Vulnerability scanning (vulscan) tools scan assets to identify missing patches, misconfigurations, exposed application vulnerabilities, and other security issues to be remediated. The top vulscan tools provide actionable lists of vulnerabilities and the context to understand significance such as the type of vulnerability and its severity. To help you select the best fitting vulnerability scanning solution, we’ve evaluated the top options and their use cases.
The seven top vulscan tools to consider are:
- Tenable: Best overall vulnerability scanner and enterprise vulscan option
- Invicti: Best for comprehensive website and application (webapp) scans
- StackHawk: Best entry-level webapp scanner for small DevOps teams
- Nmap: Best open-source tool for free IT infrastructure and port scanning
- ConnectSecure: Best basic infrastructure scanning for service providers
- Vulnerability Manager Plus: Best entry-level endpoint and server scanner
- Wiz: Best specialist tool for clouds, containers, and infrastructure as code
Top Vulnerability Scanning Tools Compared
Explore each tool’s scanning options and other key aspects below:
| Vulnerability Scanner | VulScans Performed | Complexity | Agent | Key Features |
|---|---|---|---|---|
| Tenable | • Network, Endpoint, and Server • Website and Application • IoT | High, but reduced by pre- configured templates | Optional | • Scans more than 47,000 unique assets and apps • Tenable research often adds zero-day vulns |
| Invicti | Website and Application | High | None | • Automatic and continuous scans • DAST, IAST, and SCA testing |
| StackHawk | Website and Application | Low (focused DAST tool) | None | • Offers unlimited free DAST scans for one app • CI/CD, Slack and GitHub integration |
| Nmap | Network, Endpoint, and Server | High, but simplified by a script library | None | • Quick host discovery • Free tool |
| ConnectSecure | Network, Endpoint, and Server | Low (focused IT Infrastructure tool) | Yes | • Multi-tenant scanning and reporting • Automated alerts and ticket generation |
| Vulnerability Manager Plus | Network, Endpoint, and Server | Low (focused IT Infrastructure tool) | Yes | • Scans devices for end-of-life, peer-to-peer, and third-party software vulnerabilities • Offers a free tier |
| Wiz | Cloud and Container | Low (focused IT Infrastructure tool) | No | • Native cloud and Kubernetes vulnerability scanner • Scans infrastructure-as-code (IaC) |
For more details about the creation of this top seven list, read about our selection process below.

Tenable
Best Overall & Most Integrated Enterprise Vulnerability Scanning Tool
Tenable builds off of the popular Nessus vulnerability scanning tool to deliver integrated enterprise scale vulnerability detection that evaluates 47,000 unique IT, IoT, OT, operating systems, and applications. It provides consolidated capabilities for both network as well as website and application (webapp) vulnerability scanning backed by proprietary research that discovers zero-day vulnerabilities and powers their proprietary threat intelligence feed.
| Tenable Pros | Tenable Cons |
|---|---|
| One tool to scan both IT infrastructure as well as websites and applications | Requires multiple licenses to obtain full capabilities for scanning |
| Executive dashboards and powerful filtering to dig into findings | Some users complain of false negatives and limited API integration |
| Internally developed threat intelligence provides advance warning for 0-day vulns | Unsuitable for entry-level needs due to steep learning curve and limited free scans |
Pricing
Tenable provides their products based on annual subscriptions with multi-year discounts. They offer Nessus network vulnerability in three versions and a separate license for web application scanning.
- Tenable Web App Scanning: Starts at $5,250 per year for 5 domains
- Nessus Essential: Free, but only scans 16 IP addresses and doesn’t include compliance checks, content audits, or technical support
- Nessus Professional: Starts at $3,590 per year for unlimited IT and configuration assessments and has options for advanced support and on-demand training
- Nessus Expert: Starts at $5,290 per year and builds off of Nessus Professional to add external attack surface discovery, infrastructure as code (IaC) scanning, and more
Free trial versions are available for the commercial products. Resellers may offer discounted or bundled pricing.
Key Features
- Preconfigured templates to enable quick starts
- Automatic full scans trigger with all new vulnerabilities added
- Continuous scans check vulnerabilities and compliance configurations
- Multi-tenant options and customizable templates for IT service providers
- Automated alerts for Security Incident and Event Management (SIEM) tools

For more information, read our article on enterprise vulnerability scanning tools that compares Tenable against Intruder, Qualys, and more.

Invicti
Best Website & Application Vulnerability Scanning Tool
Invicti delivers the most comprehensive array of website and application (webapp) vulnerability scans and reduces wasted time with the least false positives in the industry. The robust scanner offers automated on-premises or SaaS hosted-scanning that integrates with standard development pipeline tools for efficient workflows. Invicti, formerly known as Netsparker, remains the industry leader in both the diversity of webapp scans and the quality of the results.
| Invicti Pros | Invicti Cons |
|---|---|
| Detects misconfigured configuration files | Users complain of a steep learning curve |
| Actively reduces false positives and provides proof of exploit | Customers complain about ineffective multi-factor authentication testing |
| Integrates with pipeline tools and issue trackers (Jenkins, Jira, GitHub, etc.) | Users notice slowness in the scans on larger web applications |
Pricing
Invicti doesn’t publish pricing information but bases licenses upon the number of user seats and the number of scanned websites. The three levels of licensing include:
- Standard: Provides on-premises installation of a desktop scanner for one user
- Team License: Provides ongoing multi-user access and provides capabilities for built-in workflow tools, PCI compliance, and asset discovery
- Enterprise: Licenses provide access to hosted and on-premises deployments as well as custom workflows and dedicated tech support
Key Features
- Automated and continuous scans to update website, application and API inventories
- DAST, IAST, and SCA options for dynamic (DAST) and interactive application security testing (IAST) as well as Software Composition Analysis (SCA) testing
- Crawls dynamic-input pages and complex paths authenticated by form submission, OAuth2, NTLM/Kerberos, multi-level forms, password-protected areas, and more
- Continuous updates regularly increase the capabilities of this enterprise tool

For more on the best options for webapp vulnerability scanning tools, read our article that compares Invicti against AppScan, Burp Suite, and more.

StackHawk
Best Entry-Level WebApp Scanner
StackHawk offers more limited scanning options but provides a free tier to kick start vulnerability scanning capabilities for the needs of smaller or inexperienced DevOps teams. The highly focused DAST scanner integrates with CI/CD automation and Slack to triage findings and enable rapid correction. Teams unfamiliar with webapp scanning can gain experience and develop workflows using StackHawk’s free tier and continue to use StackHawk as they grow.
| Stackhawk Pros | Stackhawk Cons |
|---|---|
| Unlimited scans for one application for the free tier enable robust entry-level capabilities | Requires use and knowledge of Docker infrastructure |
| Unlimited scans on unlimited applications starting with the lowest paid tier | Only provides email based support for the free version |
| Continuously adds features that apply to all versions of the tool | Requires a paid license for more than one application |
Pricing
Stack Hawk offers four levels of licensing that can be billed monthly or customers can gain discounts for annual billing.
- Free Tier: Enables DAST scanning for one application, automatable in CI/CD
- Pro Tier: Costs $49 per developer per month (minimum of five) with unlimited scanning, expanded integrations, custom test data, and either email or Slack customer support
- Enterprise Tier: Costs $69 per developer per month and adds single sign-on, role-based permissions, API access for scan results, dedicated Slack support, and a premiere Zoom support option
- Custom pricing: With volume discounts available for large development teams
Key Features
- DevSecOps integration for CI/CD, GitHub, and Slack to improve speed for remediation
- API support for REST, GraphQL, and SOAP integration and API security testing
- Custom scan discovery allows more advanced scanning options
- cURL-based reproduction criteria to reproduce alerted vulnerabilities for analysis

StackHawk is covered in more depth in both the best options for webapp vulnerability scanning tools and in the options for the best entry-level vulnerability scanning tools suitable for small and medium-sized businesses (SMB). These articles compare StackHawk against Dastardly, Detectify, Zap, and more.

Nmap
Best Open-Source IT Infrastructure & Port Scanner
Nmap incorporates preconfigured vulnerability scanning scripts to methodically scan open ports on each IP address in a target range for potential misconfigurations and vulnerabilities. As an open-source tool, it provides a quick, free, and light-weight solution that incorporates easily into other scripts for automated deployment and scanning. The favorite tool for both ethical hackers and malicious hackers, Nmap provides a glimpse of what vulnerabilities an attacker might see.
| Nmap Pros | Nmap Cons |
|---|---|
| Free, open-source tool with a large user base and active community support | No formal support for customers |
| Quickly scans open ports on a system and determines available TCP/UDP services | Requires some expertise in IT knowledge and programming to use effectively |
| Interrogates ports to determine running protocols, applications, and version numbers | Requires programming to integrate results into ticketing platforms or management tools |
Pricing
Nmap is an open-source tool available for free to end users and only requires a license when incorporated into commercial tools.
Key Features
- Quick host discovery to determine available IP addresses and open ports on a network
- Uses TCP/IP stack characteristics to guess device operating systems
- 500+ developed scripts for enhanced network discovery and vulnerability assessment
- Custom Nmap scripts provide powerful automation and integration capabilities
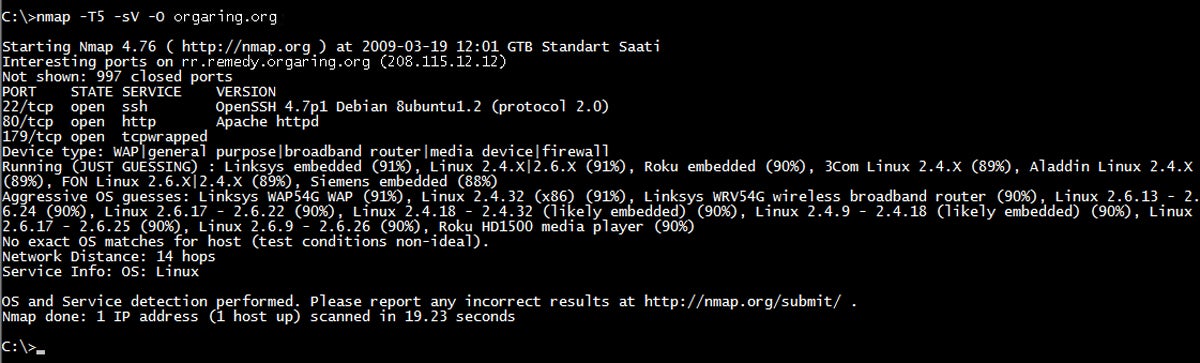
For more information on Nmap, read our article on open-source vulnerability scanning tools that compares Nmap against OpenVAS, OpenSCAP, and more.

ConnectSecure
Best Basic Infrastructure Scanning Tool for Managed Service Providers
ConnectSecure is a vulnerability scanner that managed IT service providers (MSPs) and managed IT security service providers (MSSPs) select because of flat rate pricing, multi-tenant capabilities, and a dedication to distribution through partners. It scans for vulnerabilities and compliance issues for endpoints (Windows, MacOS, Linux), servers, network equipment, printers, and mobile devices (through Mobile Device Management integration).
| ConnectSecure Pros | ConnectSecure Cons |
|---|---|
| Excellent coverage of the expected devices for most simple IT environments (endpoints, servers, and basic network equipment) | May not be suitable for more complex needs and environments that must scan complex cloud environments, containers, IoT, etc |
| Customizable reports enable provider or customer branded reports | Requires an agent to be deployed for most functions |
| Options for basic ticket generation or vulnerability management such as applying patches or prioritizing vulnerabilities | Additional vulnerability management and other capabilities may increase complexity for deployment and configuration |
Pricing
ConnectSecure offers a 14-day free trial and four tiers of flat-rate pricing:
- Up to 2,500 devices: $299 per month
- 2,501 to 5,000 devices: $499 per month
- 5,001 to 10,000 devices: $999 per month
- More than 10,000 devices: Contact for quote
Key Features
- Multi-tenant capabilities with prioritized multi-client reporting and role-based customized reports with white-label options
- Visual client dashboards provide easy-to-understand, customizable, and non-technical automated reports for clients
- Robust integration options with popular ticketing systems (ConnectWise, SyncroMSP, etc.) and communication tools (email, Slack, Microsoft Teams)
- Robust asset and threat management options for asset discovery, patch deployment, compliance management, and prioritization of threats and vulnerabilities

Our article on MSP/MSSP-friendly vulnerability scanning tools will also cover competitors such as RapidFire VulScan and Syxsense Security Scanner.

Vulnerability Manager Plus
Best Entry-Level Endpoint & Server Scanner
MangeEngine’s Vulnerability Manager Plus helps small IT teams to start vulnerability scanning of endpoint devices and web servers with minimal investment thanks to free trials and a free tier. Integration with other ManageEngine tools enables future expansion as the sophistication and capabilities of an organization grow. The free tier allows for the smallest teams to develop a vulnerability scanning and management program with assurance of support for future growth.
| Vulnerability Manager Plus Pros | Vulnerability Manager Plus Cons |
|---|---|
| Combines vulnerability assessment, compliance, patch management, and system security configuration into one tool | Doesn’t offer extensive integration options for 3rd party ticketing or vulnerability management tools |
| Entry-level-friendly with easy set up, low cost, and coverage of common IT needs | Doesn’t support automatic deployment to the cloud or scan containers, IoT, or webapps |
| Open port detection for all IT assets | Immediate patch deployment may be limited |
Pricing
ManageEngine offers three editions of Vulnerability Manager Plus, all licensed annually for a single technician and with free trials available for the paid tiers. The scanning of network devices may require additional licenses.
- Vulnerability Manager Plus Free: Permits scans for up to 20 workstations and 5 servers
- Vulnerability Manager Plus Professional: Starts at $695 to scan up to 100 workstations
- Vulnerability Manager Plus Enterprise: Starts at $1,195 for 100 workstations and adds audit compliance, patch management, remote shutdown scheduling, and more
Key Features
- Operating system and third-party software scans detect end-of-life software, peer-to-peer software, as well as unpatched vulnerabilities
- Detects setup vulnerabilities with scans for default credentials, firewall misconfigurations, open shares, and user privilege issues
- Basic web server vulnerability scanning for unused web pages, misconfigured HTTP headers/options, expired certificates, and more
Read our article on the best entry-level vulnerability scanning tools suitable for small and medium businesses (SMB) to compare Vulnerability Manager Plus against Tenable Nessus Essentials and GFI Languard.

Wiz
Best Specialist Tool for Cloud & Container Scanning
Wiz provides specialized vulnerability scanning for multi-cloud, Platform-as-a-Service (PaaS), Kubernetes containers, and other cloud infrastructure without affecting business operations or stealing resources from active workloads and processes. It natively connects to virtualized resources to provide hyper-focused vulnerability detection for the newest classes of IT assets.
| Wiz Pros | Wiz Cons |
|---|---|
| Agentless scanning does not consume container or virtual machine resources | Users report setup can be cumbersome and tedious |
| Cloud native solution for cloud infrastructure | Integrations can be difficult or incomplete |
| Scans integrate directly into CI/CD workflows for efficient DevSecOps performance | Actions must be established for each project for scanning – they can’t be cloned |
Pricing
Wiz doesn’t publicly list pricing but does offer custom pricing quotes based on the number of billable cloud workloads running in an environment. The AWS marketplace lists starting prices for 12-month contracts for the Cloud Infrastructure Security Platform as $24,000 for Wiz Essentials and $38,000 for Wiz Advanced with cloud detection and response and other capabilities.
Key Features
- Native cloud connections to AWS, Azure, Google, Oracle, and Alibaba
- Kubernetes built-in support on multiple platforms
- Infrastructure-as-code scanning and cloud infrastructure entitlement management
- Incorporates zero-day vulnerabilities discovered by the Wiz research team
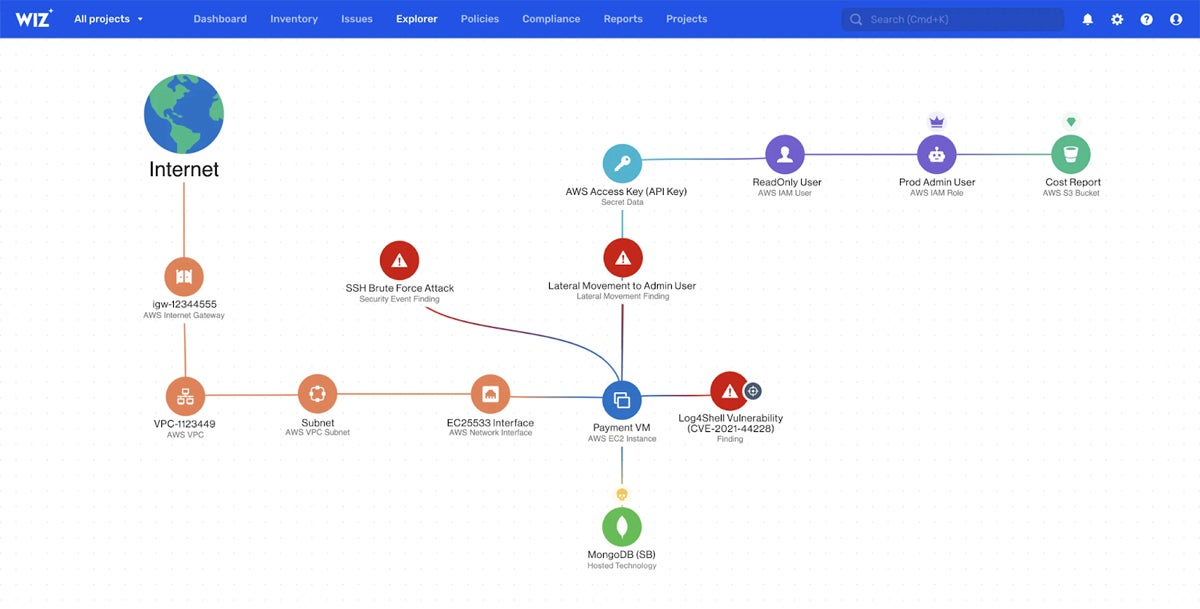
Read about other specialty solutions in our article on specialized vulnerability scanning tools for clouds and data lakes.
How We Evaluated the Best Vulnerability Scanning Tools
This list of the top vulnerability scanning tools draws from research on the top solutions for the major vulnerability scanning categories. Buyers searching for vulnerability scanning tools primarily seek standalone solutions that can be installed or integrated with existing security stacks and IT ticket processes.
Therefore, inclusion criteria focus primarily on stand-alone vulnerability scanning tools, although some entry-level vulnerability management tools were considered and evaluated based exclusively on their vulnerability scanning capabilities. The criteria excludes solutions that incorporate vulnerability scanning features into other tools such as penetration testing, asset management, patch management, etc.
To select the best options from the remaining tools, we considered the key criteria relevant to the buying decision: scanned assets, user skill, price and licensing, scanning capabilities, integrations, and customer support.
Scanned Assets
The types of assets a vulscan tool scans provided the first criteria to segregate the tools. After all, direct comparisons between webapp and network scanners often fail because of the phenomenal differences between the types of scans. We therefore segregated the tools into comparison sets based on website and application, IT infrastructure, and specialty scanning needs (IoT, cloud, container, etc.).
User Skill
User skill, sophistication, and resources became the next consideration for comparison. For example, the sophisticated needs of an international bank (enterprise) can’t be compared against the straightforward and streamline needs of a small high school (entry-level or SMB). Additionally, we considered the specialized needs of managed service providers for multi-tenancy, customized reports, etc.
Price & Licensing
Price remains a key consideration for all buying decisions. When comparing products, we considered the price to features ratio, pricing transparency, availability of details for required and optional licenses, annual or volume discounts, and availability of free trials.
Scanning Capabilities
We evaluated all tools on their core scanning features, vulnerability source quality, and false positive information. We evaluated infrastructure scanners based on support to scan a diverse range of devices found in the modern environment, including IoT, network equipment, and containers. We compared webapp scanners based on scan type (DAST, IAST, etc.), CI/CD integration, API scans, and support for web forms, passwords, and dependencies.
Integrations
Vulnerability scanning tools need to plug into existing process for ready adoption and deployment. For integration concerns, we considered ease of installation, ease of administration, deployment options (SaaS, on-site, docker container, etc.), automation, and exporting vulnerabilities to existing IT ticketing systems or security incident and event management (SIEM) solutions.
Customer Support
Everyone needs help at some point, so for customer support, we considered hours of availability, the availability of diverse contact options (phone, Slack, etc.), and options for premium support. We also included support for sales channel partners under this category to consider the needs of various types of service providers and resellers.
Frequently Asked Questions (FAQ)
Why Are There So Many Types of Vulnerability Scanning Tools?
The first vulnerability scanners tested local network devices and those needs remain. However, the expanding scope of IT assets drives the development of specialty vendors that focus on specific assets and enterprise vendors that add new features to their already-complicated tools.
Meanwhile, the universal need for vulnerability management leads to the incorporation of vulnerability scanning capabilities in other tools (penetration testing, endpoint security, etc.) or the addition of management and remediation capabilities to existing vulnerability scanners.
Is Vulnerability Scanning the Same as Patch Management?
Vulnerability scanning is not the same as patch management. Patches will correct some vulnerabilities, but other vulnerabilities stem from misconfiguration or deliberate selection of dangerous options in firewalls, security tool settings, or in writing software. Vulnerability scanning needs to be performed separately, but it can be used to confirm patch installation.
For resource constrained teams, many tools offer free trials that can be used to test drive capabilities. When in-house vulnerability scanning proves unmanageable, consider vulnerability-management-as-a-service (VMaaS), MSPs, or MSSPs to offload the tasks and ensure that critical vulnerabilities will be detected and remediated quickly.
Can You Use Multiple Vulnerability Scanning Tools?
A typical organization often uses multiple vulnerability scanning tools to fully test all IT assets. The best solution may even use redundant scanning tools to compare results.
For example, simulate typical hacker activity by using free open-source vulnerability scanners such as Nmap. Then use commercial vulnerability scanners to further analyze results, detect false positives, and prioritize remediation.
Bottom Line: Vulnerability Scanning Starts & Finishes Critical Security Processes
Security depends upon the rapid identification of vulnerabilities and an equally rapid resolution before attackers can exploit them. Vulnerability scans start the detection process and also complete the cycle with another round of vulnerability scans. The final scans confirm vulnerability elimination and generate reports needed to prove asset security for executives, stakeholders, and compliance auditors.
For more insight into the vulnerability discovery and management process, consider how to conduct a vulnerability assessment.




