-
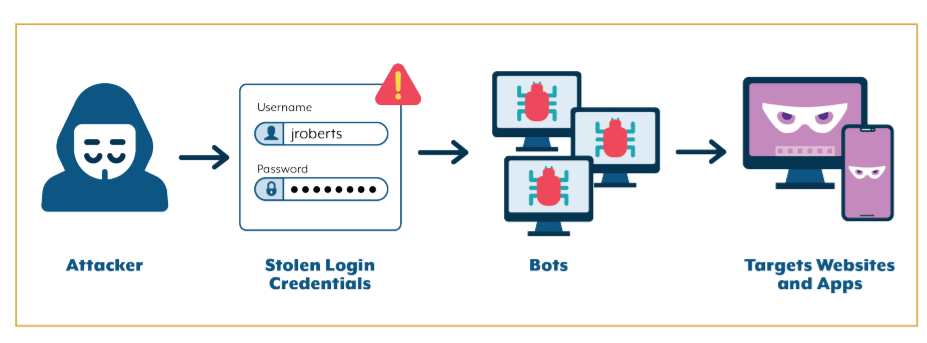
NY AG Investigation Highlights Dangers of Credential Stuffing
A report last week by the New York Attorney General’s Office put a spotlight on the ongoing threat of credential stuffing, a common technique used by cybercriminals that continues to spread and is helping to fuel the push for security practices that don’t involve usernames and passwords. AG Letitia James’ office ran a months-long investigation […]
-

SolarWinds-Like Supply Chain Attacks will Peak in 2022, Apiiro Security Chief Predicts
Cyberthreats against software supply chains moved to the forefront of cybersecurity concerns a year ago when revelations of the attack on software maker SolarWinds emerged. Now one security researcher – Moshe Zioni, vice president of security research for application risk management startup Apiiro – is predicting that supply chain attacks will likely peak in 2022 […]
-

The Link Between Ransomware and Cryptocurrency
There are few guarantees in the IT industry, but one certainty is that as the world steps into 2022, ransomware will continue to be a primary cyberthreat. The dangers from ransomware have risen sharply since WannaCry and NotPetya hit the scene in 2017, and this year has been no different. A pair of recent reports […]
-
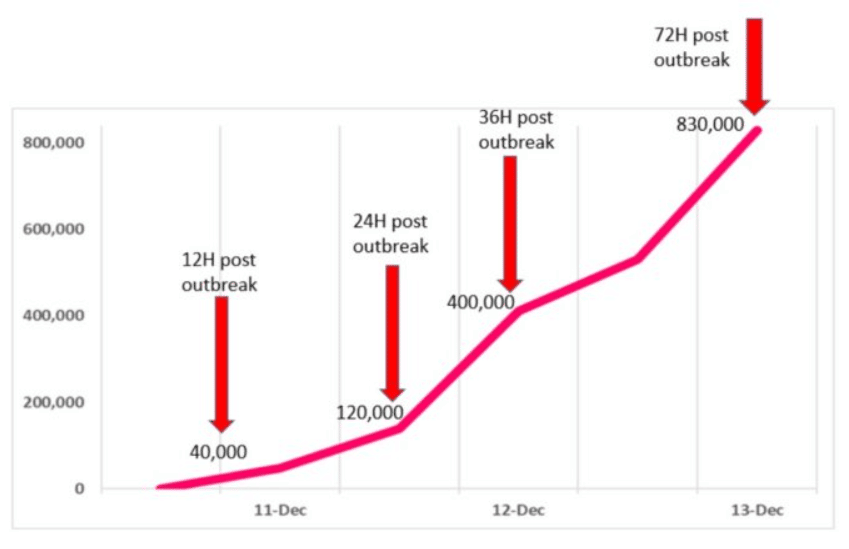
Nation-State Attackers, Ransomware Groups Take Aim at Apache Log4j Flaw
Nation-state cyber threat groups and ransomware attackers are moving in to exploit a critical flaw found in the seemingly ubiquitous Apache Log4j open-source logging tool, as attacks spread just days after the vulnerability that could affect hundreds of millions of devices was made public late last week. Microsoft researchers reported that the remote code execution […]
-
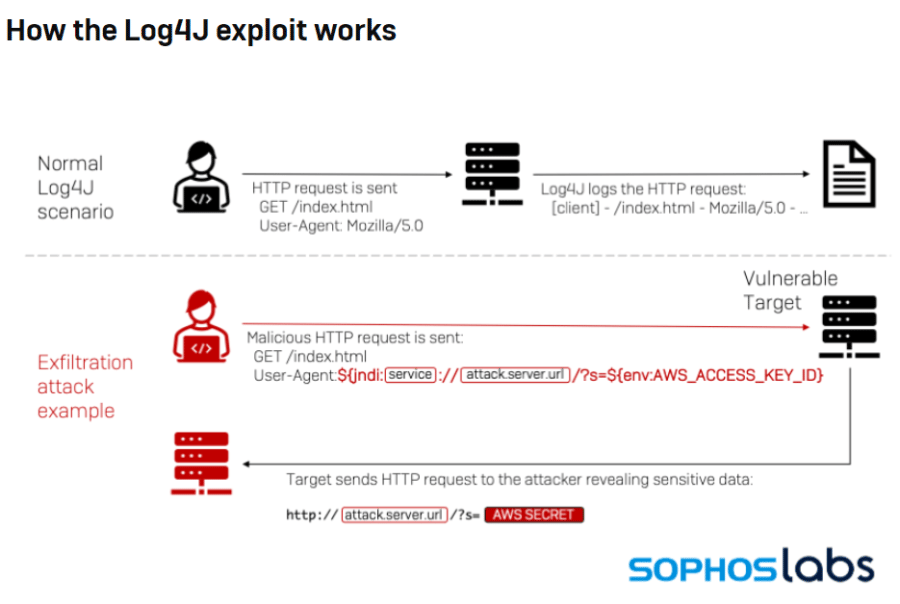
Log4Shell Exploitation Grows as Security Firms Scramble to Contain Log4j Threat
Cybercriminals are quickly ramping up efforts to exploit the critical flaw found in the widely used Log4j open-source logging tool, targeting everything from cryptomining to data theft to botnets that target Linux systems. The cybersecurity community is responding with tools for detecting exploitation of the vulnerability, a remote code execution (RCE) flaw dubbed Log4Shell and […]
-

Cybersecurity ‘Vaccines’ Emerge as Ransomware, Vulnerability Defense
Cybersecurity vaccines are emerging as a new tool to defend against threats like ransomware and zero-day vulnerabilities. Cybersecurity firms have released “vaccines” in recent days to protect against the widely used STOP ransomware strain and the new Apache Log4Shell vulnerability. Germany-based G Data CyberDefense released software designed to trick the STOP ransomware variant into believing […]
-
Apache Log4j Zero Day Exploit Puts Large Number of Servers at Severe Risk
A critical vulnerability in the open-source logging software Apache Log4j 2 is fueling a chaotic race in the cybersecurity world, with the Apache Software Foundation (ASF) issuing an emergency security update as bad actors searched for vulnerable servers. Log4j 2, developed by the ASF, is a widely used Java package that enables logging in an […]
-
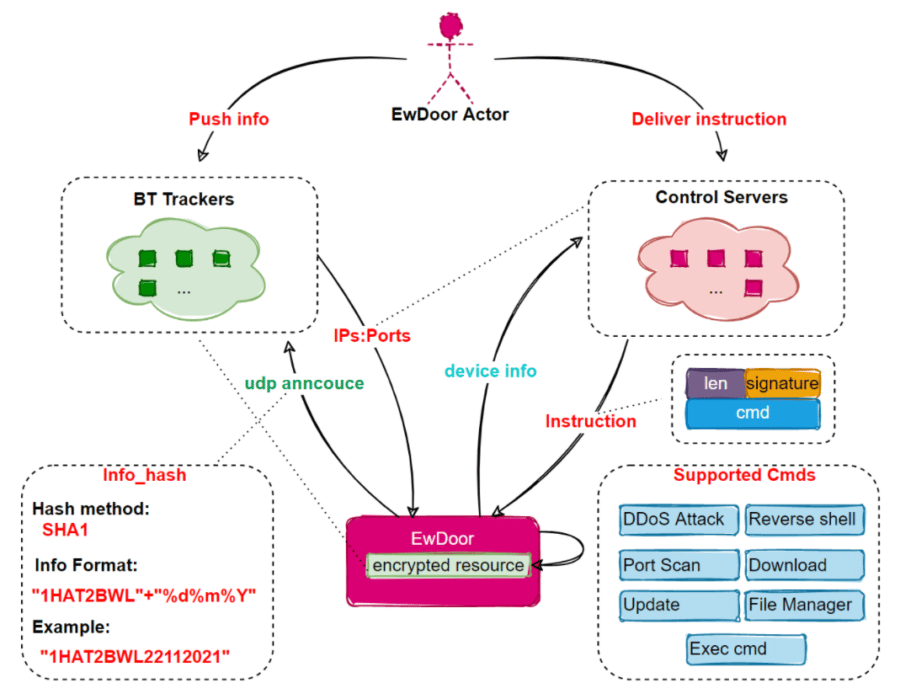
AT&T Looks to Shut Down Botnet that Attacked 5,700 Network Appliances
AT&T is working to stop a botnet that has infected at least 5,700 network edge servers inside its networks and appears designed to steal sensitive information and launch distributed denial-of-service (DDoS) attacks. Researchers at Netlab, the network security unit of Chinese tech giant Qihoo 360, wrote in a report this week that the rapidly updated […]
-
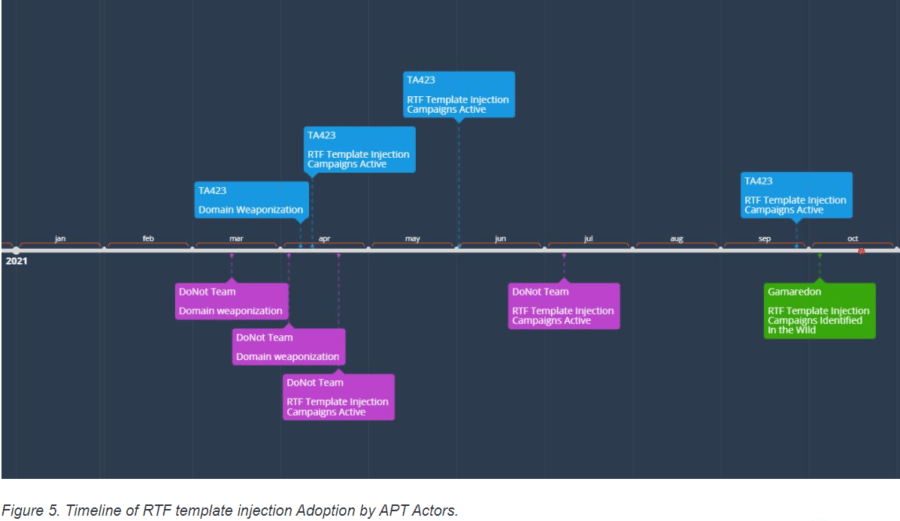
Nation-State Attackers Use RTF Injection to Easily Spread Malware
Hacking groups linked to Russia, China and India are leveraging a novel attack technique that makes it easier for them to spread malware, steal data and evade detection, according to a report this week by security firm Proofpoint. The advanced persistent threat (APT) groups are using a technique called rich text format (RTF) template injections, […]
-

China’s Data Privacy Law Poses Challenge for International Companies
Businesses that have spent the past three-plus years adapting to the European Union’s far-reaching data privacy law now have to decide how they will respond to a similar law in China that has been criticized as being more vague in its wording and harsher in its penalties. China’s Personal Information and Privacy Law (PIPL), enacted […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis





