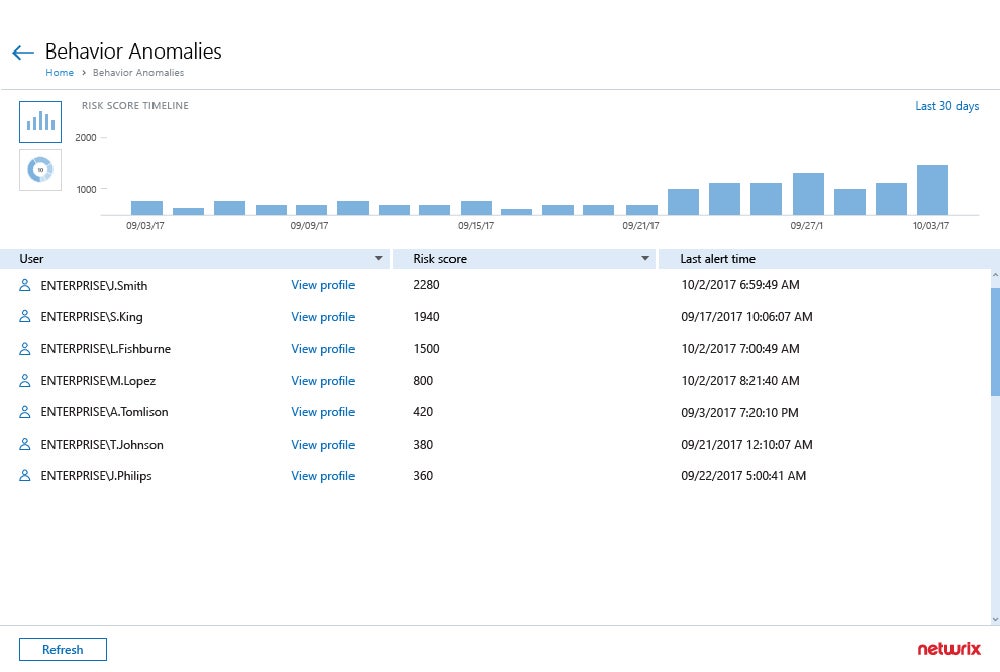
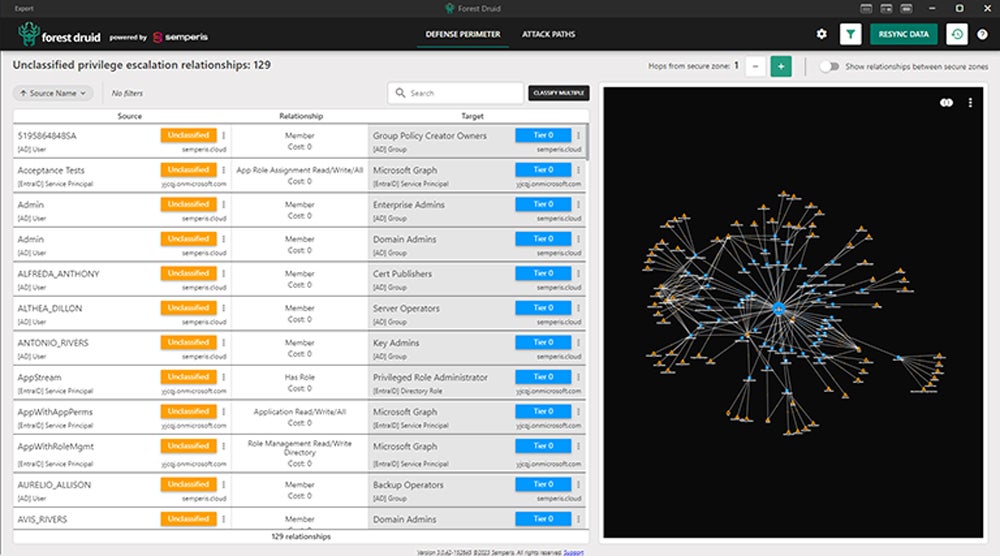
Active Directory security tools protect the critical Active Directory (AD) services that manage identities and access throughout a network. While many specialty AD tools exist, the best tools cover a breadth of capabilities to audit, monitor, harden, and secure AD. To help you select the right solution for your needs, I compared capabilities, ranked the tools, and identified strong use cases for each of the top-ranking solutions.
Here are the six best Active Directory security tools:
- Tenable Identity Exposure: Best overall Active Directory security tool
- Varonis Data Security Platform: Best for integrated data discovery
- CrowdStrike Falcon Identity Protection: Best for integrated EDR
- SolarWinds ARM: Best for integrated Active Directory operations
- Netwrix Auditor: Best for compliance reporting for data access
- Semperis Directory Services Protector: Best for free tool options
Table of Contents
Top Active Directory Security Tools Comparison
The following table provides a quick overview of the top six tools across four important AD security functions and pricing.
| Audit Accounts & Privileges | Attack Path Discovery | Real-Time Protection | AD Backup & Recovery | Pricing | |
|---|---|---|---|---|---|
| Tenable Identity Exposure | ✔️ | ✔️ | ✔️ | ❌ | Contact for quote |
| Varonis Data Security Platform | ✔️ | ✔️ | ✔️ | ❌ | Contact for quote |
| CrowdStrike Falcon Identity Protection | ✔️ | ✔️ | ✔️ | ❌ | $24.71+/ month/ endpoint for 1,000 licenses |
| SolarWinds ARM | ✔️ | ❌ | ❌ | ❌ | $2,083+ |
| Netwrix Auditor | ✔️ | ❌ | ✔️ | ✔️ | Contact for quote |
| Semperis Directory Services Protector | ✔️ | ✔️ | ✔️ | ✔️ | Contact for quote |
Although some Active Directory tools may score highly in one category or another, I found that Tenable Identity Exposure offers the best overall value. Learn more below how each solution fared in terms of pricing, features, and primary use cases, or jump down to see how I evaluated the products.
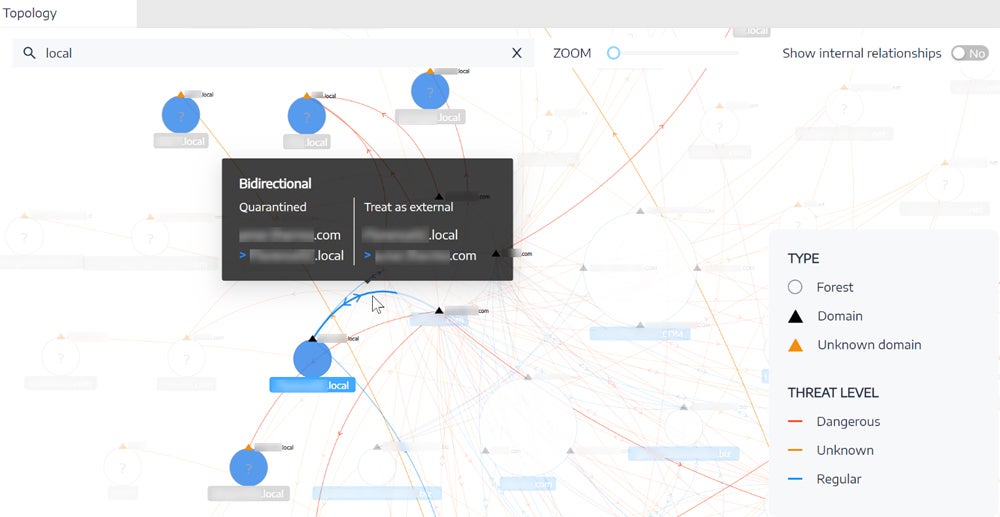
Tenable Identity Exposure – Best Overall AD Security Tool
Overall Rating: 4.4/5
- Audit and harden features: 4.8/5
- Monitoring, response, and recovery features: 4.6/5
- Ease of use: 4.5/5
- Price and value: 3.6/5
- Support availability: 3.4/5
Tenable Identity Exposure earns the highest score overall and the top score for audits and hardening features. The tool uses an intuitive GUI to clearly expose vulnerabilities, misconfigurations, attack paths, and groups policy object (GPO) issues through an interactive topology. The AD and Entra ID (formerly Azure AD) protection tool also tops ease of use with flexible software-as-a-service (SaaS), local, or even Tenable One platform deployment options.

Pros
Cons
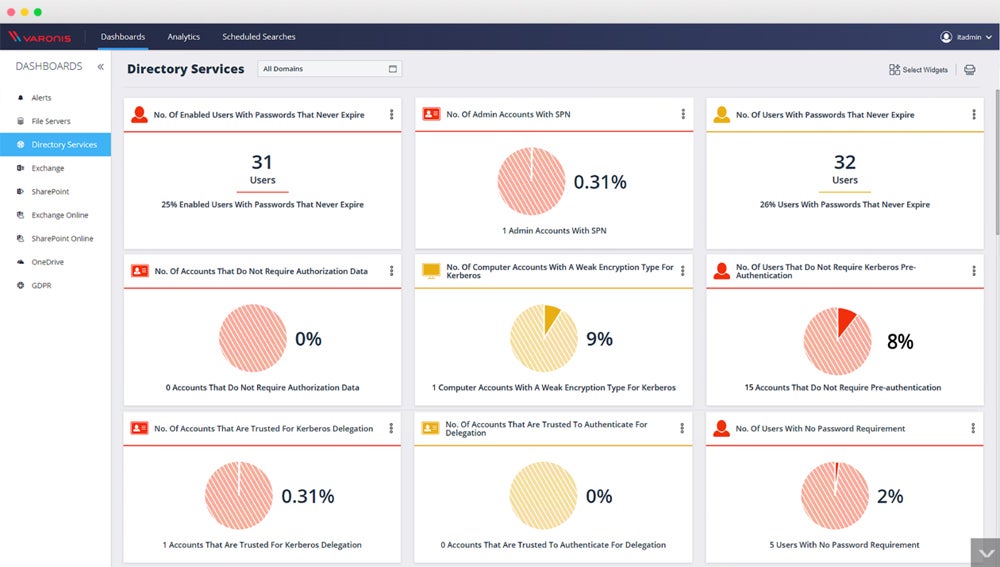
Varonis Data Security Platform – Best for Integrated Data Discovery
Overall Rating: 4.3/5
- Audit and harden features: 4.7/5
- Monitoring, response, and recovery features: 4.6/5
- Ease of use: 4.2/5
- Price and value: 3.5/5
- Support availability: 3.2/5
The cloud-native Varonis for Active Directory not only provides a full range of identity threat detection and response (ITDR) features; the platform also finds, classifies, and labels sensitive data to define the most critical assets to protect. In addition to protecting identity, Varonis integrates advanced user and entity behavior analytics (UEBA) capabilities and data protection capabilities to provide holistic user and data tracking, monitoring, and protection.

Pros
Cons
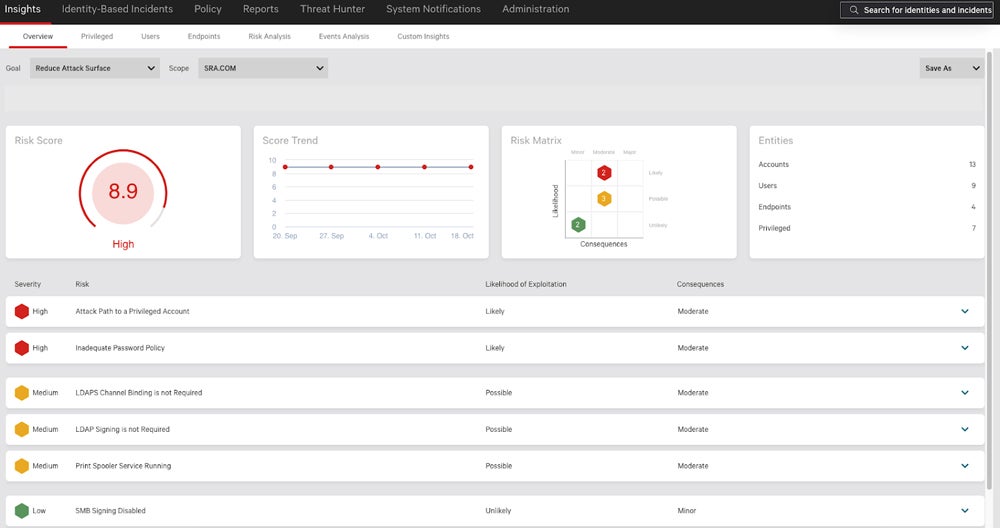
CrowdStrike Falcon Identity Protection – Best for Integrated EDR
Overall Rating: 4.1/5
- Audit and harden features: 4.7/5
- Monitoring, response, and recovery features: 4.5/5
- Ease of use: 3.4/5
- Price and value: 3.7/5
- Support availability: 2.9/5
The CrowdStrike Falcon Identity Protection provides good auditing and stellar AD threat detection and active protection. Some customers will purchase the tool separately, but many will opt to add Identity Protection through existing endpoint detection and response (EDR) or extended detection and response (XDR) agents. Once combined, Crowdstrike provides unified endpoint and ITDR protection.

Pros
Cons
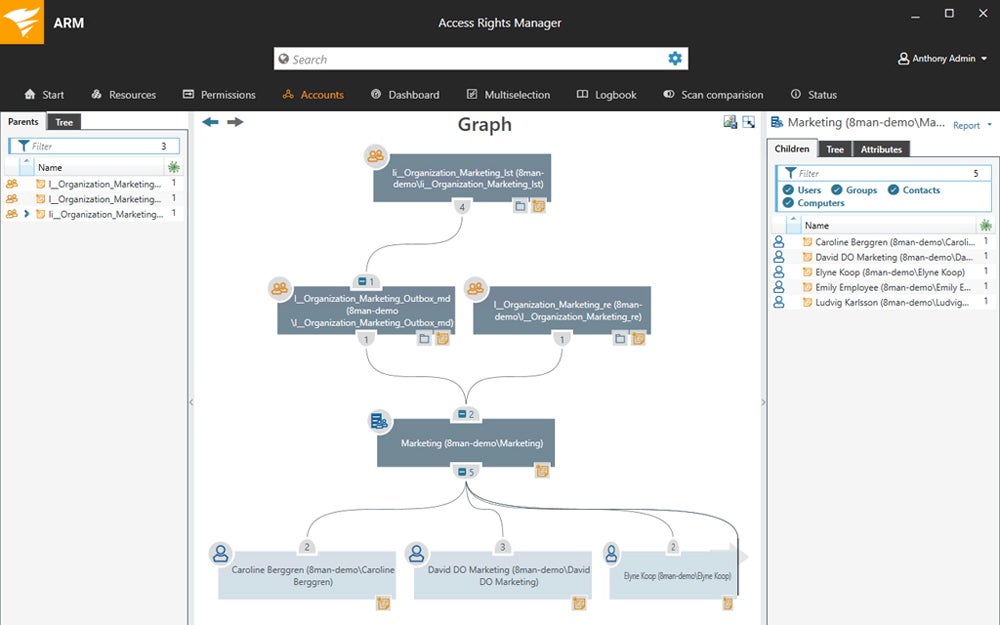
SolarWinds ARM – Best for Integrated AD Operations
Overall Rating: 4.1/5
- Audit and harden features: 4.6/5
- Monitoring, response, and recovery features: 3.9/5
- Ease of use: 3.8/5
- Price and value: 4.0/5
- Support availability: 3.6/5
SolarWind Access Rights Manager (ARM) combines Active Directory auditing and AD operations. This allows IT teams to save time by automating password reset and delegating rights management to group managers. The tool also scored highest for both support availability and price and licensing information, thanks to clear pricing, 24/7 phone support, onboarding support options, and robust self-help documentation.

Pros
Cons
Netwrix Auditor – Best for Compliance Reporting
Overall Rating: 4/5
- Audit and harden features: 4.7/5
- Monitoring, response, and recovery features: 5.0/5
- Ease of use: 3.2/5
- Price and value: 2.9/5
- Support availability: 2.5/5
Netwrix Auditor anchors the Netwrix suite of AD tools and provides the templated and customizable reports. Automated report options and on-demand customization will satisfy broad compliance requirements by documenting user access to regulated data in detail and as needed. These tools combine to earn the top score for monitoring, response and recovery features to provide strong overall security for AD as well.

Pros
Cons
Semperis Directory Services Protector – Best for Free Tool Options
Overall Rating: 4/5
- Audit and harden features: 4.8/5
- Monitoring, response, and recovery features: 4.9/5
- Ease of use: 3.5/5
- Price and value: 2.0/5
- Support availability: 3.4/5
Semperis Directory Services Protector (DSP) delivers the core of the Semperis Identity Resilience Platform complimented by two powerful free tools: Purple Knight and Forest Druid. Many teams start with Purple Knights user auditing or Forest Druid’s attack path mapping for initial security and then graduate to DSP or other Semperis modules as needs and sophistication grow. The light free software requires no integration and has low system requirements.

Pros
Cons
Top 5 Features of Active Directory Security
The top five features of Active Directory security harden, monitor, and enable quick reactions to attacks through examination of connections, integrating with existing security infrastructure, change monitoring, rapid alerts, and inspection of user and group permissions.
AD Forest Inspection
AD Forest inspection examines the connections between assets (data, devices, etc.), users (individuals, system functions, APIs, etc.), and groups (authorization categories). The examination focuses on Tier0 assets that can directly control the most secure levels of Active Directory and checks for excessive permissions and dangerous attack paths.
Alert & Log Integration
Security professionals require alerts and logs from AD security to integrate with existing SIEM, SOAR, and other network security tools. The sheer volume of information coming from security infrastructure will quickly overwhelm a team if they need to implement, learn, and monitor separate processes just for Active Directory.
AD Changes Auditing
AD security tools monitor and record details related to changes to active directory and permit change auditing to verify authenticity. All tools need to record changes, better tools enable roll-back of unauthorized changes, and the best tools can automatically detect and reverse unapproved changes.
Real-Time Alerts
Real-time alerts enable security teams to capture information on potential threats promptly and react quickly. In an environment of continuous attacks, security teams can no longer wait to check log files individually and require systems to identify, prioritize, and rapidly bring potential threats to the forefront.
User & Group Access Auditing
User and group access auditing inspects access rights for individuals and the user group classifications used to manage group permissions. AD provides manual functionality, but effective AD security tools enable users to quickly expose potentially dangerous issues such as excessive administrator rights, weak passwords, non-expiring passwords, and continuing access for terminated employees.
How I Evaluated the Best Active Directory Security Tools
The evaluation of the AD security tools weighed five different criteria, with the most emphasis placed on overall features. Each category contained a number of sub-criteria with their own weights that helped produce a five-point rating for each category and in total. After determining the top six tools based on their overall score, I considered the tools’ pros, cons, and features to identify strong use cases for each solution.
Evaluation Criteria
To evaluate the tools, I focused primarily on the breadth of features needed for active directory security. Next, I considered usability, support availability, and price and licensing information.
- Audit and harden features (30%): Assesses tool capabilities to check accounts for vulnerabilities, identify attack paths, harden security, and manage rights effectively.
- Criterion winner: Tenable Identity Exposure
- Monitoring, response, and recovery features (30%): Examines tool capabilities to monitor changes, issue alerts, aid investigations, and provide compliance reports.
- Criterion winner: Netwrix Auditor
- Ease of use (15%): Considers the number of installations, dashboards, and agents to provide AD security, other identities managed (Okta, 365, etc.), and installation options.
- Criterion winner: Tenable Identity Exposure
- Price and licensing info (15%): Bases evaluations on price and licensing information transparency, the number of licenses required, and free tools and trials available.
- Criterion winner: SolarWinds Access Rights Manager
- Support availability (10%): Considers the different support options for everyday use and initial installation, support hours, and premium support options.
- Criterion winner: SolarWinds Access Rights Manager
Frequently Asked Questions (FAQs)
How Are AD Security Tools Helpful?
AD security tools help manage Active Directory more intuitively, rapidly, and comprehensively to tighten control over the critical functions that AD delivers. They also analyze existing identities for potential issues, track changes for signs of malicious activity, and provide alerts for any detected attacks.
What Is the Difference Between AD Security & ITDR?
AD security secures the lightweight directory access protocol (LDAP) functions delivered by AD and similar tools. Identity threat detection and response (ITDR) expands the scope to include integration with MFA, SOAR, identity and access management (IAM), privilege access management (PAM), and other tools for a more comprehensive overview and integration into the security stack.
How Does AD Security Satisfy Compliance Requirements?
AD security adds controls to protect the access management required by all major cybersecurity compliance standards. AD security tool reports should directly provide information that proves user activity and data access fall within specific compliance requirements to avoid additional efforts to meet regular compliance requirements.
Bottom Line: AD Security Provides Fundamental Protection
Active directory stores access permissions and authorization throughout a network and literally defines who holds the keys to the kingdom. Make sure to implement effective AD security to provide this critical component with the protection and monitoring necessary to provide a foundation for the rest of an organization’s security stack. Start by selecting the most promising option and experience a demo or try out the free version.
This article explains how to secure AD against future attacks, but to determine if past attacks have been successful, read about how to tell if Active Directory is compromised.