential requirements. Some risk management software targets specific types of risk. For example, some tools specialize in project risk management, whereas others specialize in financial risk management. Several top risk management software products offer specific protection for compliance-related risks like GDPR, GLBA, and HIPAA.
Similarly, an SMB organization serving a specific region won’t require the exact extent of enterprise-level features that a global network of offices needs.
Integration with Existing Systems
The next factor to consider is how a solution will fit with your current technology stack. You should ensure that the products you are considering can integrate with other security solutions you already have in place, including:
- Security incident event manager (SIEM)
- Next-generation firewalls (NGFW)
- User and entity behavior analytics (UEBA)
- Endpoint detection and response (EDR)
Choosing a program that doesn’t integrate with your current security architecture could lead to gaps in security or expensive overhauls of tools to match the risk management solution.
Budget and Contract
Finally, identify your budget and contract requirements. Advanced RM tools, such as those that use artificial intelligence (AI) or those built for enormous organizations, are often substantially more expensive than other options. If you don’t require these more advanced features, make sure you’re not paying more than what you need.
Also read: Best Patch Management Software
Analysis of the Top Risk Management Vendors
- Diligent and Galvanize
- LogicManager
- MetricStream
- NAVEX Global
- OneTrust
- OnSpring
- Reciprocity
- Resolver
- Riskonnect
- RSA Archer
- SAI360
- ServiceNow

Diligent and Galvanize
Diligent — combined with its acquisition of Galvanize for $1 billion in February 2021 — is an industry leader in IT risk management. Though Galvanize is the more popular platform, Diligent’s suite of solutions covers the gamut of risk management categories. Galvanize ThirdPartyBond recently made our Top Third-Party Risk Management solutions, but its stack of products also includes audit, compliance, risk, fraud, and internal control solutions.
For industry recognition in 2021, Diligent was a Leader in the Gartner Magic Quadrant for IT Risk Management and a Strong Performer in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, Diligent has an average score of 4.5 out of 5 stars with 328 reviews across four risk management solution categories.
- Standardized templates and workflows for audits across the hybrid IT environment
- Automated workflows for process owners managing the testing of controls and issues
- Maintain library of historical audits, risk and control matrices, and workflows
- Prioritize risks based on business impact severity and risk appetite
- One-click reports for quick visibility and sharing data with stakeholders

LogicManager
LogicManager is an enterprise risk management specialist with solutions for IT governance and cybersecurity, business continuity, incident management, internal audits, vendor risk, and more. The Boston-based vendor’s cybersecurity stack includes IT asset management, vulnerability management, and compliance-specific products for ISO, HIPAA, PCI, ORSA, GDPR, GLBA, BSA, and CCPA. LogicManager’s configurable reports and dashboards give clients the data needed to complete regulatory compliance documentation with ease.
For industry recognition in 2021, LogicManager was a Challenger in the Gartner Magic Quadrant for IT Risk Management and a Strong Performer in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, LogicManager has a score of 4.6 out of 5 stars with 111 reviews across three solution categories.
- Create a repository of routine risk mitigation activities, controls, and procedures
- Heat maps and risk matrices for administrator visibility into risks
- Robust taxonomy technology for connecting risks across controls, processes, and people
- Pre-built, configurable risk assessments with standardized criteria
- Access to libraries of industry-specific potential risks to inform cybersecurity

MetricStream
MetricStream is an undisputed industry leader for risk management solutions for integrated GRC, business performance and resilience, and cyber risk management. BusinessGRC covers operational risk, regulatory compliance, internal audits, and third-party risk for general enterprise needs. Alternatively, CyberGRC offers cyber risk quantification, threat and vulnerability management, and cyber policy administration. CyberGRC helps clients streamline cyber risk management by documenting and maintaining cyber risks, assets, controls, and processes.
For industry recognition in 2021, MetricStream was a Leader in the Gartner Magic Quadrant for IT Risk Management and a Strong Performer in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, MetricStream has a score of 4.6 out of 5 stars with 74 reviews across four risk management solution categories.
- Built-in dashboards offering risk heat maps and role-based insights
- Central repository for risks, threats, vulnerabilities, processes, and assets
- AI-powered issue management with root cause analysis and remediation
- Cyber risk quantification based on FAIR model for visualizing the financial impact of risks
- Assess IT risks and controls to meet security frameworks like ISO 27001 and NIST

NAVEX Global
NAVEX Global is an industry leader in GRC management solutions, offering an integrated platform for risk and compliance management in NAVEX One. This three-in-one platform includes the company’s swath of ethics and compliance (E&C), integrated risk management (IRM), and environmental, social, and governance (ESG) solutions. NAVEX IRM has third-party risk, business continuity, health and safety, and operational risk functionality. NAVEX Global can also help clients build and automate sustainable information security management systems.
For industry recognition in 2021, NAVEX Global was a Leader in the Gartner Magic Quadrant for IT Risk Management and a Contender in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, NAVEX Global has a score of 4.7 out of 5 stars with 101 reviews across four risk management solution categories.
NAVEX Global Features
- Real-time, centralized console for viewing and understanding environmental risk data
- Prioritize remediation actions based on severity and other risk indicators
- Assess the flow of specific data and the impact of data breaches or leaks
- Continuous monitoring that launches investigations and updates asset libraries
- Access to professional services for a custom solution, processes, and workflow planning
Read more: How to Use MITRE ATT&CK to Understand Attack Behavior

OneTrust
OneTrust is the youngest vendor to make our list and specializes in privacy, security, and data governance. Already boasting 75% of the Fortune 100 as clients, OneTrust has seen rapid growth since its launch in 2016. The company’s product portfolio includes discovery, vendor risk, GRC, ethics, and ESG, backed by 200 patents and OneTrust’s Athena AI and robotic automation capabilities. OneTrust’s range of risk management tools includes helping clients comply with industry standards frameworks like ISO, NIST, SOC 2, and hundreds more.
For industry recognition in 2021, OneTrust was a new addition to the Leader’s circle in the Gartner Magic Quadrant for IT Risk Management and a Leader in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, OneTrust has a score of 4.5 out of 5 stars with 207 reviews across three risk management solution categories.
OneTrust Features
- 500+ pre-built connectors for streamlining integration between applications
- Establish policies and reinforce best practices, test programs, and audit procedures
- No-code configuration management with drag-and-drop templates and workflows
- Identify, monitor, and respond to internal and external risks
- Access to OneTrust’s database of privacy and security compliance research

OnSpring
OnSpring’s business process management tools include GRC, ITSM, business operations, and regulatory framework solutions. The Kansas-based company’s GRC platform hits the gamut of risk management functionality with controls and policy management, internal audits, incident management, and business continuity. Clients building infrastructure around specific regulatory requirements can choose from OnSpring’s framework solutions for CMMC, GDPR, HIPAA, HITRUST, ISO, NERC, NIST, and PCI.
On Gartner Peer Insights, OnSpring for the moment holds a perfect 5 out of 5 with nine reviews in two risk management solution categories.
OnSpring Features
- Central risk register containing risks, controls, policies, and audit procedures
- Access control by role, group, and user for managing risk data
- Auto-assign risk data by severity and action steps for remediation
- Assess residual and inherent risks by heat maps or historical trends
- Execute risk assessments, control tests, policy updates, and audit projects

Reciprocity
Starting in 2009, Reciprocity is a GRC specialist known for its ZenGRC Platform covering solutions across compliance, audits, privacy, and third-party risk management. Reciprocity’s risk management platform includes critical features for privacy expectations, incident management, and disaster recovery to ensure business continuity. Reciprocity’s newest tool, Risk Intellect, pairs nicely with ZenGRC as it helps clients determine their risk posture and prioritize remediation actions with expert guidance.
Reciprocity was a Challenger in the Gartner Magic Quadrant for IT Risk Management and a Contender in the Forrester Wave on GRC Platforms for industry recognition. On Gartner Peer Insights, Reciprocity has 23 reviews in the IT Risk Management solution category.
Reciprocity Features
- Evaluate business, controls, systems, and connections risks with multivariable scoring
- Built-in risk registry with using industry frameworks (SOC 2, CCPA, GDPR, ISO, PCI)
- Reporting on vulnerabilities, the severity of risks, workflows, and benchmarking
- Continuous risk monitoring with automated alerts and playbooks for real-time action
- Access to planning services, professional risk officers, and GRC experts

Resolver
Resolver is an enterprise risk management vendor offering solutions for corporate security, risk and compliance, and information security teams. With 100 integrations to top applications, Resolver Information Security includes IT risk and compliance management to protect data against cyber-attacks and data breaches. Resolver offers granular reporting and visualizations to help administrators leverage configurable workflows. Organizations can seamlessly automate and duplicate compliance processes with a risk register and policy and document repositories.
Resolver was a Niche Player in the Gartner Magic Quadrant for IT Risk Management for industry recognition in 2021. On Gartner Peer Insights, Resolver has 35 reviews across three risk management solution categories.
- Data-driven recommendations to leverage existing risk processes and workflows
- No-code, drag-and-drop functionality for configuration management
- In-app trending of historical data and business intelligence connectors
- Flexible reporting engine and an easy-to-use interface for personnel adoption
- Identify, respond, and remediate threats or business disruptions
Also read: AI & ML Cybersecurity: The Latest Battleground for Attackers & Defenders

Riskonnect
Launched in 2007, Riskonnect is an integrated risk management leader with GRC solutions for project risk, internal audits, compliance, third-part, and enterprise risk management. Riskonnect also offers managed regulatory compliance services like automating priority regulatory functions or sorting out complex regulatory issues requiring expert assistance. Riskonnect is industry-certified (SOC 2 Type 2 and ISAE 3401) and protects data with encryption, audit logs, and firewalls across a globally secure data center network.
For industry recognition in 2021, Riskonnect was a Niche Player in the Gartner Magic Quadrant for IT Risk Management and a Contender in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, Riskonnect holds 17 reviews across two risk management solution categories.
- Consolidate risk data from multiple sources and analyze with actionable intelligence
- Aggregate all corporate policies, procedures, and requirements in a central location
- Manage complex audit procedures across risk frameworks
- Assess and mitigate insured and non-insured risks threats across the IT environment
- Integrate personnel, systems, and claims data with automated routine processes

RSA Archer
RSA’s Archer is perhaps the most recognized name in risk management, offering a robust stack that includes solutions for business resiliency, audits, third-party governance, compliance, and cybersecurity risk management. Archer IT & Security Risk Management has capabilities for issues and policies management, cyber risk quantification, controls assurance, incident and breach response, and vulnerability management. Archer can also help clients improve cybersecurity through CMMS practices and process management.
For industry recognition in 2021, RSA Archer was a Leader in the Gartner Magic Quadrant for IT Risk Management and a Challenger in the Forrester Wave on GRC Platforms and Business Continuity Management. On Gartner Peer Insights, RSA Archer has 293 reviews across four risk management solution categories.
- Continuously monitor and manage IT security risks with actionable threat intelligence
- Audit lifecycle management with quality control and planning for risk issues management
- Gain business context after a breach for prioritizing and escalating actions
- Controls assurance for documenting, evaluating, and reporting on enterprise controls
- Monitor and assess third-party relationships, vendor risks, and performance

SAI360
The recently rebranded SAI360 is an enterprise provider of cloud-based software specializing in sustainability, GRC, and environmental, health, and safety (EHS) solutions. For IT risk and cybersecurity, the SAI 360 platform include vulnerability and risk assessments, policy management, and pre-mapped frameworks and controls. With a central repository for vulnerability scanning tools, incidents, and data feeds, SAI360 can help clients automate IT risk management processes.
For industry recognition in 2021, SAI360 was a Leader in the Gartner Magic Quadrant for IT Risk Management and a Challenger in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, SAI360 has a score of 4.8 out of 5 stars with 82 reviews across three risk management solution categories.
- Flexible, centralized policy library for migrating policies and automating workflows
- Identify and analyze risks through globally recognized frameworks
- A risk register for monitoring and leveraging indicators for specific risks
- Customized and recurring report options with insights for leadership
- Continuous vulnerability and virus scanning and intrusion prevention

ServiceNow
ServiceNow Risk Management is a governance, risk, and compliance-centric software designed to identify real-time risks, alert stakeholders, and improve decision-making. ServiceNow’s enterprise provider of digital workflow and IT service management solutions offer an industry-leading risk management solution. ServiceNow’s solution has core administrative features for compliance policies, audits, third-parties, business continuity, and continuous monitoring.
For industry recognition in 2021, ServiceNow was a Leader in the Gartner Magic Quadrant for IT Risk Management and a Leader in the Forrester Wave on GRC Platforms. On Gartner Peer Insights, ServiceNow has 223 reviews across three risk management solution categories.
ServiceNow Features
- Move towards certified risk management framework and duplicate models
- Define ownership, risks, and controls in a risk repository for clear visibility
- Create standard taxonomy and risk register for business, compliance, and audit
- An automated risk assessment engine can support multiple risk frameworks
- Integration with ServiceNow’s extensive IT products and services

Workiva
Launched in 2008, Workiva is the cloud platform vendor offering solutions for accounting, audit, compliance, finance, and risk. The Iowa-based company’s enterprise resource planning capabilities for clients include internal audit management, Sarbanes-Oxley (SOX) compliance, and solutions for ESG, SEC, statutory, and management reporting. Workiva’s solutions include encryption at rest and in transit, SSO with SAML and 2FA, SCIM provisioning, and identity access management for cybersecurity functionality.
For industry recognition, Workiva was a Leader in the Forrester Wave on GRC Platforms for 2021. On Gartner Peer Insights, Workiva has a 4.4 out of 5 stars with 70 reviews in the IT Risk Management solution category.
Workiva Features
- Access and manage all policies, standards, and procedures in a central repository
- Map SOX compliance posture with real-time status updates for remediation
- Automated evidence gathering and engagement reports for audit management
- Customize certifications based on client requirements, calendar, and more
- Workiva Marketplace offers templates, connectors, and services for the implementation
The Future of Risk Management
As with most software, the future of risk management tools will include further advancements and machine learning and AI adoption. These new technologies help RM software better identify and prevent gaps in cybersecurity, identify signatures of known attacks, and predict more advanced threats through anomaly detection. As potential threats become more advanced, security solutions are sure to follow suit to manage tomorrow’s risks.
Updated by Sam Ingalls on February 16, 2022.








