Encryption scrambles data to make it unreadable to those without decryption keys. Proper use of encryption preserves secrecy and radically lowers the potential damage of a successful cybersecurity attack.
The understanding of different encryption types will often be confused by the many possible, inconsistent, and confusing ways that “encryption type” can be used. To minimize confusion, this article explains and classifies encryption types, explores what encryption will be best for which situation, and discusses how to effectively use encryption through the following topics:
For a more basic overview of encryption, consider reading: What Is Encryption? Definition, How it Works, & Examples.
Classifications of Encryption Types
To avoid confusion, let’s examine the different ways ‘type’ can be applied to encryption and how we will cover them in this article:
- Encryption category types will explain the overarching and basic categories of classification for encryption, including the two most important: symmetric and asymmetric encryption.
- Encryption algorithm types will provide an overview of the mathematical algorithms used to encrypt data (AES, RSA, etc.), their significance, and their pros and cons.
- Encryption tool types will discuss the major classifications of encryption tools available for use by an organization.
Although each is a ‘type’ of encryption, some sources mix these together, which can be confusing for those trying to understand encryption. We provide the additional distinctions to help better explain how encryption works and to better illustrate the tool to use for specific use cases.
Encryption Category Types
An encryption category type provides an overarching classification that encompasses multiple encryption algorithms or tool types. These conceptual buckets provide definitions that help to define the inherent weaknesses and strengths of families of algorithms and tools.
The two most important encryption categories are symmetric and asymmetric encryption. These critical encryption concepts encompass the vast majority of encryption algorithms and tools currently in wide use and can be used in combination for secure communication.
Other important categories of encryption categories include:
- Homomorphic encryption, which continues to rise in importance with the processing of sensitive and regulated data.
- Block ciphers process plain text in fixed-sized chunks for encryption.
- Format-preserving encryption (FPE) used to create encrypted fields with specific formatting and length requirements for databases.
- Stream ciphers process data as it passes through the algorithm and is used in communication.
We will also briefly discuss hashing, which is often associated with encryption but is not actually a type of encryption.
Symmetric Cryptography: Best for Speed
Symmetric cryptography uses the same concept as shared keys for a house — one or more individuals use an identical key to unlock the lock for access. Symmetric encryption works much the same way — to encrypt and decrypt messages with a single, shared key.
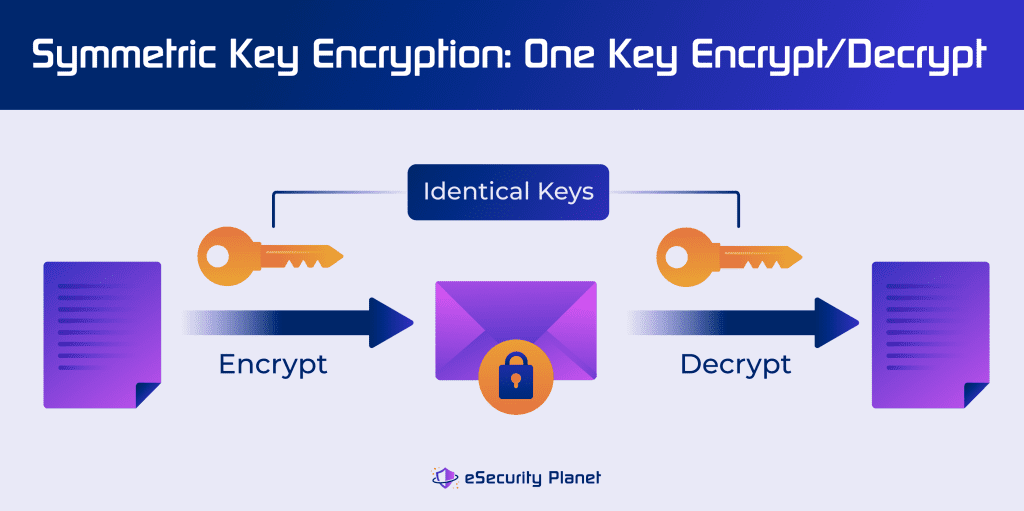
Users can establish a symmetric key to share private messages through a secure channel, like a password manager. Unfortunately, while symmetric encryption is a faster method, it is also less secure because sharing the key exposes it to theft.
Phishing and social engineering are common ways threat actors can obtain a symmetric key, but cryptanalysis and brute force attempts can also break symmetric key ciphers. Symmetric encryption is often used for drive encryption, WiFi encryption, and other use cases where speed performance is paramount and a password can be safely shared.
Modern algorithms use variable input, variable key lengths, and multiple rounds to compensate for symmetric key weaknesses.
Asymmetric Cryptography: Best for Sharing
Asymmetric cryptography works more like providing a code to unlock a small panel in an otherwise locked door for deliveries. The shared public key of asymmetric cryptology can encrypt documents, but decryption requires the use of a private key that is not intended to be shared.
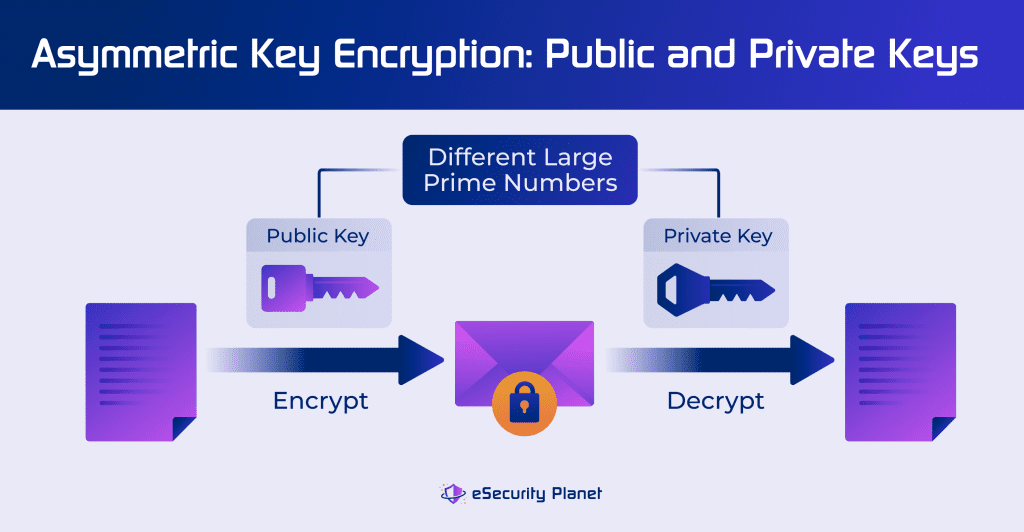
Although more complicated and expensive to implement, asymmetric encryption ensures secure communications over distributed networks without exposing the encryption keys to theft. Asymmetric encryption does not use multiple rounds for encryption but instead uses variable-length, large sized prime numbers.
The larger key sizes and prime number calculations can take much longer to process than symmetric encryption; however, asymmetric algorithm public keys can be published to enable much more secure sharing of encrypted files.
The asymmetry of the algorithm enables either of the keys to encrypt the data, but that same key cannot be used for decryption. Typical examples of use include:
- Sender encrypts data with recipient’s public key; recipient decrypts data with their private key.
- Sender encrypts data with their own private key to verify the source of a document and re-encrypts the data with the recipient’s public key for security; the recipient uses their private key to access the message and uses the sender’s public key to decrypt the message.
| Symmetric | Asymmetric | |
|---|---|---|
| Keys | 1 – Private | 2 – Public and Private |
| Bits | 128 – 192 – 256 | 2,048 – 4,096 |
| Speed | Faster | Slower |
| Overhead | Less complex and expensive and use less memory and processing power | More complex and expensive and use more memory and processing power |
| Security Risk | Vulnerable to key theft, should not be used for sharing encrypted data, quantum computers can guess keys | Quantum computers can guess keys |
| Examples | AES, Blowfish, 3DES | DHM, RSA, ECC |
| Use Cases | Full drive encryption, WiFi data encryption | Website communication, proving identity |
Symmetric + Asymmetric Encryption
Software developers and organizations increasingly use both symmetric and asymmetric encryption methods to give users speed and security in communication. A common example is the standard Transfer Layer Security (TLS) protocol used to enable secure website browsing.
Also known as hybrid encryption, the bundle of the two methods usually starts with a handshake between users through asymmetric cryptography to establish security. Within the asymmetric connection, parties then securely share symmetric algorithms keys to enable faster processing of messages.
Homomorphic Encryption
Homomorphic encryption allows for a set of limited operations on ciphertext without decrypting the message. Homomorphic models include:
- Partial homomorphic encryption (PHE) for algorithms that can perform a single operation on encrypted data.
- Somewhat homomorphic encryption (SHE) for algorithms capable of performing two operations on encrypted data.
- Fully homomorphic encryption (FHE) for algorithms capable of the broadest range of operations on encrypted data.
Google, IBM, and Microsoft continue to explore FHE capabilities to process specific data while maintaining its secrecy and have released open-source encryption libraries. However, these techniques lack widespread adoption or incorporation into commercial tools.
Block Ciphers
Encryption algorithms operate on chunks of data to render them unreadable without a proper decryption key. Block cipher encryption uses fixed-sized blocks of data such as 128 or 64 bit blocks. Many symmetric algorithms are block ciphers; asymmetric algorithms use different key lengths, so technically they are not block ciphers because there is a variable block length between the public and private keys.
When the plaintext to be encrypted is shorter than the block length, the data is padded by the algorithm to reach the block length before encryption. Data longer than the block length will be broken into smaller blocks prior to encryption and also padded if the smaller blocks fall below the block size.
A weakness of block ciphers is that encryption of identical, full-sized plaintext blocks can yield identical encrypted blocks, which can enable brute force detection of keys. Algorithms avoid this issue by using multiple passes of different block sizes or by applying variable-input-length algorithms to the data before it is processed by the encryption algorithm.
Format-Preserving Encryption (FPE)
The category of format-preserving encryption addresses the storage of encrypted data in legacy databases with strictly defined formats and field lengths. These databases cannot tolerate variances caused by many encryption algorithms that intentionally add padding to short encryption to obscure the length of the original data or convert both letters and numbers into hexadecimal code.
For example, the Social Security number “111-11-1111” might be encoded into the plaintext numeric code of “049049 049049 049049 049049 049,” which cannot be used in a database with a limit of 9 characters. Format preserving algorithms will instead transform the number into a 9-character numeric string so that the database utility will be preserved.
Format-preserving encryption can use existing encryption algorithms, such as AES (see below). However, programmers typically incorporate specially designed algorithms so specialized that we will not cover them in more detail in this article, such as the Thorp Shuffle, Variable Input Length (VIL) Ciphers, and the Hasty Pudding Cipher.
Streaming Ciphers
When sending data through a high-speed router or switch, the full size of the data will be unknown. Storing the data until it reaches a specific block size can cause unacceptable delays for processing and transmission.
Streaming ciphers solve the problem by using a key to encrypt data one bit at a time. Streaming ciphers are symmetric algorithms that use a secret key to feed a random number generator. Asymmetric keys cannot usually be used for streaming encryption because the block sizes cannot be known. The wired equivalent privacy (WEP) and Wi-Fi protected access (WPA) algorithms incorporate streaming ciphers to encode Wi-fi data transmissions.
Not Really Encryption: Hashing
Although associated with the verification of the integrity of a file, hashing algorithms such as the 128-bit message digest algorithm (MD-5) or the eight 32-bit-word secure hash algorithm (SHA-256) do not change the data of a file. Instead, the algorithm analyzes the bits of the contents to create a single number that represents the contents.
An added space or deleted letter will create a completely different hash value for a file, so hash values will often be used to verify that a file has not been altered during a copying or transmission process. However, since hashing algorithms leave the data in plaintext, hashing does not defend the data against unauthorized access.
Encryption Algorithm Types
Encryption algorithms are defined by the specific math formulas and the process required to perform an encryption transformation. While cryptologists develop many different algorithms, this article will focus on the main encryption algorithms adopted for use in IT data encryption:
- DES
- 3DES
- Blowfish
- Twofish
- DHM
- RSA
- AES
- ECC
- Post-quantum
DES: The Data Encryption Standard
The need for a government-wide standard to encrypt sensitive information became evident as early as 1973. The U.S. National Bureau of Standards (now the National Institute of Standards and Technology, or NIST) made a public request for potential ciphers.
IBM and lead cryptographer Horst Feistel soon proposed a symmetric-key block cipher algorithm that became called the Data Encryption Standard (DES). By the 1990s, DES received wide criticism for its vulnerability to brute force attacks and its short key size.
- Significance: First US national encryption standard
- Pros: Fast, easy to use
- Cons: Vulnerable to brute force attacks as early as the 1990s
- Used for: Obsolete, replaced by TDES
| Key Sizes | Block Sizes | Rounds | Structure |
|---|---|---|---|
| 56 bits (+ 1 bit for parity) | 64 bits | 16 | Feistel |
TDES: The Triple Data Encryption Standard
Triple DES (TDES), or 3-DES, improves upon the original DES encryption algorithm with three stages of encryption using three different keys:
- Stage 1: Key 1 used to encrypt plaintext data.
- Stage 2: Key 2 used to decrypt the encrypted data from step 1 to create a new document (does not reproduce original document; it will not be readable in this form).
- Stage 3: Key 3 used to re-crypt the data from step 2 to produce another encrypted document.
The symmetric block cipher TDES provides a dramatic improvement in strength over DES, but TDES has since been replaced by AES (see below). New applications no longer use TDES, but TDES-encrypted data can be found in legacy environments and Microsoft only retired 3DES from use within Office 365 in 2019.
- Significance: Replaced DES
- Pros: Much stronger than DES
- Cons: Remains vulnerable to brute force attacks, quantum attacks
- Used for: Obsolete, replaced by AES, however, legacy use remains for ATM pins, UNIX passwords, older payment systems
| Key Sizes | Block Sizes | Rounds | Structure |
|---|---|---|---|
| 112 or 168 bits | 64 bits | 16 rounds per stage | Feistel |
Blowfish
Bruce Schneier developed the symmetric block cipher Blowfish to replace the DES in 1993. The Blowfish encryption algorithm was released to the public without a required license and is known for its flexibility, speed, and resilience compared to other older encryption standards.
The algorithm uses 64-bit block sizes and encrypts them individually over 16 rounds using a key length between 32 and 448 bits. Each round consists of four actions that further scramble the data for encryption processing. This standard is not recommended to be used on files greater than 4 GB due to its small block size.
- Significance: Early open-source encryption tool, replaced by Twofish
- Pros: Fast, fairly secure, free
- Cons: Vulnerable to brute force and quantum attacks, slow for key changes
- Used for: Still in use for password management; file and disk encryption; older Secure Shell (SSH) protocol tools (OpenSSH, PuTTY, etc.); and is embedded in Linux and OpenBSD operating systems
| Key Sizes | Block Sizes | Rounds | Structure |
|---|---|---|---|
| 32 to 448 bits | 64 bits | 16 | Feistel |
Twofish
Twofish offers a next generation version of Blowfish developed in 1998 that uses keys between 128 and 256 bits long, block sizes between 128 and 256 bits, and 16 rounds of encryption. While more complex than Blowfish, the symmetric block cipher encryption is optimized for 32 bit CPUs, which enables better performance.
As with Blowfish, Twofish has also been made available in the public domain, allowing free use and incorporation of the algorithm into applications. While competitive with AES in speed on generic hardware, AES can be significantly faster using AES hardware acceleration.
- Significance: Replaced Blowfish, but remains smaller in adoption
- Pros: Stronger encryption than Blowfish, fast performance
- Cons: Not as fast as AES with hardware accelerators, theoretically vulnerable to quantum brute force attacks
- Used for: File and folder encryption
| Key Sizes | Block Sizes | Rounds | Structure |
|---|---|---|---|
| 128, 192, or 256 bits | 128 to 256 bits | 16 | Feistel |
DHM: Diffie-Hellman-Merkle Introduces Key Exchange

Shortly after the release of DES, three computer scientists – Whitfield Diffie, Martin Hellman, and Ralph Merkle – published their research on public-private key cryptography in 1976. Their Diffie-Hellman-Merkle (DHM) key exchange pioneered asymmetric encryption and supported much longer key lengths of 2,048 to 4,096 bits.
- Significance: First asymmetric encryption algorithm published
- Pros: More secure for sharing information than symmetric algorithms
- Cons: Not widely adopted, more resource intensive, vulnerable to brute force attack
- Used for: Not widely adopted
RSA Encryption
A year after DHM’s release, three cryptographers – Ron Rivest, Adi Shamir, and Leonard Adleman – developed the asymmetric RSA public-key cryptosystem. The three innovators and MIT patented the RSA algorithm, a proprietary system available through RSA Security until its public release in 2000. The RSA algorithm remains the most popular public key cryptographic system today and introduced the concept of digital signatures for authentication outside of academia.

RSA depends on multiplying two very large randomized prime numbers to create a third, even larger prime number. While it’s very difficult for most computers to factor these prime numbers quickly, the algorithm has been found vulnerable to quantum computing attacks and tends to be a slow algorithm to implement. The algorithm is now in the public domain and RSA calculators websites can be used to examine how the process works.
- Significance: First commercially available public key, asymmetric algorithm
- Pros: Enables secure sharing
- Cons: Slow to implement, vulnerable to brute force attacks (especially quantum-powered)
- Used for: Secure messaging, payments, small encrypted files
AES: The Advanced Encryption Standard
In 1997, the NIST renewed its call to the public cryptography community for the successor to DES. Two Dutch cryptographers – Joan Daemen and Vincent Rijmen – submitted the eventual pick known as Rijndael. By 2001, the NIST dubbed it the Advanced Encryption Standard (AES) and officially replaced the use of DES. AES offered larger and different key sizes with a family of ciphers to choose from and remains one of the most popular standards over 20 years later. AES encrypts data over 10-14 rounds in block sizes of 128 bits and with key sizes between 128 and 256 bits.
While both DES and AES use symmetric block ciphers, AES uses a substitution-permutation network wherein plaintext goes through multiple rounds of substitution (S-box) and permutation (P-box) before finalizing the ciphertext block. Similarly, a client or application can decrypt the AES message by reversing these S-box and P-box transformations.
Most organizations use one of the AES algorithms for file encryption, full-disk encryption, application encryption, wifi transmission encryption, virtual public network (VPN) encryption, and encrypted protocols such as transport layer security (TLS).
- Significance: Most widely adopted symmetric, block cipher algorithm
- Pros: More secure than legacy encryption, faster than asymmetric options
- Cons: Vulnerable to key theft and brute force attacks
- Used for: Protocols, VPN, full-disk encryption, Wi-Fi transmission encryption
| Key Sizes | Block Sizes | Rounds | Structure |
|---|---|---|---|
| 128, 192, 256 bits | 128 bits | 10, 12, 14 | SP-network |
ECC: Elliptic-Curve Cryptography
Professors at the University of Washington and Columbia University independently published research in 1985 on elliptic curve cryptography (ECC), but it didn’t come into widespread implementation until the mid-2000s. Like RSA, ECC is an asymmetric encryption algorithm, but instead of using prime numbers, it uses elliptic curves to generate public and private keys.
The use of elliptic curves enables equivalent security with smaller key sizes than RSA, which enables faster execution of the encryption and decryption algorithms. ECC has proven to be a popular alternative choice to RSA but has also been found to be vulnerable to threats such as twist-security and side-channel attacks.
- Significance: Popular asymmetric encryption alternative to RSA
- Pros: Faster than RSA and uses smaller key sizes, more secure for sharing than symmetric encryption algorithms
- Cons: Vulnerable to twist-security, side-channel, and quantum-powered attacks
- Used for: Email encryption, cryptocurrency digital signatures, internet communication protocols
What Is Next? Post-Quantum Cryptography
Based on quantum mechanics rather than mathematical operations, quantum computers can utilize Shor’s algorithm to find prime factors much more rapidly than traditional computers. This allows an attacker with access to a large enough quantum computer to break asymmetric standards like DHM, RSA, and ECC by determining an organization’s private key from the public key.
Although not commonly available, the development of quantum computers is seen as a near future certainty. Data stolen today may be securely encrypted using today’s standards and uncrackable for the next 5-10 years. However, if the attacker who stole the information gains access to affordable quantum computing resources in the future, the encryption may easily be broken.
Post-quantum cryptography (PQC) describes research, algorithms, and vendors developed to address quantum attacks and secure the next generation of IT environments and data. The NIST and the US National Security Agency (NSA) started to release algorithms and resources in 2022 against quantum threats.
Still, research remains in early stages, so initial standards remain in draft form and a full mitigation architecture for federal agencies isn’t expected until the 2030s. Currently, the four recognized algorithms include:
- CRYSTALS-Kyber (FIPS 203) defines an algorithm incorporated into an asymmetric key encapsulation mechanism (KEM) standard designed to allow for quantum-resistant sharing of secure keys over public channels.
- CRYSTALS-Dilithium (FIPS 204) defines an algorithm incorporated into a standard to create quantum-resistant digital signature schemes to verify sources and identities.
- SPHINCS+ (FIPS 205) defines an algorithm incorporated into a stateless hash-based, quantum-resistant digital signature standard to verify sources and identities.
- FALCON (FIPS pending) will define an algorithm and a digital signature standard based on fast-fourier lattices.
Encryption Tool Types
Information technology uses encryption to protect data at rest and data in transit in many different ways. The broadest applications of encryption include:
- Encrypted data transmission protocols
- Full disk encryption
- File encryption
- Email encryption
- Application Embedded Encryption
- Digital certificates
While these are the solutions most often purchased and deployed, encryption can also be found incorporated into security solutions such as cloud access security brokers (CASB), next-generation firewalls (NGFW), password managers, virtual private networks (VPN), and web application firewalls (WAF).
Encrypted Data Transmission Protocols
Many fundamental protocols incorporate encryption into their programming to provide universal protection invisible to most users. Major protocols include:
- DomainKeys Identified Mail (DKIM) enables the authentication of email senders by hosting a public key for an encrypted block of text in sent emails.
- Internet protocol security (IPSec) provides encryption at the IP packet level and creates a secure tunnel for packets belonging to multiple users and hosts.
- Kerberos provides single sign-on and user authentication against a central authentication and key distribution server by distributing authenticated tickets for securing and supporting authentication on a local area network.
- Layer 2 Tunneling Protocol (L2TP) provides a framework for doubly-encrypted transmission of data using an encrypted tunnel between devices.
- Secure/Multipurpose Internet Mail Extension (S/MIME) upgrades email security.
- Secure Shell (SSH) secures remote terminals and provides support for single sign-on and secure tunneling for TCP streams.
- Transmission Control Protocol (TCP) adds encryption, server authentication, and client authentication to communication between devices and applications and enables HTTPS connections.
Full Disk Encryption
To protect data at rest, an entire hard drive can be encapsulated within an encrypted container. This feature can be included in firmware, in operating systems, or as a feature in open-source, shareware, or commercial applications.
Full-disk encryption protects against the theft of the device or hard drive when they are powered down by rendering the contents of the device unreadable without the security key. However, these applications typically use symmetric encryption and are vulnerable to stolen keys. Additionally, full-disk encryption does not protect against data theft from the device when the device is powered on and the data is unencrypted for use.
File Encryption
File encryption protects data at rest while the device is powered on and the data is otherwise available for use. Encryption is applied on either a folder or individual file basis and decryption is applied as needed when the information is required.
File encryption tends to require more user interaction and is more difficult to apply on a universal basis than full disk encryption. File encryption can add strong security, but it remains vulnerable to stolen passwords and can be more vulnerable to lost passwords than full disk encryption, which may have an admin password established by IT.
Email Encryption
Email encryption places email content in encrypted containers for safe transmission using unencrypted email protocols. Email encryption options exist within major email tools, but many organizations choose to deploy additional tools with more robust options for deployment or encryption.
Application Embedded Encryption
Applications such as databases, websites, and other programs can incorporate encryption within the programming to protect data. Databases offer the most varied types of encryption for fields, columns, or entire database storage instances. Other types of encryption can detect and encrypt specific data types, such as credit card numbers and Social Security numbers, throughout the application.
Digital Certificates
Digital certificates provide publicly published keys that can be used to verify identity or to encrypt and decrypt information. Certificates must be maintained with current information and replaced before they expire.
How to Choose an Encryption Type or Algorithm
When selecting encryption types, enterprises should first consider their security requirements based upon the organization’s risk. Risk defines the most important data in the organization from a financial, operational, and regulatory perspective, which aids in determining where and how encryption can protect that data.
Effective risk analysis requires effective classification of data, an accurate inventory of data locations, and an effective picture of how the most important data flows through the organization. The risk analysis will determine the security needs, and then a range of encryption solutions should be considered, not just the type of tool that is most commonly used or the most convenient to apply.
The top features of a commercial tool (other than cost) to consider include:
- Centralized policy management
- Speed of the tool
- Key management and automation
- Support for hardware-based cryptographic acceleration
- Ability to report for compliance
- Monitoring, logging, and auditing capabilities
- Operating system (OS) support
- Installation and configuration processes
- Impact on operations and user experience
- Encryption algorithm options
- Legacy encryption support
Unfortunately, encryption can result in loss of functionality, decreased performance, and even lost data, depending upon factors such as:
- User error
- Memory and hard drive requirements vs. available resources
- Required changes to infrastructure
- Required changes to devices
Solutions that require extensive changes to the infrastructure and end user devices should generally be used only when other options cannot meet the enterprise’s security needs. After selecting a tool, an organization may have the option to select from multiple available security algorithms. They should consider whether this algorithm is current or obsolete, is validated or untested, and suits the use case.
In addition to tool and algorithm considerations, an organization should also consider the way in which the encryption can be obtained and the economic consequences:
- Direct tool purchase offers the potential for one-time pricing and professional customer support but can become obsolete or may be narrowly focused.
- Open-source software will generally be free but will lack professional customer support, require the most resources to implement, may become obsolete, and will usually be narrowly focused on how it can be used.
- Add-on encryption is often a service provided by specific vendors for specific use cases, such as a cloud provider’s cloud storage encryption added to protect cloud resources.
- Encryption as a service offers a broad range of encryption options, will be continuously updated, and requires the least effort to manage; however, this option involves giving up control of company secrets to an outside party.
The selection of a tool can be a collaborative and iterative process. Affected users should be involved in testing encryption tools and deployment can be rolled out in stages to avoid disruptions and data loss. As with security, encryption should be applied in layers appropriate for the use: database, local file, email, or entire drives.
Bottom Line: Encryption Adds a Strong Layer to a Security Stack
Encryption may be required by compliance standards and customers expect important data will be encrypted for protection and to guard against theft. However, encryption alone will not fully protect valuable data. Encryption provides a very strong layer of defense, but it should complement a full security stack of solutions and services to protect servers, endpoints, network connections, applications, and more.
To read more about encryption, consider:
This article was originally written by Sam Ingalls and published on May 26, 2022. It was updated by Chad Kime on December 7, 2023.




