Breach and attack simulation (BAS) tools can automatically spot vulnerabilities in an organization’s cyber defenses, akin to continuous, automated penetration testing. BAS solutions often recommend and prioritize remediation to maximize security resources and minimize cyber risk.
A few vendors refer to advanced BAS solutions as security validation or continuous threat exposure management (CTEM). Several of these tools also assess broader security defenses and potential attack paths, a market known as attack surface management. Artificial intelligence and machine learning are an important part of the BAS market, as automated cybersecurity tools are needed to keep up with the huge volume of vulnerabilities and emerging threats.
We analyzed the market for BAS tools to come up with this list of the top 19 vendors, plus an additional 8 honorable mentions, followed by more on breach and attack simulation technology and buying considerations.
- AttackIQ: Best for AI/ML security testing
- Cymulate: Best user experience
- Picus Security: Best for detecting logs and alert gaps
- SafeBreach: Best for integration with other security tools
- XM Cyber: Best for attack path management
- CyCognito: Best for risk detection and prioritization
- FireMon: Best BAS tool for visualization
- Akamai Guardicore: Best for microsegmentation, visibility and control
- Mandiant: Best BAS tool for threat intelligence
- Qualys: Best for vulnerability management and security compliance
- IBM Randori: Best BAS tool for red teaming
- Rapid7: Best for affordable risk analysis
- BreachLock: Best for network and web pentesting
- Horizon3.ai: Best BAS tool for small businesses
- NetSPI: Best BAS tool for pen testers
- Pentera: Best for automated security validation
- Scythe: Best for adversary emulation
- Skybox Security: Best for integration with data sources
- Tenable: Best for analytics and attack surface visibility
- Honorable Mentions
- What is Breach & Attack Simulation Software?
- Why Do Companies Use BAS?
- BAS features
- Deployment Options for BAS
- Bottom Line: Breach and Attack Simulation (BAS) Tools
Featured Partners
eSecurity Planet may receive a commission from merchants for referrals from this website
20 Best Breach and Attack Simulation (BAS) Vendors Comparison Chart
| Best for | Exposure management | Attack path analysis | Integration with third-party service | Full kill chain APT | Starting price | |
|---|---|---|---|---|---|---|
| AttackIQ | AI/ML security testing | Yes | Yes | Yes | Yes | $227,500.00 one-time payment, per year |
| Cymulate | User experience | Yes | Yes | Yes | Yes | $7,000 |
| Picus Security | Detecting logs and alert gaps | Yes | Yes | Yes | Yes | $30,000 |
| SafeBreach | Integration with other security tools | Yes | Yes | Yes | Yes | $18,000 |
| XM Cyber | Attack path management | Yes | Yes | Yes | Yes | $7,500 |
| CyCognito | Risk detection and prioritization | Yes | Yes | Yes | Yes | $30,000 |
| FireMon | BAS tool for visualization | Yes | Yes | Yes | Yes | Not provided by vendor |
| Akamai Guardicore Infection Monkey | Network micro-segmentation, visibility and control | Yes | Yes | Yes | Yes | Open source and free |
| Mandiant | Threat intelligence | Yes | Yes | Yes | Limited | Not provided by vendor |
| Qualys | Vulnerability management and security compliance | Yes | Yes | Yes | Yes | $542 per month |
| Randori | Red teaming | Yes | Yes | Yes | Limited | Not provided by vendor |
| Rapid7 | Affordable risk analysis | Yes | Yes | Yes | Yes | $1.62 per asset per month |
| BreachLock | Network and web pentesting | Yes | No | Yes | No | Not provided by vendor |
| Horizon3.ai | Startups and small businesses | Yes | Yes | Yes | Yes | $24,999 per year |
| NetSPI | BAS tool for pen testers | Yes | Limited | Yes | Yes | Not provided by vendor |
| Pentera | Automated security validation | Yes | Yes | Yes | No | Not provided by vendor |
| Scythe | Adversary emulation | Yes | Limited | Yes | Limited | Not provided by vendor |
| Skybox Security | Integration with different data sources | Yes | Yes | Yes | Limited | Not provided by vendor |
| Tenable | Analytics and attack surface visibility | Yes | Yes | Yes | Limited | $2,934.75 per year |

AttackIQ
Best for AI/ML security testing
AttackIQ started as an automated validation platform in 2013 in San Diego, California. The platform enables organizations to test and measure their security posture across environments. Informed by the MITRE ATT&CK matrix and its wealth of cyber adversary behavior, clients can run advanced scenarios targeting critical assets and continuously improve their defensive posture.
AttackIQ’s Anatomic Engine is a standout feature, as it can test ML and AI-based cybersecurity components. With the capacity to run multi-stage emulations, test network controls, and analyze breach responses, AttackIQ remains a top contender among BAS solutions.
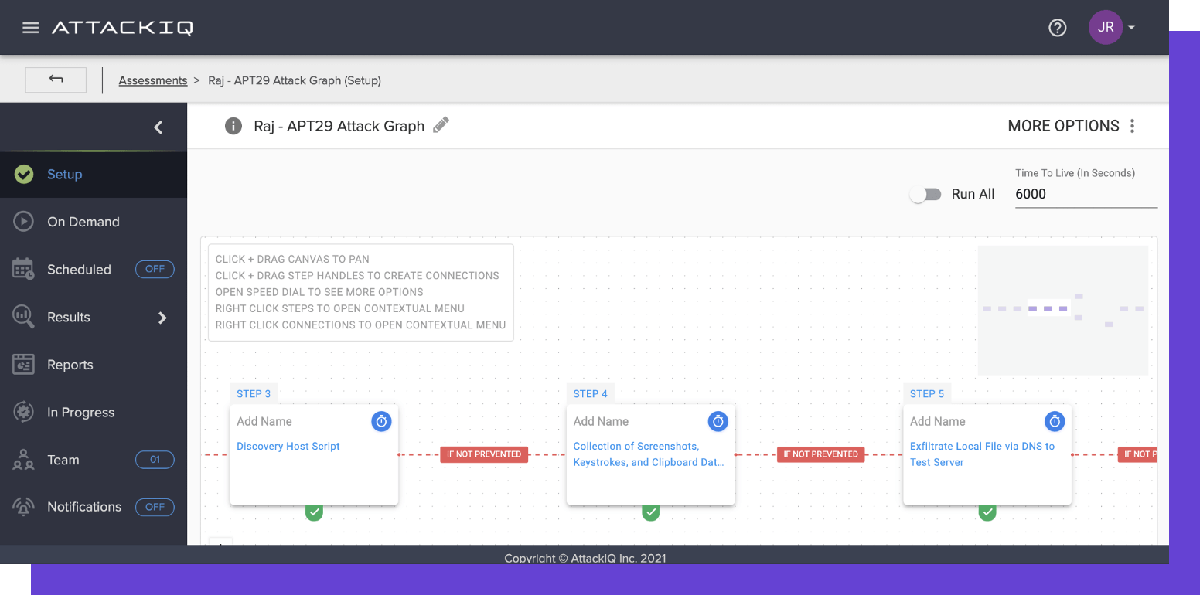
AttackIQ Features
- Integration: Integrates with various third-party solutions, including Palo Alto Networks, Splunk, Cisco, and RSA
- OS support: Supports all major operating systems, including Windows, Linux, macOS
- Flexible deployment: AttackIQ can be deployed on-premises and in the cloud
- Security posture Insight: Real-time visibility into security performance
- Cloud security: Validate native security controls embedded within cloud providers like Azure and AWS
- Risk management: Uses MITRE ATT&CK framework to validate NIST 800-53 and CMMC security controls automatically
Pros
- Support for on-premises and cloud environments
- Validates native cloud security controls
- AI/ML security validation
Cons
- Users would like to see more integrations
- Some complaints about deployment challenges
Pricing
AttackIQ does not publicly list pricing information on its website. However, they offer a free trial and a personalized online demo to help potential buyers understand their services and determine the best pricing option for their needs.
The little pricing that’s publicly available on the Azure Marketplace suggests it’s not a cheap product — AttackIQ Starter Pack Bundle: $227,500.00 one-time payment per year, or $580,125.00 one-time payment for a 3-year billing term — but users understand that they’re getting a product that goes well beyond the basics.
Note that AttackIQ Starter Pack Bundle rates are subject to change starting August 1, 2023. The updated price for the one year billing term will be $250,250 one-time payment while the 3-year billing term price will increase to a $638,138 one-time payment.

Cymulate
Best for usability and user experience
Cymulate is the first of two Israeli vendors in our top-tier BAS solutions. Founded in 2016, the Rishon LeZion-based vendor specializes in breach and attack simulation and security posture verification. By employing the MITRE ATT&CK framework and mimicking an array of advanced hacker strategies, the Cymulate platform assesses network segments, detects vulnerabilities, and optimizes remediation.
To confront the dynamic threat landscape, Cymulate offers continuous security validation that provides consistent guidance for action. Deploying Cymulate with near-unlimited attack simulations can be completed within minutes via a single lightweight agent.

Cymulate Features
- Attack remediation: Allows you to prioritize remediation based on attackable vulnerabilities
- Endpoint security: Detects and prevents endpoint ATT&CK TTPs such as ransomware and worms
- Data exfiltration: Ensures that company sensitive data can not be exfiltrated
- Full kill chain APT: Validate your enterprise defense against APT attack scenarios such as Fin8, APT38, Lazarus and custom scenarios
- Email gateway: Test your security against thousands of malicious email formats, attachments, and URLs
- Web app firewall: Evaluate your security against web apps attack such as OWASP top ten
Pros
- Users praise its resources for cyber risk assessments and penetration testing
- Easy to setup and use
- Offers instant threat alerts
- Signature and behavioral based endpoint security
Cons
- Some users reported that the scanning capability can be made better
- Adding more integration with other security tools can further improve the tool
- Reporting capability can be made better
Pricing
Pricing information for this product is unavailable on the vendor’s website. Potential buyers can contact the Cymulate sales team for custom quotes tailored to their needs. Cymulate offers a 14-day free trial, and potential buyers can also request a product demo. Publicly available pricing on AWS shows that the Cymulate 7 attack vector bundle for organizations with up to 1,000 endpoints may cost about $7,000 a month or $91,000 per year.

Picus Security
Best for detecting logs and alert gaps
Picus Security is a continuous security validation vendor founded in 2013 and located in San Francisco, California. Recognized in each of our top BAS lists, Picus has raised over $32 million through Series B and a corporate funding round by Mastercard in May 2022. The Picus Security Control Validation (SCV) platform scans for vulnerabilities and offers guidance for configuring security controls.
Integrating into an existing security information and event management (SIEM) system, the Picus SCV helps identify logging and alert gaps where additional action is required to optimize your SIEM. With MITRE ATT&CK and kill chain visibility, administrators deploying SCV can take the necessary steps to prevent the next advanced attack.
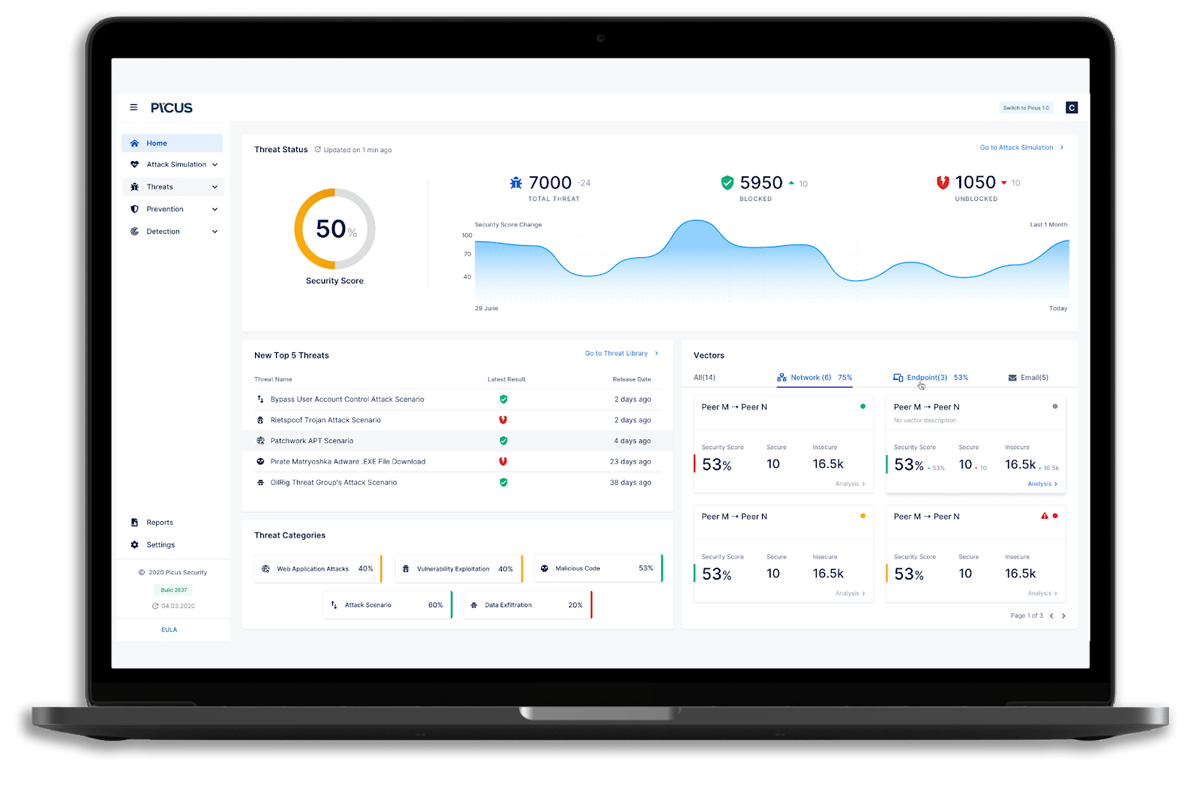
Picus Security Features
- Threat library: Picus Security’s threat library of over 3500 threats covering the MITRE ATT&CK framework is updated regularly
- Security control validation: Test the efficacy of your network security and detection controls, including firewalls, web and email gateways, SIEM, EDR, and SOAR tools
- Mitigation library: Picus Security provides over 70,000 actionable recommendations to remedy security gaps, as well as vendor-specific mitigation suggestions targeted to your environment
- Attack Path Validation (APV): Picus APV helps security teams automatically detect and visualize an evasive attacker’s path to important systems and accounts
- Integration: Picus integrates with various third-party tools, including Citrix, Cisco, IBM Security, McAfee, F5, Trend Micro and more.
Pros
- Continuous assessment
- Provides users with recommendations to further help strengthen their networks
- Automated testing
- Supports over 100 APT and malware scenarios
Cons
- Users feedbacks from review sites shows that Picus Security has a complex initial setup
- Some users say technical support are some time insufficient, product documentation can be improved to help users resolves minor issues quickly
Pricing
Picus Security does not advertise pricing on its website, as packages and services are tailored to the customer’s exact needs. Generally, prices for their services range from $30,000 to $120,000, depending on the scope of the chosen package. To receive a custom quote tailored to your needs, contact their sales team. You can also take advantage of their 14-day free trial or request a product demo.

SafeBreach
Best for integration with other security tools
SafeBreach holds multiple patents and awards for its BAS technology. Founded in 2014, the California-based vendor is a pioneer in breach simulation. Since our last update, SafeBreach earned a $53.5 million Series D funding round in November 2021. The BAS platform can detect infiltration, lateral movement, and data exfiltration by offering cloud, network, and endpoint simulators.
SafeBreach continuously validates tools and the organization’s overall security posture with an ever-changing threat landscape. When flagged, administrators have the visibility to take prompt action against potential vulnerabilities. With the SafeBreach platform deployed, organizations can expect increased security control effectiveness, real threat emulation, and improved cloud security.

SafeBreach Features
- Integration: SafeBreach integrates with various technology solution providers, including Splunk, ServiceNow, Google BigQuery, Tanium, Checkpoint, IBM, Slack, Qualys and more
- Reporting: Provides real time reporting and remediation action
- SafeBreach-as-a-Service: SafeBreach is available as a fully managed software solution consisting of platform licensing, ongoing strategy, and full support
- RansomwareRx: Allows users to run a customized, no-cost attack scenario based on actual ransomware behavior—including MITRE ATT&CK TTPs
- No-code: Allows users to plan every aspect of attack in a single no-code environment
Pros
- Ability to simulate over 15,000 attacks
- Dashboards display security risks over time
- Offers cloud, network, and endpoint simulators
Cons
- Customer support can be made better. Users reported slow response time
- User interface takes time to learn and get use to
Pricing
SafeBreach doesn’t advertise prices on its website. Interested buyers can contact its sales team for custom quotes. You can also request a free demo to learn how to leverage the product for your environment. Publicly available pricing on AWS shows that SafeBreach simulator can cost about $18,000 for an annual subscription.

XM Cyber
Best for attack path management
XM Cyber is a Tel Aviv-based cyber risk analytics and cloud security vendor launched in 2016. Born from the thought leadership of the Israeli intelligence sector, the XM Cyber Breach and Attack Simulation, previously known as HaXM, is a leading BAS solution. In its short history, the vendor has been at the forefront of BAS innovation, winning several awards and pushing other vendors forward.
XM Cyber identifies an organization’s most critical assets and works backward with attack-centric exposure prioritization, identifying the exploit routes. Analyzing every potential attack path and crafting remediation options informed by risk impact give administrators visibility in real-time to secure their network. Through its success, XM Cyber was acquired for $700 million by the Schwarz Group in November 2021.
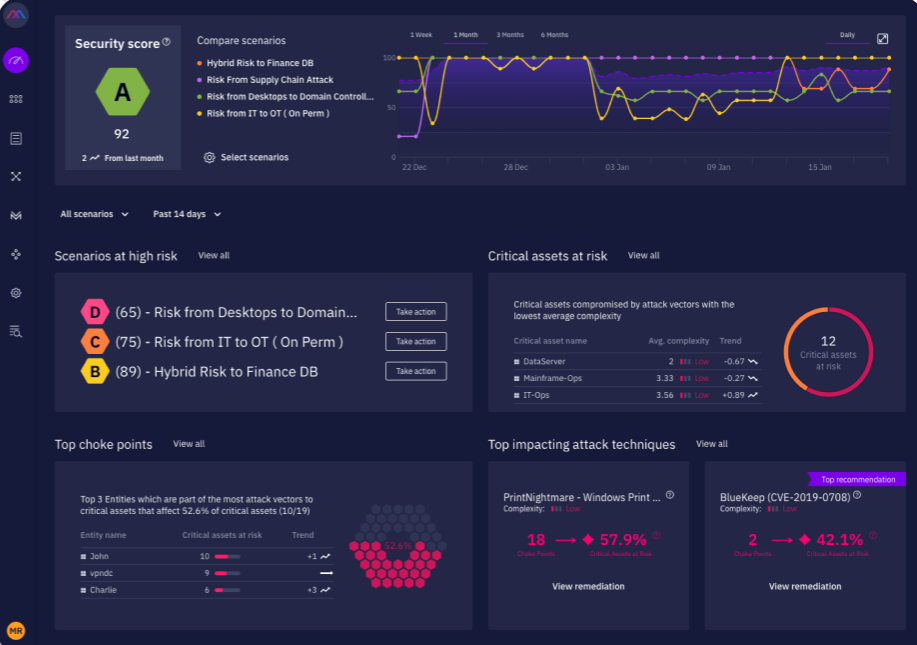
XM Cyber Features
- Flexible: Allows organizations to prioritize security exposures and focus remediation activities across cloud, SaaS and on-premises
- Compliance validation: Automate compliance validation and reporting for key standards such as ISO, NIST, GDPR, SWIFT and PCI
- Attack path management: APM allows users to detect attacks before they happen proactively
- Hybrid cloud security: Identify exposures across your AWS, Azure and GCP environments
- Active Directory security: Neutralize Active Directory risks across on-premises and cloud environments
- Automated red teaming and penetration testing: Provides real-time evaluation of your security tools’ performance and uses attack modeling to reveal misconfigurations, mismanaged credentials, and risky user activity
Pros
- Track users’ overall security posture and risk level
- Advance analytics capability
- End-to-end network scanning
- Provides users with visibility into their critical attack paths
Cons
- Users report that the tool is expensive, making it hard for small businesses to buy
- The customer support can be improved and optimized for fast response time
Pricing
This is a quote-based tool, and the price is available on request. Contact XM Cyber for custom quotes. You can also request a personalized demo to learn more about the solution. AWS Marketplace shows pricing for XM Cyber’s hybrid attack simulation for up to 1,000 assets cost about $7,500 per month or $90,000 per year, while its next-generation vulnerability management costs about $1,083 per month or $13,000 per year for up to 1000 assets.
Read more on security automation:
- Hyperautomation and the Future of Cybersecurity
- Top Security Orchestration, Automation and Response (SOAR) Solutions
- Vulnerability Management as a Service (VMaaS): Ultimate Guide

CyCognito
Best BAS tool for risk detection and prioritization
CyCognito is committed to exposing shadow risk and bringing advanced threats into view. One of the youngest BAS vendors started operations in 2017 and resides in Palo Alto, California. Founded by tenured national intelligence professionals, CyCognito identifies attacker-exposed assets to enhance visibility into the attack and protect surfaces.
According to the vendor, clients identify up to 300% more assets than they knew existed on their network. Through the CyCognito platform, organizations can define risk categories, automate offensive cybersecurity operations, and prepare for any subsequent advanced attack. The budding vendor continues to grow with a Series D of $100 million in December 2021.

CyCognito Features
- Graph business and asset relationships: The CyCognito platform leverages machine learning, natural language processing, and graph data structure to uncover and consolidate all corporate relationships in your organization, from acquired companies to joint endeavors and cloud infrastructures.
- Test security: CyCognito testing capabilities detect attack vectors that could be used to breach enterprise assets, including data exposures, misconfigurations and even zero-day vulnerabilities.
- Risks prioritization: CyCognito automatically prioritizes risks based on the following principles
- Attackers’ priorities
- Business context
- Discoverability
- Ease of exploitation
- Remediation complexity
- Integration: The platform integrates with SIEMs, ITSM, CMDBs, and communications software.
- Security framework: CyCognito satisfies most common security frameworks such as MITRE ATT&CK Framework, NIST cybersecurity framework, CIS critical security controls and ISO/IEC 27000 and regulatory compliance standards, including GDPR, NIST 800-53, CCPA, PIPEDA, BDSG and POPI act.
Pros
- Supports cloud and on-premises environments
- Attack surface management
- Advanced analytics
Cons
- CyCognito is difficult to learn and use, new users need extensive training to understand the tool
Pricing
Product pricing is available on request. Contact the CyCognito sales team for custom quotes. For its attack surface management product, data from AWS marketplace shows a cost of $30,000 for 12 months, $55,000 for 24 months, and $80,000 for 36 months – limited to 250 assets max.

FireMon
Best BAS tool for visualization
Started in 2001, FireMon is a Kansas-based vendor for cybersecurity, compliance, and risk mitigation. One of the earliest companies to address change detection and reporting, compliance, and behavioral analysis, FireMon has a track record that includes over 1,700 organizations. FireMon’s vulnerability management technology can be found under Security Manager and Cloud Defense, offering real-time risk assessment, mitigation and validation. FireMon’s attack path graphics and analysis are suitable for administrators who desire greater visibility.
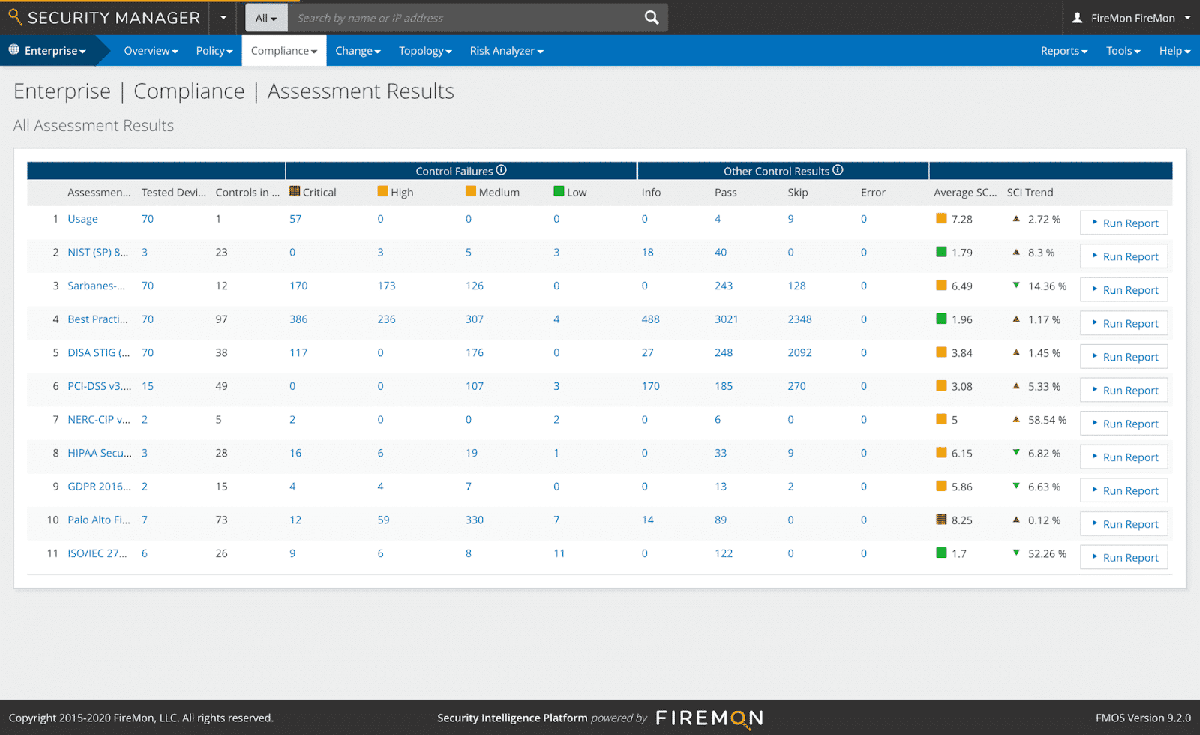
FireMon Features
- Integrations: FireMon integrates with a range of technologies, including ITSM tools (ServiceNow, Accenture, Jira Software, Redseal and BMC), SIEM/SOAR solutions (Splunk, Komand, Demisto and Swimlane), and vulnerability scanners (Qualys, Rapid7, and Tenable)
- Optimize response: Real-time event analysis and intelligent routing of high-priority events
- Notification: Send alerts directly using existing tools, including Slack, Teams, and Jira
- Compliance: Support for common compliance standards, including CIS and PCI-DSS
- Visualization: Comprehensive reporting and dashboards
- Automatic enforcement: Adhere to security requirements from CIS, NIST and AWS, and implement monitoring/logging, IAM, and backup across all cloud accounts and providers
Pros
- Intuitive user interface
- Users find its historical log capability beneficial
- Tracks firewall rule change
- Easily identify misconfigurations
Cons
- Customer support and documentation could be improved
- Complex initial setup, which leads to slow implementation time
Pricing
FireMon does not publicly disclose pricing information. In addition to custom quotes, you can also request a demo to learn more about the platform. FireMon also offers bring your own license (BYOL) plans for Azure and AWS.

Akamai Guardicore
Best for micro-segmentation and enhanced visibility and control
A decade into a maturing zero trust solution space, Guardicore has been an upstart microsegmentation company addressing security for assets across hybrid environments. The Tel Aviv-based company was acquired by Akamai in September 2021 for $600 million.
For BAS, Akamai Guardicore’s open source platform Infection Monkey offers continuous testing and reports on network performance against attacker behavior. On par or better than some proprietary solutions, Infection Monkey is environment agnostic, handles varying network sizes, and offers analysis reports based on zero trust, ATT&CK MITRE, and BAS.
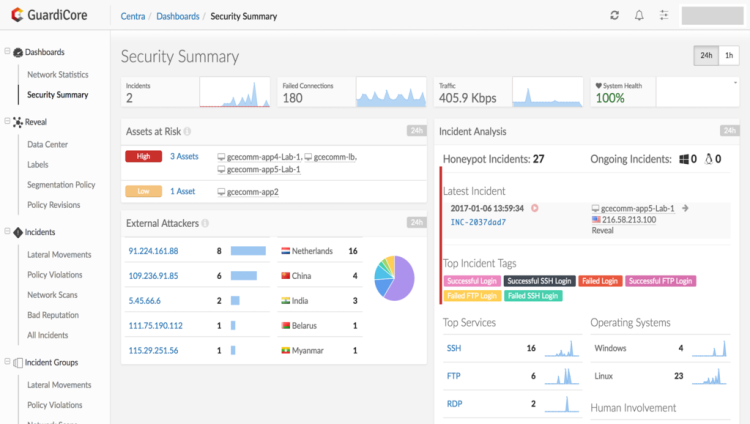
Guardicore Features
- Legacy system support: Support legacy systems such as Windows 2003, CentOS 6, RHEL5, and AS400
- AI-powered segmentation: Implement AI-recommended policies with templates to address ransomware and workload attributes like processes, users, and domain names
- Broad platform support: Support modern and legacy OSes across bare-metal servers, virtual machines, containers, IoT, and cloud instances
- Integrations: The platform integrates with third-party solutions such as CyberArk, Duo, Okta, Google Cloud Platform, Microsoft Azure, Oracle, AWS, Cisco, Check Point and more
- Flexible deployment: Secure IT infrastructure with a mix of on-premises workloads, virtual machines, legacy systems, containers and orchestration, public/private cloud instances, and IoT/OT
Pros
- Users can create audit reports
- Support for on-premises, container, and cloud environments
- Free open source version available
Cons
- The search and filtering capabilities can be improved to help users easy concatenate fields
- The Guardicore central user interface can be improved to enhance navigation
Pricing
Akamai Guardicore’s Infection Monkey can be downloaded for free, while cloud users would need to pay infrastructure costs.

Mandiant
Best BAS tool for threat intelligence
In our first BAS update, Virginia-based startup Verodin made the list before its acquisition by FireEye in 2019. Integrated into the Mandiant Security Validation platform, Mandiant — now part of Google — continues to lead the way through an eventful few years.
With integrated threat intelligence, automated environmental drift detection, and support for optimizing existing cybersecurity tools like SIEM, Mandiant eases a client’s monitoring job to focus on taking action. Mandiant notes clients can save big financially in the form of controlled vulnerabilities and speed response time to advance TTP by almost 600%.
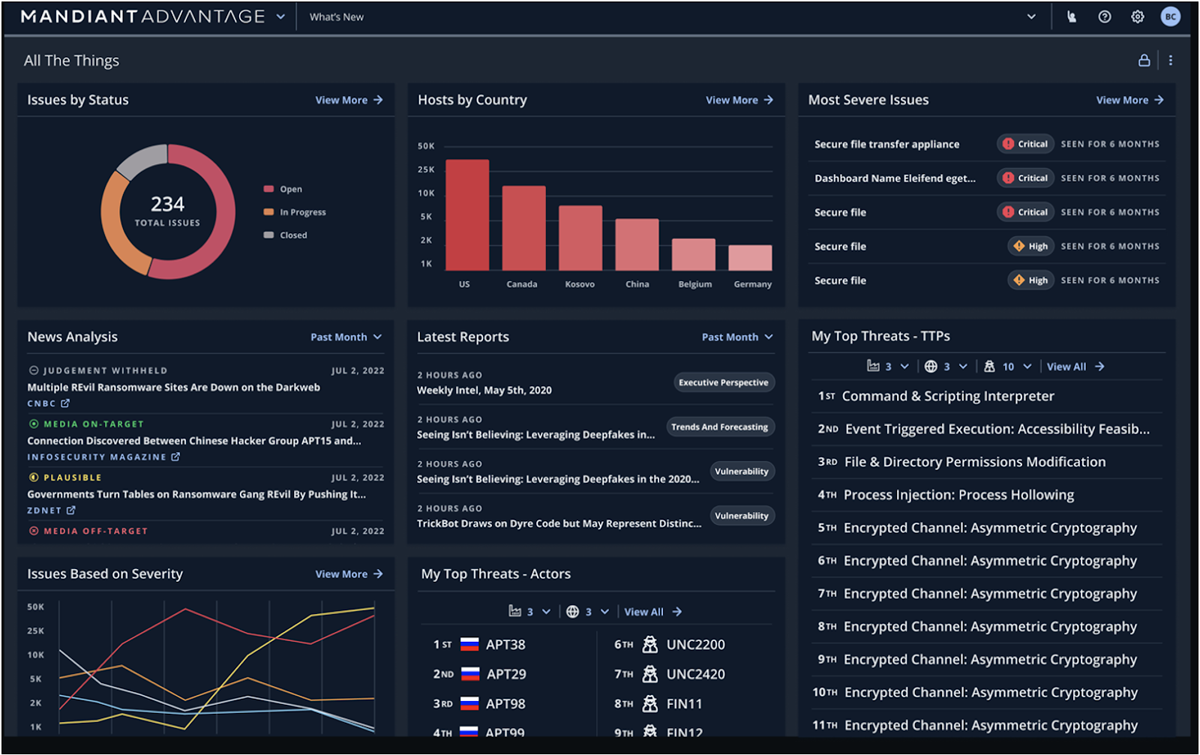
Mandiant Features
- Breach analytics: Continuously monitors an organization’s real-time and historic threat alert data to identify and prioritize indicators of compromise (IOCs) present in their environment
- Security validation: Provides security teams with real data on how security controls behave under attack
- Visibility into external exposure: Identify unknown or unmanaged vulnerable internet-facing assets
- Attack surface management: The platform allows organizations to identify unsanctioned resources, digital supply chain monitoring and assess high-velocity exploit impact
- Digital threat monitoring: Provides visibility into the open, deep and dark web
Pros
- Automated defense
- Security validation and threat intelligence
- Flexible deployment
Cons
- Mandiant customer support response time can be improved for fast issues resolution
- Users report that the on-premises client is too processor-intensive
Pricing
Mandiant doesn’t publish pricing information for Security Validation, but CDW offers pricing info on a range of Mandiant Verodin offerings.

Qualys
Best BAS tool for vulnerability management and security compliance
Qualys is a leading provider of cloud security and compliance solutions – and one of the older vendors to make our list, founded in 1999 in San Francisco. The Qualys Vulnerability Management, Detection, and Response (VMDR) platform is their most popular product and a top BAS solution.
From analyzing vulnerabilities with six sigma accuracy to identifying known and unknown network assets, Qualys VMDR is a comprehensive solution that’s fully cloud-based, and the vendor offers a set of features and several add-ons for organizations requiring more. Those include mobile device support, cloud security assessments, and container runtime security.
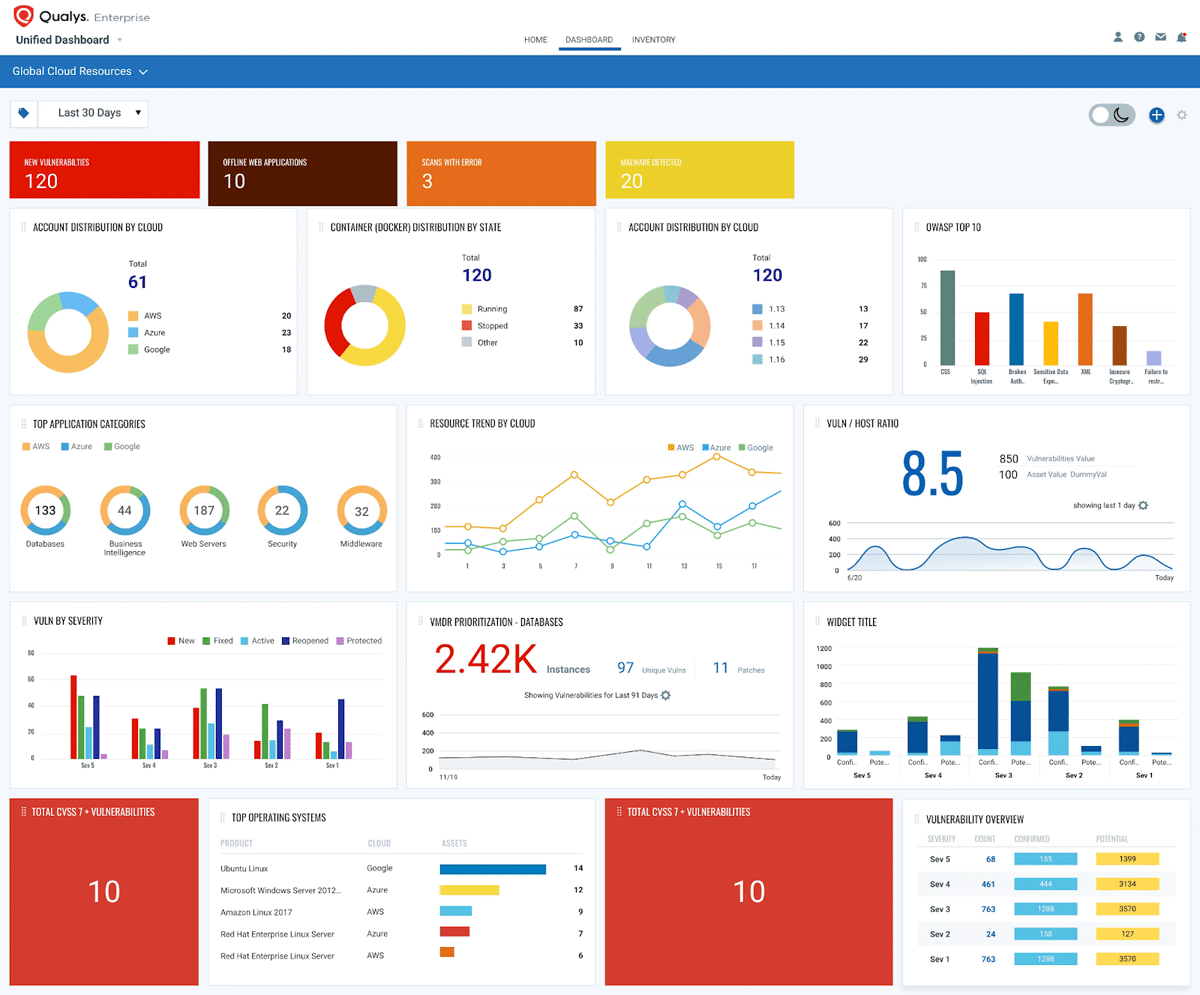
Qualys Features
- Asset monitoring: Automatically identifies all known and unknown assets, on-premises, endpoints, clouds, containers, mobile, operational technology, and IoT, to generate a comprehensive, categorized inventory.
- Prioritize remediation: Qualys offers real-time threat information and asset inventory correlation to give you an overview of your threats.
- Validate file integrity: Qualys’ FIV solution monitors OSes continuously, logging and managing events centrally, and correlating and tracking changes.
- Systems monitoring: Qualys collects IoC data from your assets and stores, processes, indexes and analyzes it.
- Detects critical vulnerabilities, malware, exploits and misconfigurations.
Pros
- Integrates with ITSM tools like Jira and ServiceNow
- Automates remediation with no-code workflows
- Customizable dashboard
- Straightforward initial setup
Cons
- Users report that the tool’s remediation module can be complex
- The tool is pricey, making it unaffordable for many small businesses
Pricing
Qualys offers a free trial of their cloud platform for 30 days, after which pricing depends on the type of subscription and the specific services required. The company offers solutions for small businesses, mid-market, and enterprise environments. You can contact Qualys directly for more information on pricing.
Publicly available pricing shows that Qualys VMDR starts at $542 per month or $5,422 per year for 128 hosts.

IBM Randori
Best BAS tool for red teaming
A part of the budding attack surface management (ASM) solution market, Randori was one of the top cybersecurity startups before its acquisition by IBM in June 2022. Launched in Waltham, Massachusetts in 2018, Randori’s black-box approach maps attack surfaces to identify and prioritize an organization’s most valuable targets.
Whether it’s continuous automated red teaming (CART), preparing for zero-day attacks, or inspecting shadow IT, the Randori Platform offers robust insights into the cyber kill chain. Organizations can test their managed detection and response (MDR), managed security service provider (MSSP), and Security Operations Center (SOC) capabilities, as well as the effectiveness of tools like SIEM, SOAR, and EDR.

Randori Features
- Detect shadow IT: The platform helps identify forgotten assets, blind spots, and process failures.
- Notification: Randori provides alerts on new vulnerabilities and misconfigurations, such as unauthenticated services, pages with outdated copyright and new applications with poor quality.
- Continuous and automated red team: Randori helps organizations Prioritize investments in security tools by assessing the risks in your people, process and technology with regard to opportunistic, social, and zero-day attacks.
- Validate security investments: Randori helps organizations validate the efficacy of their SIEM, EDR, SOAR, threat intelligence, and MDR partners.
Pros
- Continuous automated red teaming
- Shadow IT discovery
- Attack surface management
Cons
- Steep learning curve for new users. The interface can also be improved to help users more easily navigate the platform.
Pricing
Randori doesn’t advertise product pricing on its website. Potential buyers can request product demos and pricing details by filling out a short form on their website.

Rapid7
Best BAS tool for affordability and risks analysis
Rapid7 kicked off operations in 2000, and fifteen years later released the Insight platform, bringing together vulnerability research, exploit knowledge, attacker behavior, and real-time reporting for network administrators.
Rapid7’s BAS solution is InsightVM and comes with an easy-to-use dashboard, where clients can manage everything from risk prioritization and automated containment to integrated threat intelligence feeds. Rapid7’s goal is to make cyber risk management seamless, with features devoted to remediation and attack surface monitoring.

Rapid7 Features
- Lightweight endpoint agent: Automates data collection from all your endpoints, including those from remote workers.
- Live dashboards: InsightVM dashboards are not static, they are interactive and allow you to create custom cards for admins or CISOs.
- Real risk prioritization: Leverage InsightVM real risks score to prioritize threats based on their severity and potential impact automatically.
- IT-integrated remediation projects: Streamline the process of responding to threats by integrating InsightVM with IT’s ticketing systems.
- Cloud and virtual infrastructure assessment: The platform integrates with cloud services and virtual infrastructure to ensure your technology is configured securely.
- Attack surface monitoring with project sonar: Continually scan your attack surface for vulnerabilities and misconfigurations to identify risks before they can be exploited.
- Container security: Monitor container workloads and external images for vulnerabilities and compliance issues in an automated, integrated fashion. Organizations can integrate InsightVM with CI/CD tools, public container repositories, and private repositories.
- RESTful API: Quickly integrate Rapid7 solutions with your existing security tools and processes via API.
Pros
- Transparent pricing
- Risk scoring based on attacker analytics
- Integrated threat feeds
- Live dashboard
- Good value
Cons
- Users say that the reporting is only available with direct access to the console, meaning a user needs access to the local server or VM instance to pull the reports
- Users say scan engine management is difficult
Pricing
Rapid7 InsightVM pricing is based on the number of assets being managed. Buyers looking to cover their entire network can contact the Rapid7 sales team for custom quotes and enjoy volume-based discounts.
- 250 assets: $2.19 per asset per month ($26.25 per year)
- 500 assets: $1.93 per asset per month ($23.18 per year)
- 750 assets: $1.79 per asset per month ($21.43 per year)
- 1000 assets: $1.71 per asset per month ($20.54 per year)
- 1250 plus assets: $1.62 per asset per month ($19.43 per year)

BreachLock
Best BAS tool for network and web penetration testing
Launched in early 2019, BreachLock is a top BAS company focused on penetration testing as a service (PTaaS). While relatively new, the New York City startup already has a growing reputation.
The on-demand SaaS solution offers testing for servers, IoT devices, APIs, mobile and web apps, and cloud infrastructure to give clients end-to-end visibility of exposure to risk.
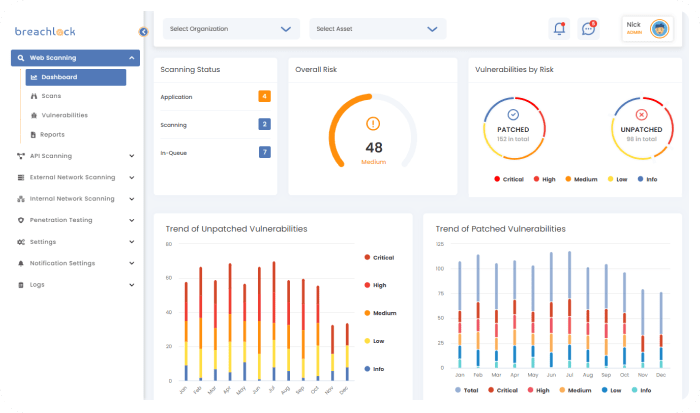
BreachLock Features
- Vendor security assessment: BreachLock validates mobile and web applications, APIs, external and internal networks, cloud environments, and IoT.
- Cloud penetration testing services: The platform experts can test your cloud security in AWS cloud, GCP cloud, and Azure cloud, cloud technology, cloud platforms, and cloud-hosted SaaS applications.
- Network penetration testing: BreachLock experts manually test your external and internal networks.
- Web application penetration testing: Users’ web applications will be manually tested by the BreachLock team for OWASP and business logic security flaws.
Pros
- Efficient support team
- Vulnerability scanning
- Online and offline reporting
Cons
- The GUI could use a facelift to be more intuitive
- Users says they find the documentation confusing
Pricing
This is a quote-based solution. Contact the BreachLock sales team for custom quotes.

Horizon3.ai
Best BAS tool for startups and small businesses
Another top cybersecurity startup, Horizon3.ai also offers a cloud-based BAS solution with its autonomous penetration testing as a service (APTaaS), NodeZero.
Across hybrid IT environments, NodeZero identifies internal and external attack vectors and verifies the effectiveness of security tools and remediations. Started in October 2019, the San Francisco-based company most recently earned a $30 million Series B in October 2021.
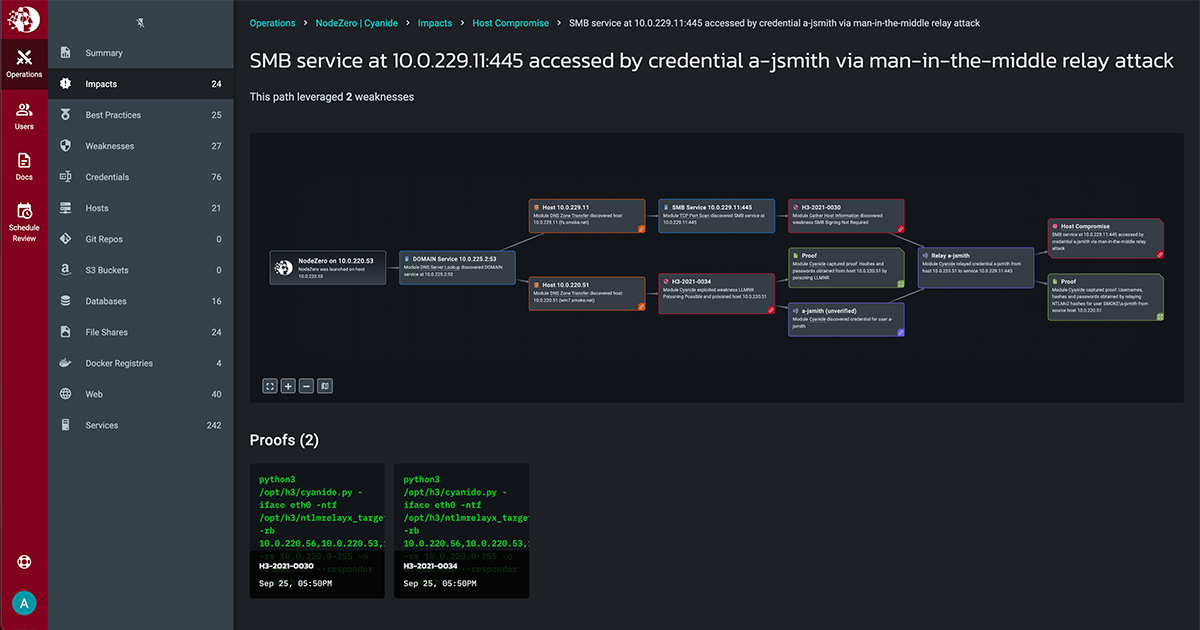
Horizon3.ai Features
- Availability: The solution is available 24/7, allowing organizations to continuously evaluate their security posture and proactively identify and remediate attack vectors.
- Attack surface management: Provides coverage for internal and external attack vectors on-premises, in the cloud or in hybrid environments.
- Monitor attack path: NodeZero helps users understand the attack vectors that lead to a critical breach to mitigate attacks.
- Coverage: NodeZero algorithm fingerprints external, on-premises, IoT, identity, and cloud attack surfaces.
Pros
- Scalable
- Easy to use and helpful support team
Cons
- Some users find the tool cost-prohibitive
- Users say the tool lacks automated testing capabilities, whch means they can’t run tests on schedule
Pricing
Although Horizon3.ai doesn’t advertise pricing on its website, they offer a 30-day free trial and custom pricing for users. Enterprise users can contact the company for a tailored quote. Additionally, buyers can request product demos for more information about the solution. Publicly available pricing shows that Horizon3.ai pricing may range from about $24,999 per year to $327,467 per year.

NetSPI
Best BAS tool for pen testers
Founded in 2001, NetSPI has a track record of delivering pen testing to the top cloud providers, healthcare companies, banks, and more.
The Minneapolis, Minnesota-based company’s PTaaS, Resolve, offers clients an orchestration platform to manage the lifecycle of vulnerabilities. With two-way synchronization with tools like ServiceNow and Jira, Resolve can reduce time to remediation.
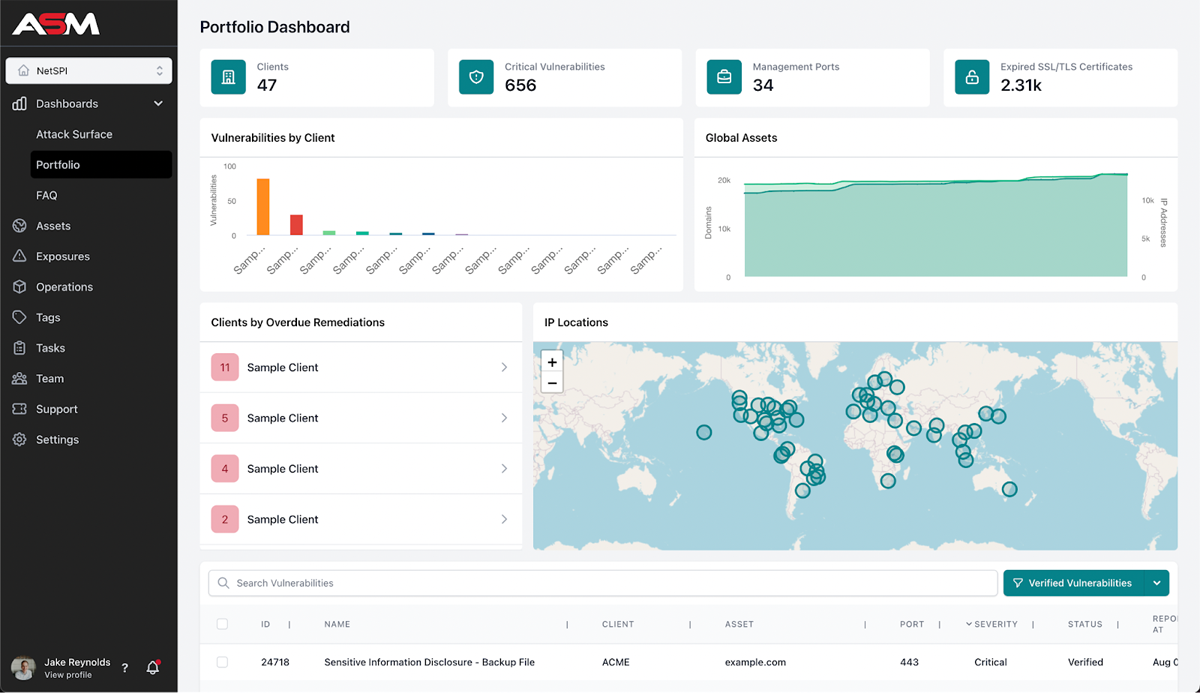
NetSPI Features
- Identify detection gaps: NetSPI identifies detection gaps such as missing data sources, disabled and misconfigured controls, broken telemetry flows, incomplete coverage and kill chain gaps.
- Validate controls: The platform validates controls, including endpoint controls, network controls, Active Directory controls, SIEM capabilities and MSSP capabilities.
- MITRE ATT&CK simulation: The platform helps organizations stay resilient against the attacks listed in the MITRE ATT&CK framework.
- Attack surface management: NetSPI detects known and unknown potential vulnerabilities of public-facing assets.
Pros
- Detects misconfigured controls
- Customizable solution
- Extensive testing services
Cons
- Can be expensive, particularly for smaller organizations or those with limited budgets
Pricing
NetSPI is a quote-based tool. Potential buyers can contact the sales team for custom quotes. They can also request a demo to better understand the platform. You can also visit AWS Marketplace to subscribe to this solution.

Pentera
Best BAS tool for automated security validation
Formerly known as Pcysys, Pentera has emerged as another top BAS solution in a field that has attracted a number of Israeli security startups.
Started in 2015, the Pentera Automated Security Validation (ASV) Platform inspects internal and external attack surfaces to emulate the latest threat behavior. With a Series C round worth $150 million in January 2022, Pentera has the resources to continue growing.

Pentera Features
- Continuous validation: The platform validates an organization’s security programs, such as defense controls, security policies, password configurations, and critical assets in near-real time.
- Agentless: Pentera is a fully automated platform that provides immediate discovery and exposure validation across a distributed network infrastructure.
- Model attacker behavior: Pentera enables security teams to emulate malicious actors, providing insights needed for anticipating and preventing an attack.
- Prioritize remediation: The platform generates a risk-based remediation roadmap with a focus on high-priority systems.
- Attack surface management: Detect known and unknown exposures, external and internal, to identify attacker’s most attractive target.
Pros
- Remediation priority capability
- Easy to deploy and intuitive
- Efficient technical support
- Offers different testing scenarios, including black box, gray box, targeted test, and AD strength assessment tests
Cons
- Users reported difficulty understanding the documentation
- Some users say the scheduler is not flexible
Pricing
Pentera does not publicly disclose pricing information. However, they do offer a free demo of their software, which could be requested by contacting their sales team. Contact the vendor for a custom quote.

Scythe
Best BAS tool for real-world adversary emulation campaigns
Launched in 2018, Scythe is an adversary emulation platform offering services for red, blue, and purple teams to optimize visibility into risk exposure.
Available as a SaaS or on-premises solution, the Virginia-based startup also offers developer-friendly clients a software development kit to create custom validation modules in Python or native code.
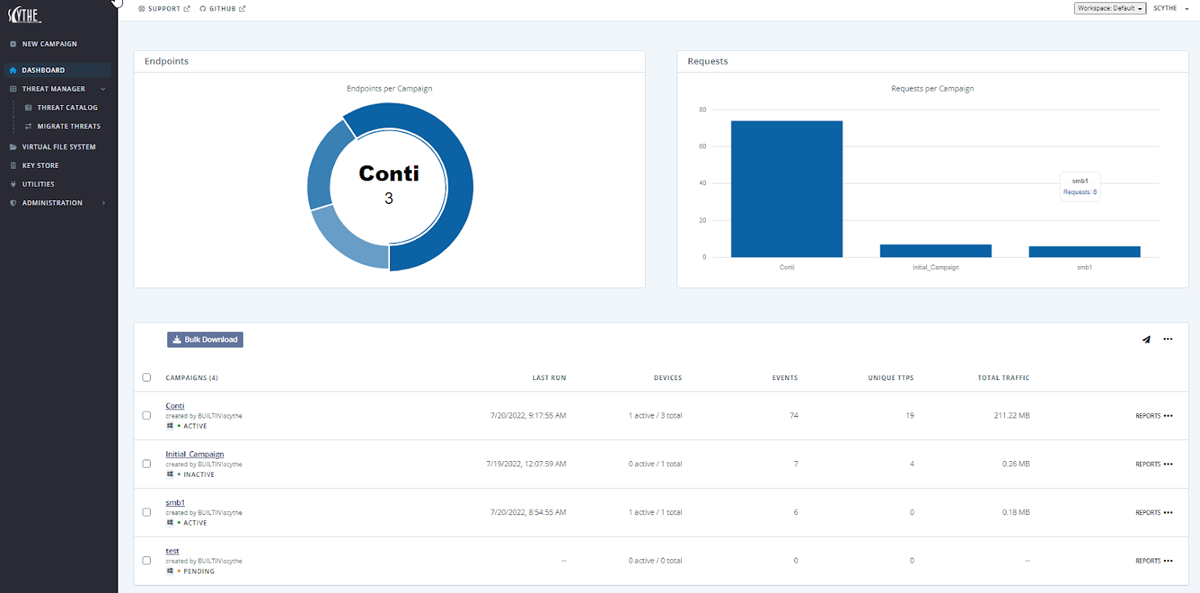
Scythe Features
- Visibility: The platform offers real time visibility of “real-world risk posture and exposure.”
- Prioritize remediation: Scythe prioritizes vulnerabilities to focus on the highest-risk issues.
- Threat library: Scythe’s public threat library helps organizations be prepared for both known and unknown threats.
- Reports: The platform allows users to customize reports. Scythe also offers insights and prioritized recommendations to help users remediate critical issues quickly.
Pros
- Customizable tool
- Supports red, blue, and purple teams
- Increases detection and reduces response times
Cons
- Training is limited to live online and documentation
- Lacks integration with Check Point IPS and Infinity
Pricing
Scythe serves enterprises, consultants and managed service providers. Their price is tailored to the customer’s needs and requirements. To get a quote, you will need to contact their sales team, and you can also request a demo to gain a better understanding of the product.

Skybox Security
Best BAS tool for integration with data sources
Twenty years after its founding, Skybox Security’s stack of products include threat intelligence, vulnerability control, network assurance, change management, and firewall assurance to form the Security Posture Management Platform.
Alongside a robust set of integrations, Skybox offers organizations visibility into IT and OT infrastructure, path analysis, and risk scoring.
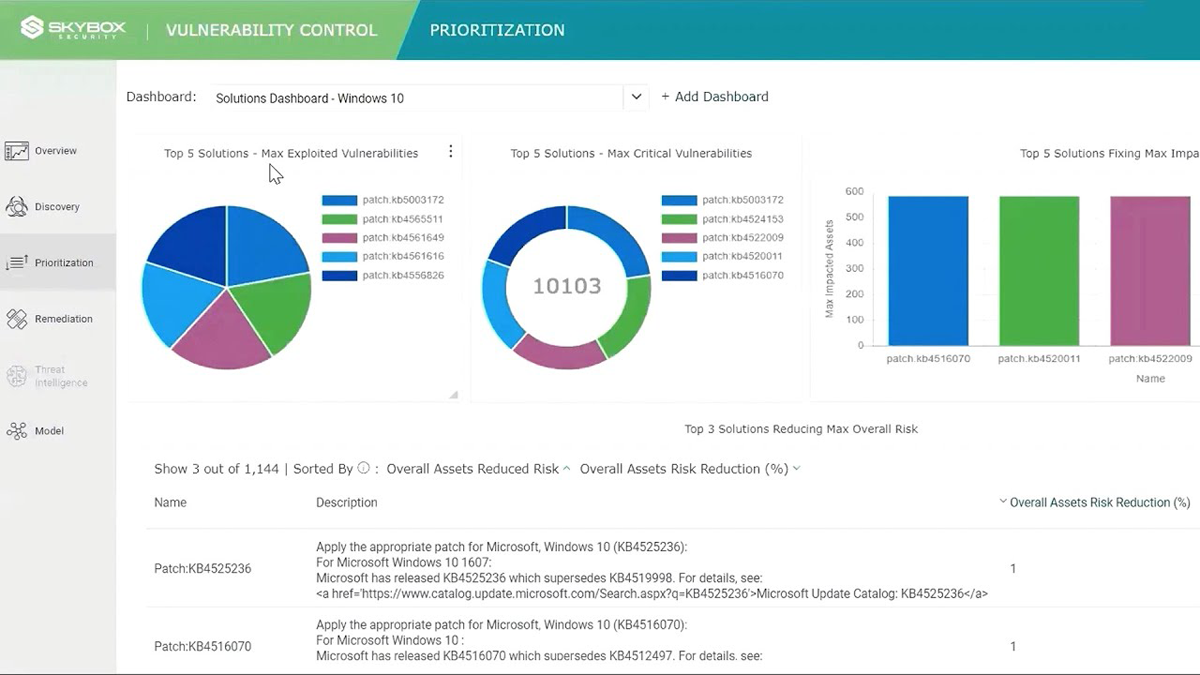
Skybox Security Features
- Vulnerability discovery: The platform allows organizations to gather, aggregate, and normalize data from scanners, EDR, CMBDs, security controls, network technologies, OT assets, and Skybox threat intelligence.
- Vulnerability assessment and prioritization: Assess and prioritize remediation with precise risk scores (CVSS, exploitability, importance, exposure).
- Rule optimization: Conduct analysis, optimize, and audit firewall rules; remove redundant, shadowed, or overly permissive rules.
- Context-aware change management: Gain visibility, assess rule and policy changes, spot misconfigurations, and identify potential vulnerability exposures.
Pros
- Attack surface visibility
- Path analysis and risk scoring capability
- Extensive integration with third-party services
Cons
- Some challenges with customized reports
- Technical support could be more responsive
Pricing
Skybox Security does not list pricing. To obtain pricing information, customers must contact the company directly. It’s also available on Azure.

Tenable
Best BAS tool for analytics and attack surface visibility
A longtime leader in vulnerability management, Tenable continues to look to the future of cyber exposure management while organizations undergo digital transformation.
Started in 2002, the Columbia, Maryland-based cybersecurity vendor’s portfolio includes solutions for ransomware, zero trust, application security, and a range of compliance and security frameworks.
Tenable Features
- Visibility: Provides a unified view of all enterprise assets and associated software vulnerabilities, configuration vulnerabilities and entitlement vulnerabilities, whether on-premises or in the cloud, to identify risk exposure.
- Predict and prioritize: Protects organizations against cyber attacks.
- Eliminate attack paths: Maps critical risks to the MITRE ATT&CK framework to visualize all possible attack paths on-premises and in the cloud.
- Comprehensive asset inventory: The platform provides comprehensive visibility into an organization’s assets and exposures (vulnerability management, web app security, cloud security and active directory security).
Pros
- Transparent pricing
- Attack surface management
- Attack path analysis
- About 500 prebuilt scanning policies
Cons
- Users report that the vulnerability scanning engine has high false positives and negatives
- Users say Tenable support response could be quicker
Pricing
Tenable offers four pricing plans. They include:
Nessus Professional
- 1 Year – $3,644.25
- 2 Years – $7,106.29
- 3 Years – $10,386.11
Nessus Expert
- 1 Year – Promotional price: $5,364.25 (Actual price $8,051.75)
- 2 Years – Promotional price: $10,460.29 (Actual price $15,700.91)
- 3 Years – Promotional price: $15,288.11 (Actual price $22,947.49)
Tenable Vulnerability Management
Pricing for this plan depends on the number of assets. They rates below are for 65 assets (minimum number of assets supported for this plan)
- 1 Year – $2,934.75
- 2 Years – $5,722.76
- 3 Years – $8,364.04
Tenable Web App Scanning
- 5 FQDNs – $3,846.35
Add-ons
- Advanced Support: $430 (24×365 access to phone, email, community, and chat support)
- On-Demand Training: $268.75 (1 year access to the Nessus Fundamentals On-Demand Video Course for 1 person)
Honorable Mention BAS Solutions
With so many options out there, it can be difficult to know which BAS vendor is right for you. The following companies offer a range of features and capabilities that make them viable options for organizations looking for comprehensive security defense.
Aujas
Aujas services include identity and access management, risk advisory, security verification, security engineering, managed detection and response, and cloud security.
Detectify
Detectify is a security solution designed to help AppSec and ProdSec teams protect their external attack surfaces. Their core products include surface monitoring and application scanning. Detectify solution can be used for attack surface protection and other uses.
DXC Technology
DXC Technology is a Fortune 500 global IT services provider headquartered in Ashburn, Virginia. It was formed in 2017 by the merger of the former Hewlett Packard Enterprise’s Enterprise Services business and Computer Sciences Corporation (CSC). Its services include technology consulting, cloud and mobility solutions, application services, and business process services.
Foreseeti
Foreseeti is an automated cybersecurity risk management platform that helps organizations reduce their cyber risk and improve their security posture. Foreseeti enables organizations to quickly identify security gaps, prioritize cyber risks and create action plans to reduce those risks.
Keysight
Keysight BAS platform enables organizations to simulate cyber attacks and rapidly detect, respond and remediate threats. The platform provides a comprehensive view of the security posture of an organization, enabling customers to assess their level of risk and reduce their attack surface. Keysight achieves this via its security solutions, including Threat Simulator, ThreatARMOR and Security Operations Suite.
NeSSi2
NeSSi2 (Network Security Simulator) is an open source tool for network security simulation. NeSSi2 includes a graphical user interface and a library of components that can be used to build, configure, and monitor simulations.
NopSec
NopSec is an enterprise cyber security platform that helps organizations discover and manage vulnerabilities, detect and respond to threats, and automate security operations. It provides a comprehensive cybersecurity platform with a wide range of capabilities, including vulnerability management, risk simulation and attack, threat detection and response, and security automation.
ReliaQuest
GreyMatter Verify is ReliaQuest‘s BAS platform. It allows security operations teams to simulate breaches and identify gaps in their security posture.
What is Breach & Attack Simulation Software?
Breach and attack simulation solutions go beyond vulnerability assessments, penetration testing, and red teaming by offering automated and advanced breach simulation.
To test the strength of network security, organizations must put themselves in the shoes (or hoodies) of malicious actors. Security teams lean on existing threat intelligence, outsource system auditing to cybersecurity firms, and pray they fend off the next advanced attack. As a software, hardware, cloud, or hybrid solution, BAS offers the latest in automated vulnerability management, risk analysis, and network testing.

Featured PartnersFeatured Cybersecurity Software
eSecurity Planet may receive a commission from merchants for referrals from this website
Why Do Companies Use BAS?
Malicious attacks and advanced persistent threats (APTs) pose a constant risk to SMBs and enterprise organizations. In response to the ever-evolving nature of threats, several security tools have evolved to address rapidly changing threats, among them vulnerability assessments, penetration testing, red teaming, and breach and attack simulation.
Without disrupting business continuity, these methods can test attacks and other malicious activities and provide valuable insight into defensive needs.
While pentests can take as much as a couple of weeks, red team assessments typically last 3-4 months. Those human tests yield important insights, but they’re expensive. To augment those practices, BAS offers an around-the-clock automated solution.
BAS Features
Given the wide range of breach and attack simulation tools, features can vary, but a few in particular help to automate vulnerability management.
APT Simulation
Breach and attack simulators assess and verify the most recent and advanced tactics, techniques, and practices (TTP) circulating the globe.
Advanced persistent threats, in particular, are daunting to organizations due to social engineering, zero-day vulnerabilities, and an incredible capacity to go unnoticed and undetected. No tool is guaranteed to stop every attack. Still, a BAS system can make APT attacks harder by detecting zero-day vulnerabilities and identifying potential attack routes for malicious actors moving through a network.
Automated vs. Manual
For penetration testing, red teaming, or in-house security audits, organizations and third-party security contractors are responsible for manually designing and executing each passthrough. Whether the scan was targeting a critical asset or doing a vulnerability assessment of the entire network, manual network testing is resource-intensive and expensive.
BAS solutions have the technological prowess to augment these tests by automating the deployment of custom scans and attacks pertinent to the specific network, informed by threat intelligence feeds and the broader industry ecosystem.
Real-Time Insights
Malicious actors don’t care what time it is and will gladly take advantage of a small window of opportunity. Given this, SMB and enterprise organizations know that 24/7 monitoring is necessary, or at least an objective in progress.
Firms can save internal resources devoted to vulnerability and attack simulations by outsourcing BAS. Network administrators can rest better knowing that vulnerabilities should result in a timely notification.
Flexible For Evolving Infrastructure
Organizations moving to the cloud or considering alternatives to on-premises infrastructure require a solution covering everything. As a newer technology, breach and attack simulation can deploy to most infrastructures or network segments, including organizations moving towards a hybrid cloud or SD-WAN.
Add to this the headaches caused by mergers and acquisitions. For a global economy chock full of digital transformation and network changes, deployment flexibility for diverse environments is critical.
Deployment Options for BAS
There are a number of ways to deploy a BAS tool. Here are the main ones.
Agent-Based Vulnerability Scanning
The most straightforward deployment of BAS is the agent-based method. Similar to a vulnerability assessment but offering more visibility, this approach means placing agents in an organization’s LAN to continue testing network segments.
A critical downside to the agent-based method is its lack of oversight of the perimeter and, typically, an inability to exploit or validate vulnerabilities. That said, the agent-based process for deployment is still an improvement from past tools, thanks to its ability to report vulnerabilities and map out potential attack routes.
Malicious Traffic-Based Testing
Monitoring traffic, including malicious packets, is an inherent component of any modern cyberinfrastructure. Whether it’s an NGFW, IDPS, SIEM, EDR, NDR, or a combination of these tools, comprehensive solutions to address risks are a focal point for advanced network security. The malicious traffic-based testing approach attacks the network to identify vulnerabilities and – more importantly – report instances where core security solutions like IDPS and SIEM miss malicious traffic.
Like agent-based scanning, several agents in virtual machines (VMs) sit positioned throughout the network. Using a database of breach and attack scenarios, these VMs serve as the targets for testing. However, like the agent-based method, the traffic-based deployment option also leaves your perimeter out of the equation.
Black Box Multi-Vector Testing
The most advanced approach to BAS typically involves cloud deployment of agents to network locations, while the software solution maintains communication with the BAS platform. Unlike the previous two methods, the black box multi-vector approach for deployment includes analysis for perimeter-based breaches and attacks.
Much like the classic black box example for agent-machine I/O, this method aims to test as many inputs on multiple attack vectors to detect malfunctions. Suffice it to say that this method is the most desirable for enterprises because it offers the most visibility into its defensive posture.
Bottom Line: Breach and Attack Simulation Tools
When honing a skill, the saying goes, “practice makes perfect.” And then someone interjects, “Actually, perfect practice makes perfect.”
While maybe a bit too literal, they’re right in the context of cybersecurity. Threats today require proactive defensive strategies and can’t wait to be attacked to prepare. All it takes is one hidden misconfiguration and an advanced TTP for a network to fall victim to malicious actors.
Pen testing and red team services continue to make defenses more robust, offering critical insight into vulnerabilities, breach detection, and attack vectors. Breach and attack simulation is a natural step for SMB and enterprise organizations that require the latest cybersecurity tools. In an age where APTs wreak massive damage to critical and sensitive infrastructures, the need for constant, active scanning for the newest threats makes sense.
Read next: AI Will Save Security – And Eliminate Jobs
This updates a July 2022 article by Sam Ingalls




