-
Apple Patches Vulnerabilities in iOS Exploited by Spyware
Apple continues to be haunted by spyware developed by an Israeli security firm that hostile governments used to hack into Apple devices to spy on journalists, activists and world leaders (see Apple Security Under Scrutiny Amid Fallout from NSO Spyware Scandal). News of the nefarious uses of NSO Group’s Pegasus software first surfaced in July. […]
-
REvil Ransomware Group Resurfaces After Two Months Away
It was a short hiatus for the REvil ransomware group that signed off in July following several high-profile attacks by the Russia-based crew on such companies as global meat processor JBS and tech services provider Kaseya. The cybercrime gang shut down its dark web sites, including its public and payment sites and a negotiation portal […]
-
Vulnerability Could Expose HAProxy to HTTP Request Smuggling Attack
A critical vulnerability discovered in the open-source load balancer and proxy server HAProxy could enable bad actors to launch an HTTP Request Smuggling attack, which would let them bypass security controls and gain unauthorized access to sensitive data. Researchers with JFrog Security uncovered the vulnerability, CVE-2021-40346, during their regular searches for new and previously unknown […]
-
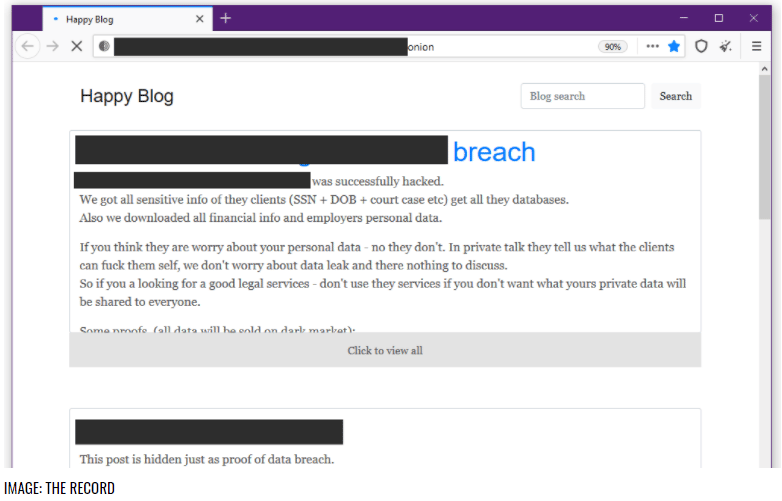
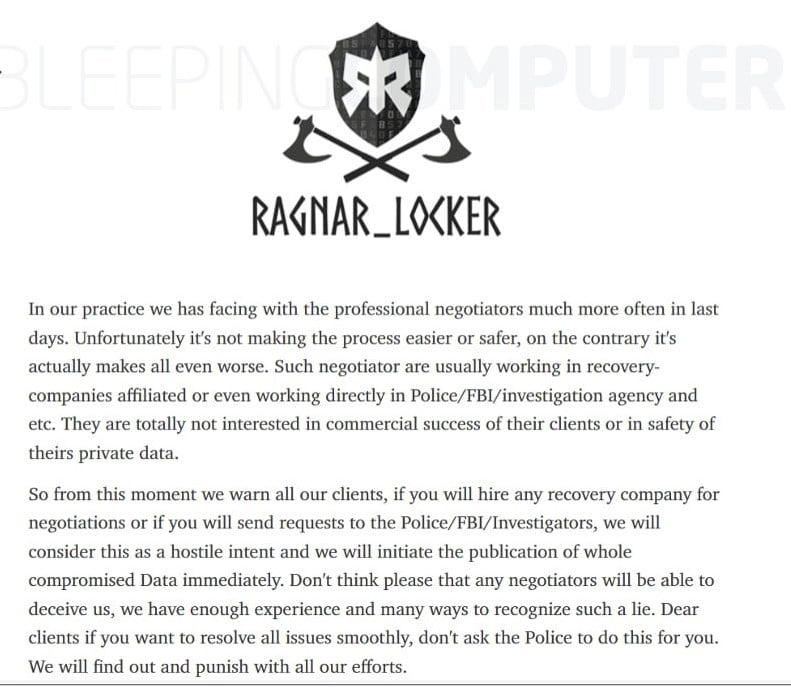
Ransomware Group Ragnar Locker Threatens Data Leaks if Law Enforcement Contacted
The cybercriminal gang behind the Ragnar Locker ransomware attacks is threatening victims that it will go public with data captured in an attack if they contact law enforcement agencies or hire negotiators. The Ragnar Locker group posted on its darknet leak site a note outlining the warning, putting even more pressure on target companies (which […]
-
Salesforce Email Service Used for Phishing Campaign
Cybercriminals are using Salesforce’s mass email service to dupe people into handing over credit card numbers, credentials and other personal information in a novel phishing campaign that highlights the threats to corporate networks that can come from whitelisted email addresses. According to a recent blog post from email security service provider Perception Point, the bad […]
-
LockFile Ransomware Uses Unique Methods to Avoid Detection
The LockFile ransomware family has made an impression in the relatively short amount of time it’s been around. The malware garnered a lot of attention over the past several months after being detected exploiting high-profile Microsoft vulnerabilities dubbed ProxyShell and PetitPortam. Now security researchers with Sophos have found that the LockFile operators are using novel […]
-
Microsoft, Google Among Tech Giants Pledging Big Money to Cybersecurity
Some of the biggest names in tech are promising to spend more than $30 billion to bolster cybersecurity capabilities, from securing the supply chain and expanding the adoption of the zero trust model to growing the talent pool, ramping up security awareness and revamping parts of the National Institute of Standards and Technology (NIST) framework. […]
-
Microsoft Issues ProxyShell Advisory After Attacks Begin
Microsoft this week issued an advisory about three vulnerabilities referred to collectively as ProxyShell days after security researchers at a federal government cybersecurity agency warned that cybercriminals were actively trying to exploit them. The ProxyShell vulnerabilities that affect Microsoft Exchange servers were put on full display at this month’s Black Hat 2021 conference when Devcore […]
-
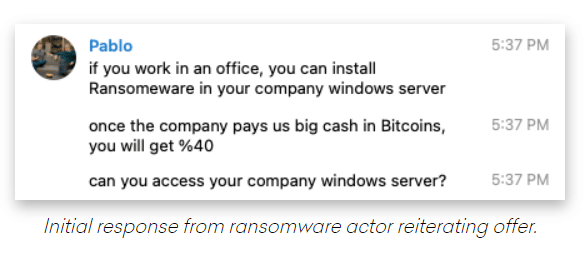
Ransomware Groups Look for Inside Help
Ransomware attackers, who use myriad methods to get their malware into the systems of businesses large and small in hopes of pulling down millions of dollars, are now going directly to the source. A researcher with email security solutions vendor Abnormal Security found a threat actor directly emailing employees of a company urging them to […]
-
Cloudflare: Mirai Botnet Launched Record-Breaking DDoS Attack
Cloudflare last month fought off a massive distributed denial-of-service (DDoS) attack by a botnet that was bombarding 17.2 million requests per second (rps) at one of the internet infrastructure company’s customers in the financial services space. The attack was almost three times larger than any previous attack that Cloudflare is aware of, according to Omar […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis