SAML is an open standard facilitating the communication and verification of credentials between identity providers and service providers for users everywhere.
In 2005, the open standard consortium OASIS released SAML 2.0 to broad appeal. As smart mobile devices boomed, so did the number of web applications and the need to address never-ending logins. SAML was essential to addressing this challenge and introduced single sign-on (SSO) as a reliable tool for individuals up to enterprise organizations. The other most common use of SAML is for federation networks between infrastructure not necessarily linked to web services.
This article looks at the SAML protocol, how it works, the involved parties, and where it fits in the evolution of identity and access management (IAM).
Table of Contents
- What is SAML?
- Service Providers and Identity Managers
- How Does SAML Work?
- Why is SAML Important?
- OAuth vs SAML
- IAM History: SAML in Context
What is SAML?
The Security Assertion Markup Language (SAML) manages transactions between web service providers and identity providers using the Extensible Markup Language (XML). These communications on the backend of username and password login processes ensure users get authenticated by the overarching identity manager and authorized to use the given web service(s).
Context: Authentication vs. Authorization
A foundational piece of the digital access puzzle is the difference between authentication and authorization. Authentication confirms user identity, and authorization grants specific rights to a web application, user, or device.
Read more: Best Privileged Access Management (PAM) Software
Service Providers and Identity Managers
Service providers and identity managers play a critical part in the federation process, allowing users access to specific data.
Service Providers
The exponential growth of applications serving consumer to enterprise IT needs and wants means a universe of service providers. Service providers are the organizations and web services offered to users through a valid request. Application and software developers are responsible for establishing the necessary backend database and protocol for storing and accepting user account credentials.
Popular service providers include top business application vendors like SAP, Microsoft, Oracle, Adobe, Google, and Salesforce.
Identity Managers
Identity managers offer organizations a system wherein a set of credentials can merge to become a federated identity for a specific user to access applications across platforms. Like directory services, organization administrators can control access to particular data with network user identity management.
Examples of popular enterprise identity provider systems include Microsoft and Azure Active Directory (AD), Lightweight Directory Protocol (LDAP), and Google Suite, while other vendors include Oracle, Okta, OneLogin, and Auth0.
Also read: Best Zero Trust Security Solutions
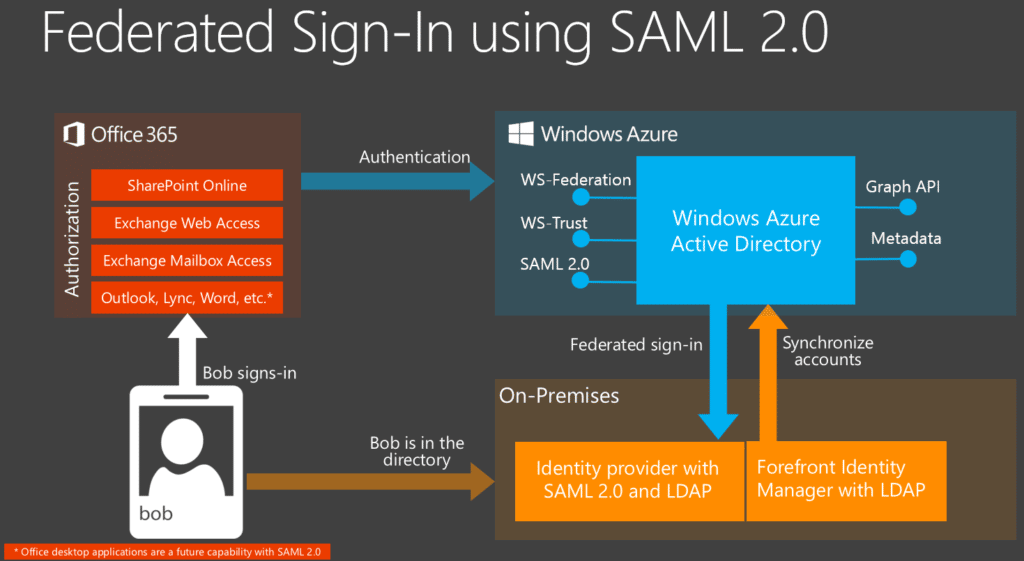
How Does SAML Work?
- A user logs into the identity provider’s SSO.
- The user submits a request for a privileged web page.
- The service provider confirms user credentials with the identity provider.
- The identity provider responds by validating the user.
- The user accesses the web page requested.
Why is SAML Important?
Whereas web service providers have long played the role of identity managers, the emergence of identity providers offers users convenient access for storing credentials and, therefore, access to a list of accounts. SAML is the federated authentication and authorization process in this split of responsibilities, simplifying communication between parties.
Read more: How Machine Identities Can Imperil Enterprise Security
OAuth vs SAML
OAuth is also an example of a language web service providers use to communicate on behalf of users and applications, but they address different sides of the authorization-authentication coin.
SAML is a standard managing identity management and federation, including systems like SSO. OAuth is a pure authorization protocol that pairs with OpenID Connect (OIDC), which handles authentication.
SAML might be the more trusted and mature protocol of the two; however, OIDC is a newer authentication protocol designed for mobile and web applications. Another notable difference between the two languages is OAuth’s use of the JSON Web Token (JWT). While SAML uses XML, JWTs are more lightweight, self-contained, and include a digital signature for independent verification without the authorization server.
While SAML 2.0 remains widely in use, the growth of OAuth 2.0 paired with OIDC means it isn’t deployed nearly as much.
Learn more about OAuth 2.0 with OAuth: Our Guide to Industry Authorization.
IAM History: SAML in Context
In 2001, the Organization for the Advanced for Structured Information Standards (OASIS) began work on what would become an industry-first XML framework for exchanging authentication and authorization data. A year later, SAML 1.0 would become an official OASIS standard. In 2005, OASIS released 2.0, which gained widespread appeal for web developers and service providers by the end of the decade.
While SAML 2.0 led the way, the first two iterations of OIDC, OpenID, were released in 2006 and 2007 as alternative authentication protocols. The launch of OAuth 1.0 in 2010 and OAuth 2.0 two years later meant third parties had a deliberate protocol for authorizing secure, user-agent, delegated access. Rather than dealing with a separate protocol for authentication needs, the release of OpenID Connect in 2014 gave developers an added layer fulfilling initial access across accounts.
Despite the recent prevalence of OAuth and OIDC for authentication and authorization, SAML 2.0 remains a widely offered and used protocol for enterprise organizations.
Also read: Best Next-Generation Firewall (NGFW) Vendors








