Data loss prevention (DLP) best practices are principles that help prevent intentional or unintentional data erasure. By following these guidelines, organizations can reduce the detrimental impact of data loss and quickly resume operations after an incident. This also protects sensitive data and minimizes legal and reputational issues. Explore some real-world instances below and discover when and how to use DLP procedures for optimal data security.
When Should You Incorporate a DLP Strategy?
If you or your business handles sensitive data, operates in regulated industries, or suffers from repeated cybersecurity threats, it’s time to evaluate the need for DLP strategies. Proofpoint’s 2024 data loss landscape report reveals 84.7% of enterprises have experienced data loss, with an average of 15 incidents per company per year, underscoring the importance of properly implementing DLP methods. Consider these factors:
- Sensitive data handling: Determine whether your company handles customers’ personally identifiable information (PII), proprietary software code, product designs, or any other unique creations crucial for your company’s competitive edge.
- Industry-specific rules: Check relevant regulations on a regular basis to verify data security compliance, and use DLP to protect sensitive data and reduce regulatory risks.
- Data storage: Identify whether your organization’s data storage is on-premises or cloud-based. Analyze the storage’s security protocols and scalability.
- Potential threats: Conduct risk assessments, vulnerability scans, and penetration testing to evaluate potential threats and weaknesses.
- Company resources: Examine your budget allocations and IT infrastructure capabilities. Determine whether there are enough financial and technology resources to adopt and sustain effective DLP initiatives.
12 Data Loss Prevention Best Practices
A data loss prevention policy lays the groundwork, but the effectiveness of data security hinges on adopting globally accepted best practices. These are values to be enforced and maintained, not just tasks to be completed. From tailoring your DLP policy to promoting a collaborative culture inside the organization, explore these established practices for a stronger data security approach.
Tailor Your DLP Policy
This approach begins with a thorough examination of the types of data that your business handles. Categorize this data according to its sensitivity level, taking into mind factors such as confidentiality and regulatory compliance. Perform a review of industry-specific rules to verify compliance with your policy framework. Then, evaluate current network security measures to discover any gaps or redundancy that should be corrected.
By modifying your DLP policy in this way, you can develop an effective plan that meets your organization’s specific requirements and improves overall data security efforts. Aligning the policy with industry regulations reduces compliance risks while avoiding potential penalties or legal difficulties. Furthermore, personalizing the policy enables you to address threats and vulnerabilities specific to your business.

Choose the Right DLP Solution
To choose the best DLP solution, conduct extensive research on providers to determine their capabilities and compatibility with your organization’s requirements. Ensure that the tools you purchase are in line with data management standards, regulatory needs, and your financial limits. To make an informed decision, evaluate features, scalability, and integration capabilities.
Consider these top three DLP products:
- Forcepoint DLP: Best overall option for visibility and global compliance (30-day free trial)
- Clumio Protect and Discover: Best for AWS business environments (14-day free trial)
- Proofpoint Enterprise DLP: Best for standalone email protection (contact for free trial)
Choosing the right DLP solution ensures effective data protection, compliance with rules, and a reduced risk of data breaches. It maximizes resource usage by investing in products that target specific security needs, hence improving your organization’s overall cybersecurity posture.
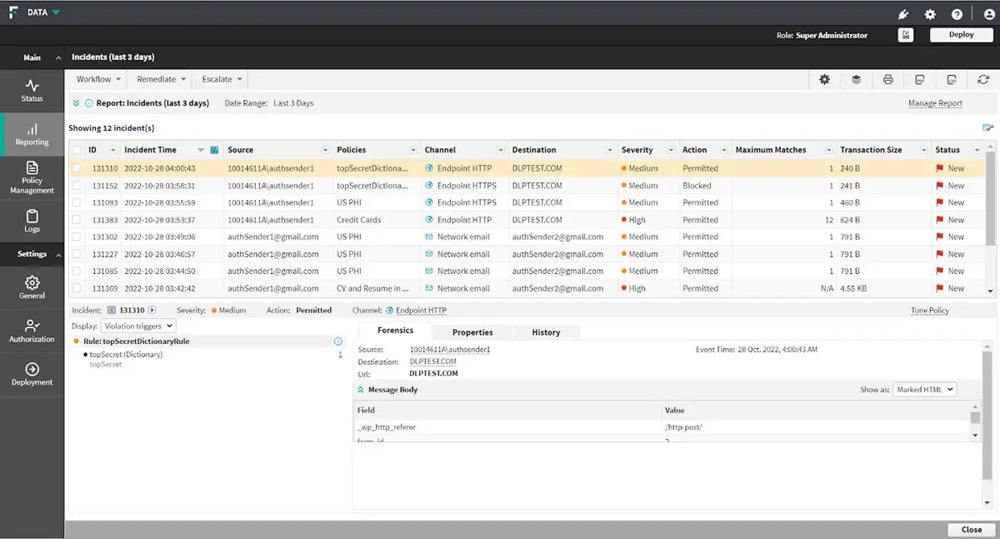
If you’re looking for more options, check out our comprehensive guide on the top DLP solutions.
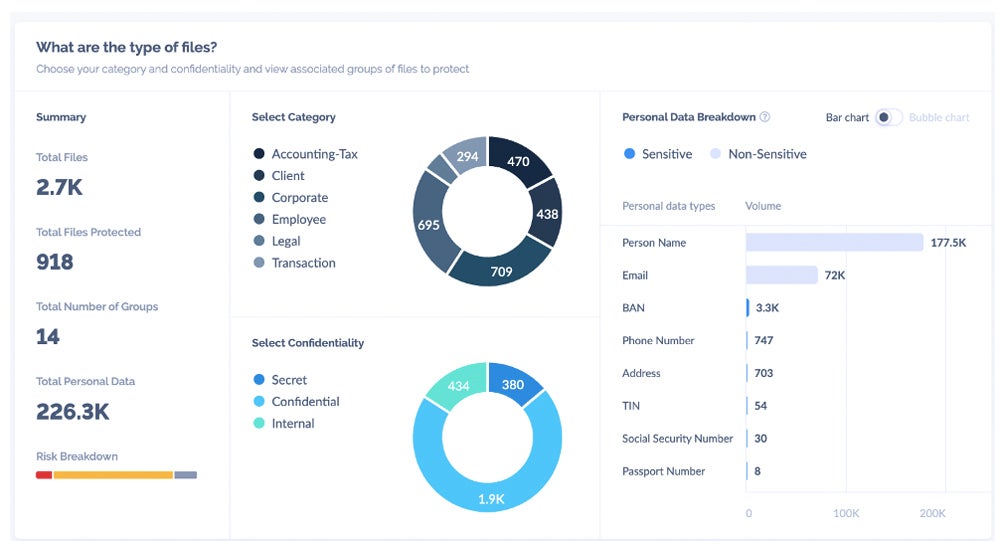
Prioritize & Classify Data
To successfully prioritize and classify data, understand the regulatory requirements and potential consequences on sensitive information. Determine essential data types, such as intellectual property and personal information, to steer defense resources where they’re most required. Classify data by context to make it easier to manage and track. Conduct content analysis to improve safety measures.
This approach enables focused defense strategies, ensuring that resources are allocated efficiently to safeguard the most important information. It simplifies data management operations and enhances tracking capabilities, thus enhancing overall data security posture. Periodic review allows businesses to respond to changing data landscapes and emerging threats while retaining strong security measures over time.
Train Employees on Their Roles in Data Security
To initiate employee data security training, first examine the organization’s particular risk landscape and regulatory requirements. Customize training materials to address these specific concerns, including data handling protocols, password management, and phishing attempt identification. Use cybersecurity training tools, seminars, online courses, and simulations to successfully engage staff and reinforce fundamental network security principles.
Organizations that invest in employee data security training can considerably mitigate the risk of data breaches and minimize the potential consequences of security incidents. Well-informed employees can better identify and respond to security threats. Furthermore, adopting DLP systems alongside training activities improves the organization’s ability to enforce security regulations and detect suspicious conduct, consequently strengthening cybersecurity defenses.

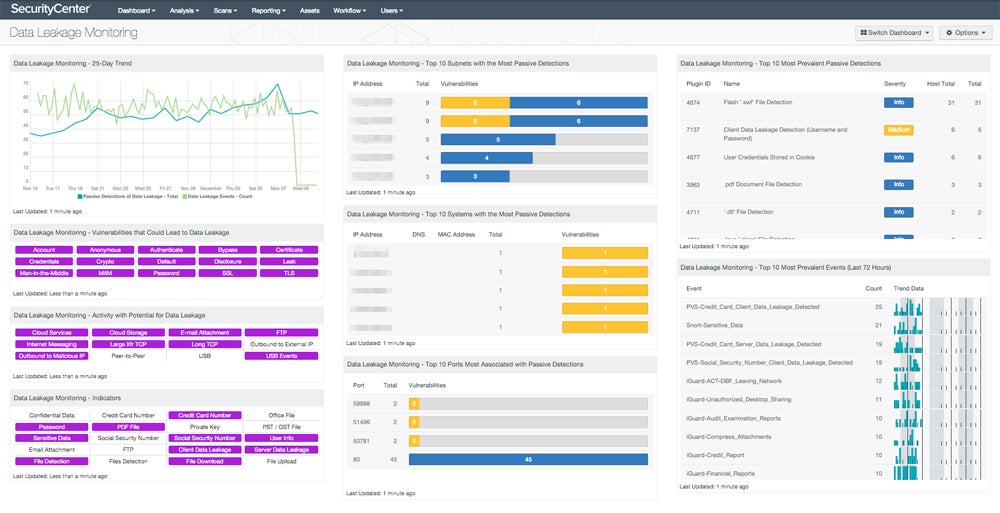
Use Monitoring Tools for Data Visibility
For continued data visibility, begin by deploying monitoring technologies that track data travel across the organization’s network. Determine where data originates, how it’s stored, and where it’s transported. Real-time data loss prevention systems continuously monitor data flows, allowing firms to catch and react to any suspicious activity or potential data breaches.
In addition, continually refining and modifying these monitoring systems reduces false alarms and assures precise detection of security incidents. By keeping all stored data visible, organizations may proactively detect and resolve possible security concerns before they become full-fledged data breaches.
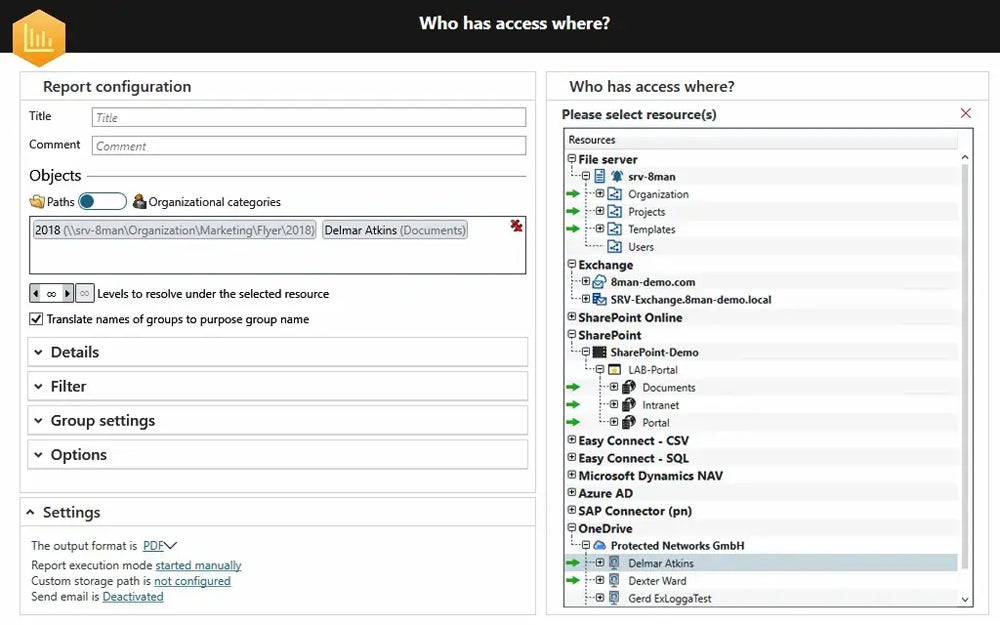
Limit Data Access
To reduce the danger of unauthorized access and breaches, this technique adheres to the principle of least privilege, providing individuals access to only the information they need. Use access restrictions and conduct regular assessments to ensure that permissions are appropriate for the user’s job. Regular audits, strong access controls, and early permission revocations help to limit the risks associated with changes in user intent.
Encrypt Data
This practice entails using data encryption tools to keep sensitive data confidential and safe from illegal access or exploitation, even if the device is lost or stolen. Encrypt data at rest with encryption algorithms and secure storage techniques. To encrypt data in transit, employ secure encryption and communication protocols such as Transmission Control Protocol (TCP) and Transport Layer Security (TLS).
Here are some options for data encryption tools:
- 7-Zip: Best for worldwide use (free to download)
- AxCrypt: Best for Simplified Business File Sharing (30-day free trial)
- NordLocker: Best for Cloud-Based Business File Sharing (14-day free trial)
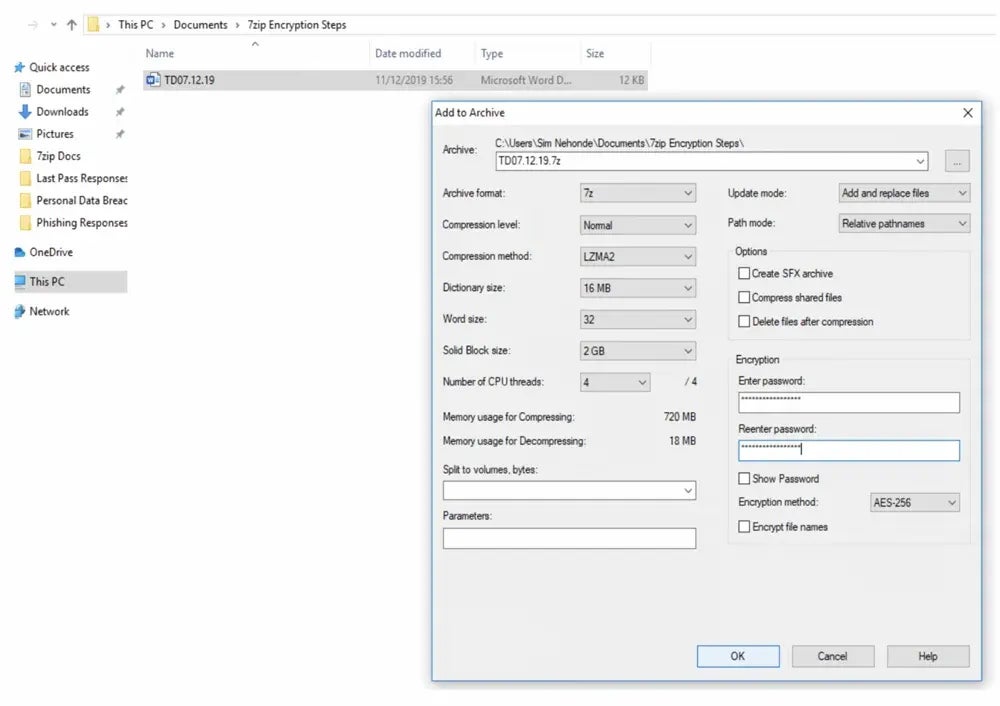
Explore other alternative solutions by reading our review on the best encryption software and tools.
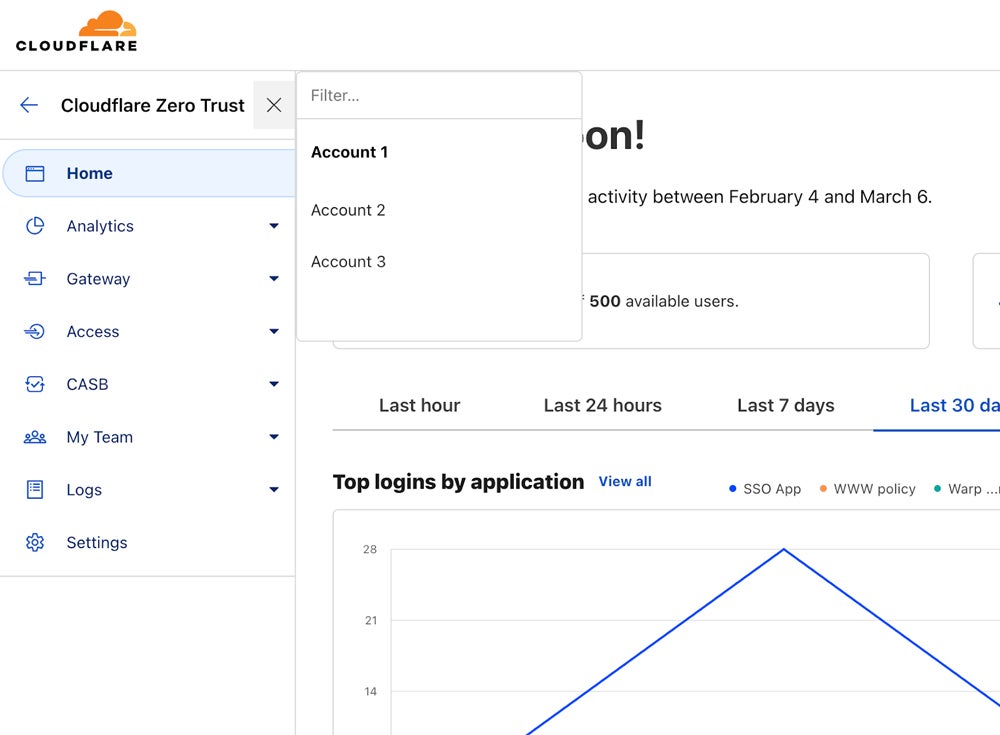
Employ Authentication Methods for All Users & Devices
A zero trust approach rejects any sort of inherent trust and requires continual verification of all users and devices. Implement stringent access rules, multi-factor authentication, and continuous monitoring to authenticate all access attempts, regardless of prior trust status. This strategy examines all network traffic and access attempts to reduce the likelihood of unauthorized access or exploitation.
Implement the 3-2-1 Backup Rule
When applying the 3-2-1 backup rule, make sure you have three copies of your data: one primary and two backups. Keep these copies on two separate types of media: hard disks, cloud storage, and tape backups. Then, keep one duplicate offshore to protect against localized disasters such as fires, floods, and theft.
Multiple copies of data on different media allow redundancy, lowering the chance of total data loss due to hardware failures or cyberattacks. Storing one copy offsite protects against disasters, ensuring that data is still accessible even if the primary location is compromised.

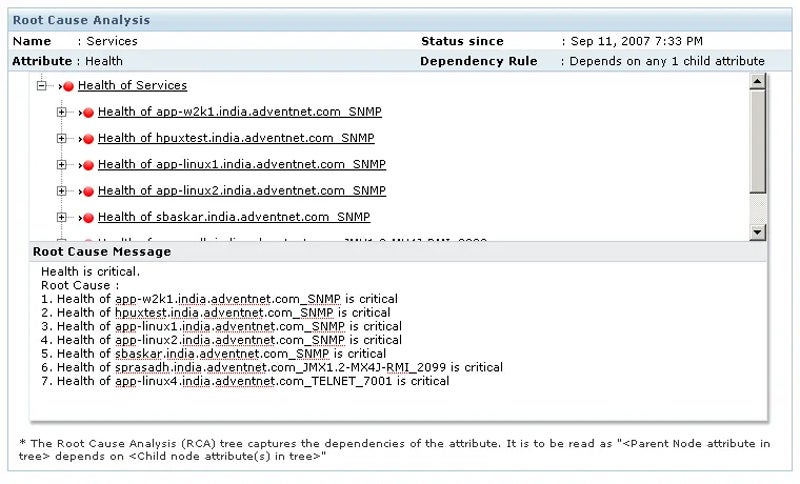
Use the 5-Whys Root Cause Analysis (RCA) Method
To do this method, identify the problem and ask “why” to reveal its underlying causes. Repeat the procedure iteratively, at least five times, delving deeper with each “why” until the underlying cause is discovered. Then, create fixes that successfully address the root cause. Use automation tools to help you perform root cause analysis faster.
This strategy provides businesses with greater insights into their difficulties, resulting in more effective problem solving. It encourages a thorough evaluation of problems, allowing teams to address not just the symptoms but also the root causes. This strategy also promotes a culture of continual development, which prevents similar problems from occurring in the future.
Review & Refine the DLP Strategy
To examine and modify your current DLP approach, start by securing essential data sets and identifying gaps. Expand data identification efforts and ensure that DLP solutions are regularly updated to counter emerging risks. Conduct security audits to assess controls and detect flaws, and then prioritize corrective activities. Use the lessons learned to determine the future enhancements required to protect against data loss threats.
Enhance Collaboration Among Internal Users
Involve all stakeholders in the organization’s data security activities. Everyone, from senior management to front-line staff, is responsible for maintaining a thorough data security policy. Encourage regular talks, training, and awareness workshops to help integrate DLP practices into the organization’s culture. An effective DLP implementation requires participation and cooperation from all users to successfully meet the company goals and requirements.
3 Real Examples of DLP Best Practices in Action
DLP is more than just theory; lapses in DLP can result in disastrous consequences. Data loss threats have persisted over time, as evidenced by incidents such as the Cloudflare breach in 2023, GitLab’s database failure in 2017, and the Toy Story incident in 1998. Analyzing past data loss occurrences allows you to assess the severity of potential risks and the effectiveness of their existing DLP measures. Explore these real-life examples for additional insights.
Cloudflare’s Thanksgiving Cyberattack
Incident: On Thanksgiving 2023, an intruder exploited stolen credentials to get access to Cloudflare’s Atlassian server, trying to infiltrate their global infrastructure. Despite getting access to internal documents, Cloudflare’s Zero Trust architecture prevented more network traversals and data compromise. No user data was lost. Cloudflare responded by rotating more than 5,000 production credentials, triaging 4,893 computers, and replacing hardware in a new data center.
DLP best practice: Zero trust architecture — Cloudflare’s Zero Trust technology halted the attacker’s attempts to exploit compromised credentials by prohibiting lateral movement and restricting access, preventing data breaches and minimizing damage.
GitLab’s 300 GB Data Loss
Incident: In 2017, GitLab experienced an 18-hour outage caused by a database sync failure. Engineers attempted manual re-sync, mistaking it for a spam attack and accidentally losing 300GB of existing user data, which affected projects, comments, and new accounts.
DLP best practice: GitLab’s emphasis on regular database security practices like backups and disaster recovery processes helps to reduce the impact of data loss. Despite initial difficulties, a recent database snapshot saved during an engineer’s testing enabled the prompt restoration of lost data.
Toy Story 2’s Accidental File Deletion
Incident: During a file cleanup, Toy Story 2’s database repository was put at risk when an animator accidentally deleted Toy Story 2’s root folder, erasing all the movie’s data. Luckily, a technical director salvaged the film as she had backup copies of the repository on her own computer. While newer, unbacked files were lost, major portions were recovered, saving the project from cancellation or the need to start over.
DLP best practice: Regular backup and immutable storage solutions — while backup copies spared the Toy Story 2 project from disaster, newer files were lost due to a lack of backups. Implementing the 3-2-1 backup technique, which included redundant copies on different mediums, could have avoided data loss. Additionally, using an immutable storage solution would’ve kept all the files intact.
How to Implement a Data Loss Prevention Strategy in 5 Steps
To prevent illegal data access or leakage, effective DLP strategies must include a clearly defined scope, data security awareness and governance efforts, use cases mapping, dependencies identification and improvement, and a gradual DLP implementation. This allows enterprises to protect their assets, comply with laws, and reduce risks to their reputation and operations.
1. Define the Program’s Scope
To determine the program’s scope, prioritize risks, and identify data that needs security, such as intellectual property. Data flow mapping allows you to trace data origins, destinations, and applications. To effectively support the program, adopt security policies that are consistent with DLP objectives. This ensures tailored protection, minimal disruptions, and effective alignment of security measures with business objectives.
2. Initiate Awareness & Governance Efforts
Communicate data practices, benefits, and consequences to all stakeholders. Refine data handling processes by establishing acceptable norms and procedures. Then, work with the legal and procurement teams to include DLP requirements in contracts. Maintain open communication lines via a collaborative platform for continual customer input and queries, supporting continuous iteration as business demands change.
3. Map Your DLP Use Cases
First, determine the precise detection and context needs for each location. Then, decide what types of DLP tools are required to offer the necessary control. Because one provider may not cover all DLP components, select vendors who can secure data across several identified use cases, or integrate it with other tools. Before selecting a solution, thoroughly test it to verify that it meets the needs of the business and is effective.
4. Address & Improve Identified Dependencies
Dependencies, whether technical or procedural, can reduce DLP efficacy. For example, DLP suffers when users have uncontrolled data access. Implement identity management practices to limit access to data based on valid business requirements. Additionally, employ data categorization to detect sensitive data and inform data permissions, thereby improving overall DLP efficacy and data security.
5. Implement in Small Stages, Manage & Refine Over Time
To minimize disturbance during large-scale rollouts, start DLP implementation gradually, with a “monitoring only” phase to adjust policies. Communicate progress to users, focusing on data handling changes. Transition to operational mode and collect metrics such as resolved incidents and blocked data instances to ensure continual development. Allocate resources to modify DLP policies to meet evolving business demands and data types.
Bottom Line: Secure Your Operations with Data Loss Prevention Best Practices
DLP best practices involve continuous and proactive management of data security. Organizations can accomplish comprehensive data protection by integrating these principles into their everyday operations. Continuously monitor, evaluate, and adjust these strategies as your organizational demands change. To keep data secure, have a strong cybersecurity posture that involves a combination of DLP and other types of security solutions.
Integrate DLP with secure storage and backup solutions for comprehensive data protection.




