Password managers are security tools that store, manage, and share authorization credentials safely for individual users and groups. In this article, I evaluate the top password managers and their ability to deliver and support solutions for businesses of all sizes with enterprise capabilities such as centralized management and reporting.
The top password managers for enterprises are:
- 1Password: Best overall password manager
- Bitwarden: Best for self-hosting requirements
- LastPass: Best for core and enterprise features
- RoboForm: Best for affordable business pricing
- Keeper: Best government solution
- NordPass: Best for quick implementation
Featured PartnersFeatured Partners: Password Management Software
eSecurity Planet may receive a commission from merchants for referrals from this website
Top Password Manager Comparison
Here is a quick overview of the top six password managers and their key features:
| Groups Management | Password Generator or Checker | SOC2 & ISO 27001 Security Certification | Business Pricing/User/Month (Billed Annually) | |
|---|---|---|---|---|
| 1Password | Yes | Both | SOC 2 Only | • Teams: $19.95 up to 10 users • Business: $7.99 |
| Bitwarden | Yes | Both | SOC 2 Only | • Teams: $4 • Business: $6 |
| LastPass | Yes | Both | Both | • Teams: $4 up to 50 users • Business: $7+ |
| RoboForm | Yes | Both | None listed | $3.33 |
| Keeper | Yes | Both | Both | • Business Starter: $2 up to 10 users • Business: $5 |
| NordPass | Yes | Both | Both | • Business: $3.99 up to 250 users • Enterprise: $5.99 |
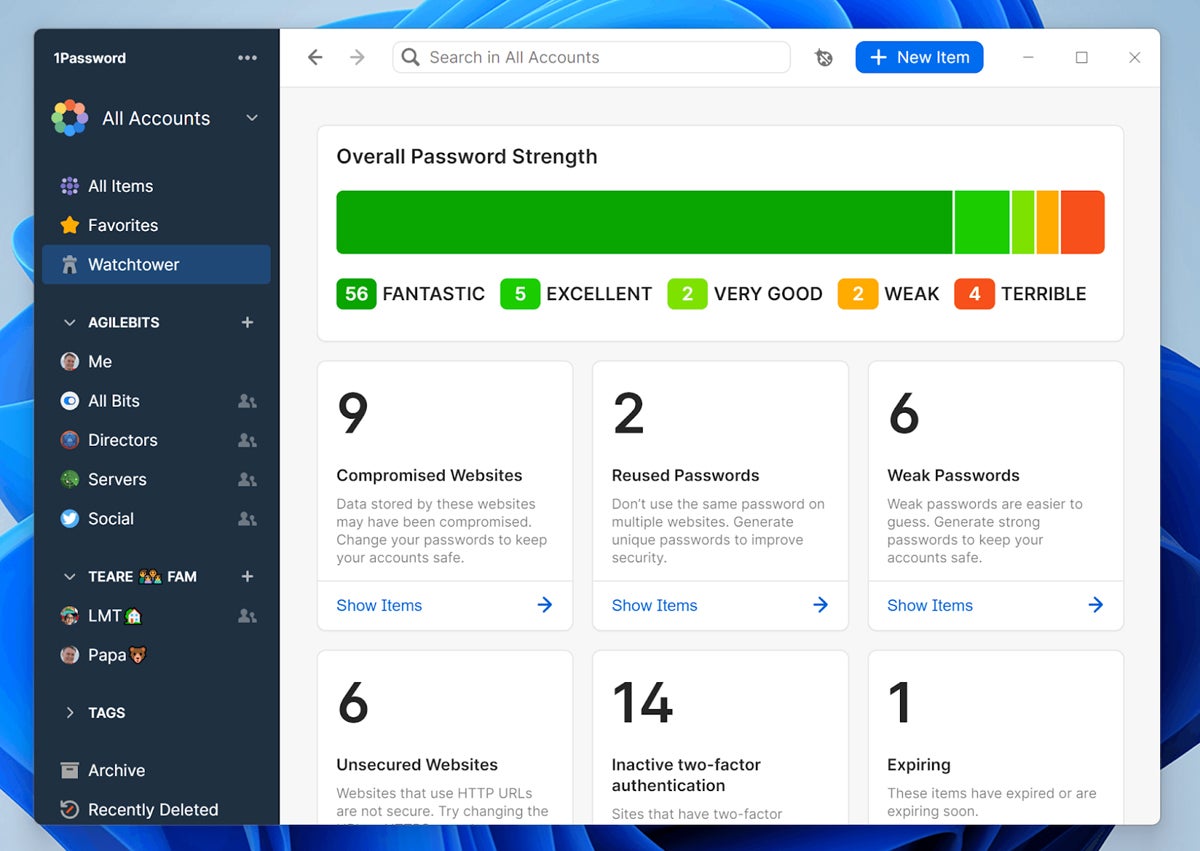
1Password – Best Overall Password Manager
Overall Rating: 4.1/5
- Business pricing: 2.5/5
- Core features: 4.5/5
- Customer support: 4.6/5
- Enterprise features: 3.8/5
- Security: 4/5
- Extras: 4.3/5
1Password balances user experience and security to provide the top-rated password manager that also wins in the categories for customer support and ease of use, security, and extras and perks. 1Password offers unique features to hide vaults while traveling, virtual payment cards, and native support to save Single Sign-On (SSO) credentials when using Google, Facebook, LinkedIn, or others to login to third party websites and applications.

As of version 8, 1Password no longer supports self-hosted vaults but instead provides consistent features across all desktop and mobile versions. It also introduced support for passkey login for Beta testing in 2023. 1Password also delivers enterprise features such as bulk-upload of credentials, security information and event management (SIEM) connections, and cross-domain identity management (SCIM) integration.
Pros
Cons
For more perspective on 1Password, read how it stacks up against Bitwarden, Dashlane, Keeper, and LastPass.
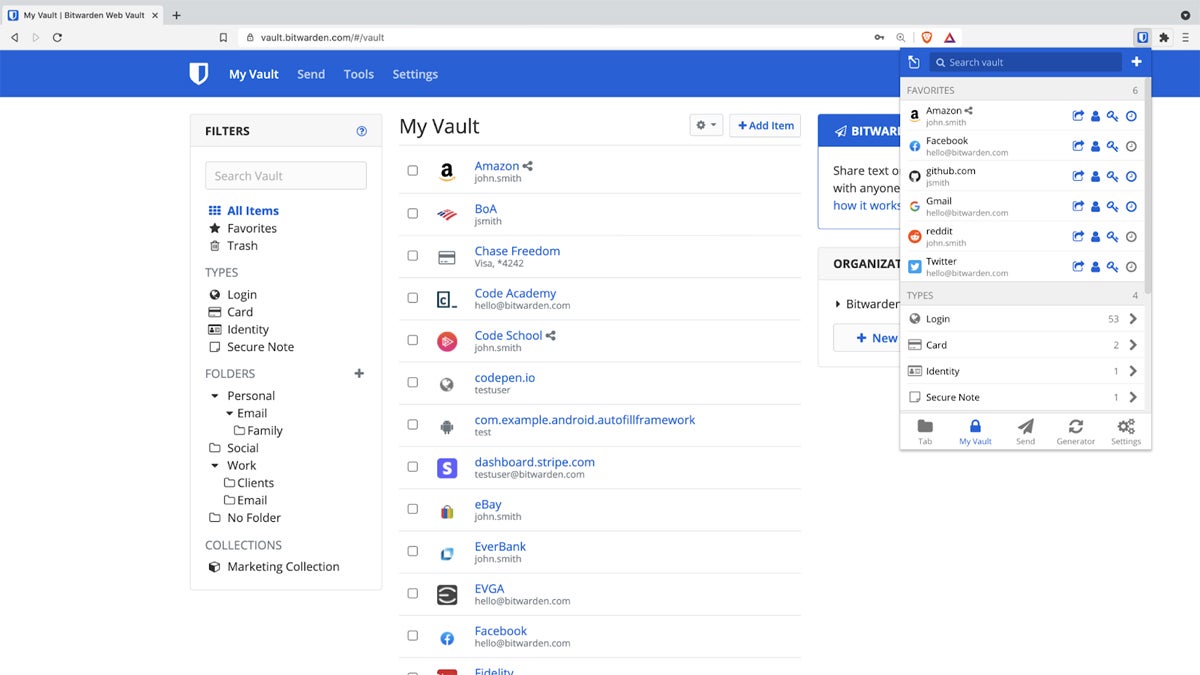
Bitwarden – Best for Self-Hosting Requirements
Overall Rating: 3.7/5
- Business pricing: 3/5
- Core features: 4.4/5
- Customer support: 4.4/5
- Enterprise features: 4.1/5
- Security: 3/5
- Extras: 1.5/5
Of the top six solutions, Bitwarden delivers the only open-source and self-hosting password management option. Security pros that prefer to examine code in detail will choose Bitwarden and their users won’t suffer because the solution provides rich features, wide compatibility, and a good user experience. The self-hosting allows for full control of the entire password manager infrastructure, which some compliance standards may require.

Bitwarden allows unlimited users for their Teams license and supports extensive login options for user’s password vaults, such as biometrics, FIDO2 WebAuthen credentials, authenticator apps, email, YubiKey, and SSO. Currently, the tool primarily restricts MFA options to the Bitwarden Authenticator app when logging into third-party apps and websites. However, a passkey feature in beta will deliver passwordless access as another option in the future.
Pros
Cons
Read how Bitwarden stacks up in detail against 1Password and LastPass in terms of features and security.
LastPass – Best for Core & Enterprise Features
Overall Rating: 3.5/5
- Business pricing: 2.3/5
- Core features: 4.6/5
- Customer support: 3.8/5
- Enterprise features: 4.2/5
- Security: 1.8/5
- Extras: 1.8/5
LastPass earns third place in the password manager ranking through extensive features valued by users and administrators. Users often cite superior user experience compared with other applications because of effective core features such as password sharing, password generation, digital wallets, continuous device sync, wide platform support (OS, device, browser plugins), and form autofill.

Although known for user-friendly features, LastPass also provides features needed by enterprises such as group management, bulk upload, and integration with both identity managers and SIEM tools. To further document security capabilities, LastPass earned both ISO 27001 and SOC2 certification for their cloud-hosted vault.
Pros
Cons
For more information, read the LastPass product review.
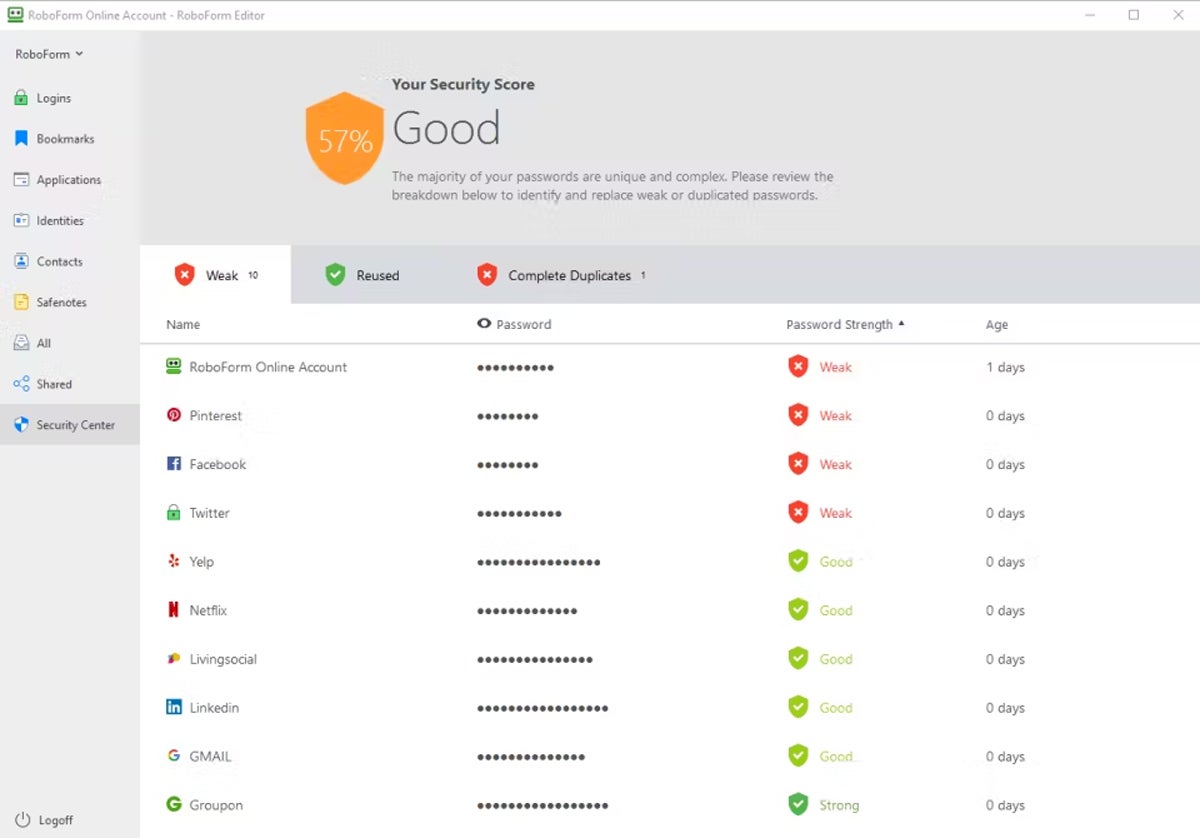
RoboForm – Best for Affordable Business Pricing
Overall Rating: 3.4/5
- Business pricing: 4/5
- Core features: 4.4/5
- Customer support: 2.6/5
- Enterprise features: 3.3/5
- Security: 3.5/5
- Extras: 1/5
Launched as a form-filling utility in 1999, RoboForm introduced a business password manager solution in 2009. RoboForm offers only one license that provides all features and capabilities for a single price that can only be improved with multi-year commitments or volume discounts. The tool provides highly functional capabilities and integration options to major identity provider solutions such as Active Directory (AD) and Azure AD.

RoboForm continues to evolve and introduce new capabilities that improve security. The tool supports a number of MFA options to access local vaults, including TOTP authentication apps (Google Authenticator, Authy, etc.), email, SMS one-time password, and biometrics. RoboForm also introduced passkey support in September 2023 to support passwordless site login.
Pros
Cons
Keeper – Best Government Solution
Overall Rating: 3.3/5
- Business pricing: 2.8/5
- Core features: 3.7/5
- Customer support: 4.1/5
- Enterprise features: 3.9/5
- Security: 2.5/5
- Extras: 2.1/5
Keeper provides the only FedRAMP and StateRAMP certified password management solution and backs up their capabilities with both ISO 27001 and SOC 2 certification. Government agencies with low to high risk impact levels for executive agency cloud deployments will find Keeper a good solution to use. Fortunately, Keeper also provides a solid password management solution with strong features and good user experience ratings.

Keeper offers 24/7 support via phone, chat, and a self-help library. Tickets and email support responses areguaranteed within 1 or 2 days. The Enterprise license offers a full suite of integration support for SCIM tools for automated user provisioning and deprovisioning and multi-factor authentication. Keeper also offers add-on vaults for developer secrets such as SSL Certificates, SSH Keys, API Keys, and more.
Pros
Cons
For even more information regarding Keeper, read a direct comparison against 1Password.
NordPass – Best for Quick Enterprise Implementation
Overall Rating: 3.2/5
- Business pricing: 2.6/5
- Core features: 4.2/5
- Customer support: 3.5/5
- Enterprise features: 3.9/5
- Security: 2.2/5
- Extras: 0.5/5
NordPass provides strong password authentication capabilities to all tiers of their business licenses, including admin panels for user management, business vaults, unlimited password and note storage, the NordPass Authenticator, MFA access, and 24/7 support. Enterprise licensees benefit even more with premium support that provisions a dedicated account manager and face-to-face onboarding services for rapid and smooth implementation.

A relatively new entrant into the password management market, NordPass launched in 2019 and continues to add capabilities for desktop, application, and browser plug-in versions. Recent additions include email masking, import support for Proton Pass, Dutch language support, and FIDO U2F support for YubiKey and other USB security keys for vault access.
Pros
Cons
For more information on NordPass, also consider reading how it is one of the best LastPass alternatives.
Top 6 Features of Password Manager Software
To ensure the security of login credentials for online accounts, a password manager offers users the ability to securely store and manage them. In addition, enterprise password managers enable group management, shared secrets, and centralized management, enforcement, and reporting.
2FA or Multi-Factor Authentication
2FA or multi-factor authentication adds extra layers of security with identity verification that uses a second or third factor of authentication. Typical password managers support vault access MFA such as biometric authentication, security questions, email, passkeys, USB keys (YubiKeys), authenticators, and single-sign-on (SSO).
Admin Management & Reporting
Enterprises need centralized management to ensure consistent policy enforcement throughout the organization as well as the reporting to prove it. Admins also need intuitive and actionable reports that allow for quick detection and remediation of weak, reused, expired, or breached passwords.
Cross-Platform Support
Adoption requires availability, so password managers need to provide users with cross-platform support across a multitude of operating systems (Windows, macOS, Linux), browsers (Chrome, Firefox, Edge, etc.), and platforms (laptops, phones, tablets, watches). Synchronization (aka: sync) across platforms is both convenient as well as ensures that a lost device won’t cause future access problems.
Groups Sharing
Enterprise password managers enable group and folder sharing between groups or classes of users such as departments (marketing, accounting, etc.), levels (managers, admins, etc.), and roles (shipping, design, etc.). Some solutions enable sharing to be permanent, expire after a term, or be used once.
Integration Options
Enterprise password managers need to connect to other systems to enable fast responses. Look for integration options with SCIM, Active Directory, and similar identity management solutions for fast response to employee on- and off-boarding as well as SIEM integration for security alert monitoring and response.
Password Management
An enterprise solution will incorporate a password generator that allows users to create strong, unique passwords for each account longer and more complex than the typical user could memorize. The solution will also check existing passwords for weakness, reuse, and attempt to detect breached credentials. Password managers can share passwords safely, enforce password policy, and provide centralized reporting and management for administrators.
How We Evaluated the Best Password Management Solutions
In my evaluation of the top password management solutions, I used six weighted criteria containing their own weighted subcriteria. The resulting values generate scores out of five points for each criteria and roll up to the overall score out of five points for the solution. Only the solutions with the top six overall scores made our final cut and an evaluation of unique features and product strengths informed the primary use cases for each password manager.
Evaluation Criteria
All password managers need to deliver fundamental password management features, therefore I weighted this the heaviest. Enterprise requirements for support and overall security also received high ratings, with slightly less emphasis on security since most solutions offered similar capabilities. Pricing, enterprise features, and extras and perks all earned equal weighting.
- Core password management features (35%): The subcriteria considered for this category include fundamental password management features, recovery options, MFA vault access support, digital wallets, and support for various OS and browsers.
- Criterion Winner: LastPass
- Customer support and ease of use (20%): This category considered customer reported complexity (setup and admin), cloud status website information, dedicated customer service availability, and customer support ratings, hours, and options.
- Criterion Winner: 1Password
- Security (15%): These subcriteria evaluate breach history, security certifications (SOC2, ISO 27001), master password encryption, availability of open source code for review, and support for MFA options to log into third-party applications and websites.
- Criterion Winner: 1Password
- Business Pricing (10%): To account for varying needs from SMBs to the Fortune 100, these subcriteria evaluated different licensing tier prices, the lowest tier’s maximum number of users, billing flexibility, FedRAMP or StateRAMP authorization, and free trials.
- Criterion Winner: RoboForm
- Enterprise Business Management Features (10%): This category considers group support, integration with identity management solutions, monitoring and reporting, bulk upload and approval of users, migration support and self-hosting options.
- Criterion Winner: LastPass
- Extras & Perks (10%): To evaluate features that deliver additional value, this category considers flat fee site licenses, passkey support, guest accounts provided, added family accounts for users, virtual payment cards, and travel security.
- Criterion Winner: 1Password
Frequently Asked Questions (FAQs)
What Is an Enterprise Password Manager?
An enterprise password manager secures corporate passwords, login credentials, shared credit card numbers, and other shared secrets. It also provides centralized setup, reporting, control, and enforcement of company policies.
Should Companies Use a Password Manager?
All companies should use a password manager to protect against breached, weak, and reused passwords. Professional solutions also can’t be fooled by look-alike web pages, which offer some protection against phishing, man-in-the-middle, and other attacks that attempt to steal credentials.
What Are the Problems with Password Managers?
Password managers improve security but remain vulnerable to the same problems as all security tools: weak master passwords, software vulnerabilities, user avoidance, and credentials theft by malware infestations on local devices. These issues can be countered by integrating password managers into a security stack that detects and counters them.
Are Passwords the Same as Passkeys?
Passwords are not the same as passkeys. Passwords use combinations of letters and numbers to provide a single unlock code for symmetric encryption and passkeys use the public key of supporting websites and applications to create asymmetric encryption codes unique to the device and user.
Bottom Line: Password Managers Strengthen Security Stacks
Every user who starts using a password manager increases the ability to manage more complex and more frequently changed passwords. Businesses that adopt enterprise grade solutions can enforce complexity, improve compliance, and improve general security with centralized management of passwords and sharing. Take advantage of the free trial offerings to test a solution and find out if it is the right one for you!
To strengthen the security stack further, learn how privileged access management (PAM) or identity and access management (IAM) provides additional protection.