-
ThycoticCentrify Ransomware Report: 83 Percent of Victims Paying Ransom
The bulk of companies hit by ransomware are deciding that paying the ransom is the best and fastest way to get their businesses back online, despite growing pressure from the federal government and some in industry to not give into the cybercriminals’ demands. A report this week by researchers at ThycoticCentrify – the result of […]
-
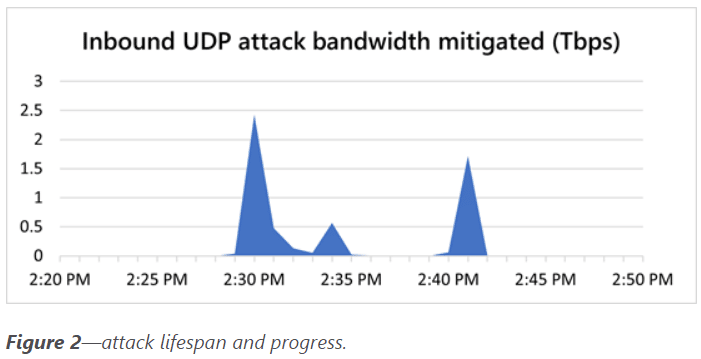
Microsoft Azure Attack Illustrates Ongoing DDoS Threats
Officials with Microsoft’s Azure public cloud said the company in late August was able to stave off a record distributed denial-of-service (DDoS) attack against a European customer that originated in the Asia-Pacific region. The attack, which hit 2.4 terabits per second, was 140 percent higher than a 1 Tbps attack last year and higher than […]
-
Google Sending Security Keys to 10,000 Users at High Risk of Attack
Google is giving out 10,000 free security keys to high-risks users, an announcement that came a day after the company warned 14,000 of its high-profile users that they could be targeted by the notorious Russia-based APT28 hacking group. The moves were part of a larger push by Google in recent months to make cybersecurity a […]
-

White House, Congress Target Ransomware Payments
The surge in ransomware attacks in the last year have spurred attempts by government officials to bolster cybersecurity defenses, and those actions advanced on multiple fronts this week. In an op-ed piece published by CNBC, U.S. Deputy Attorney General Lisa Monaco wrote that the threat of ransomware to the country’s national security and public safety […]
-
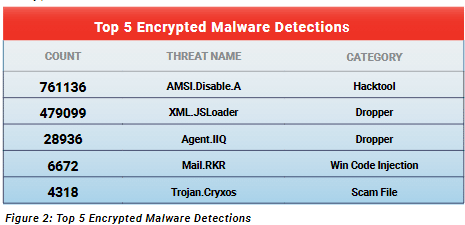
More Than 90 Percent of Malware in Q2 Came Via Encrypted Traffic: WatchGuard
A surprising 91.5 percent of all malware detected on networks of WatchGuard Technologies customers in the second quarter came over encrypted connections, raising the security risk for the 80 percent of such organizations that lack processes for decrypting and scanning HTTPS traffic for threats. WatchGuard, which sells network security, intelligence and endpoint protection solutions, included […]
-
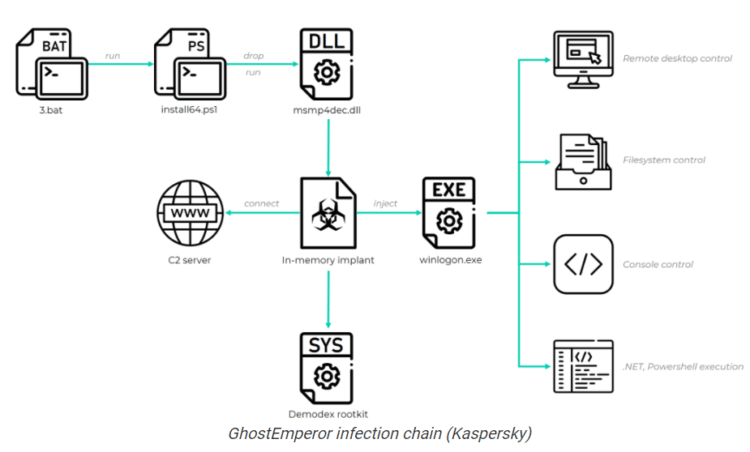
Chinese Attackers Use New Rootkit in Long-Running Campaign Against Windows 10 Systems
A previously unknown but highly skilled Chinese-speaking cyberespionage group is using sophisticated malware to attack government and private entities in Southeast Asia through a long-running campaign that targets systems running the latest versions of Microsoft’s Windows 10. The group – which researchers with Kaspersky Lab are calling GhostEmporer – uses a multi-stage malware framework designed […]
-
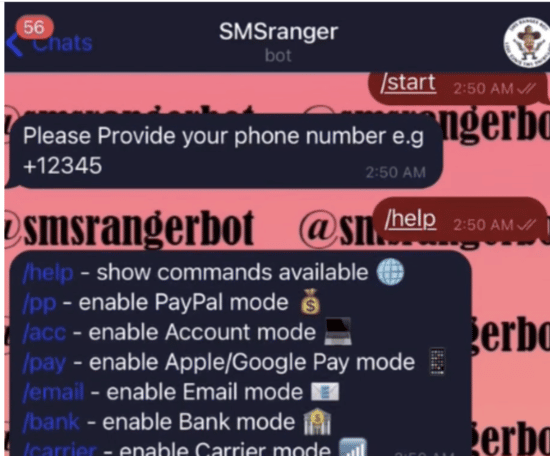
Attackers Use Bots to Circumvent Some Two-Factor Authentication Systems
Underground services are cropping up that are designed to enable bad actors to intercept one-time passwords (OTPs), which are widely used in two-factor authentication programs whose purpose is to better protect customers’ online accounts. By using the services, cybercriminals can gain access to victims’ accounts to steal money. Security expert Chris Krebs wrote in a […]
-
Attackers Exploit OMIGOD Flaw in Azure Despite Microsoft Fixes
Cybercriminals are targeting Linux-based servers running Microsoft’s Azure public cloud environment that are vulnerable to flaws after Microsoft didn’t automatically apply a patch on affected clients in its infrastructure. According to cybersecurity firm Recorded Future, the attacks began the night of Sept. 16 after a proof-of-concept exploit was published earlier in the day on GitHub. […]
-

McAfee Finds Years-Long Attack by Chinese-Linked APT Groups
An investigation by McAfee researchers into a case of a suspected malware infection uncovered a cyber attack that had been sitting in the victim organization’s network for years stealing data. The investigators said the advanced threat actors used a mixture of known and unique malware tools in the attack – which they dubbed Operation Harvest […]
-
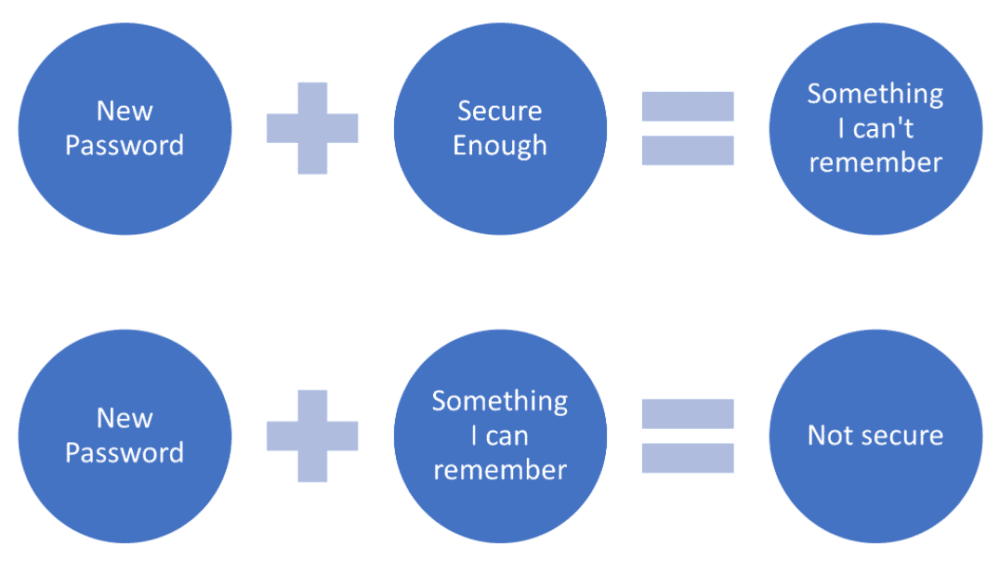
Microsoft Expands Passwordless Sign-on to All Accounts
Microsoft for the past few years has been among the loudest vendors calling for a security future that doesn’t include passwords. In 2018, the software giant took the step of doing away with passwords for people signing into its Edge web browser, saying instead they could use a number of alternatives. Since then, the company […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis





