-

Top 40 Cybersecurity Companies You Need to Know 2024
The cybersecurity industry is constantly evolving. Learn about the top cybersecurity companies and what each does best.
-

‘Rapid Reset’ DDoS Attack Hits HTTP/2 Web Servers
A vulnerability in the HTTP/2 protocol dubbed “Rapid Reset” has led to record DDoS attacks on web servers in recent months. Google, AWS and Cloudflare jointly revealed the attacks and vulnerability today, but noted that every modern web server remains vulnerable to the attack technique. Web server vendors and projects also announced mitigation measures and […]
-

Cisco to Acquire Splunk for $28 Billion
In a blockbuster deal that could shake up the cybersecurity market, Cisco announced this morning that it will acquire Splunk for $28 billion. If the deal clears regulatory hurdles, it would give Cisco a big position in the market for centralized cybersecurity management solutions like security information and event management (SIEM) and security orchestration, automation […]
-

Palo Alto Networks PA Series Review: NGFW Features & Cost
Palo Alto Networks boasts a long history of innovation and strong independent test scores, earning our rating as the top overall cybersecurity company. Enterprise security buyers might pay a premium for Palo Alto products, but they can typically buy with confidence. That said, the next-generation firewall (NGFW) market — where we also list Palo Alto […]
-

Security Buyers Are Consolidating Vendors: Gartner Security Summit
Security buyers are consolidating vendors at an unprecedented rate, leading to a number of converged security platforms. Here are the details.
-

Western Digital Cyber Attack a ‘Wake Up Call for ASIC Vendors’
Update: In a statement on the extent of the data breach disclosed last month, Western Digital said it has control of its digital certificate infrastructure and is “equipped to revoke certificates as needed.” “Regarding reports of the potential to fraudulently use digital signing technology allegedly attributed to Western Digital in consumer products, we can confirm […]
-
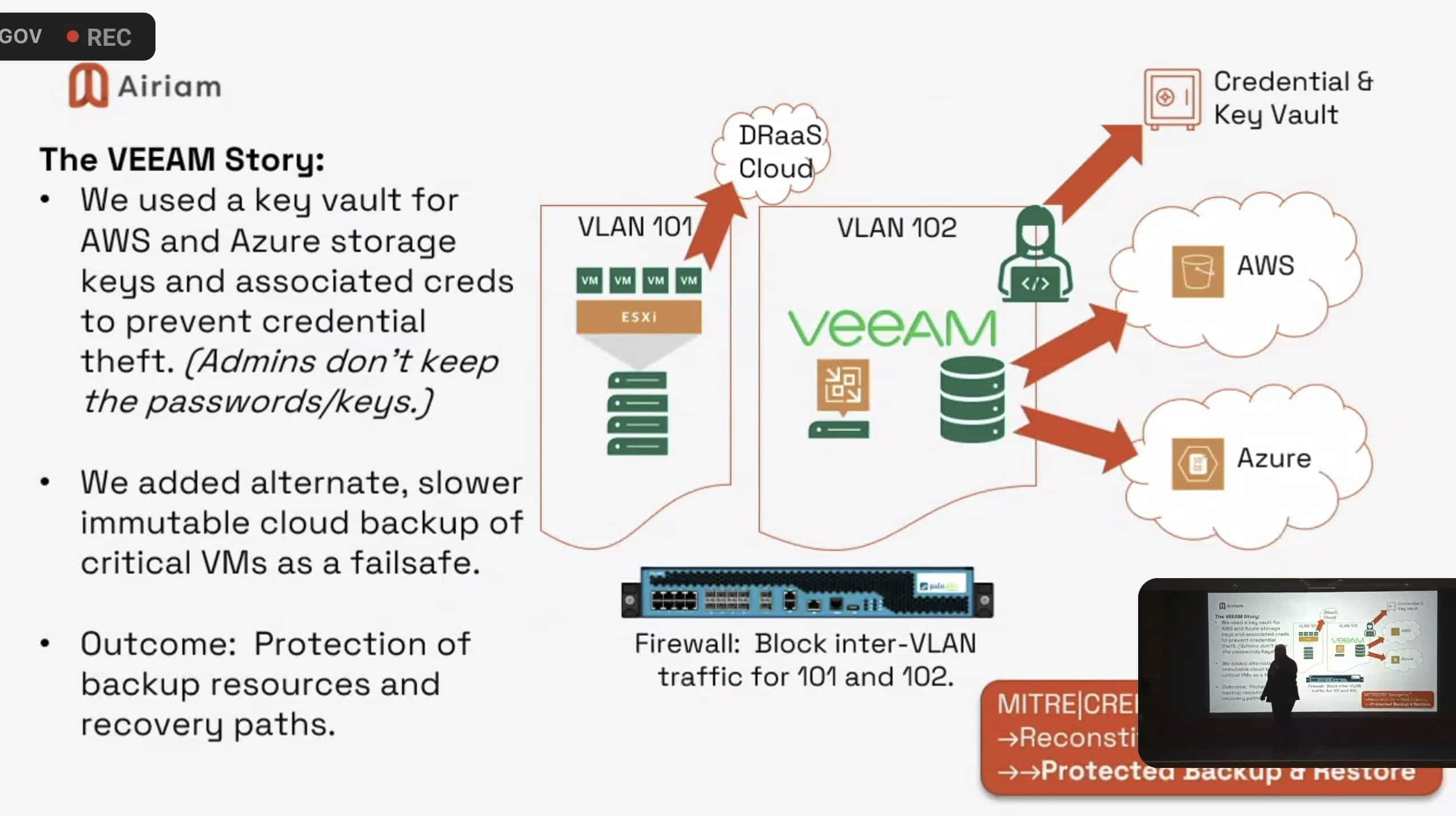
MITRE ResilienCyCon: You Will Be Breached So Be Ready
Speakers at last week’s MITRE ResilienCyCon conference had a surprisingly candid message for attendees: You will likely be breached at some point so focus on the controls and response capabilities your organization needs to survive a cyber attack. The conference’s focus on cyber resilience doesn’t mean that organizations should abandon core security defenses like EDR, […]
-
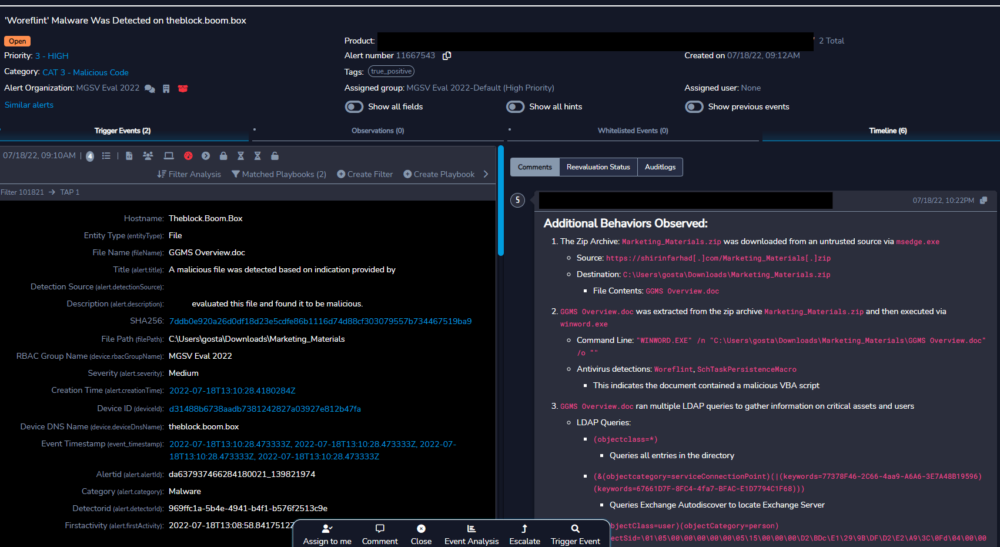
MSSPs Fare Well in First MITRE Evaluations
If MITRE Engenuity’s new MSSP evaluations are any indication, managed security service providers are a little like children from Lake Wobegon: They’re all above average. Of the 15 MSSPs that participated in MITRE’s first-ever security services testing, only three failed to report attack techniques in all 10 of the evaluation steps, and in two of […]
-

Healthcare Cyberattacks Lead to Increased Mortality, Lower Patient Care: Ponemon Study
Nearly a quarter of healthcare organizations hit by ransomware attacks experienced an increase in patient mortality, according to a study from Ponemon Institute and Proofpoint released today. The report, “Cyber Insecurity in Healthcare: The Cost and Impact on Patient Safety and Care,” surveyed 641 healthcare IT and security practitioners and found that the most common […]
-

eSecurity Planet’s 2022 Cybersecurity Product Awards
The editors of eSecurity Planet have been giving advice to enterprise security buyers for more than a decade, and for the last five years we’ve been rating the top enterprise cybersecurity products, compiling roughly 50 lists to date on every product imaginable, from networks to endpoints and out to the cloud and beyond. This year, […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis





