-
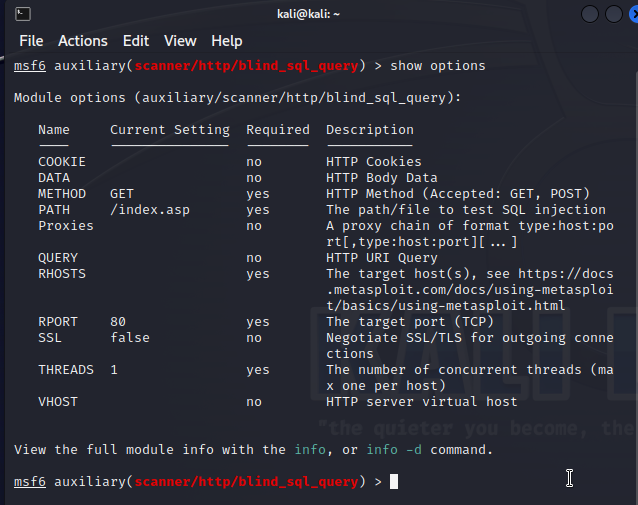
Kali Linux Penetration Testing Tutorial: Step-By-Step Process
Kali Linux turns 10 this year, and to celebrate, the Linux penetration testing distribution has added defensive security tools to its arsenal of open-source security tools. It remains to be…
-
How UPX Compression Is Used to Evade Detection Tools
Compression is a great way for hackers to hide malware and render it undetectable. Here’s what to do about that.
-
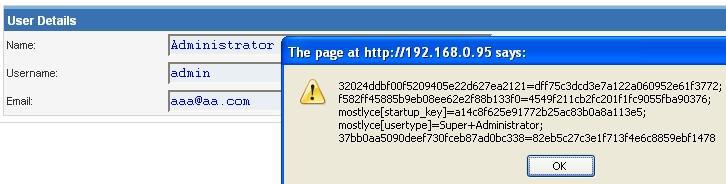
How to Use Input Sanitization to Prevent Web Attacks
Despite all of our investments in security tools, the codebase can be the weakest link for any organization’s cybersecurity. Sanitizing and validating inputs is usually the first layer of defense.…
-
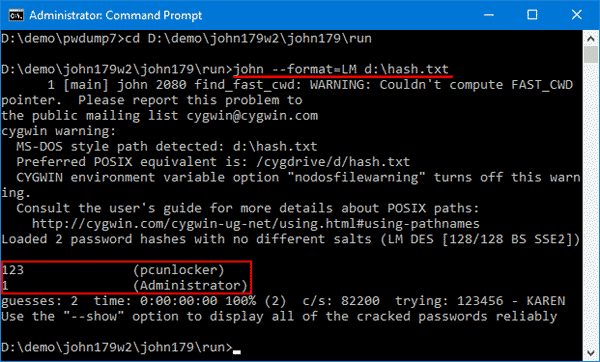
John the Ripper: Password Cracking Tutorial and Review
John the Ripper is a popular password cracking tool that can be used to perform brute-force attacks using different encryption technologies and helpful wordlists. It’s often what pen-testers and ethical…
-
Open Source Security Index Lists Top Projects
Two venture investors have launched an index to track the most popular open source security projects. Chenxi Wang of Rain Capital and Andrew Smyth of Atlantic Bridge unveiled the Open…
-
Cybercriminals Use VSCode Extensions as New Attack Vector
Microsoft’s Visual Studio Code integrated development environment (IDE) is used by as much as 75% of developers, so any security issue has widespread implications. And Aqua Nautilus researchers have discovered…
-
GitHub Adds New Security Features for Open Source Community
GitHub has announced new features that could improve both developers’ experience and supply chain security. The “private vulnerability” reports announced at GitHub Universe 2022 will allow open-source maintainers to receive…
-
REMnux: The Linux Toolkit for Reverse Engineering and Malware Analysis
REMnux is a free community distribution that ethical hackers, security researchers, and many other security pros can leverage to build their own labs and speed up malware analysis. Whether you’re…
-
Threat Group Continuously Updates Malware to Evade Antivirus Software
Kaspersky researchers recently found evidence of an advanced threat group continuously updating its malware to evade security products, similar to a release cycle for developers. Kaspersky revealed that APT10, also…
-
Cybercriminals Use Fake Public PoCs to Spread Malware and Steal Data
GitHub proofs of concept (PoCs) for known vulnerabilities could themselves contain malware as often as 10% of the time, security researchers have found. Researchers at the Leiden Institute of Advanced…
Get the free newsletter
Subscribe to Cybersecurity Insider for top news, trends & analysis