Using misconfigured multi-factor authentication (MFA) and an unpatched Windows vulnerability, Russian state-sponsored hackers were able to breach a non-governmental organization (NGO) and escalate privileges, the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI revealed last week.
By using a misconfigured Cisco Duo MFA implementation to force enrollment of a new device, the hackers were then able to use the “PrintNightmare” Windows Print Spooler vulnerability (CVE-2021-34527 and CVE-2021-36958) to obtain administrator privileges.
Inactive Accounts and Default Configurations
Hackers gained initial access by brute-forcing an existing account via “a simple, predictable password” to enroll a new device in the MFA procedures, the agencies said. The targeted organization was using the default MFA configuration, so it was possible to re-enable MFA for a dormant account with a new device owned by the attackers.
MFA was automatically disabled because the account was inactive for a long period. Unfortunately, the account was still enabled in Active Directory, which allowed hackers access to the network.
After that, they modified a domain controller file, c:\windows\system32\drivers\etc\hosts, to redirect all MFA calls (e.g., logins) to localhost instead of the MFA server.
They exploited a default policy in MFA protocols called “Fail open” that disables verification if the MFA server is unreachable. They then authenticated to the victim’s VPN to initiate a remote desktop protocol (RDP) connection to the domain controllers. That’s how they obtained credentials for other domain accounts and replicated the operation to bypass MFA.
This unfortunate turn of events shows how adversaries can quickly sneak into a system and exploit vulnerabilities to escalate privileges and compromise the whole network. Even with such significant flaws, proper network segmentation and zero trust could have reduced the damage, perhaps blocking the attack at some point.
In privileged areas, there are no small problems.
Also read: Top 9 Active Directory Security Tools
PrintNightmare Remains a Struggle
Admins have struggled with PrintNightmare fixes and patches, and hackers can still exploit a vulnerable Windows Print Spooler service to elevate their privileges.
Print spooler is a service in Windows that manages all print jobs sent to the print server. You can actually observe the service in Windows by opening the services.msc utility. It works great but researchers found a bug in the driver installation procedure that allows bypassing authorization using a RPC (Remote Procedure Call) function to install a malicious DLL and ultimately execute arbitrary code.
There are multiple POCs (proofs of concept) available publicly like this python script that work on a “fully patched Domain Controller.” Microsoft partially mitigated the bug but not the privilege escalation. Applying the patches does not eliminate all risks but not doing so would be a significant risk.
Of course, you could disable the Print Spooler service but that would disable print both locally and remotely, which does not look like a valid solution:
![]()
Print Spooler has a long history of bugs and misdiagnosis, but CVE-2021-34527 allows compromising the entire Windows system and affects an extensive range of Microsoft products.
The bug itself does not require high privileges, as any authenticated user is enough to attack domain controllers:
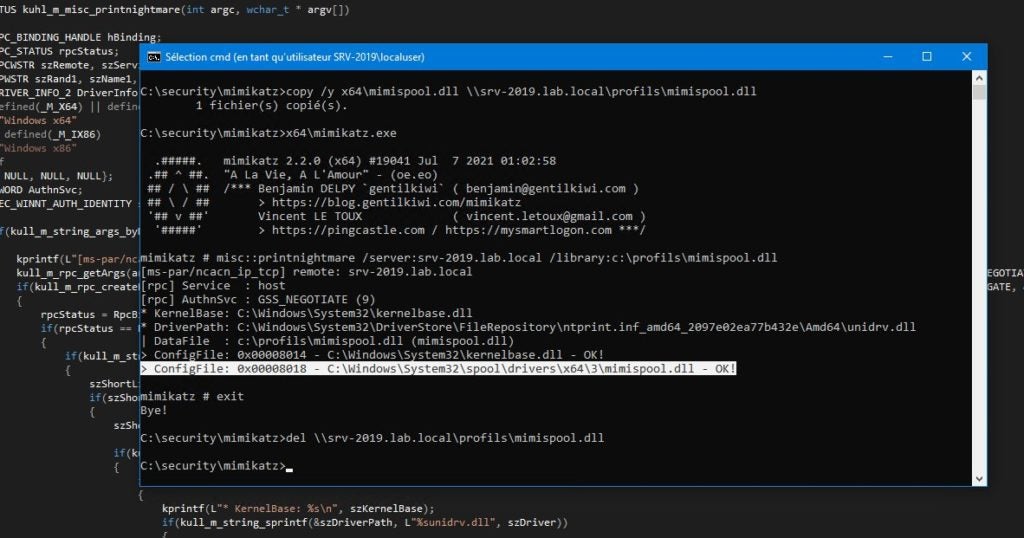
Mitigations that would consist of restricting permissions for driver installations could be challenging because you have to modify Windows registry entries, so if it’s not executed correctly, you might damage the system.
Also read: Best Patch Management Software
Protecting Against PrintNightmare, MFA Exploits
FBI and CISA recommend a long list of mitigations and security and network best practices, which can consist of hardening login policies and restricting admin privileges but also monitoring remote access or unapproved protocols. Here is the full list:
Mitigations
- Enforce MFA for all users, without exception. Before implementing, organizations should review configuration policies to protect against “fail open” and re-enrollment scenarios.
- Implement time-out and lock-out features in response to repeated failed login attempts.
- Ensure inactive accounts are disabled uniformly across the Active Directory, MFA systems etc.
- Update software, including operating systems, applications, and firmware on IT network assets in a timely manner. Prioritize patching known exploited vulnerabilities, especially critical and high vulnerabilities that allow for remote code execution or denial-of-service on internet-facing equipment.
- Require all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to have strong, unique passwords. Passwords should not be reused across multiple accounts or stored on the system where an adversary may have access.
- Continuously monitor network logs for suspicious activity and unauthorized or unusual login attempts.
- Implement security alerting policies for all changes to security-enabled accounts/groups, and alert on suspicious process creation events (ntdsutil, rar, regedit, etc.).
Security Best Practices
- Deploy Local Administrator Password Solution (LAPS), enforce Server Message Block (SMB) Signing, restrict Administrative privileges (local admin users, groups, etc.), and review sensitive materials on domain controller’s SYSVOL share.
- Enable increased logging policies, enforce PowerShell logging, and ensure antivirus/endpoint detection and response (EDR) are deployed to all endpoints and enabled.
- Routinely verify no unauthorized system modifications, such as additional accounts and Secure Shell (SSH) keys, have occurred to help detect a compromise. To detect these modifications, administrators can use file integrity monitoring software that alerts an administrator or blocks unauthorized changes on the system.
Network Best Practices
- Monitor remote access/ RDP logs and disable unused remote access/RDP ports.
- Deny atypical inbound activity from known anonymization services, to include commercial VPN services and The Onion Router (TOR).
- Implement listing policies for applications and remote access that only allow systems to execute known and permitted programs under an established security policy.
- Regularly audit administrative user accounts and configure access control under the concept of least privilege.
- Regularly audit logs to ensure new accounts are legitimate users.
- Scan networks for open and listening ports and mediate those that are unnecessary.
- Maintain historical network activity logs for at least 180 days, in case of a suspected compromise.
- Identify and create offline backups for critical assets.
- Implement network segmentation.
- Automatically update antivirus and anti-malware solutions and conduct regular virus and malware scans.
Remote Work Environment Best Practices
- Regularly update VPNs, network infrastructure devices, and devices used for remote work environments with the latest software patches and security configurations.
- When possible, implement multi-factor authentication on all VPN connections. Physical security tokens are the most secure form of MFA, followed by authenticator applications. When MFA is unavailable, require employees engaging in remote work to use strong passwords.
- Monitor network traffic for unapproved and unexpected protocols.
- Reduce potential attack surfaces by discontinuing unused VPN servers that may be used as a point of entry for attackers.
Vigilance is Required
Regular vulnerability assessments and pentesting are becoming less optional all the time. System administrators can schedule scans to spot unauthorized system modifications or unwanted additional SSH accesses.
Evidence of compromise, also known as IoCs (Indicators of Compromise), are helpful for determining what happened after an attack. Typical IoCs can be unusual activities in privileged accounts, suspicious registry changes, traffic leaving the network (outbound), suspicious DNS requests, or geographical anomalies such as login attempts from countries where the organization does not have any business activities.
Organizations can use specific software to check file integrity and detection tools such as EDR, but these efforts should cover the entire attack surface, including all potential endpoints.
Aggressive patch management, network segmentation, and hardened security policies can be powerful mitigations.
The attack showed that inactive accounts and default policies are prone to lateral movements and used for privilege escalation. You should absolutely ensure such dormant accounts are disabled uniformly across your entire network, including Active Directory, MFA, and other procedures.
Indeed, it’s best if you remove access for all unused resources such as old accounts or VPN servers that hackers will likely use as a point of entry.
Read next: Top Vulnerability Management Tools




