This past week, both JetBrains TeamCity and Atlassian Confluence products have run into more hiccups as their string of vulnerabilities continues. Apple’s also had plenty to patch, and Cisco, OpenEdge, and VMware appeared in the news, too. JetBrains and Atlassian users should pay special attention since vulnerabilities continue cropping up in the same products. And all IT and security teams should follow vulnerability news for vendor bulletins and updates.
March 4, 2024
JetBrains Server Issues Continue with New Vulnerabilities
Type of vulnerability: Authentication bypass.
The problem: Two authentication bypass vulnerabilities, CVE-2024-27198 and CVE-2024-27199, allow unauthenticated attackers to exploit JetBrains TeamCity servers. The more severe CVE-2024-27198 allows a threat actor to take over the entire server. Researchers at Rapid7 discovered these vulnerabilities in late February and released information regarding them on March 4.
These are different JetBrains vulnerabilities than the ones mentioned in past recaps. We’ve seen multiple over the last couple of months, but these are new and not to be confused with CVEs from 2023. Potential exploits of the new vulnerabilities can include remote code execution on TeamCity servers.
JetBrains released a detailed blog post explaining the specific timeline of discovering the vulnerabilities, the conflict with Rapid7, and JetBrains’ stance on releasing vulnerability information. Its position is that immediately releasing vulnerability data to the public allows threat actors to exploit the issues before customers have sufficient time to patch them.
However, Rapid7’s policy holds that silent patching limits the ways experienced IT pros can participate in protecting networks and information systems. Because of these differences, JetBrains decided not to coordinate with Rapid7 in disclosing the vulnerability information.
The fix: Deploy JetBrains TeamCity version 2023.11.4 to all servers that can support it. This release includes installation files and updated Docker images. According to JetBrains’ blog post, the new version and the related security patch plug-in solves both authentication bypass vulnerabilities.
March 5, 2024
New Apple Vulnerabilities Necessitate Rapid Patching
Type of vulnerability: Multiple issues, including kernel security bypass vulnerabilities.
The problem: On March 5, Apple released a security notice for its new operating systems, iOS 17.4 and iPadOS 17.4. These new OS versions fixed multiple CVEs. Two of the more severe vulnerabilities are CVE-2024-23225, found in Kernel, and CVE-2024-23296, found in RealtimeKit (RTKit). Both vulnerabilities allow an attacker to bypass standard kernel memory protections when the attacker has arbitrary read and write capabilities within the kernel.
Other CVEs fixed in the new update included CVE-2024-23243, which allowed an application to potentially view sensitive location data, and CVE-2024-23262, which allowed an application to potentially spoof system notifications and the user interface.
The fix: Deploy iOS 17.4 and iPadOS 17.4 to all devices that will support them as soon as possible. These releases fix over 30 vulnerabilities.
If your business doesn’t have a good method of quickly finding vulnerabilities, consider investing in a vulnerability scanning product specifically designed for websites, applications, or DevOps use cases.
VMware Vulnerability Affects ESXi, Workstation & Fusion
Type of vulnerability: Use-after-free vulnerability potentially leading to code execution.
The problem: CVE-2024-22252, a use-after-free vulnerability, could allow a threat actor to execute code using admin privileges on a VMware virtual machine. This issue affects VMware ESXi, Workstation, and Fusion. According to the National Instutite of Standards and Technology, the exploitation is contained within the VMX sandbox in ESXi, but in Workstation and Fusion, the vulnerability could lead to code execution on machines where the products are installed.
Specific products affected include:
- VMware ESXi
- VMware Workstation Pro / Player (Workstation)
- VMware Fusion Pro / Fusion (Fusion)
- VMware Cloud Foundation (Cloud Foundation)
The fix: VMware created the following table for users so they know which fixed versions to apply:

March 6, 2024
Cisco Offers Fixed Releases for Secure Client Vulnerability
Type of vulnerability: Carriage return line feed (CRLF) injection attack by an unauthenticated remote attacker.
The problem: Cisco’s Secure Client software has a vulnerability, CVE-2024-20337, that allows an attacker to complete a carriage return line feed injection attack. According to Cisco, after exploiting the Secure Client vulnerability, an attacker could execute arbitrary code or access sensitive data in the browser, like valid SAML tokens. Whichever user’s privileges the attacker has exploited could then be used to create a remote access VPN session.
Insufficient validation of user-supplied input causes this vulnerability, according to Cisco. It affects the following products:
- Secure Client for Linux
- Secure Client for macOS
- Secure Client for Windows
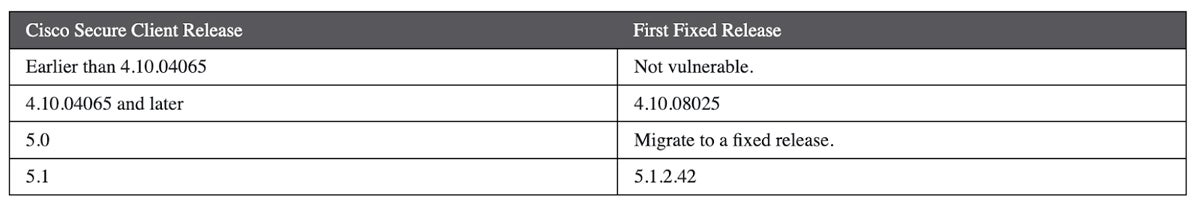
The fix: Cisco provides the following information on fixed software releases:
Proof of Concept Released for OpenEdge Vulnerabilities
Type of vulnerability: Potential authentication bypass.
The problem: Progress Software’s OpenEdge Authentication Gateway and AdminServer have a vulnerability in the following versions:
- OpenEdge Release 11.7.18 and earlier
- OpenEdge 12.2.13 and earlier
- OpenEdge 12.8.0
According to Progress, when OpenEdge Authentication Gateway “is configured with an OpenEdge Domain that uses the OS local authentication provider to grant user-id and password logins on operating platforms supported by active releases of OpenEdge, a vulnerability in the authentication routines may lead to unauthorized access on attempted logins.”
The same unauthorized login access can occur when OpenEdge Explorer (OEE) and OpenEdge Management (OEM) connect to AdminServer. The vulnerability, CVE-2024-1403, has a critical severity rating.
Progress also notes that AdminServer logins are always vulnerable because they only support OS local logins. OpenEdge Authentication Gateway is only vulnerable to authentication bypass when admins configure OpenEdge domains to use the operating system’s local authentication provider.
Progress released the notice in late February; on March 6, Horizon3AI released a proof of concept for an OpenEdge exploit. The proof of concept is available on GitHub for interested users, as well as a longer blog post that provides detailed code information and walks pros through Horizon3AI’s process.
The fix: Progress Software has released the following versions of OpenEdge LTS, in which the vulnerability is fixed:
- 11.7.19
- 12.2.14
- 12.8.1
March 8, 2024
Exploits of Confluence Vulnerabilities Continue
Type of attack: Remote code execution.
The problem: CVE-2023-22527, a remote code execution vulnerability in outdated versions of Atlassian Confluence Data Center and Confluence Server, is currently being actively exploited. Atlassian disclosed the vulnerability in January, but threat actors continue to capitalize on the issue: VulnCheck recently published a blog post and noted that the vulnerability has at least 30 unique exploits, as of March 8.
VulnCheck also observed that multiple instances of exploitation use freemarker.template.utility.Execute, which will easily be picked up by endpoint detection and response platforms.
The vulnerability affects the following Confluence Data Center and Server versions:
- 8.0.x
- 8.1.x
- 8.2.x
- 8.3.x
- 8.4.x
- 8.5.0-8.5.3
The fix: Atlassian recommends updating your instance of Confluence Data Center or Confluence Server to one of the most recent versions:
- Confluence Data Center and Server:
- 8.5.4 (LTS)
- 8.5.5 (LTS)
- Confluence Data Center only:
- 8.6.0 (Data Center Only)
- 8.7.1 (Data Center Only)
- 8.7.2 (Data Center Only)
Read next:
- VulnRecap 3/4/24 – Ivanti, Ubiquiti, AppLocker Under Attack
- 6 Best Vulnerability Management Software & Systems in 2024










