User and entity behavior analytics (UEBA) tools help businesses understand and mitigate user threats more accurately and efficiently. They typically offer features like behavioral baselines, integrated threat intelligence, and remediation workflows. If your organization is looking for a UEBA tool to protect your systems and networks from user threats, I’ve compiled a list of popular enterprise solutions for analyzing user behaviors and responding to threats.
Here are my picks for the top seven UEBA tools:
- Rapid7 InsightIDR: Best overall UEBA solution
- Microsoft Sentinel: Best for core UEBA features
- FortiSIEM: Best for Fortinet networking environments
- LogRhythm SIEM: Best for advanced SIEM needs
- Cynet: Best for combined UEBA and NDR needs
- Exabeam: Best for third-party security integrations
- Splunk UBA: Best standalone user analytics solution
Top UEBA Solutions Comparison
The following table broadly compares a few features of my top picks and the availability of free trials.
| Threat Intelligence | Compromised User Detection | Peer Groups | Response Playbooks | Free Trial | |
|---|---|---|---|---|---|
| Rapid7 InsightIDR | ✔️ | ✔️ | ❌ | ✔️ | 30 days |
| Microsoft Sentinel | ✔️ | ✔️ | ✔️ | ✔️ | 31 days |
| FortiSIEM | ✔️ | ✔️ | ❌ | ➕ | ❌ |
| LogRhythm SIEM | ✔️ | ✔️ | ❌ | ✔️ | ❌ |
| Cynet 360 AutoXDR | ✔️ | ✔️ | ❌ | ✔️ | Contact for length |
| Exabeam | ✔️ | ✔️ | ✔️ | ✔️ | ❌ |
| Splunk UBA | ❌ | ✔️ | ✔️ | ➕ | Contact for length |
✔️ = yes ❌= no ➕ = add-on or another product from the vendor
Based on my evaluation of the products, all are strong security solutions, but Rapid7 InsightIDR is the clear winner because it offers many UEBA-specific features, strong administrative capabilities, and transparent pricing. Continue reading to learn more about my top picks, or jump down to see how I evaluated the best UEBA solutions.
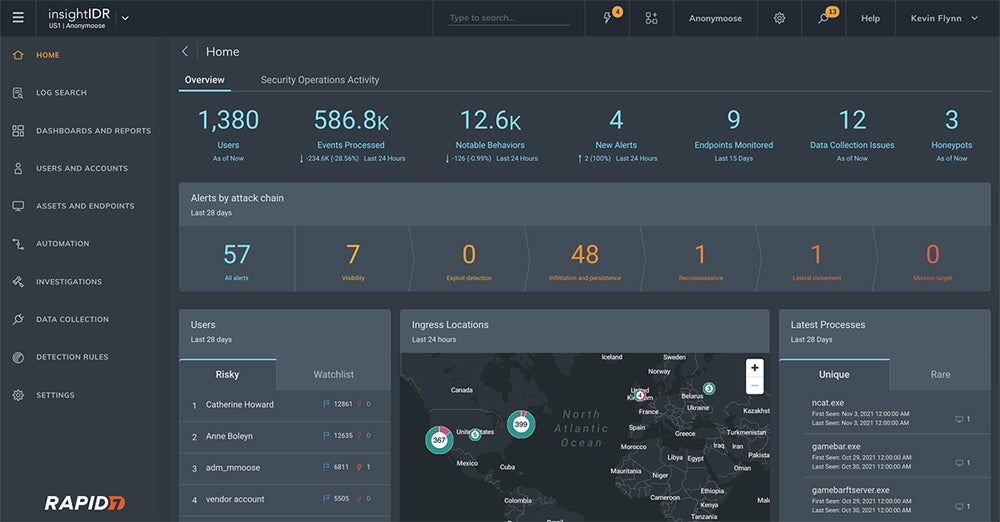
Rapid7 InsightIDR – Best Overall UEBA Solution
Overall Rating: 4.5/5
- Pricing: 5/5
- Core features: 4.9/5
- Additional features: 4.7/5
- Ease of use and administration: 5/5
- Customer support: 4.5/5
Rapid7 InsightIDR is a combined SIEM and XDR platform that continuously baselines normal user activity beyond defined indicators of compromise. It’s designed to detect hard-to-spot threats, such as attackers posing as company employees or data exfiltration attempts from malicious insiders. If you’re looking for a combined security solution, InsightIDR is a great choice. Its strong feature set and administrative capabilities make it our best overall UEBA.

Pros
Cons
For more information, read our full review of Rapid7 InsightIDR.
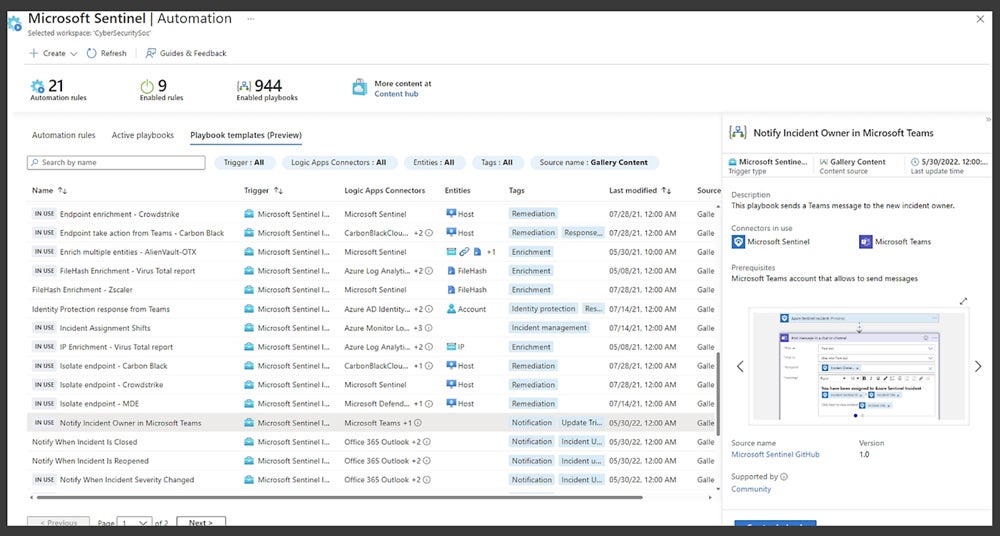
Microsoft Sentinel – Best for Core UEBA Features
Overall Rating: 4.1/5
- Pricing: 4.8/5
- Core features: 4.3/5
- Additional features: 4.2/5
- Ease of use and administration: 4/5
- Customer support: 3.3/5
Microsoft Sentinel is a cloud-based SIEM solution that also provides UEBA functionality. Its features include incident prioritization, peer grouping, and incident timelines. Aside from these tools, Sentinel offers many other UEBA and SIEM features — consider Sentinel if you’re particularly focused on extensive security capabilities. It also integrates with Defender, Microsoft’s XDR product, and is a great choice for Azure Cloud businesses.
Pros
Cons
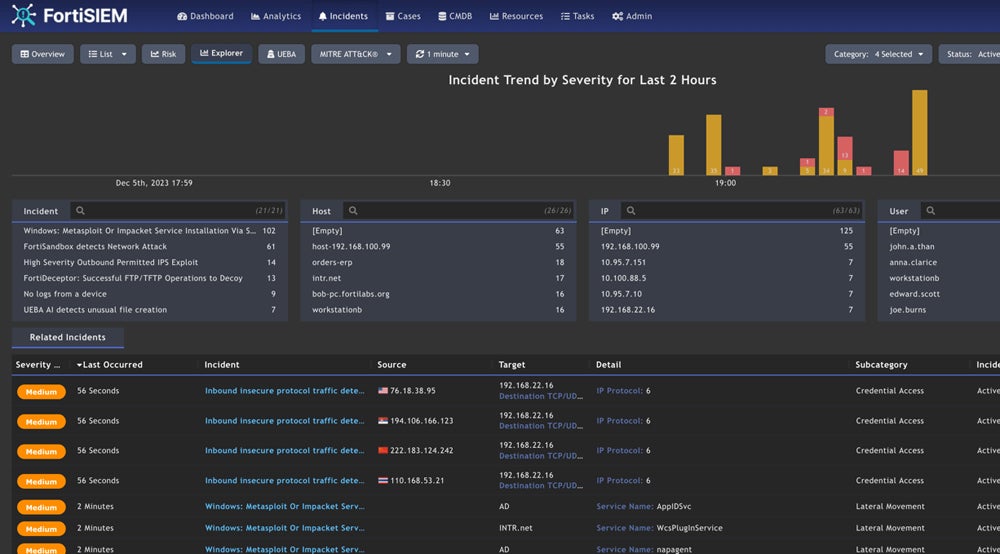
FortiSIEM – Best for Fortinet Networking Environments
Overall Rating: 3.8/5
- Pricing: 3.3/5
- Core features: 3.5/5
- Additional features: 2.3/5
- Ease of use and administration: 5/5
- Customer support: 4.4/5
FortiSIEM is a comprehensive SIEM product offered by renowned network security vendor Fortinet. It includes UEBA features like insider threat identification, user risk scores, and compromised account detection. FortiSIEM is a strong solution for any business. Still, it’s particularly beneficial for teams that already use Fortinet networking devices like firewalls because it integrates with FortiGate appliances, allowing them to share data.

Pros
Cons
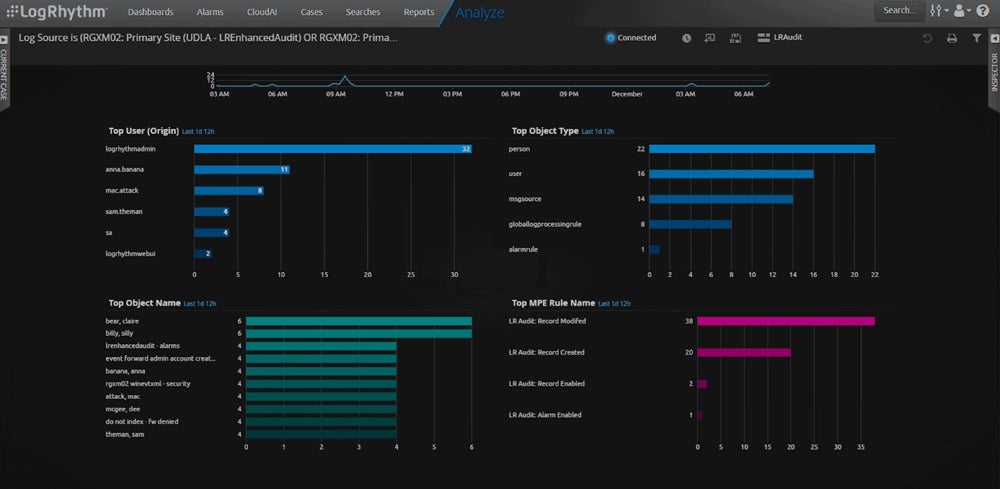
LogRhythm SIEM – Best for Advanced SIEM Needs
Overall Rating: 3.5/5
- Pricing: 2.3/5
- Core features: 3.9/5
- Additional features: 3.3/5
- Ease of use and administration: 3.8/5
- Customer support: 3.6/5
LogRhythm offers a strong SIEM platform with UEBA functionality, using machine learning to detect anomalies such as insider threats, brute force attacks, and admin abuse. LogRhythm’s file integrity monitoring feature hunts for inappropriate file access; consider LogRhythm if you store large numbers of files with sensitive company data. LogRhythm can take months to customize fully; it’s a good solution for experienced teams with advanced SIEM requirements.

Pros
Cons
For more information, read our full review of LogRhythm SIEM.
Cynet 360 AutoXDR – Best for Combined UEBA & NDR Needs
Overall Rating: 3.4/5
- Pricing: 4.5/5
- Core features: 3.4/5
- Additional features: 3.2/5
- Ease of use and administration: 3/5
- Customer support: 3.3/5
Cynet 360 AutoXDR is an extensive detection and response platform, offering organizations a single, multi-tenant platform that converges endpoint, user, and network security functions within one suite. UBA falls under the platform’s network security. Because Cynet’s XDR platform offers a wide range of UBA features and other security tools, it’s a good choice for large organizations, particularly teams also looking for network detection and response.

Pros
Cons
To learn more about the platform, read our review of Cynet 360 AutoXDR next.
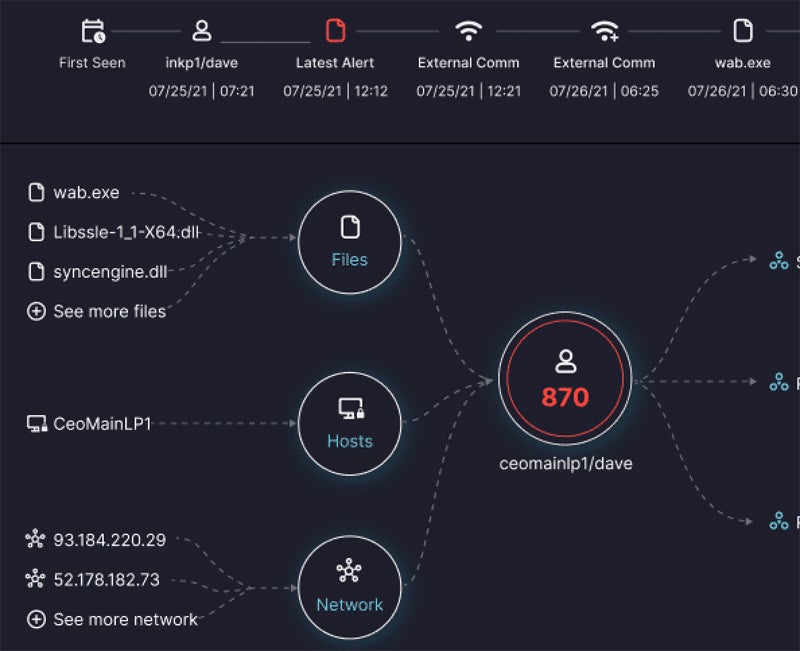
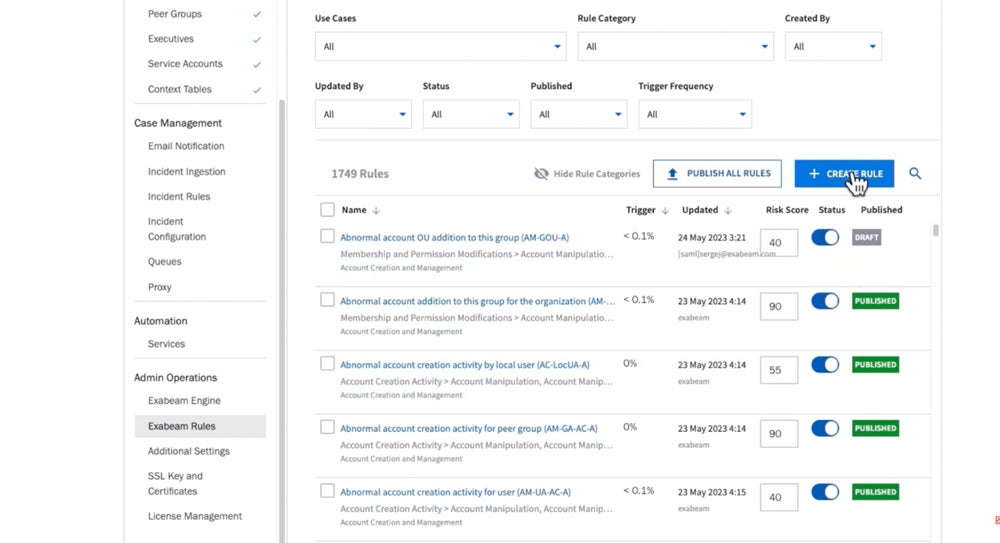
Exabeam – Best for Third-Party Security Integrations
Overall Rating: 3.4/5
- Pricing: 2.3/5
- Core features: 3.3/5
- Additional features: 4.1/5
- Ease of use and administration: 3.7/5
- Customer support: 3.4/5
Exabeam is a security operations provider that offers UEBA as one of its main capabilities. Key features include event timelines, role-based access control, and the option to retain your existing SIEM platform. Exabeam integrates with hundreds of third-party security tools; there’s plenty of variety, too, including non-security data sources like Salesforce. I recommend Exabeam for organizations that want a wide variety of data sources.

Pros
Cons
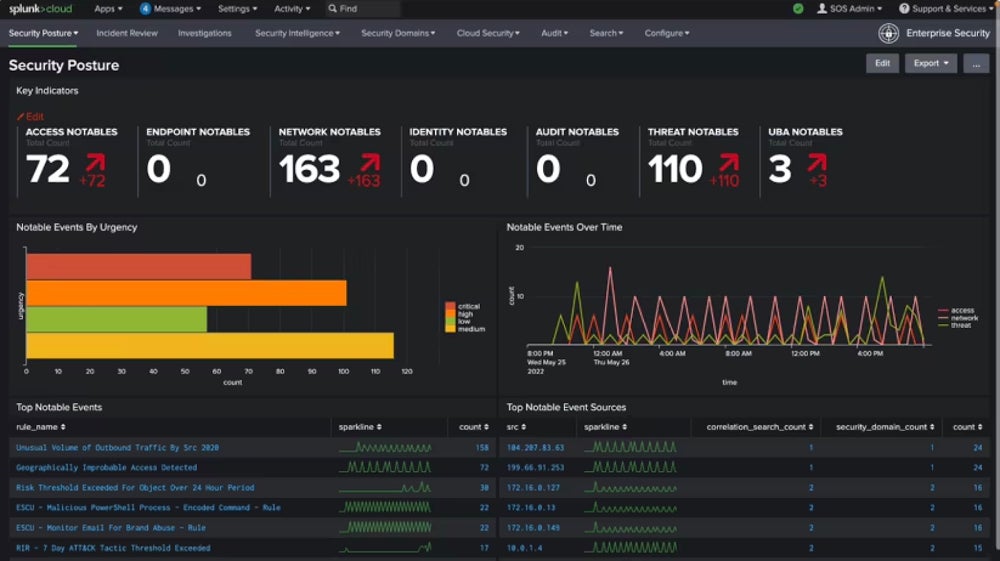
Splunk UBA – Best Standalone User Analytics Solution
Overall Rating: 3.3/5
- Pricing: 3.5/5
- Core features: 2.9/5
- Additional features: 3.8/5
- Ease of use and administration: 2.8/5
- Customer support: 4.2/5
Splunk UBA is a rare standalone behavioral analytics product that provides the capabilities teams need to monitor, analyze, and detect user threats. Organizations can improve their security posture with Splunk’s threat workflow regardless of business size or skill set. This technology narrows business-wide raw events down to a few possible threats. I recommend Splunk for teams that want a standalone solution dedicated strictly to user analytics.

Pros
Cons
Key Features of UEBA Tools
While UEBA as a security category now often fits within larger platforms, a few key capabilities are consistent across the industry. Core UEBA features include infrastructure monitoring, analytics, alerts, and user management.
Monitoring
In a security infrastructure, networks, devices, and applications must be monitored. UEBA tools constantly observe IT systems and notify admins when network traffic and the behavior of devices or applications aren’t consistent with preconfigured standards.
Analytics
In UEBA solutions, behavioral analytics are based on machine learning technology. ML identifies user behaviors to determine whether they fit predetermined criteria for typical actions. If the UEBA tool decides a user’s erratic behavior is dangerous, it highlights this pattern on the dashboard for security admins to view.
Alerts & Prioritization
UEBA tools trigger alerts when a significant enough anomaly occurs. Because these tools study typical user and application patterns over time, they notice when something unexpected happens. UEBA tools often prioritize alerts — ranking the risk level so IT and security staff can decide which to tackle first.
User & Entity Management
UEBA solutions monitor user permissions and determine whether a particular user’s behavior contradicts their assigned permissions. This helps decrease privileged access exploitation and may also reveal malicious insider activity. UEBA solutions also often monitor entities, or assets like laptops or servers, to determine whether their behavior is anomalous and needs to be quarantined or shut down.
Advanced Threat Identification
When UEBA tools monitor systems and notice anomalies, they often identify what kind of issue is occurring. These include threats like lateral movement and data exfiltration, and UEBA solutions may also tell you whether the threat is internal or external to your organization. This information is useful for helping you handle threat actors, particularly if they’re your own employees.
How I Evaluated the Best UEBA Solutions
To determine which UEBA solutions were the best choices for businesses, I created a product scoring rubric with five major categories that all buyers should consider. Each category received a weight based on its importance, and the categories all contained multiple subcriteria, which were also weighted. I researched the products and their capabilities, and the top solutions received their final score based on how they met the subcriteria and how those were weighted.
Evaluation Criteria
To evaluate the solutions, I first considered core UEBA features, such as integrated threat intelligence and alert management. I then looked at ease of use and administrative features, like documentation, training videos, and APIs for developers. Finally, I evaluated pricing, including free trials; additional features like data exfiltration and automated remediation, and customer support, including different channels and availability of demos.
- Core features (30%): I evaluated features like log retention, incident prioritization, and integrations with Active Directory.
- Criterion winner: Microsoft
- Ease of use and administration (25%): This category included capabilities that make a UEBA solution easier to use, like a single pane of glass for management.
- Criterion winner: Multiple winners
- Pricing (15%): I looked at the transparency of vendor pricing, as well as subscription duration and free trials.
- Criterion winner: Rapid7
- Additional features (15%): In this category, I considered nice-to-have features like role-based access controls and lateral movement detection.
- Criterion winner: Rapid7
- Customer support: I analyzed the availability of support channels like phone, email, and live chat, as well as demos and the option to have a technical account manager.
- Criterion winner: Rapid7
Frequently Asked Questions (FAQs)
What’s the Difference Between SIEM & UEBA?
Both SIEM and UEBA solutions collect data within an organization’s infrastructure. However, UEBA focuses more on rapid alerts based on user actions, while SIEM focuses more on logging and identifying anomalies in those logs. Although SIEM data can be used for rapid response to incidents, it’s not as focused on user behavior.
However, SIEM vendors are increasingly adding behavioral capabilities to their systems, a convergence of SIEM and UEBA that benefits users. This list is representative of that shift, too, since both FortiSIEM and LogRhythm are SIEM platforms first and foremost.
What’s the Difference Between UEBA & EDR?
EDR covers all business endpoints, such as laptops, mobile devices, and servers, and often provides user behavior analytics. UEBA and EDR are very similar, but EDR solutions focus more on incident response technology, while UEBA is more centered around advanced behavioral study. Some platforms, like Rapid7 InsightIDR, offer both in the same product.
Your business would want to deploy EDR if the security teams are focused on strong endpoint coverage; if you’re looking at user behavior across employees, contractors, and service users, you’d choose UEBA. But both can work well together in a business’s security infrastructure if they’re well-integrated.
Why Do I Need a UEBA Tool?
If your organization has multiple users accessing company resources, like applications and cloud file-sharing solutions, you should consider a UEBA solution. Users present some of the biggest dangers to enterprise security, and a behavioral analytics platform like UEBA will help your security, and IT teams manage the deluge of user activity data to identify anomalous patterns that could indicate a threat.
UEBA tools can also be used to reveal patterns over time. If a particular user behavior becomes consistent, that could be a vulnerability for your security team to address. Without a dedicated security solution, it’s hard to standardize finding and understanding long-term data.
Bottom Line: UEBA Helps You Better Understand Your Users & Business Risks
UEBA solutions provide valuable insights for businesses as they work to understand user and application behavior across their tech infrastructures. The more data is generated by network traffic and company software, the more information about users and assets that IT and security professionals have to analyze and distill. UEBA does some of that work for them, redirecting their workload from manual efforts to more strategic ones.
Of course, UEBA tools don’t entirely eliminate manual IT work, nor are they set-and-forget solutions. But it’s rewarding to configure UEBA to fit your own infrastructure closely: alerts make more sense, and you’ll begin to better understand behavioral patterns in databases, networks, and applications. UEBA is a long-term investment for businesses that want to improve their security posture by knowing exactly what their users are doing.
Read more about how behavioral analytics works in security environments next.
Drew Robb contributed to this buyer’s guide.