There are 20,000 or more new software and hardware vulnerabilities every year. It falls to IT security teams to determine where those vulnerabilities lie in their organization and which ones they need to prioritize.
That process can be overwhelming. Vulnerability management tools can help, but even then, finding, patching and testing vulnerabilities can still take an extraordinary amount of time. That’s where more automated solutions can help — and one growing in popularity is vulnerability management-as-a-service (VMaaS).
Jump ahead to:
- What is Vulnerability Management as a Service?
- Top 8 Vulnerability Management as a Service Providers
- What are the Main Steps Involved in VMaaS?
- Benefits of Using VMaaS
- Disadvantages of Using Vulnerability Management Services
- Vulnerability Management as a Service Costs
- Choosing a Vulnerability Management Service
What is Vulnerability Management as a Service?
Vulnerability management is so much more than being able to run vulnerability scans against an environment. It includes patch management and IT asset management (ITAM), and increasingly it also incorporates automation and remediation. The goal of vulnerability management is to be able to rapidly address vulnerabilities in the environment through remediation, mitigation, or removal.
VMaaS is a way to deliver these services via the cloud rather than downloading and running on-premises software. VMaaS is a continuous process of identifying, assessing, reporting on, and managing vulnerabilities across on-premises and cloud identities, workloads, platform configurations, and infrastructure.
Some VMaaS vendors will deliver prioritized remediation plans for security teams to address. Others may automate the fixes too. And some operate in a more hands-on and involved way, similar to a managed security service provider (MSSP), some of which also offer vulnerability management services. The level of assistance and control required is up to the buyer.
Also read: Is the Answer to Vulnerabilities Patch Management as a Service?
Top 8 Vulnerability Management as a Service Providers
These are the VMaaS vendors that stood out in our analysis of a number of use cases. Some are delivered over the cloud rather than on-premises. Some do the scanning, scheduling, and prioritization but leave remediation to local IT resources. Others take care of everything. The right service for you is the one that best meets your needs within your budget, of course.
Ivanti VMaaS: Best for Automation

Ivanti Neurons for RBVM (risk-based vulnerability management) can ingest data from multiple third-party scanners to help close security gaps and blind spots. These tools autonomously analyze data from vulnerability scanners and provide insight to IT and security teams so they don’t have to sift through that data manually.
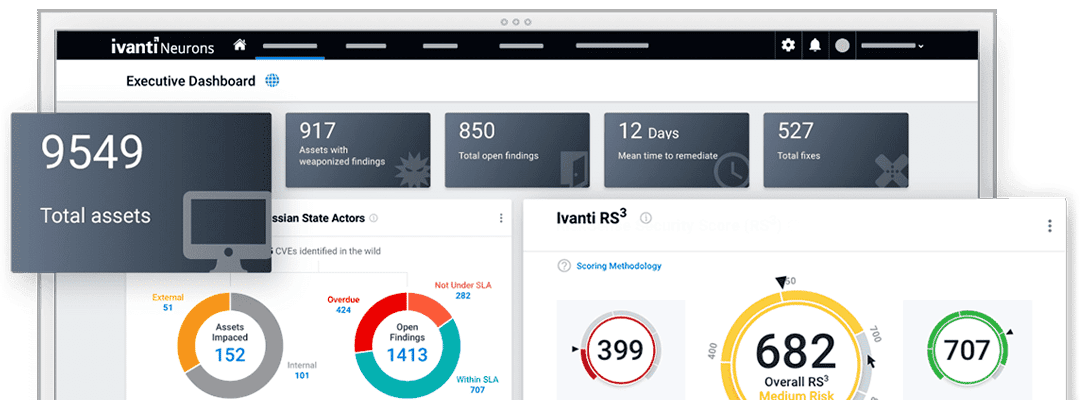
Ivanti Neurons for RBVM provides comprehensive network and application scanning capabilities, allowing organizations to identify, measure, prioritize and analyze vulnerabilities in their IT environment. Additionally, Ivanti’s solution can be easily integrated with other security solutions such as CoalFire Cybersecurity, CrowdStrike Falcon Spotlight, Aqua Security, and Qualys Vulnerability for maximum protection.
Key Features
- Ivanti’s service pairs expert security analysts with scanning tools and processes to identify network and application vulnerabilities.
- Scan findings are automatically correlated and contextualized with threat data and analysis and prioritized.
- The service offers easy-to-follow remediation plans.
- Misconfigurations and vulnerabilities can be identified on internal and/or external networks.
- The service finds code weaknesses and pinpoints coding errors and their exploitability within web applications.
- The service offers validation of identified critical scanner vulnerabilities and verifies false positives, reducing noise and data overload.
Key Capabilities
- Diverse data sources: This service allows you to gather data from various sources, including network scanners, vulnerability discoveries, and manual findings from research and pen testing teams.
- Through its vulnerability knowledge base, Ivanti Neurons’ threat engine delivers insight into vulnerabilities associated with ransomware.
- Ivanti’s vulnerability risk rating (VRR) assesses a vulnerability’s risk based on its attributes and real-world threat scenario.
- Customizable data organization
- Alerts and notifications
Pricing
This is a quote-based service; interested purchasers must fill out a pricing request form to get a tailored price for their business.
ServiceNow Vulnerability Response: Best for SecOps

ServiceNow Vulnerability Response is a comprehensive vulnerability management service built on the Now Platform and is built for streamlining the process of identifying, assessing and responding to security vulnerabilities.
Vulnerability Response integrates with the configuration management database (CMDB) to provide a single source of truth for all vulnerability-related information. It enables organizations to quickly identify, analyze and respond to potential threats and vulnerabilities.
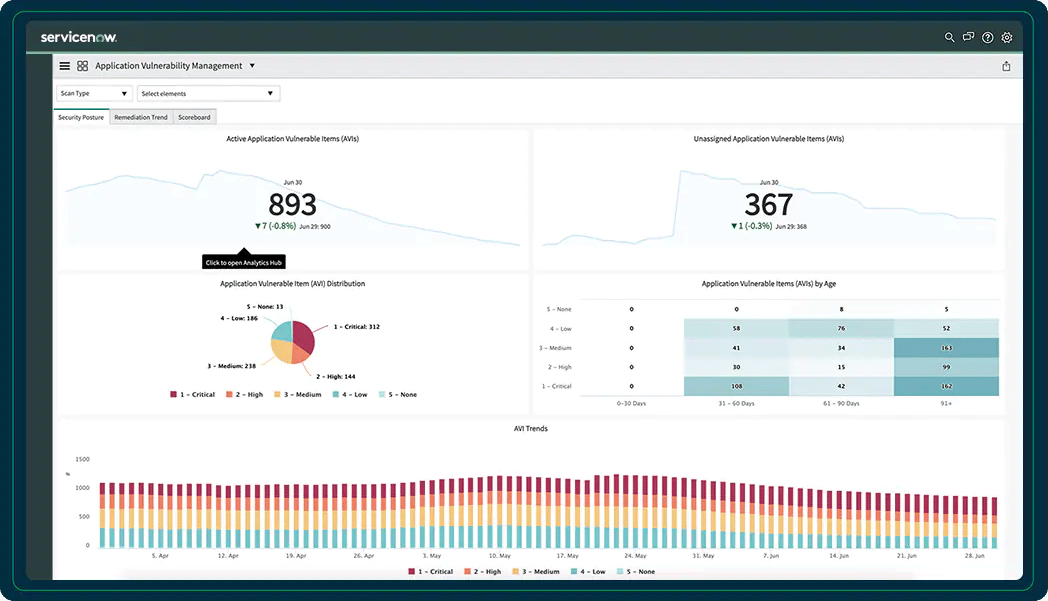
ServiceNow Vulnerability Response allows organizations to track, prioritize and remediate vulnerabilities as well as to automate responses to threats, ensuring rapid response times. It offers broad coverage of operating systems, applications, and cloud environments.
The platform allows customers to create custom policies and rules to ensure compliance with industry standards and best practices. It also offers visibility into risk posture and allows organizations to quickly assess the impact of potential threats and take the necessary steps to protect their systems.
Additionally, ServiceNow Vulnerability Response is compatible with a number of other tools, such as Qualys and Rapid7, to ensure that all vulnerabilities are quickly identified and remediated.
Key Features
- ServiceNow Vulnerability Response offers complete visibility of an organization’s IT environment.
- The service assesses dynamic and static testing results to track vulnerable items and coordinate the remediation of applications.
- With ServiceNow, users can view the organization’s highest priority remediation activities and monitor their completion.
- ServiceNow Vulnerability Response includes patch orchestration, which quickly identifies and recommends patches for critical vulnerabilities and schedules patch updates.
- The service works strategically with IT teams to remediate vulnerabilities using collaborative workspaces.
Key Capabilities
- Addresses application vulnerabilities
- Third-party integrations with vulnerability-scanning solutions
- Cloud container security
- Configuration compliance to prioritize and remediate cloud configuration issues
- Exception management with scheduled deferments and automatic reactivation
Pricing
Although the pricing for this solution is not available on the vendor website, interested buyers can contact the sales team for a quote. Additionally, you can also book a demo to get a better understanding of the solution before committing to purchasing it. The demo would help you learn more about the features of the solution, the platform’s benefits, and the solution’s scalability.
Syxsense Active Secure: Best for Ease of Use

Syxsense Active Secure is an advanced security solution that offers a comprehensive set of security tools and services to help organizations protect their networks, systems, and data. It provides end-to-end protection for on-premises, remote, roaming and cloud services.
It provides multi-OS support, including Windows, Mac, and Linux, as well as inventory and asset management, visibility into desktops, laptops, servers, and virtual machines, and remote control features to help with distributed team device management.
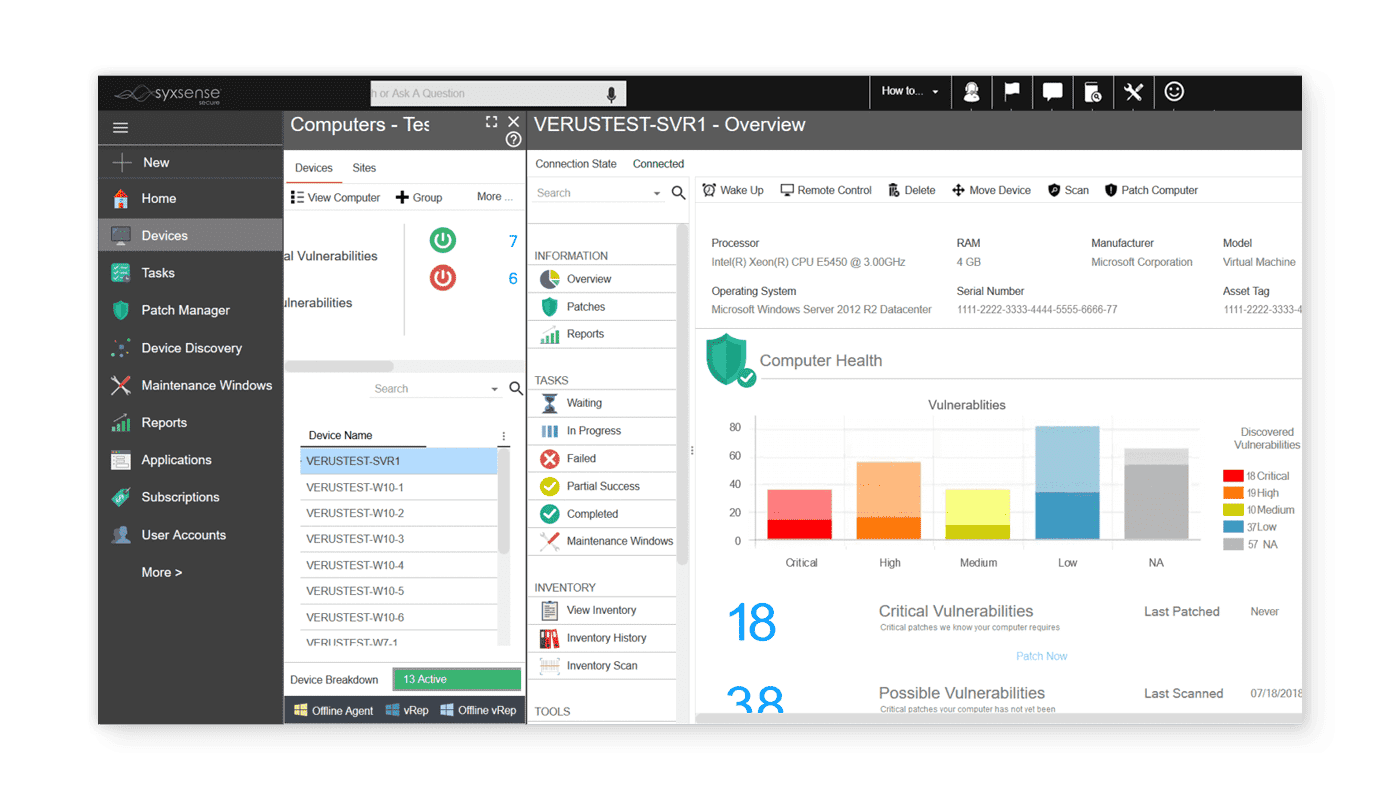
With Syxsense Active Secure, organizations can proactively monitor and protect against malicious activity and unauthorized access, detect and respond to advanced threats, and ensure compliance with industry standards and government regulations.
The solution goes beyond vulnerability management to include features such as real-time threat detection and response, user and system activity monitoring, vulnerability and patch management, endpoint security, and more. With its intuitive user interface, Syxsense Active Secure makes it easy to manage and secure your business environment.
Syxsense can perform all aspects of the vulnerability life cycle. It provides vulnerability scanning, patch management, IT management, and remediation. In addition, Syxsense finds and remediates vulnerabilities related to all computing devices (laptops, desktops, servers) except network hardware.
Key Features
- Syxsense provides 24-hour coverage and compliance assessment.
- Users can get accurate data from thousands of devices in under 10 seconds.
- Syxsense Active Secure instantly detects and eliminates running .exes, malware, or viruses.
- Syxsense enables businesses to meet governance or compliance regulations with help from its services team.
- Users will have access to experts that actively prevent zero-day attacks.
- Those upgrading to the full Syxsense Enterprise suite also gain automated remediation and mobile device management (MDM) functions.
Key Capabilities
- 100GB of cloud storage
- Hardware and software inventory
- OS and third-party patching
- Windows 10 feature update management
- Cortex drag and drop workflow builder
Pricing
Syxsense Active Secure offers three pricing plans: Syxsense Manage, Syxsense Secure, and Syxsense Enterprise. The pricing for each plan is determined based on the number of endpoints you want to manage. Buyers must request a quote from Syxsense to get an exact price for their needs.
Flexera Software Vulnerability Management: Best for Comprehensive Patch Management

Flexera Software Vulnerability Management (SVM), formerly Secunia Corporate Software Inspector, is available in a cloud edition. It is focused squarely on the challenge of identifying, prioritizing and patching software vulnerabilities.
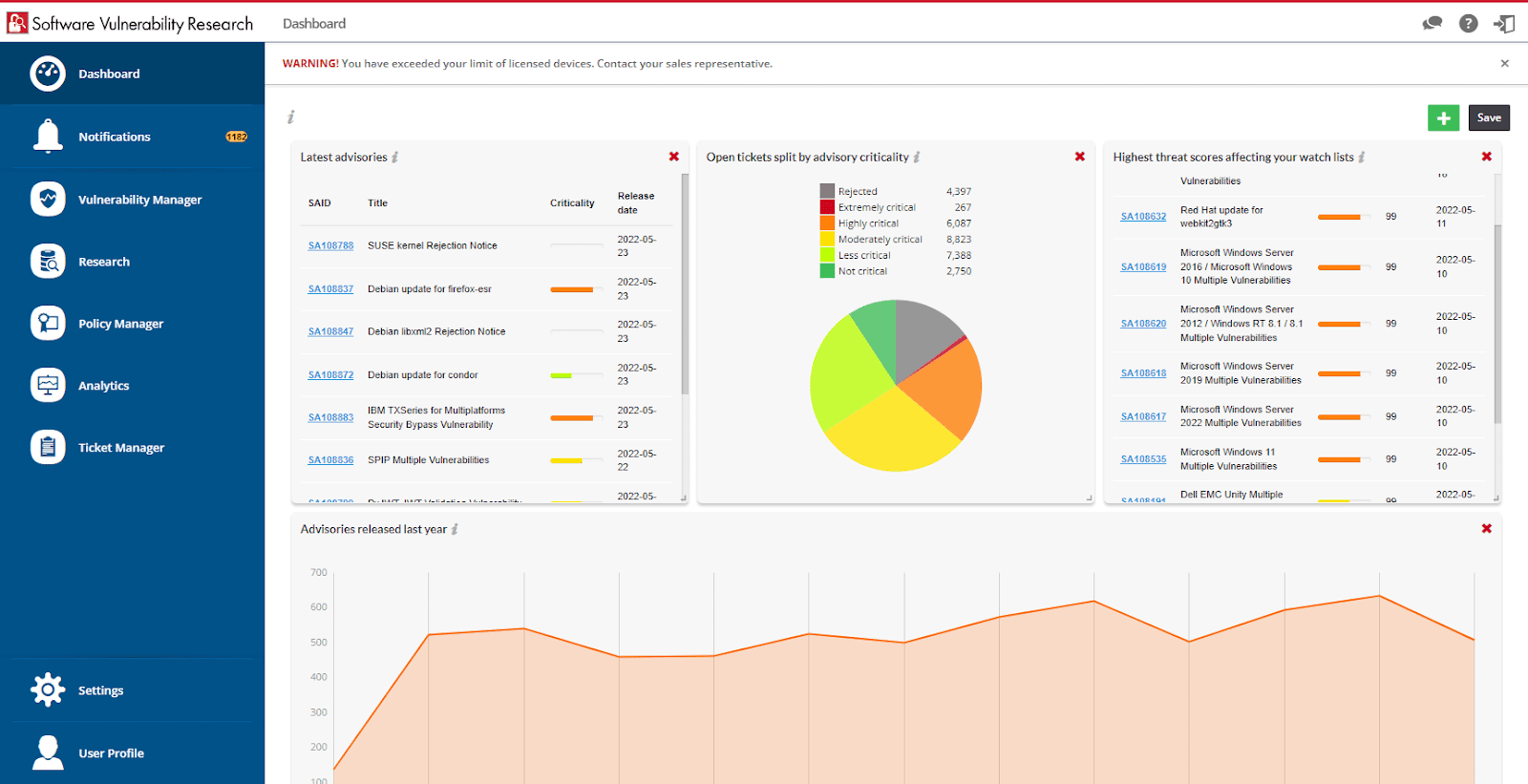
Software Vulnerability Management tool is a comprehensive vulnerability and patch management solution that enables organizations to detect vulnerabilities in their IT environment and prioritize and deploy patches quickly to reduce risk across Windows, Mac and Red Hat Enterprise Linux systems.
The solution collects vulnerability intelligence from the National Vulnerability Database, identifies the security vulnerabilities present on the system, and prioritizes the vulnerabilities based on their severity.
It then creates and publishes patches to address those vulnerabilities and integrates with patch deployment tools such as Microsoft WSUS and System Center Configuration Manager to deploy the patches to the affected systems.
Key Features
- Covers a wide range of Microsoft and non-Microsoft (third-party) product vulnerabilities.
- Security advisories consolidate all vulnerabilities related to a patch or version.
- The Secunia Research team validates and rescores vulnerabilities to prioritize actions.
- Flexera claims to detect more third-party applications than any other solution.
- Prioritization is made according to CVSS scores for patches, a Flexera criticality rating, and a threat score based on the likelihood of exploitation.
- Flexera Software Vulnerability Management has released over 4,000 patches.
- Automation features allow users to automatically set the criteria for patches they would like to publish.
- Integration is available with endpoint management solutions such as Intune, ConfigMan, WSUS, Workspace ONE, or BigFix for deployment.
Key Capabilities
- Patch automation
- Third-party application coverage
- Threat intelligence and prioritization
- Reports and dashboards
Pricing
Pricing for Flexera Software Vulnerability Management is available upon request.
Asimily Insight: Best for Healthcare Organizations

Asimily Insight is more specialized than some on this list, but it shows the diversity of the VMaaS market. It is a vulnerability management and risk remediation platform built for Internet of Medical Things (IoMT) devices — the critical web-connected equipment used by hospital systems, pharmaceutical labs, and other healthcare organizations.
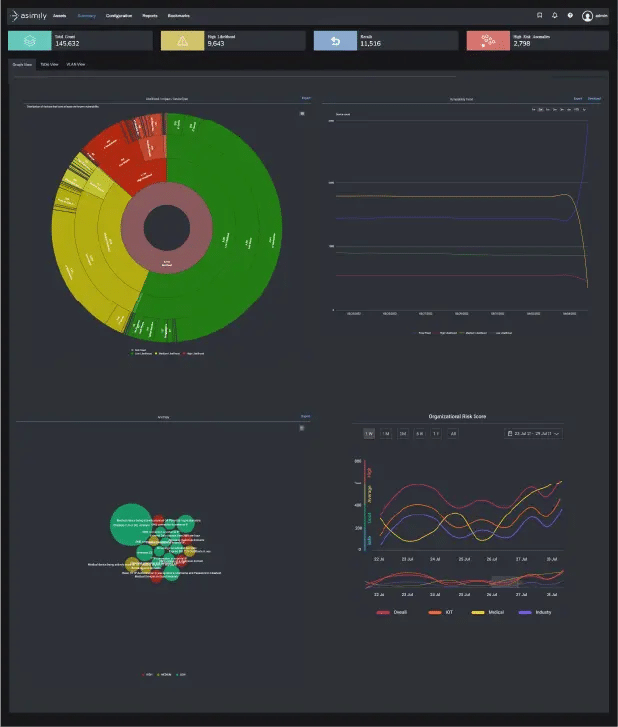
Asimily Insight helps organizations secure IoT, IoMT, and laboratory connected devices. It provides visibility into threats and risks across the entire network, allowing organizations to identify, assess, and remediate threats before they can cause damage.
The tool provides forensics analysis, anomaly detection, prevention and remediation and policy management, as well as continuous monitoring of threats on the network. It also offers an advanced dashboard to help teams better understand and manage their security posture.
Key Features
- Instead of showing a laundry list of vulnerabilities (many of which are not exploitable or patchable), it predicts potential paths for an attacker into an IoMT device to solve the most significant problems.
- Asimily Insight prioritizes remediation and mitigates risk when patching is not an option.
- Distributed Sniffer captures network traffic from any devices on the network — either on demand or automatically in response to a network anomaly event.
- Asimily Insight provides risk and vulnerability assessment and modeling on pre-procurement devices and those that haven’t been connected to the network.
Key Capabilities
- Identify and classify all types of devices
- Forensic analysis
- Track enterprise asset utilization
- Vendor management
- Proactively secure devices before purchase
- Identify compromise indications and exploit attempts
Pricing
Asimily Insight offers personalized quotes for prospective buyers. The company’s services are tailored to each individual’s specific needs. By contacting Asimily Insight, prospective buyers can get a personalized quote that best meets their needs and budget.
Also read: Healthcare Cyberattacks Lead to Increased Mortality, Lower Patient Care: Ponemon Study
Rapid7 InsightVM: Best for Affordability and Automated Risk Assessment

Rapid7’s InsightVM platform and its Managed Vulnerability Management (MVM) service manages, executes, and prioritizes remediation across the environment. Rapid7’s solutions proactively assess risk to stay ahead of threats and attain ecosystem visibility.
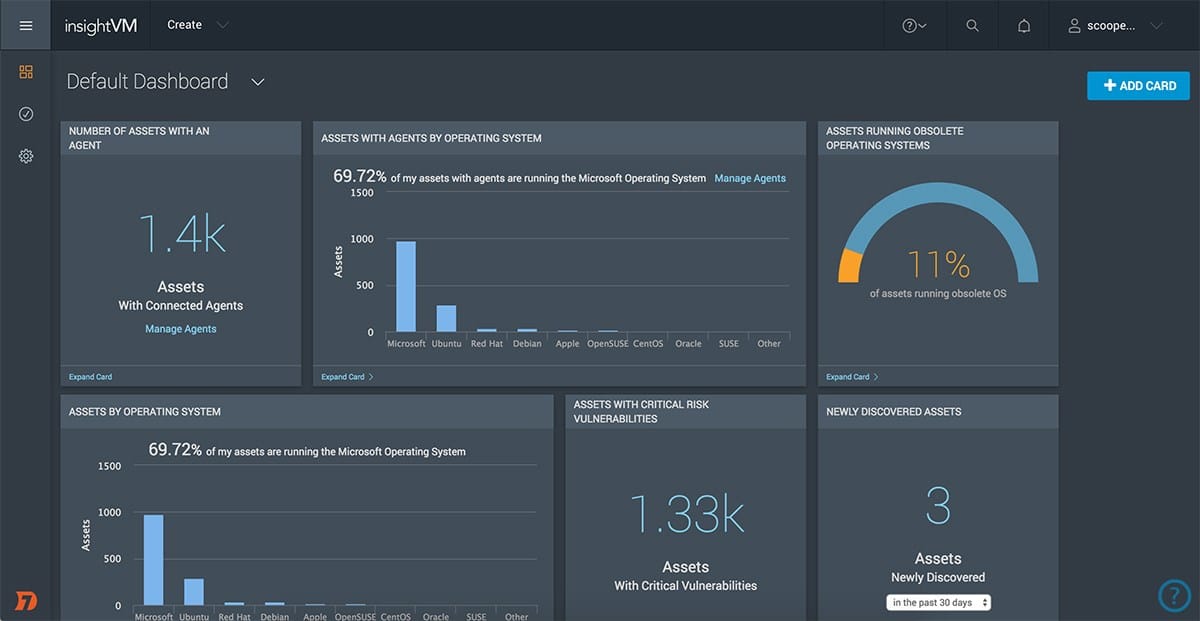
InsightVM uses advanced scanning technology to detect vulnerabilities, misconfigurations, and other risks in your network, cloud, and virtualized infrastructures. It provides detailed reports with actionable steps to help IT and DevOps teams quickly and efficiently remediate them.
InsightVM also tracks and communicates progress in real-time, allowing you to measure and communicate progress on your program goals. With InsightVM, organizations can keep their networks secure and compliant and reduce the risk of costly data breaches.
Key Features
- Rapid7 InsightVM prioritizes threats that may have the biggest impact.
- InsightVM enables users to accelerate remediation with prioritized guidance as well as exposure and risk mitigation advice.
- With InsightVM, users can enact policies, procedures, and vulnerability management processes to build collaboration across the organization, perform remediations, and measure impact.
- InsightVM features include asset discovery, cloud configuration, container assessment, and reporting.
- Rapid7 improves emerging threat response as new vulnerabilities happen.
Key Capabilities
- Internal and external network vulnerability scanning
- Remediation prioritization and guidance
- Lightweight endpoint agent
- Attack surface monitoring with Project Sonar
- Live dashboard
- Automated containment
Pricing
Rapid7 InsightVM uses a sliding scale to determine your rates. For example, the cost of managing 250 assets is $2.19 per month or $26.25 yearly; 500 assets at $1.93 monthly or $23.18 per year; 750 assets at $1.79 per month or $21.43 annually; 1000 assets at $1.71 per month or $20.54 annually; 1250 assets at $1.62 per month or $19.43 per annum.
Rapid7 also offers a 30-day free trial, available for download on Windows 64-bit and Linux 64-bit systems. This basic deployment allows the scanning of up to a maximum of 1,000 assets on your local network and provides storage for scan data, reports, and database backups.
For a managed vulnerability services quote, contact the company.
Qualys VMDR: Best for Real-time Monitoring of IT Assets

Qualys VMDR (Vulnerability Management, Detection, and Response) automatically discovers and inventories all software and hardware assets wherever they are in an environment. This cloud-based app continuously assesses vulnerabilities and applies threat intelligence to prioritize and fix actively exploitable vulnerabilities.
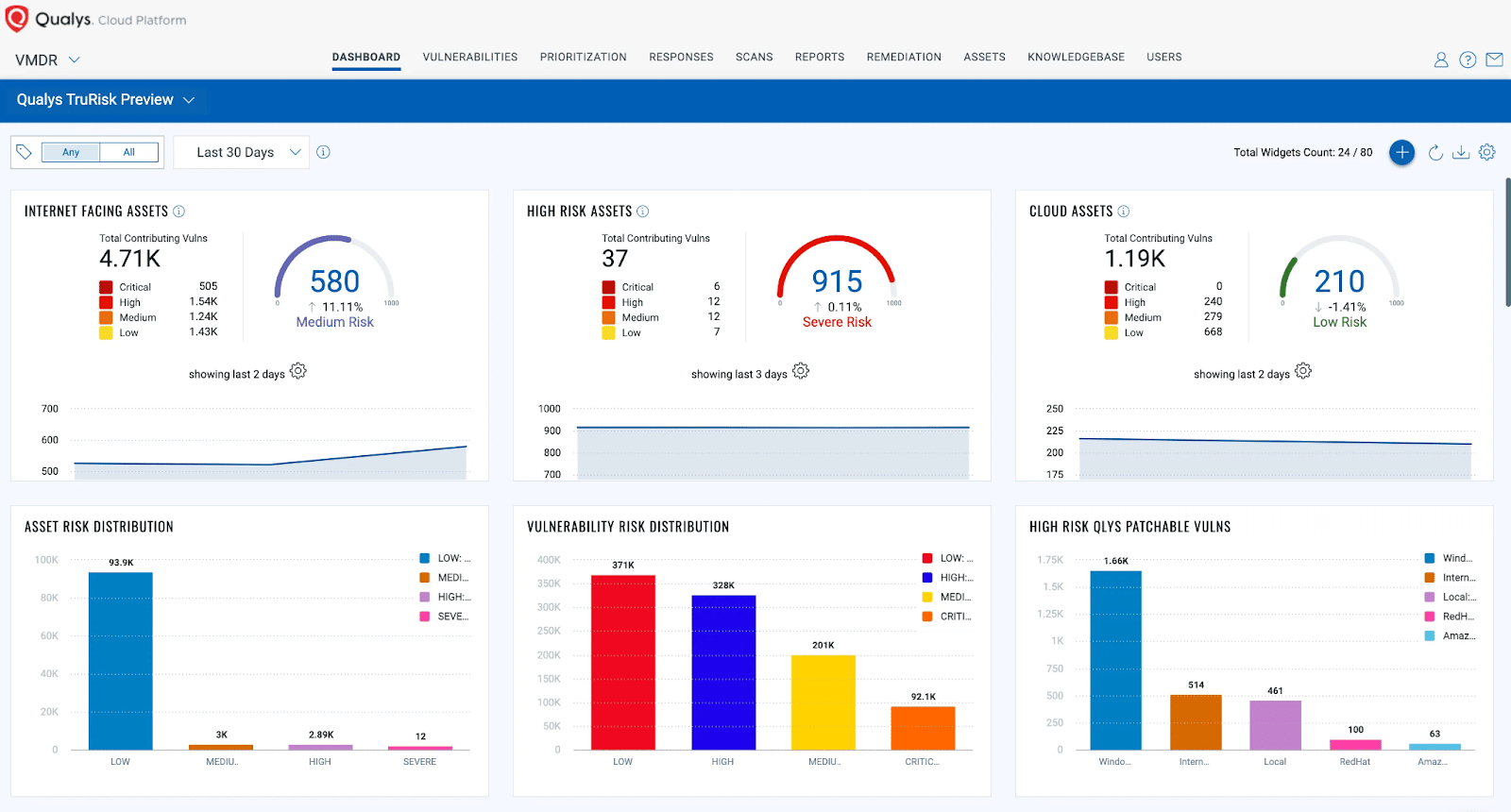
Qualys VMDR solution gives organizations real-time visibility and control of their digital assets. It helps organizations identify, prioritize, and address security vulnerabilities across their IT infrastructure, including physical, virtual, cloud, and containerized environments. It also provides capabilities for automated vulnerability scanning, patching, and response.
Qualys VMDR assesses, reports and monitors security-related misconfiguration issues based on the Center for Internet Security (CIS) benchmarks. The product detects all IT, OT, and IoT devices that are connected to your network.
Qualys VMDR integrates with other third-party solutions like Jira and ServiceNow and automatically assigns tickets, enabling remediation orchestration to reduce MTTR (Mean Time To Repair).
Key Features
- Qualys VMDR incorporates artificial intelligence (AI) and machine learning capabilities acquired from Blue Hexagon.
- Qualys VMDR offers new risk assessment and attack surface management features.
- The service provides real-time threat intelligence linked to machine learning to control and respond to evolving threats and prevent breaches.
- Qualys VMDR automatically detects the latest superseding patch for the vulnerable asset and deploys it.
- Qualys VMDR lists critical misconfigurations.
- Qualys VMDR covers mobile devices in addition to operating systems and applications.
Key Capabilities
- Automate remediation with no-code workflows
- Gather insights from over 180k vulnerabilities sourced from over 25+ threat sources
- Detect vulnerabilities and critical misconfigurations per CIS asset benchmarks
- Continuous assessment of IT assets to find vulnerabilities
Pricing
Quotes are available upon request. Qualys also offers a 30-day free trial to test the platform before buying.
Crowdstrike Falcon Spotlight: Best for Distributed Enterprises

Crowdstrike Falcon Spotlight is a cloud-based security solution that provides threat intelligence, visibility, and protection for organizations of all sizes. The solution combines advanced threat intelligence, machine learning, and artificial intelligence to detect, investigate, and remediate advanced threats.
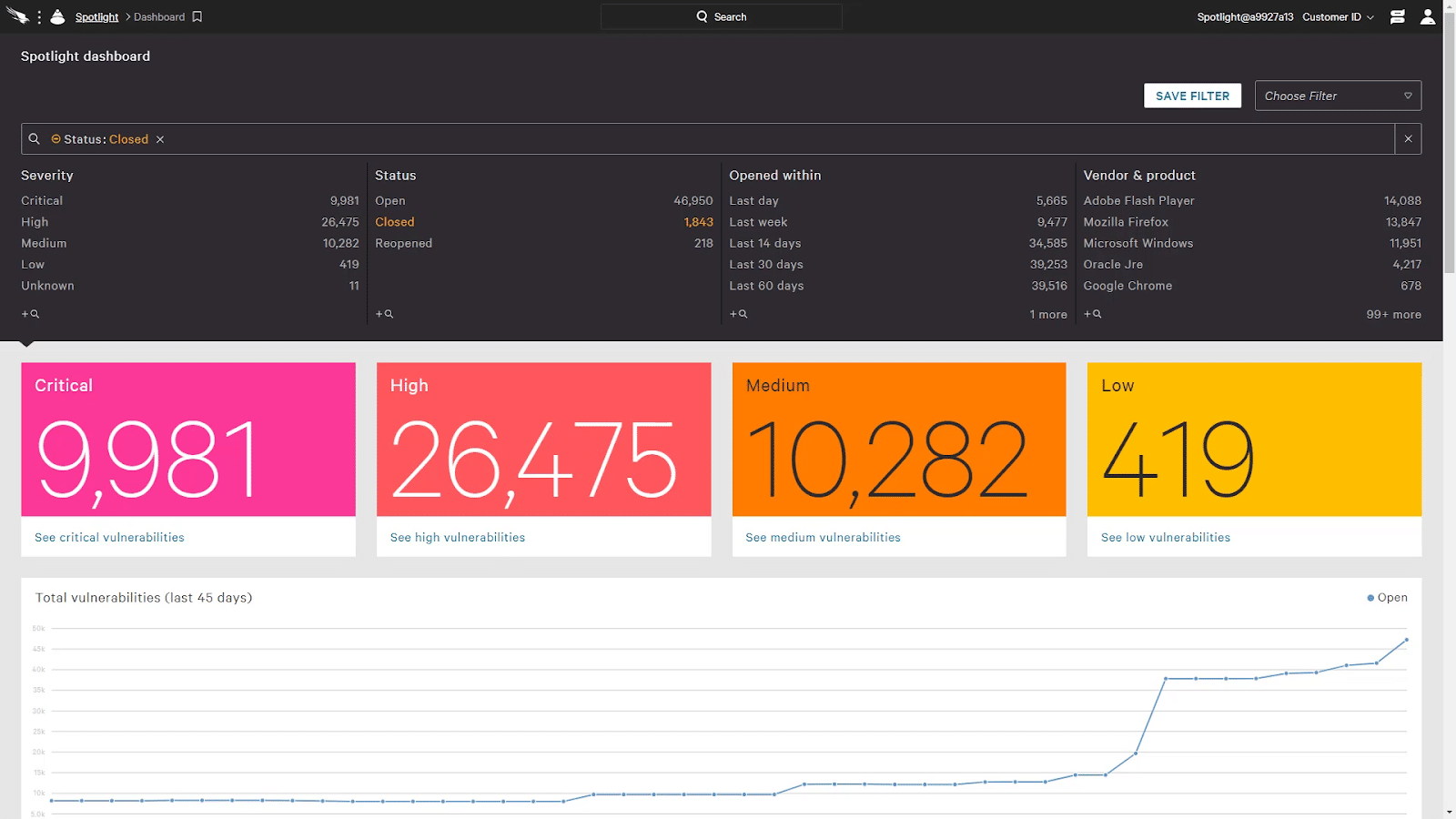
Spotlight can detect malicious activity in real-time and allows organizations to respond quickly to and mitigate these threats. Additionally, the solution provides comprehensive visibility into all activity on the network and allows organizations to identify any suspicious activity quickly.
CrowdStrike Falcon Spotlight offers automated vulnerability assessment, whether on or off the network, and fast time-to-respond. This tool brings real-time visibility to vulnerabilities and threats.
Key Features
- CrowdStrike Falcon Spotlight prioritizes and predicts which vulnerabilities are most likely to affect the organization with ExPRT rating.
- It is a module part of a more extensive Falcon suite that includes endpoint detection and response (EDR), antivirus, threat hunting and intelligence, and more.
- CrowdStrike Falcon Spotlight has built-in AI, which ties together threat intelligence with a real-time vulnerability assessment.
- CrowdStrike Falcon Spotlight is a single lightweight agent architecture.
- CrowdStrike Falcon Spotlight utilizes scanless technology to deliver an always-on, automated approach with real-time prioritized data.
- CrowdStrike Falcon Spotlight eliminates bulky reports, replacing them with its dashboard.
See the Top Endpoint Detection & Response (EDR) Solutions
Key Capabilities
- Monitors the vulnerability status of all endpoints, whether on-premises, off-premises, or in the cloud, in real-time
- No hardware appliances or infrastructure required
- Works with other CrowdStrike Falcon platforms to actively monitor all endpoints, detect any incident, investigate and remediate quickly
- Unified threat and vulnerability management
Pricing
Quote for the CrowdStrike solution is available upon request. You can also try the product free for 15 days before making a purchase decision.
What are the Main Steps Involved in VMaaS?
Vulnerability management as a service is a cyclical process that includes several steps:
-
- Discovery: The longer vulnerabilities remain undetected, the more likely they are to result in a breach. To combat this, companies should perform weekly external and internal network scans to identify new vulnerabilities.
- Prioritize Assets: Once it’s known which systems are in use, companies can assign each asset a value based on its usage or role. This context helps companies know how pressing a vulnerability is to fix.
- Assess Vulnerabilities: This helps companies understand the state of the applications and systems in their environments.
- Prioritize Vulnerabilities: During a scan, vulnerabilities will likely be uncovered. Here, companies will need to prioritize them based on their potential risk to the business, workforce, and customers.
- Remediate Vulnerabilities: Once vulnerabilities are identified and prioritized, the next step is to mitigate their impact. Here, organizations should work toward achieving an effective system-wide process between security operations, IT operations, and system administration teams to ensure everyone is on the same page.
- Verify Remediation: Once mitigated, verification ensures the incident is recorded in a tracking system which facilitates key performance metrics from the incident.
- Report on Status: Especially when there is a major software flaw, internal stakeholders may be wondering about how well the organization addressed the once-active vulnerabilities. Reporting on the status of these vulnerabilities may require additional reports and dashboards to share with different users, stakeholders, and lenses.
Benefits of Using VMaaS
Organizations often develop their own custom software applications, which can heighten application security risks. According to the Verizon Data Breach Investigations Report, 39% of data breaches came from web application compromise, which can often be a result of organizations leveraging open-source code, which can lead to the mess of dependencies that became apparent in vulnerabilities like Log4j Log4Shell and Apache Commons Text4Shell.
While the benefits of open-source code include faster application development, this code is enticing for criminals to study and exploit. That’s why finding and fixing these vulnerabilities has become so vital. By leveraging VMaaS systems that provide effective, additional layers of protection, security flaws can be found, managed. and corrected on an ongoing basis.
“Vulnerability management as a service improves on traditional vulnerability management practices by placing an agent on managed assets,” said Graham Brooks, senior security solutions architect at Syxsense. “Traditional vulnerability management tools cannot review or remediate issues beyond the traditional business network perimeter. VMaaS circumvents this dependency by allowing assets to be monitored and managed regardless of network topography.”
Disadvantages of Using Vulnerability Management Services
Like any other software on the market, vulnerability management software is far from perfect. Using vulnerability services doesn’t mean every vulnerability will be caught. Therefore, it’s important for IT teams to maintain best practices and conduct frequent scans to ensure they are not blinded by a false sense of security. VMaaS is not a panacea; IT teams will still need all the security tools they currently have.
While vulnerability management services are imperfect, they perform an essential process, and organizations need to make sure they are maximizing the benefits of these solutions. They can potentially keep an organization from becoming one of those mystifying breach headlines involving a long-patched vulnerability.
How Much Does Vulnerability Management as a Service Cost?
Costs can range drastically between vendors, as the types of services provided can also vary widely. Some security vendors simply perform vulnerability scans. Others provide fully automated management of the vulnerability life cycle.
It’s important to first understand requirements before selecting any security product vendor. Among lower functionality VMaaS products, prices can start under $1 per endpoint per month. Other platforms with higher levels of service can range up to $8 to $12 per asset per month.
Also see:
How to choose the best vulnerability management service for your enterprise
Determine your needs
The first step in selecting the best vulnerability management service for your enterprise is to determine your specific needs. Consider the size of your organization and the amount of data and systems you need to protect. Are you looking for a service that provides regular scanning, patching, and reporting capabilities? Are you looking for a service that includes policy enforcement and threat intelligence?
Research Different Solutions
Once you know what kind of threats you need protection against, you can start researching different solutions. Look into different vendors and read online reviews. Ask other companies in your industry what solutions they use and why.
Consider your Budget
Vulnerability management services can range in price from free to hundreds of dollars per month. Think about the features you need and what you are willing to spend.
Evaluate your Options
Once you have narrowed your search to a few vendors, evaluate each option on its merits. Look for data protection, system scanning, and incident response features. Make sure the service is tailored to your needs and can help you meet your security goals.
Get a Trial
Finally, request a trial of the service before you commit to purchasing it. This will allow you to test the service and see if it meets your needs.
Final Word
Vulnerability management is one of the most challenging security tasks an organization can face, but it’s also one of the most critically important. For an idea of how important cloud and security companies think it is — and the lengths they go to manage vulnerabilities — see our recent coverage of the MITRE ResilienCyCon conference: You Will Be Breached So Be Ready.
That difficulty and importance is why many companies have outsourced the task to security service providers — a trend that we expect will only grow over time.
Aminu Abdullahi contributed to this report




