The bulk of companies hit by ransomware are deciding that paying the ransom is the best and fastest way to get their businesses back online, despite growing pressure from the federal government and some in industry to not give into the cybercriminals’ demands.
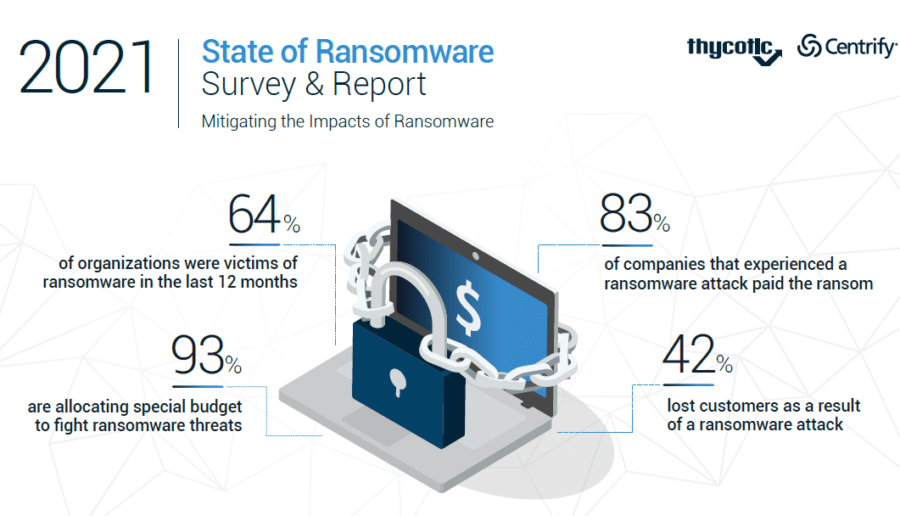
A report this week by researchers at ThycoticCentrify – the result of the merger earlier this year between privileged access management (PAM) vendors Thycotic and Centrify – found that 64 percent of the 300 U.S.-based IT decision makers surveyed were attacked with ransomware in the previous 12 months, and that 83 percent paid the ransom to restore their data.
The study is the latest in a string of similar reports that found ransomware to be the top cybersecurity threat to businesses, and that the rapid evolution of the underground industry will likely make it an even more significant danger in the coming years.
The authors of the report noted that the United States has seen an almost 200 percent increase in attacks in the past two years and that the cost to recover the data from the bad actors averages more than $100,000, 10 times what it was a year ago. They also wrote that cybercriminals are increasingly sophisticated and that the ransom demands are growing.
Ransomware-as-a-Service Grows in Importance
It’s also becoming easier for cybercriminals to launch ransomware attacks, regardless of their skill level. The amount of money to be made in the attacks is rising and the cost of the tools to do so is dropping. Ransomware developers are selling their expertise and tools by offering them in ransomware-as-a-service (RaaS) scenarios and the industry could evolve further, becoming a subscription model where organizations pay ransomware actors not to target them.
“As the odds for experiencing a ransomware attack grow, it’s not a matter of if an attack will happen, but when it will happen,” they wrote. “This means that while you are trying to prevent becoming a victim of ransomware, you must also be prepared to respond to attacks with a proven incident response plan that you test regularly.”
Read more: Best Ransomware Removal and Recovery Services
Government Responds to the Threat
In the wake of attacks earlier this year on such companies as energy supplier Colonial Pipeline, global meat processor JBS and managed services provider Kaseya – all of which caused ripples throughout the economy – the Biden Administration has been moving on multiple fronts to address the threat of ransomware, including working with tech companies, issuing guidelines and investigating attackers and tracking them through their payment methods.
In addition, the government also is trying to deter companies from paying the ransoms, arguing that doing so encourages and finances more attacks. The government also wants organizations to be more forthcoming when they’ve been attacked and when they’ve paid a ransom.
There also is no guarantee that the data can be recovered even if a ransom is paid, according to Jigar Shah, vice president at multicloud security provider Valtix.
“Often, paying the ransom does not even let you recover, as the attacker just vanishes and does not help free locked resources,” Shah told eSecurity Planet. “At this point, the major costs are on how to recover and rebuild. Forward-thinking organizations are investing in building non-fragile infrastructure using infrastructure-as-code. If you plan ahead and start your public cloud journey the right way, then you can build your infrastructure and apps such that they can be re-deployed in minutes if such an incident happens. And you can bake security right into this process.”
Even in a week when 30 countries banded together to fight ransomware and the U.S. banned the sale of hacking tools to China and Russia and took steps to curb cryptocurrency ransomware payments, ransomware attacks have continued to occur, with one knocking Sinclair Broadcast Group TV channels offline.
Also read: Best Backup Solutions for Ransomware Protection
A Focus on Prevention
That focus on prevention and developing a ransomware incident response plan is being echoed by the ThycoticCentrify researchers as well as others in the cybersecurity field. Rita Gurevich, founder and CEO of cybersecurity firm Sphere, told eSecurity Planet that recent federal government and corporate efforts have shifted the narrative around ransomware from response to prevention, including by ensuring backups are in place, improving training for users and deploying an effective access governance model.
In addition, IT and security professionals need to ensure that their skills have adapted to the increasingly sophisticated modern ransomware attacks.
“We have seen some success in tracking the methods of payments to the attackers,” Gurevich said. “This is an interesting development as cryptocurrency has always had the reputation of complete anonymity. ‘Follow the money’ has always been an investigative technique of law enforcement, and as ransomware attacks increase, the demand for proficiency in blockchain and cryptocurrency should continue to increase as well.”
Dwell Time a Threat Factor
The ThycoticCentrify researchers noted that dwell time – the time from when the bad actors get into the network to when they launch an attack and the attack is detected – is becoming a major part of the threat equation. In earlier attacks, cybercriminals would target a single computer or a limited network and the malware downloaded when a user clicked on a malicious link would encrypt the computer or server. Backups could usually be used to restore the data.
“Today, attackers focus on compromising user credentials and passwords to gain an entry point from which they can exploit our vast connected networks,” they wrote. “Once inside the network, undetected, the cybercriminals seek to elevate credential privileges, traverse the network, locate sensitive data, and plan how to exfiltrate and encrypt the data. This dwell time … enables attackers to understand the network, find and exfiltrate critical data. They will then leave crypto-locking malware on your systems to launch when they are ready. Typically, once an attacker gains access to domain administrator privileges, it is usually only a matter of hours before the ransomware is deployed and business comes to a halt.”

Also read: How Ransomware Uses Encryption – And Evolves
Paying the Ransom
Once ransomware has locked up a company’s data, they see paying the ransom as the best option for restoring the data and avoiding damage to their operations or reputations.
Cybercriminals who have used ransomware attacks to steal or access data and hold it hostage while demanding money and threatening to leak the data are increasingly targeting specific companies that, if their operations go down, will cause disruption not only to their services but also society in general. Bad actors understand that in such situations, many times entities will pay to get up and running again, according to Timur Kovalev, CTO at network security vendor Untangle.
“In addition, ransomware attacks are increasing because companies are paying the ransom,” Kovalev told eSecurity Planet. “Look at organizations such as JBS and Colonial Pipeline, who paid a $4.4 million ransom, although a good portion was returned [recovered by the FBI]. Cybercriminals see the large payouts and it encourages them to strike more often and at larger, more lucrative targets.”
Organizations Respond to Ransomware Threat
Companies are responding, according to ThycoticCentify. About 72 percent of those surveyed said cybersecurity budgets have increased due to ransomware threats and 93 percent are allocating special budgets specifically to fight those threats.
“Our research shows ransomware is a threat to organizations of all sizes and levels of sophistication,” ThycoticCentrify CEO Art Gilliland said in a statement. “The first line of defense should be solutions that secure privileged access, including multi-factor authentication (MFA) and other methods of enforcing Zero Trust, to keep would-be cyber criminals contained and limit the damage they can inflict.”
Jim Dolce, CEO of cybersecurity vendor Lookout, told eSecurity Planet that it’s increasingly important for organizations to understand the rapidly evolving nature of ransomware and the bad actors behind the attacks.
“Traditional security measures cannot keep up with the advanced modern tactics used in these attacks,” Dolce said. “Threat actors are always trying to think a step ahead and their tactics are constantly evolving. Security teams need to modernize their security posture by proactively implementing practices and tools across all corporate endpoints to mitigate the risk of these attacks before they can even get started.”
Further reading: Application Security is Key to Stopping Ransomware, Vendor Says




