
In the race to offer comprehensive cybersecurity solutions, the product known as network detection and response (NDR) is a standalone solution as well as a central component of XDR.
Whereas older solutions like antivirus, firewalls, and endpoint detection and response (EDR) have long focused on threats at the network perimeter, the intent of NDR is to monitor and act on malicious threats within organization networks using artificial intelligence (AI) and machine learning (ML) analysis.
Edward Snowden and the NSA breach of 2013, as well as dozens of other nightmares, point to the growing threat of inside threats for a universe of IT environments. Today, both outsiders with the right social engineering skills and disgruntled personnel pose risks to sensitive data when network architectures fail to implement microsegmentation and advanced network traffic analysis (NTA).
This article looks at the top network detection and response solutions in the budding sector, what NDR is, and what to consider in a NDR solution.
Also see the Top Network Monitoring Tools
Top Network Detection and Response Solutions
- Bricata
- Cisco
- Darktrace
- Exeon
- Extrahop
- Gigamon
- Vectra

Cisco
Almost 40 years after its start in Silicon Valley, Cisco remains one of the top IT and cybersecurity solution providers in the world. The Cisco Secure portfolio is massive, including next-generation firewalls (NGFW), MFA, vulnerability management, and DDoS protection. Alongside analytics solutions for cloud, malware, and logs, Cisco acquisition of Lancope in 2015 led to the development of its NDR solution, Cisco Secure Network Analytics. Built to detect and act on network threats faster, Cisco SNA is deployable as a cloud-based service, virtual machine, or on-premises appliance.
Cisco Secure Network Analytics Features
- Detection for signature-less, insider, and encrypted malware threats.
- Group-based policy adoption and reports to audit and visualize communications.
- The AnyConnect Network Visibility Module (NVM) for endpoint telemetry data.
- Malware analysis without decryption for advanced encrypted threats.
- Integrations with Akamai, Exabeam, Google, LogRhythm, Radware, and Sumo Logic.

Darktrace
Celebrating a decade in 2023, Darktrace was one of the fastest growing cybersecurity startups with a more turbulent ride since its listing on the London Stock Exchange in 2019. The Darktrace stack of solutions covers hardening, detection, and response for hybrid IT environments, including the vendor’s NDR solution, Darktrace DETECT, for applications, email, zero trust, operational technology (OT), and more. Today, the Cambridge, UK-based company puts artificial intelligence first in its security services for over 7,400 businesses in 110 countries.
Darktrace DETECT Features
- Self-learning AI to understand, secure, and optimize network interactions.
- Analyze thousands of metrics for known and unknown malware techniques.
- Integrations with AWS, Cisco, Fortinet, Microsoft, Okta, Rapid7, and ServiceNow.

ExtraHop Networks
Launched in 2007, ExtraHop’s success as a AI-based cybersecurity vendor led to its acquisition in July 2021 by Bain Capital for $900 million. Hailing from Seattle, Washington, the ExtraHop Reveal(x) 360 offers a unified threat intelligence platform for hybrid and multi-cloud IT environments. ExtraHop’s three core NDR solutions cover cloud security, network security, and IT operations. Whether it’s AWS, Google Cloud, or Azure, ExtraHop offers clients cloud-native security and comprehensive visibility into cloud workloads.
ExtraHop Reveal(x) Features
- Monitor sensitive data and workloads to prevent data breaches.
- Detects lateral movement and software supply chain attacks and vulnerabilities.
- Behavior and rule-based analytics to detect and respond to known and unknown threats.
- Identify threats and unusual activity faster to respond and remediate vulnerabilities.
- Integrations with Check Point, Citrix, CrowdStrike, IBM, Palo Alto Networks, and Splunk.

Vectra AI
Started in 2012, Vectra already stands out among the NDR marketplace, offering managed detection and response (MDR) and its threat detection and response platform. The San Jose-based company solutions span attack surfaces for all major cloud services, data centers, and Microsoft 365, with specialized threat management for ransomware, supply chain attacks, data breaches, and account compromise. Companies have plenty of integrations to choose from for tools like EDR, SIEM, threat intelligence, and Secure Access Service Edge (SASE).
Vectra Threat Detection and Response Platform Features
- Capture public cloud, SaaS, identity, network, and EDR data for analysis.
- Multiple AI modeling techniques to audit network workloads.
- Threat and risk prioritization to inform administrator action and investigation.
- Automated and manual response options for securing networks in real-time.
- Integration with AWS, Azure, Juniper, Pentera, SentinelOne, VMware, and Zscaler.

Bricata
Launched in 2014, Bricata is another vendor specializing in NDR capabilities and successful enough to catch the attention of OpenText, who acquired the Maryland based vendor in November 2021. While OpenText continues its acquisition spree (notably, acquiring Micro Focus this week), Bricata’s next-generation NDR platform continues to give security administrators visibility into user, device, system, and application behavior inside networks. In addition to real-time context and alerts, Bricata offers clients advanced forensics and threat hunting tools to make the most of investigations and remediation actions.
Bricata Next-Gen NDR Features
- Software-based and hardware agnostic with consumption-based pricing.
- Signature inspection, ML-based malware conviction, and anomaly detection.
- Automated analysis for threats with prioritized workflows to respond fast.
- Extract and store metadata for investigations and future use.
- Technology partners with Cylance, Elastic, Garland, OISF, Proofpoint, and Splunk.

Gigamon
Started in 2004, Gigamon has long been in the network visibility game with a portfolio today consisting of traffic intelligence and cloud, network, and data center visibility. Within its network security stack, Gigamon ThreatINSIGHT is the company’s cloud-based NDR solution for high-fidelity adversary detection and response. Evidence of Gigamon’s strength as an NDR solution includes being a connector for almost every other top NDR pick. Their larger technology alliance partners is extensive with 60 of the best vendors for managing network performance, vulnerabilities, and cloud infrastructure. Previously a publicly traded company (NYSE:GIMO), Gigamon was acquired by private equity for $1.6 billion in 2016.
Gigamon ThreatINSIGHT Features
- Inspection of encrypted traffic and lateral movement for any device, network, and flow.
- Omnisearch triage and investigation with up to 365 days of network metadata.
- Ongoing detection tuning and QA with the Gigamon Applied Threat Research (ATR) unit.
- Sensor and traffic diagnostics via the Gigamon technical success and SaaS Ops teams.
- Integrations with AWS, Cisco, CrowdStrike, FireEye, New Relic, Nutanix, and Riverbed.
Exeon Analytics
Another budding NDR vendor, Exeon offers advanced security analytics to protect IT and OT environments. Launched in 2016 from the campus of the Swiss Federal Institute of Technology, the Zurich-based company’s ExeonTrace seamlessly analyzes security-related log data from existing infrastructure. With comprehensive visibility, Exeon can help client’s identify data leaks, misconfigured devices, shadow IT, and unusual services. While Exeon mentions the ability to connect SIEM, EDR, and IDPS systems, the list of connectors wasn’t immediately available.
ExeonTrace Features
- Fast deployment which doesn’t require sensors or agents.
- AI-based threat scoring to prioritize investigations.
- Insight-driven visualizations including a global map of traffic sources.
- Network log data analysis for lightweight solution vs. data-heavy traffic mirroring.
Honorable Mention NDR Solutions
| Arista Networks | Blue Hexagon | Broadcom Symantec |
| Corelight | Fidelis | Hillstone Networks |
| LogRhythm | Lumu | Progress Flowmon |
| Stamus Networks | Threatbook | VMware |
What is Network Detection & Response?
Network detection and response (NDR) solutions complement tools like EDR and SIEM to analyze and detect malicious network traffic. In the next generation of network traffic analysis (NTA), NDR solutions offer AI and ML-based techniques to evaluate the latest signature-less attacks and unusual traffic patterns. When threats are detected, NDR solutions alert administrators to act or automate pre-configured preventative measures.
NDR Features
- Cognitive modeling to monitor and analyze tactics, techniques, and procedures (TTP).
- Real-time and historical view of traffic for investigating suspicious behavior.
- Context-driven visibility, advanced analytics, and IoC identification for threat hunting.
- Built-in advanced detection with ability to fine-tune configuration management.
- Integration with EDR, SIEM, SOAR, and other network security solutions.
Network Security and NDR
NDR is a complementary network security tool, joining a handful of other critical systems for an enterprise cybersecurity architecture:
- Cloud security
- Endpoint detection and response (EDR)
- Intrusion detection and prevention systems (IDPS)
- Network traffic analysis (NTA)
- Next-generation firewalls (NGFW)
- Security information and event management (SIEM)
- Security orchestration, automation, and response (SOAR)
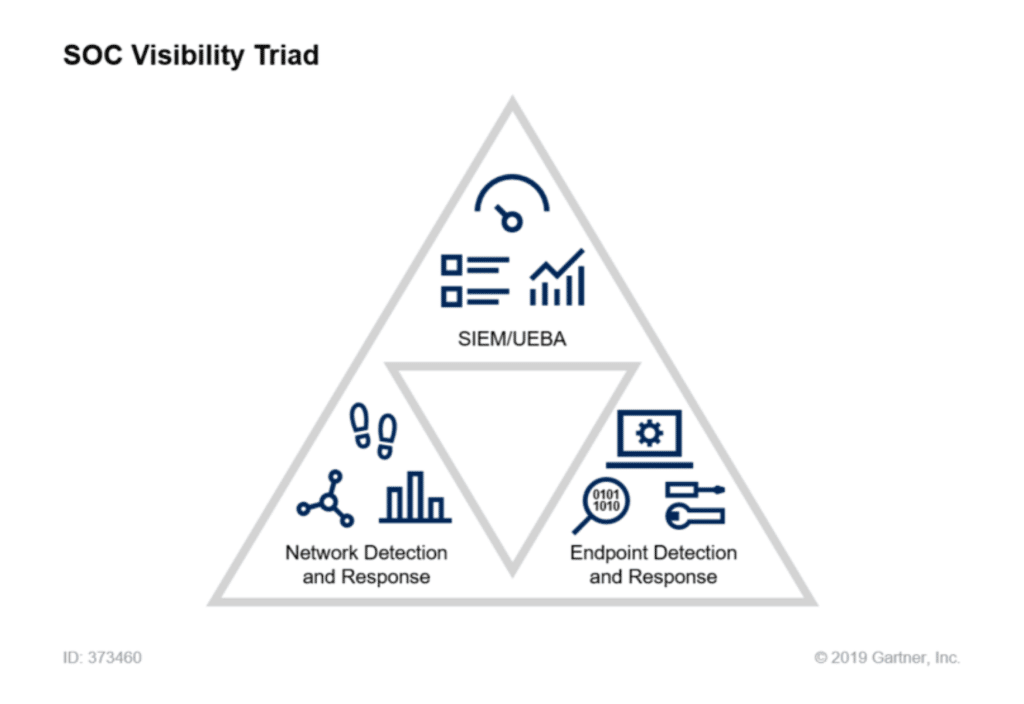
- User and entity behavior analytics (UEBA)
In 2015, Gartner Research Director Anton Chuvakin introduced the conceptual framework for what would become the “SOC visibility triad”. In a 2020 retrospective, Chuvakin explains how logs (via SIEM), endpoint data (via EDR or XDR), and network data (via NTA and NDR) are critical to security visibility.
How to Choose a NDR Solution
As an emerging security solution, NDR shouldn’t be the first priority for companies building out their cybersecurity infrastructure. That said, the above network detection and response solutions offer plenty for enterprise organizations with well-established cybersecurity postures.
While NDR vendors offer opportunities to bundle other network security tools, including robust portfolios from vendors like Cisco and Sangfor, a top consideration remains ease of integration with existing security systems for SIEM and EDR. Because most organizations aren’t starting from scratch, NDR vendors must strive for interoperability with the leading network security products.
In a crowded marketplace of cybersecurity solutions, NDR is yet another that is on the rise. Only time will tell how niche an audience it will serve. Keep an eye on how the NDR sector evolves in the years to come and whether it survives as a standalone solution and market or gets absorbed by more comprehensive frameworks like XDR.




