Kali Linux turns 10 this year, and to celebrate, the Linux penetration testing distribution has added defensive security tools to its arsenal of open-source security tools.
It remains to be seen if Kali Purple will do for defensive open source security tools what Kali Linux has done for open source pentesting, but the addition of more than 100 open source tools for SIEM, incident response, intrusion detection and more should raise the profile of those defensive tools.
For now, Kali is primarily known for its roughly 600 open source pentesting tools, allowing pentesters to easily install a full range of offensive security tools.
In this article, we’ll focus primarily on how to use this powerful OS to run a pentest and mistakes to avoid. We’ll give you an overview of what can be achieved with Kali Linux using a short selection of pre-installed tools. While this guide serves as an introduction to common pentesting phases, with practical examples that highlight best practices, it’s not a substitution for a complete professional pentesting methodology.
Also read:
- 24 Top Open Source Penetration Testing Tools
- What Is Penetration Testing? Complete Guide & Steps
- How to Implement a Penetration Testing Program in 10 Steps
- What Is a Pentest Framework? Top 7 Frameworks Explained
Table of Contents
What is Kali Linux?
Kali Linux is a popular pentesting distribution maintained by Offensive Security (OffSec), a 15-year-old private security company. Kali contains scanners, sniffers, and many other attacking tools.
The OS can power a full pentest session or more specific attacks. While there are many other pentesting distributions, Kali is the top one recommended by professionals.
Indeed, most of its pre-installed packages are available as standalone packages, but Kali incorporates and maintains high-quality solutions that are meant for professional usage.
The idea behind the operating system is to have a comprehensive toolbox that is relatively easy to update while following the best standards in the industry.
Kali is built for pentesting only. That’s why you won’t want to install it as a primary OS unless your machine is dedicated to pentesting or it’s a virtual machine.
What’s new in Kali Linux in 2023?
There have been three quarterly releases thus far in 2023, with the first one by far the most eventful.
Kali 2023.1, released in March, introduced a new kernel version and eight new packages, including CyberChef, which is a pretty convenient interface to decipher, decrypt, and decode various strings and hashes with granularity and accuracy.
The release also included a temporary patch to make sure that Python and its PIP package manager worked with Debian’s upcoming Stable release, as Kali is a Debian-based distribution. A bug with Nvidia drivers and some specific GPU models might cause all affected Linux devices to become slow or freeze; a fix was expected.
But the biggest change in Kali Linux 2023.1 was the addition of the Purple Edition for defensive security, which we’ll cover further down.
Kali 2023.2, released May 30, added a Hyper-V VM image that should be much easier for users, requiring no configuration. In addition to other changes, the 2023.2 release added 13 new tools, including a few container and SBOM tools, the Evilginx man-in-the-middle attack framework, the GoPhish open-source phishing toolkit, and TheHive open source incident response platform, among other interesting tools.
Kali’s third-quarter release, 2023.3, dropped on Aug. 23, and the main focus was changes to Kali’s internal infrastructure to coincide with the release of Debian 12. Kali Autopilot, an automated attack framework that debuted with Kali Purple, got a redesigned GUI and other new features.
Kali Linux 2023.3 also added 9 new tools, ranging from cloud and container security to automated pentesting tools, and replaced two tools that are no longer actively supported.
Is Kali beginner-friendly?
Kali is available for anyone. It’s free and open-source, so anyone can download it. It’s a good idea to try things on your own and then read the documentation or tutorials.
However, is it a good place for beginners to start? While Kali IS beginner-friendly, professional pentesting is not something you can improvise. It requires knowledge and planning to be effective.
Here are some requirements for becoming a good pentester:
- Mastery of pentesting basics: legal aspects, scopes, essential steps (such as passive recon, network discovery, enumeration, privilege escalation), post-exploitation, and persistence
- Mastery of the network layers (the OSI model, IP, subnets, and more)
- Mastery of Windows and Linux systems
- Proficiency in Python and some programming languages (like Go, C, C++, Ruby); in my opinion, this isn’t optional, but some security specialists might say otherwise
Some people learn faster than others, but there’s a massive range of tools and concepts to know, so it will take time regardless of your learning skills or speed.
Getting Started: How to Install Kali Linux
Kali Linux is remarkably easy to install. The “Get Kali” page lists various installation modes, with pre-configured images and ready-to-use virtual machines.
Virtual machines are perfect for a quick intro. Feel free to test them, even if it’s just to see what the OS looks like.
Most operating systems are supported, and you’ll find Docker containers, and even support for Android and Raspberry Pi. Windows users can install Kali using the Windows Subsystem (WSL2), for example.
The bare metal installation is not recommended for beginners, though.
You can flash ISO images on an external drive to install Kali on the device of your choice by booting from that drive.
You can also run Kali in live mode with the live distributions without installing it on your device.
Mistakes to avoid with Kali Linux
Without proper knowledge, your pentest will likely fail, as there’s no magic recipe you can apply blindly regardless of how good your tools are.
Besides, attacking tools can send multiple probes or headers along with their requests (e.g., during scanning and discovery), which can be detected and blocked by security tools. Note that Kali won’t hide your IP or cover your fingerprints automagically. You may use a VPN or install utilities to capture and forward traffic to other subnets, or configure proxychains.
You may also leverage external platforms like Linode for your setup and operations.
However, if you are a complete newbie, my advice is to not rush on the tools, and to start with free open-source projects to attack, like the Juice Shop or many other vulnerable applications that are meant to help you learn cybersecurity.
Then you might want to learn more advanced techniques or to invest in dedicated online training programs (see the final section of this article).
Pentesting is not just about servers and web apps
A penetration test aims to emulate a real attack on a targeted system. It’s actually a broad term that covers a wide range of tests and procedures, not just for web apps, and organizations can leverage regular pentests to improve their security and fix critical vulnerabilities.
Unlike vulnerability assessments, pentests involve exploitation, which means you, as an attacker, will hack the system, for real, according to the rules defined before the test. The ultimate goal is to write a good report that provides recommendations.
Note that your pentest is not an exhaustive analysis, as you will likely have limited time and only need one working exploit to achieve your mission.
It’s important to bear in mind that pentesting is not limited to hacking vulnerable servers that host apps and databases. There are multiple other attack angles to test, including:
- Network compromises
- Social engineering (e.g., phishing)
- Memory corruptions
- Wi-Fi attacks
Kali is a wonderful toolbox, because it has tools for a wide range of pentests. Web apps are good for learning because many web servers are vulnerable and expose a large surface to attackers, as organizations have to expose their network to the public.
However, if it’s necessary (and in the contract), a pentester can perform physical attacks too.
Don’t neglect the legal aspects
Laws are not the same everywhere, which means the same procedures can be legal in some countries and illegal in others. It’s especially true if you compare the EU to the U.S.
As far as I know, “Ethical hacking” is not a legally protected status. Legitimate security researchers have been sued after demonstrating critical vulnerabilities.
Scope is essential for distinguishing a pentest from a real attack. Of course, you need an explicit consent, which is usually a legal agreement, to run a pentest, but you must also define the scope very precisely before the operation.
Last but not least, installing Kali Linux at work without permission would raise liabilities too. The distribution contains sensitive programs that can expose your organization, not to mention jeopardize your employment.
Using Kali Linux: Finding Tools
There are literally hundreds of Kali Linux tools for various purposes. Beginners can start with very popular packages for classic and recurrent tasks, or they could ask security pros for their favorite tools.
While the list of tools can provide some hints, it can be confusing for beginners. Here’s a range of pentest tasks and the appropriate Kali Linux tools:
- OSINT: Use Maltego to gather information, Dmitry for passive recon
- Social Engineering: Use SET (the Social Engineer Toolkit)
- Knowledge base: Use exploitdb
- pentesting framework: Use the Metasploit Framework
- Port scanning: Use Nmap to scan the targeted network and Ndiff to compare Nmap scans (e.g., to see which ports get closed/opened)
- Wireless pentesting: Use Aircrack-ng to crack Wi-Fi, Bettercap for recon and MitM attacks on Wi-Fi and BLE (Bluetooth Low Energy) devices
- Packet sniffing: Use Scapy to manipulate packets, Ettercap is also excellent to perform MitM attacks, and Wireshark is a must-have
- Brute-Force URLs: Use Gobuster or DirBuster to scan URLs (directories, files, and DNS), and Nikto to detect server vulnerabilities
- Web fuzzing: Use Wfuzz
- Web hacking: Use BeEF to exploit XSS and other vulnerabilities with the browser or the Burp Suite to intercept requests
- SQL injections: Use sqlmap to crack vulnerable databases
- WordPress scanning: Use WPscan
- Brute-Force logins remotely: Use Hydra (Hydra GTK for the graphical interface)
- Brute-Force passwords: Use John The Ripper
- Active Directory: Use Mimikatz, Impacket
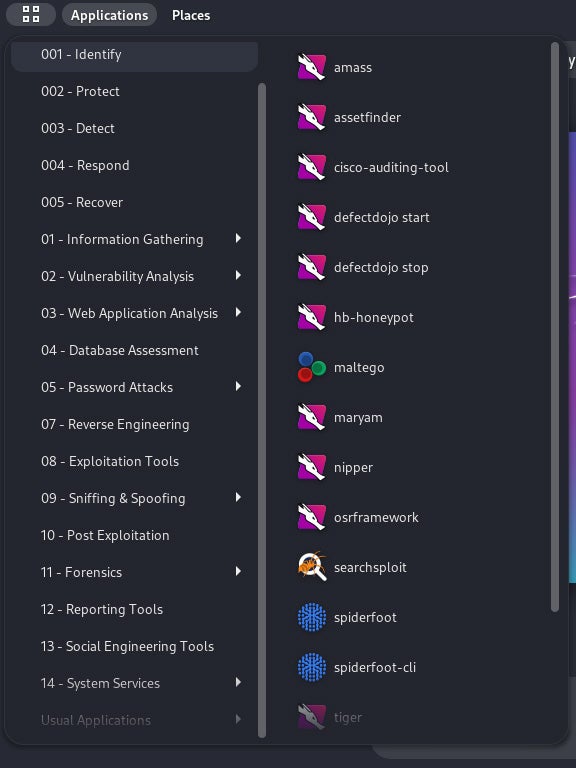
The lists won’t tell you how to use each tool or the right combination to achieve your mission. Once installed, however, Kali Linux sorts packages by categories, which adds some helpful context and labels.
The category usually matches the typical phases of a pentest, like “information gathering” or “post-exploitation,” but also recurrent tasks, such as “password attacks.”
Just open the interactive menu:
Using a Pentesting Framework
The Metasploit Framework can support many steps of your work, from scanning and discovery to exploitation, and even post-exploitation.
On Kali, just open the interactive menu or type “msfconsole” in the terminal to start the console.
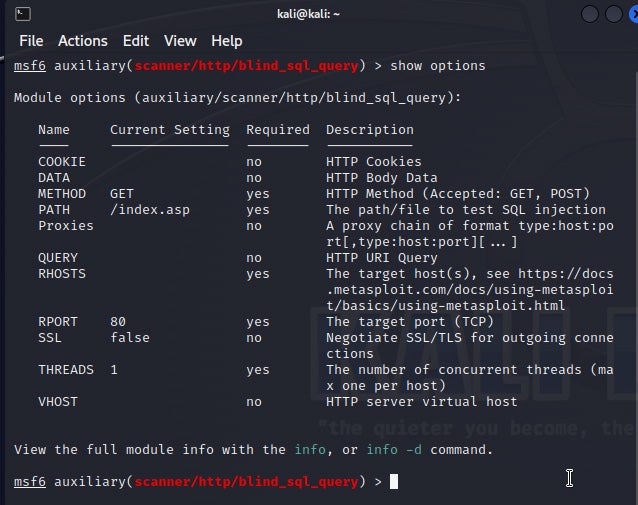
The console is verbose, so you’ll know quickly whether the exploit has succeeded. In my experience, the interface provides advanced payload capabilities and a standardized way to use very different hacking modules.
Note that you don’t have to use a framework, but you’ll have to combine several other pre-installed resources to achieve similar results. If you don’t like manual setups (e.g., for listeners) and other repetitive procedures, the console is a great option.
Of course, some cases may require other tools.
Also read: Getting Started With the Metasploit Framework: A Pentesting Tutorial
How To Use Kali Linux for Pentesting
Kali Linux contains many options to help pentesters execute each of the 7 pentesting steps. Here we’ll go through those steps and highlight Kali tools that we’ve found to be particularly helpful.
Step 1: Defining Scope and Goals
Clear goals and scope are critical for the success of your pentest. You and the organization will define the scope and the rules to apply during the test, which ensures there’s no misunderstanding and that there are clear goals.
Your customer will likely have to choose between three common approaches for the test:
- Black box: You operate without any prior access or information about the target and usually focus on gaining initial access
- Gray box: An intermediary approach where you could be given some credentials or internal information just to speed your progression and allow for deeper testing
- White box: These tests are usually longer and focus on the later phases, like post-exploitation or persistence, to challenge the system and see how resilient it is against privilege escalations, insider jobs, or lateral movements
Not all organizations will need a white box test that requires significant time and budget, but it’s sometimes necessary.
You must discuss the timeline and other legal conditions during this step too. It’s critical for your customers to explain in detail what’s allowed and what’s not in a document that will be signed by you and them.
Wild attacks may appear more realistic for beginners, but in practice, it’s not uncommon to whitelist specific IPs that will be used by the pentesters. You need to define a methodology.
Step 2: Recon and OSINT
Reconnaissance, or “recon,” can be either passive or active.
For example, OSINT (Open-source Intelligence) is an indirect way to collect information, whereas Nmap involves active scanning, as you send probes to the targeted network.
Kali has powerful OSINT tools, like Maltego (the community edition is free to use). These programs can help you organize and automate your research.
In any case, you will generally need both passive and active recon during your pentest.
Step 3: Scan and Discover
Let’s say we have an IP/URL to scan. We can use classic Nmap commands to discover services and potential hosts to attack, for example:
nmap -oN nmapscan.txt -v -A {IP/URL}
The -v option is for “verbose” and -A means “aggressive scan,” which is slower and sends more probes to the target, but it’s not problematic here, as we are not in a real case. The -oN option is to export output to a text file with essential results.
If we discover that the server hosts a vulnerable database system, we will attack it.
Step 4: Gain Unauthorized Access and Exploit
SQL injections in a vulnerable database can lead to a Remote Code Execution (RCE).
If we manage to inject malicious SQL queries in the targeted database with sqlmap, we may exploit a typical vulnerability that allows writing files to pass arbitrary commands to the server.
Many exploits consist in uploading a reverse shell, which is basically a “connect-back” channel between your machine and the targeted server.
If such a shell can be opened as a privileged user (e.g., administrator), we’ll get the same privileges for our session!
The root account grants the highest privileges, allowing pretty much any operation while remaining undetected, which is perfect for post-exploitation.
Step 5: Post-exploitation
After exploiting a vulnerability and compromising a network, you may want to show what you can do with it to your customers to prove the impact and the risks associated with the breach.
Metasploit has tons of modules for this purpose, but you can open the interactive menu of Kali Linux to get the full list of post-exploitation tools available:
If it’s a Windows/Active directory environment, Kali has several packages for that, like Mimikatz, a small but powerful utility for Kerberoasting and password dumping, or Impacket, a set of scripts to attack.
Depending on the brief and the size of the organization, you may have to get further access, and progress from the system you’ve just compromised to another.
This technique is called pivoting. You may have to demonstrate that you can maintain access and get deeper into the targeted infrastructure.
Step 6: Clean Up Your Mess
The targeted network must be restored to its original state before you started your operation, which means removing all temporary accounts, scripts, and any other modifications you made on the system.
This phase is usually skipped during a CTF (Capture The Flag event) because the goal is to practice attacking techniques, but in real-world conditions, a pentester must cover all tracks.
Step 7: Report and Make Recommendations
During this step, you will write a report containing the vulnerabilities you’ve just exploited, the potential stolen data, and the recommendations to fix the situation, including technical advice.
The report is the heart of a pentest and a critical document that literally determines the value of your work. It has to be meaningful and readable, so the organization can take concrete decisions to secure its network.
It may contain the following items:
- Techniques used to gather intelligence
- Techniques used to gain unauthorized access
- The threat model and the level of risks
- The estimated value of stolen data and credentials
You must prioritize the most relevant measures. Watch this tutorial by Hackersploit to learn more.
Open-source Alternatives to Kali Linux
There are some alternatives to Kali Linux worth considering.
Parrot OS Security Edition
Parrot OS Security should be very convenient for beginners, with lots of default configurations. Be careful when downloading the archive, though, as Parrot provides a “home edition” that is not meant for pentesting.
You’ll need the “security” edition. It’s still possible to install the home edition and the pentesting tools afterwards, but the security edition is more straightforward.
What I like about Parrot is the ease of use and the privacy-focused approach (no telemetry, anon surf, proxy).
The “Hack The Box Edition” is also worth mentioning. It aims to help beginners quickly set up a machine for a CTF (e.g., on the HTB platform), but you can use it to build a lab or a training environment for other objectives.
Black Arch Linux
You may have read that Arch is for “the real ones” (not beginners), as the installation is said to be more technical compared to many other Linux distros.
That’s not exactly true, as the latest versions are way easier to install compared to the oldest ones. You can now download a “slim” version too.
If you already use Arch, you can “upgrade” your installation to Black Arch with a dedicated installer in minutes.
Linux users may appreciate the core philosophy, which is very different from other distros like Ubuntu or Debian, and the ability to get the latest versions of security packages.

Kali Purple Edition
The Kali “Purple” edition was released recently and ships many popular packages for defensive security, including Yara and DefectDojo. There’s also a large range of forensic and reversing tools to discover.
The team added specific menus that follow the principles of the NIST Cybersecurity Framework: identify, protect, detect, respond, recover.
Users should be aware that this initiative is in its early stages, so you won’t get pre-configured VMs and the large support provided by the standard version.
Of course, you’re not supposed to migrate your current working environment to Purple right now. That would be a pretty crazy move, as this edition is not yet mature.
However, it’s stable enough to be tested, and defenders will certainly appreciate this new flavor despite the inevitable bugs and oversights.
It’s interesting to see OffSec exploring new fields. The Purple edition is aimed at Blue and Purple teams for defensive security, which means it’s a mix of both worlds, red and blue.
You can get more details about Kali Purple in the official wiki.
Resources for Kali Linux Training
Kali Linux requires effort and time. The key is to practice regularly and to learn from professionals in the field if you want to make it a career. An ethical hacking certification may help too.
The following links could help you unlock many skills:
- Kali documentation
- Kali training
- Hackersploit: penetration testing tutorials
- OffSec: OSCP certification
Bottom Line: Kali Linux
Kali Linux deserves its great reputation as a critically important toolkit for pentesters and anyone hoping to become one. If your organization contains critically important data, whether web-facing or internal, pentesting is a cybersecurity best practice you should adopt to find vulnerabilities before the bad guys do. Kali Linux is a great place to start.
Further reading:
- 10 Best Open-Source Vulnerability Scanners for 2023
- Testing & Evaluating SIEM Systems: A Review of Rapid7 InsightIDR
This article was created by Julien Maury on April 7, 2023 and updated by eSecurity Planet Editor Paul Shread on Oct. 5, 2023








