Once an organization has been breached, the overwhelming majority of critical assets are just a few attack techniques away from being compromised, according to a new study.
The report by breach and attack simulation (BAS) vendor XM Cyber noted that 63% of critical assets are just a single “hop” away from initial breach to compromise; 81% of critical assets are no more than two attack techniques away from disaster; and 94% of critical assets can be compromised in four or fewer moves by a hacker after the initial attack vector.
For the report, the XM Research team used the company’s Attack Path Management platform to examine a year of data and nearly 2 million “entities” – an endpoint, file, folder or cloud resource that a hacker can use in an attack path as they move toward critical resources.
Other key findings include:
- 73% of the top attack techniques involve mismanaged or stolen credentials.
- On average, 75% of an organization’s critical assets can be compromised in their current security state.
- 78% of businesses are open to compromise every time a new Remote Code Execution (RCE) technique is found – just yesterday, a zero-day RCE vulnerability was revealed in the Spring Java framework (CVE-2022-22963) – and combining RCE and cloud techniques could compromise 90% of organizations.
- 95% of organizational users have long-term access keys attached to them that can be exposed.
- The main attack vectors in the cloud are misconfigurations and overly permissive access.
“It is not enough that you are just monitoring the threats and alerts,” the report said. “It’s about understanding the context of these vulnerabilities within your environment and the attack paths that these vulnerabilities offer to an attacker looking to breach your critical assets.”
Breach and attack simulation tools can help by simulating attacks to find those vulnerabilities and attack paths and prioritize fixes, something like a continuous, automated pentesting tool. XM Cyber claims it goes further than other BAS tools by “checking everything” instead of just one step.
Attack techniques and vectors can be combined in different ways, XM Cyber noted, resulting in many possible combinations. Here’s one possible combination given in the report:
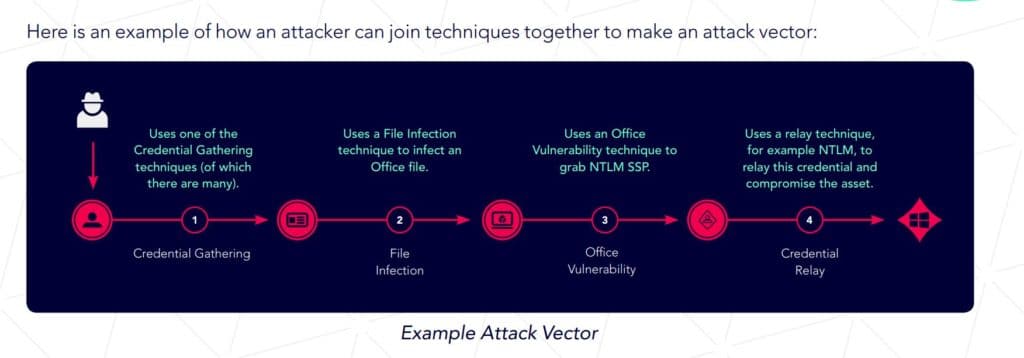
See the Top Breach and Attack Simulation Solutions
Credentials are the ‘Achilles Heel of the Cloud’
Cloud access configurations are complex, the report noted, and it can be easier to take shortcuts like setting permissions by a whole group, resulting in overly permissive access. The top attack techniques used a combination of vulnerabilities, misconfigurations and mismanaged or stolen credentials:
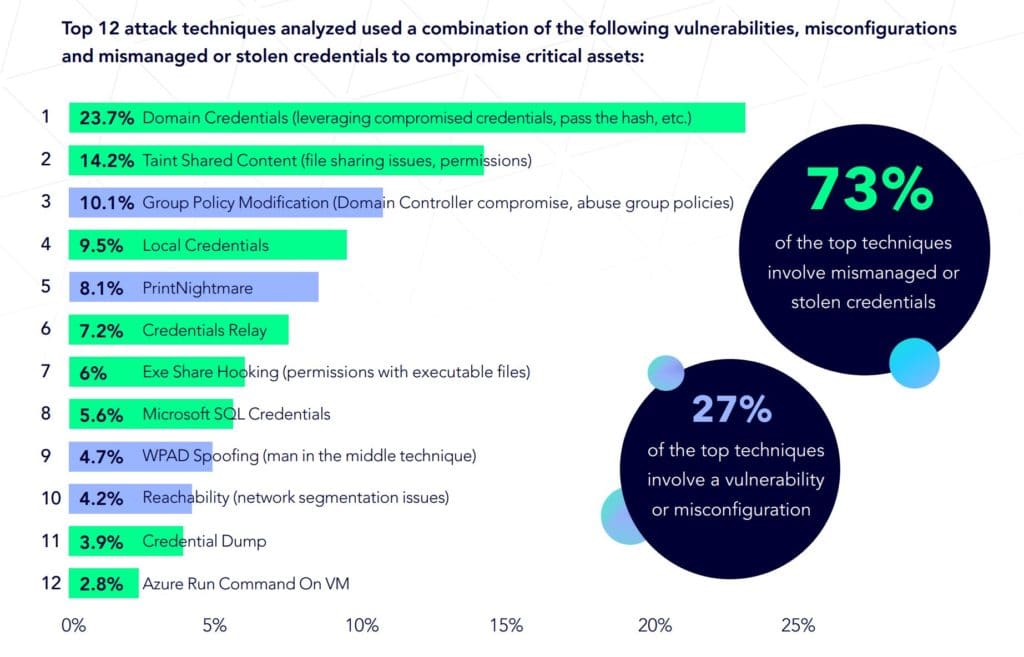
With strong patch management programs and operating system security features like user authentication, “we can prevent lots of attack vectors that abuse the different credential issues,” the report noted, but cautioned: “it is a misconception to believe patching CVEs will fix everything and stop lateral movement. The research shows that nearly 30% of an attacker’s techniques abuse misconfigurations and credentials to compromise and breach the organization.”
Hybrid clouds leave 28% of all organizations vulnerable to a cross-platform attack, creating a need for security solutions that protect critical assets regardless of where they’re located. The researchers gave the example of an on-premises desktop as the starting point for an Active Directory breach via Azure:

Reducing Threats
Solutions like XM Cyber can help organizations reduce threats by 80% by knowing where to disrupt attack paths, the report said.
“Modern organizations are investing in more and more platforms, apps and other tech tools to accelerate their business, but they too often fail to realize that the interconnection between all these technologies poses a significant risk,” stated Zur Ulianitzky, Head of Research at XM Cyber. “When siloed teams are responsible for different components of security within the network, nobody sees the full picture. One team may ignore a seemingly small risk, not realizing that in the big picture, it’s a stepping stone in a hidden attack path to a critical asset. To keep pace with today’s technology and business demands, attack path remediation must be prioritized.”
The XM Cyber report can be found here.
Read next: The Top Vulnerability Management Tools




