A surprising 91.5 percent of all malware detected on networks of WatchGuard Technologies customers in the second quarter came over encrypted connections, raising the security risk for the 80 percent of such organizations that lack processes for decrypting and scanning HTTPS traffic for threats.
WatchGuard, which sells network security, intelligence and endpoint protection solutions, included that finding in its recently-released Internet Security Report, which is based on data coming in from the vendor’s Firebox firewalls and other products and services being used by customers in areas such as antivirus, intrusion prevention and malware detection.
The report covered a range of cybersecurity issues, including network attacks – which rose by 22 percent over the previous quarter, to almost 5.1 million – ransomware (the number of incidents rose sharply in the first half of 2021, ending a three-year decline on endpoints), and the continued focus on Microsoft Office by bad actors.
Malware in Encrypted Traffic
However, what stuck out most was the amount of malware found in encrypted traffic and the threat that poses for many enterprises. With only 20 percent of organizations having mechanisms in place for decrypting and scanning HTTPS traffic for malware, that means “the remaining 80% are at risk of missing nine-tenths of the malware hitting their networks daily,” WatchGuard officials wrote.
“With much of the world still firmly operating in a mobile or hybrid workforce model, the traditional network perimeter doesn’t always factor into the cybersecurity defense equation,” Corey Nachreiner, chief security officer at WatchGuard, said in a statement. “While a strong perimeter defense is still an important part of a layered security approach, strong endpoint protection (EPP) and endpoint detection and response (EDR) is increasingly essential.”
The report’s authors wrote that WatchGuard security experts have been able to identify much of the malware that comes over encrypted connections because network administrators at customer sites have configured the Firebox appliances to decrypt HTTPS connections. However, more administrators need to do this to protect themselves against malware that they currently can’t see coming over encrypted connections.
Further reading: The Case for Decryption in Cybersecurity
Two Malware Families Dominate
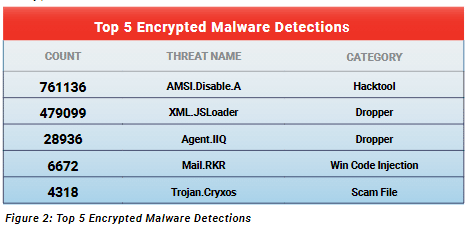
Much of the malware detected in the second quarter came from two malware families that were first seen in the prior quarter. XML.JSLoader and AMSI.Disable.A accounted for more than 90 percent of detections over HTTPS and more than 12 percent of all detections. The reach of the two malware families would likely only increase if more organizations decrypted and scanned the HTTPS traffic because more incidences of the malware would be found, the authors wrote.
AMS.Disable.A was interesting because WatchGuard added it to its top malware section in the first quarter and by the next quarter, it reached the number two spot on the list and number one on the list for overall encrypted threats, company officials said. The malware uses PowerShell tools to exploit vulnerabilities in Windows, but it uses a technique to evade detection. The malware family includes code that can disable the Antimalware Scan Interface (AMSI) in PowerShell, which enables it to bypass script security checks with its malware payload undetected.
TLS 1.3, Perfect Forward Secrecy Increase Complexity
The fact that cybercriminals are finding ways to infect encrypted traffic should serve as a warning to business executives, according to executives with several cybersecurity firms. Jake Williams, co-founder and CTO with incidence response solutions vendor BreachQuest, told eSecurity Planet that he would have guessed the amount of encrypted traffic carrying malware would be closer to 95 percent.
“This research puts numbers to what would otherwise be anecdotes,” Williams said. “Monitoring encrypted traffic is important both to detect the delivery of malware and to observe command and control (C2) patterns. TLS 1.3 and Perfect Forward Secrecy (PFS) make this more difficult and threat actors know it. Organizations considering encrypted traffic monitoring solutions should examine how they will deal with PFS to ensure they gain full value from the investment.”
Network Administrators Must Be Cautious
Taylor Gulley, senior application security consultant at nVisium, told eSecurity Planet that enterprises that want to find ways to better detect malware in encrypted traffic will want to tread lightly.
“With the world moving toward secure communications, it makes sense that malware distributors will do so too,” Gulley said. “Along with this fact, there is a rising desire for companies to inject themselves into that communication, particularly where it concerns network traffic to and from their employees in order to catch malicious traffic early. This requirement to monitor encrypted traffic for threats creates a dilemma where one must determine if the benefits outweigh the risks of such measures.”
He added that “while being a man-in-the-middle is a frequently sought position for an attacker, when a company attains the same position, similar risks present themselves.”
Decrypting network traffic will provide insights into the contents of the traffic, according to Gulley, but HTTPS traffic is being decrypted and logged, then given the nature of the traffic, information meant to remain private between two parties on the internet is now available on the system in plain text, which could lead to passwords and session tokens being stored in log files.
“Rather than work to undermine secure communications, it may be better to focus on proper endpoint security, as well as employee security awareness,” Gulley said. “By proceeding in this manner, your workforce is less likely to fall for the types of ploys that malware distributors use in the first place. Subsequently, if there is a lapse in vigilance, the endpoint security solution can then intervene where necessary.”
PowerShell, Ransomware Threats Grow
Among other key findings in WatchGuard’s report was that malware detections originating from such scripting engines as PowerShell reached 80 percent of last year’s total in only the first six months of 2021. If the pace continues, fileless malware detections will double in volume between 2020 and this year.
Ransomware, which has been the biggest security scourge worldwide in recent years, is evolving from a “shotgun blast” to one in which the bad actors are targeting large companies, according to WatchGuard officials. The attack on Colonial Pipeline by Russia-based hacking group DarkSide in May showed not only that ransomware wasn’t going anywhere, but that hackers are focusing on vital services – like hospitals, infrastructure and industrial controls – and ramping up their attacks against these targets.
In addition, the use of malware attacking Microsoft Exchange servers and generic email users to download remote access Trojans (RATs) in phishing attacks is increasing, according to WatchGuard’s report. The researchers said the increase is likely due to Q2 being the second quarter that remote workers and students returned to their offices or schools during the COVID-19 pandemic, either in a hybrid fashion or full time.
Further reading: