Vulnerability management systems based on the Common Vulnerability Scoring System (CVSS) v2 scoring system may be misguided, as a new report found that roughly half of the most critical vulnerabilities may be scored incorrectly.
“Looking at the past 10 years, in the same midyear period, we see that on average, 51.5 percent of all known 10.0 scored vulnerabilities are unspecified,” Flashpoint noted in its mid-year 2022 Report. “This means organizations could be prioritizing hundreds of issues that may not actually be 10.0—further highlighting that base CVSS scores alone should not drive vulnerability management processes.”
Flashpoint analyzed 11,860 vulnerabilities in the first six months of 2022 and found that the CVE/NVD services failed to report and detail 27.3% of them. This lack of detail can also explain why some scores may be too high as a precaution.
“To make better risk decisions, you need comprehensive vulnerability intelligence,” the report said, adding that security teams can maximize resources and reduce their immediate workload by 82 percent by first focusing on actionable, high severity vulnerabilities.
See the Best Patch Management Systems
Why Inaccurate CVSS Scores are a Big Problem
It’s hard to navigate with the wrong map. The most critical vulnerabilities are the ones that require immediate action. If the CVSS model misleads security teams, they will likely focus on the wrong tasks and miss the real emergencies.
Many security vendors have built-in features to monitor the vulnerability disclosure landscape and prioritize actions automatically according to specific parameters, including severity scores. And compliance schemes rely on these scores to require immediate remediation, which forces organizations to prioritize all vulnerabilities with a score exceeding a certain threshold.
It’s not a new issue, though, and many security experts have been noting shortcomings in the CVSS system for years, especially when it’s used for ICS vulnerability assessments and patch management.
Indeed, the severity of a vulnerability does not necessarily match the actual risk for an organization. It might give an idea of what issues could occur with a specific flaw, but it does not say whether it’s a “discovered-in-the-wild” vulnerability, which means one used in attacks before it was discovered – and thus a top priority for security teams.
It should be noted that it does not mean the CVSS score lacks value, but it’s essential to assess the impact of a vulnerability in the context of an organization. What can happen if the firewall fails? Is the vulnerability easy to exploit? Can the vulnerability cause a massive downtime or data breach?
The score is just an indicator and can’t replace proper risk management.
Make Actionable Severity Vulnerabilities the Top Priority
Wrong prioritization can have a huge impact on security teams, but Flashpoint believes they could dramatically reduce their immediate workload by first focusing on actionable severity vulnerabilities.
Rather than reading uncontextualized scores at face value, teams should prioritize the business need to reduce their backlog of tickets that constantly grows with daily security updates.
While remediation is often required for the most severe security holes first, bug bounty programs and regular pen-tests can increase the effectiveness of vulnerability management.
For example, depending on the network segmentation, the same vulnerability can be either an absolute disaster or a medium-severity issue.
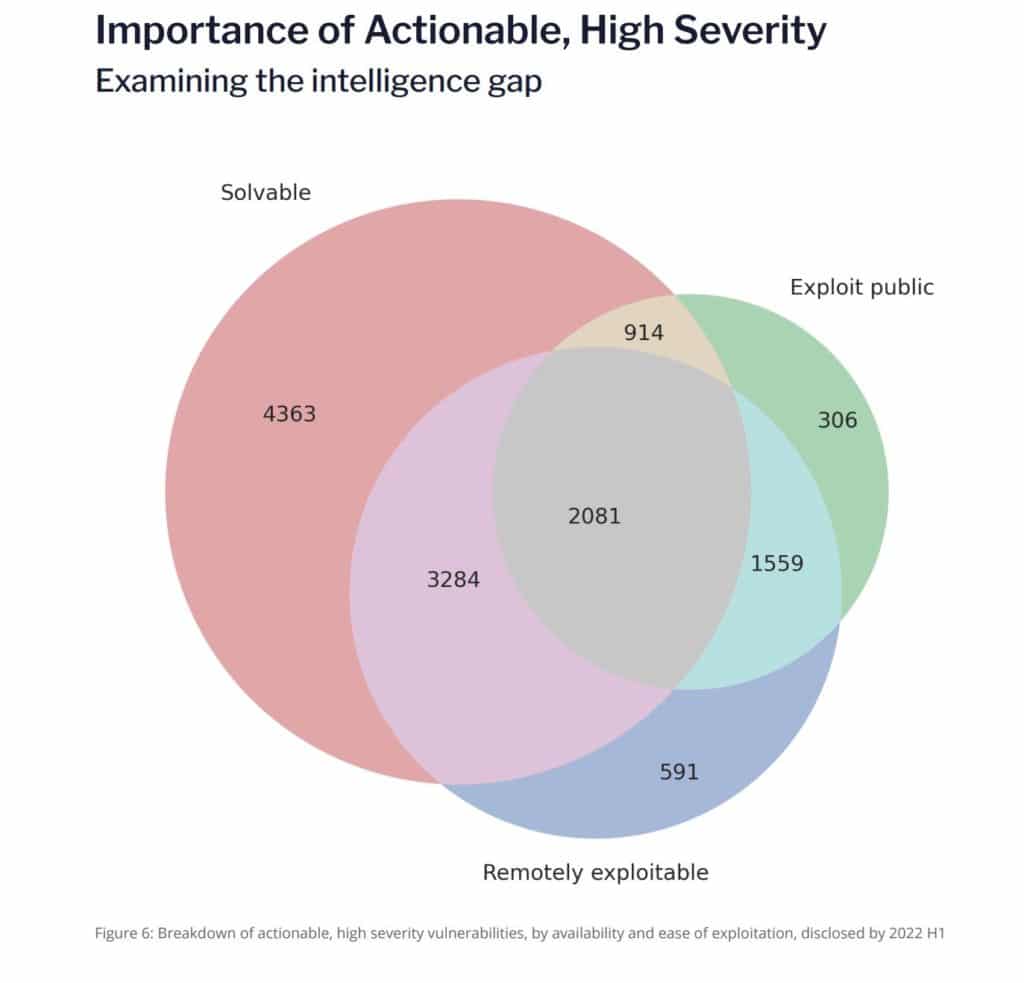
Flashpoint notes that vulnerabilities in the actionable, high severity category have three characteristics: they are remotely exploitable, have a public exploit, and have a viable solution, like a patch or upgrade. For this midyear period, 2,081 vulnerabilities hit this “sweet spot,” the researchers noted (see image below).
“These vulnerabilities should be at the top of the list for triaging, as they pose the most risk, yet are the quickest to remediate,” the report said. “Once those issues are addressed, security teams can then examine the remainder, using a risk-based approach that prioritizes at-risk assets based on business need, rather than uncontextualized base CVSS scores. As such, using these three points of metadata can be incredibly helpful for security teams to quickly reduce the most risk in their environment, resulting in better outcomes compared to top-down patching. Simple queries against a complete data set gives more power and flexibility for your team.”
‘Discovered-in-the-Wild’ Discrepancy Noted
The report also highlights a discrepancy of 85 percent concerning “discovered-in-the-wild” vulnerabilities reported in 2022 H1 compared to other resources such as Google’s Project Zero, showing that exploitation occurs more often outside of Advanced Persistent Threat (APT) attacks.
The first half of 2022, Flashpoint aggregated 37 discovered-in-the-wild vulnerabilities, compared to Project Zero’s 20.
“But examining all known discovered-in-the-wild vulnerabilities, Flashpoint’s research teams collected 311 vulnerabilities with this classification—versus Project Zero tracking 221,” the researchers said. “These statements are not meant to downplay Project Zero’s effectiveness or efforts. Instead, it shows that there are vulnerabilities within this classification that fall outside of Project Zero’s scope. And although they have not been observed to be used by APTs in their attacks, having knowledge of these issues can greatly benefit private sector organizations as they affect commonly-used software and developing technologies such as the blockchain. Ultimately, it communicates that an organization was exploited by a malicious third-party, regardless of being designated an APT or not.”
What Does All This Mean for Patch Management?
It’s unlikely your organization relies solely on abstract scores to make decisions, but if that’s the case, you should definitely revise your strategy.
Aggressive patch management can be rewarding despite the known inconveniences, as vulnerability disclosures usually inspire tons of public POCs (proofs of concept) that can be used by various attackers outside of APT groups.
Remediation can be a struggle for technical teams. It’s not exactly like pushing the “update button,” and the process can even take weeks or months.
While compliance may sometimes point in the wrong direction and give a false sense of security, outdated software is a major risk for organizations and quite often the root cause of massive attacks.
Read next: Best Vulnerability Scanner Tools







