Speakers at last week’s MITRE ResilienCyCon conference had a surprisingly candid message for attendees: You will likely be breached at some point so focus on the controls and response capabilities your organization needs to survive a cyber attack.
The conference’s focus on cyber resilience doesn’t mean that organizations should abandon core security defenses like EDR, access control and firewalls, but they should be prepared for the advanced threats that will, at some point, get past them. That also means making sure that systems will be able to continue to function, even at a reduced capacity, during an attack.
The general lack of focus on resilience, response and recovery is largely reflected in vendor offerings too. JupiterOne CISO Sounil Yu, creator of a Cyber Defense Matrix adopted by OWASP, noted the concentration of security products in protection and detection and wondered, “Is our industry actually solving the right problems?”
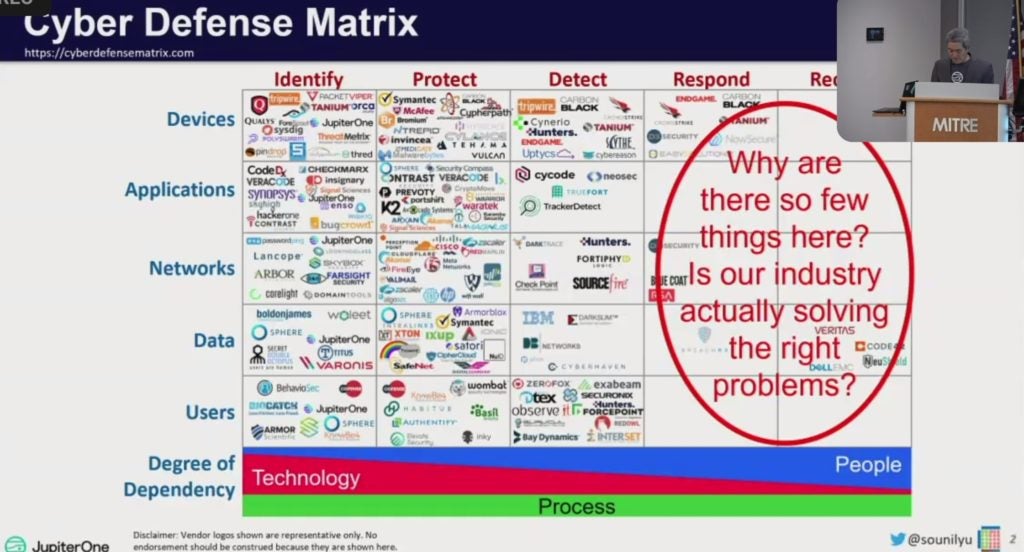
How to build in that cyber resiliency was the focus of a number of talks at the conference.
Patching Is Hard. Real Hard.
Unpatched vulnerabilities are at fault in anywhere from a third to more than half of all data breaches, depending on the study, so it’s natural to wonder why organizations don’t do a better job of patch management. The answer, based on a couple of presentations at the conference, is that patching is incredibly difficult to get right, requiring way more attention than most companies can afford to give it.
Art Ocain, VP for Cybersecurity and Incident Response at Airiam, noted that patching should be approached with a continuous deployment mindset, so teams should be able to patch 10 times a day.
Phil Venables, CISO of Google Cloud, said Google Cloud treats patching like another company might treat its top revenue-generating applications, with continuous updates similar to what a development team would use (see slides below).
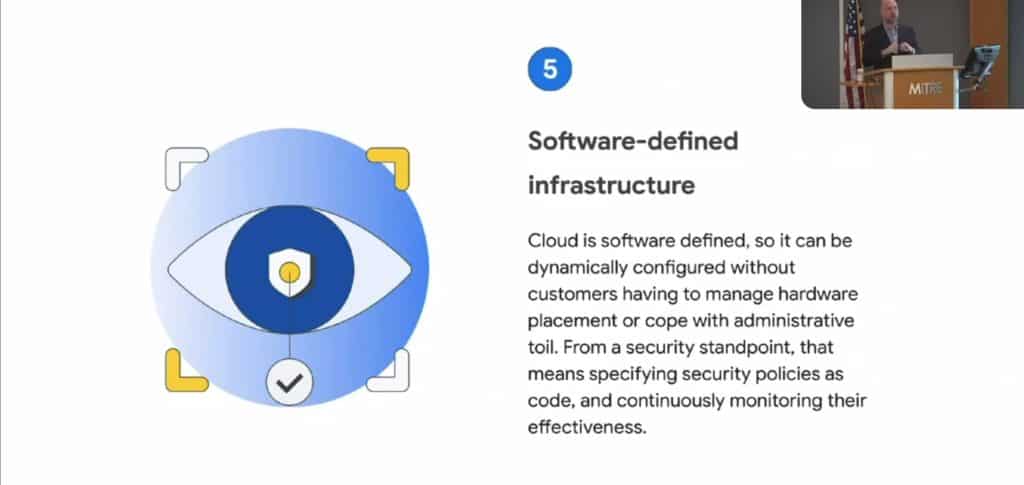
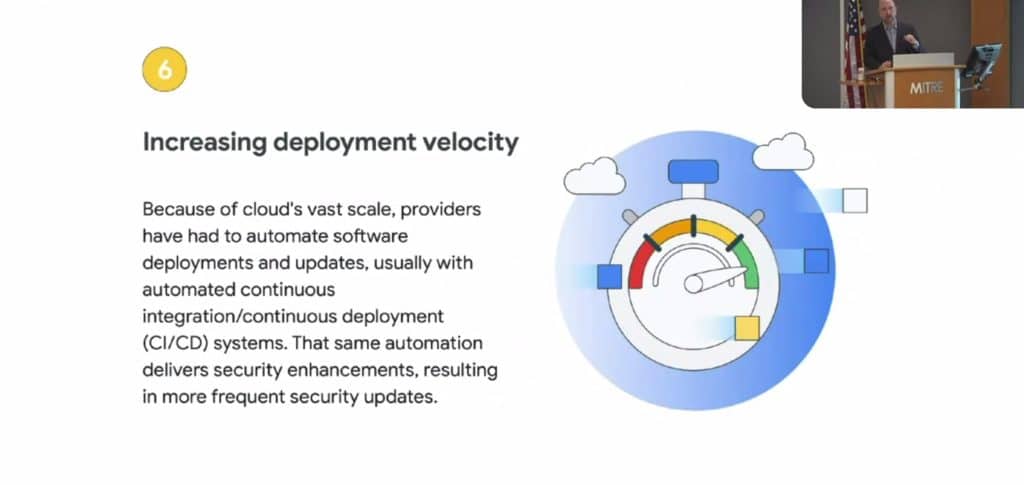
In addition to keeping up with patches, fixes and mitigations across applications, operating systems and endpoint and network hardware — there are roughly 20,000 new vulnerabilities a year, and several hundred of those are actively exploited by hackers — many organizations don’t even know everything they own, so asset management is part of the problem too.
The sheer difficulty is one reason that vulnerability management as a service (VMaaS) and similar services have been gaining traction among security buyers.
Google’s cloud security is well regarded (and the company has shared some documentation of its security architecture and practices too). Venables spent much of his presentation discussing the many ways Google Cloud reduces concentration risk (see slide below).

Also read:
- Is the Answer to Vulnerabilities Patch Management as a Service?
- MSSPs Fare Well in First MITRE Evaluations
Backup Is Hard. Really Hard.
Ransomware is the most feared cybersecurity threat, and with good reason: Its ability to destroy and steal data is almost without peer.
That double threat — exfiltration and destruction/encryption — makes backup and encryption of data critically important for recovery and to avoid extortion when hackers threaten to release sensitive data.
“Immutable backups” are often touted as the answer here. But even that needs to be incredibly secure — Ocain said Airiam has to take extra steps to protect even the laptop of the backup manager because hackers will find it. And keys and credentials are stored in a key vault so admins don’t keep them. The slide below shows the controls the MSSP has built into its backup and disaster recovery systems to keep customer data safe.
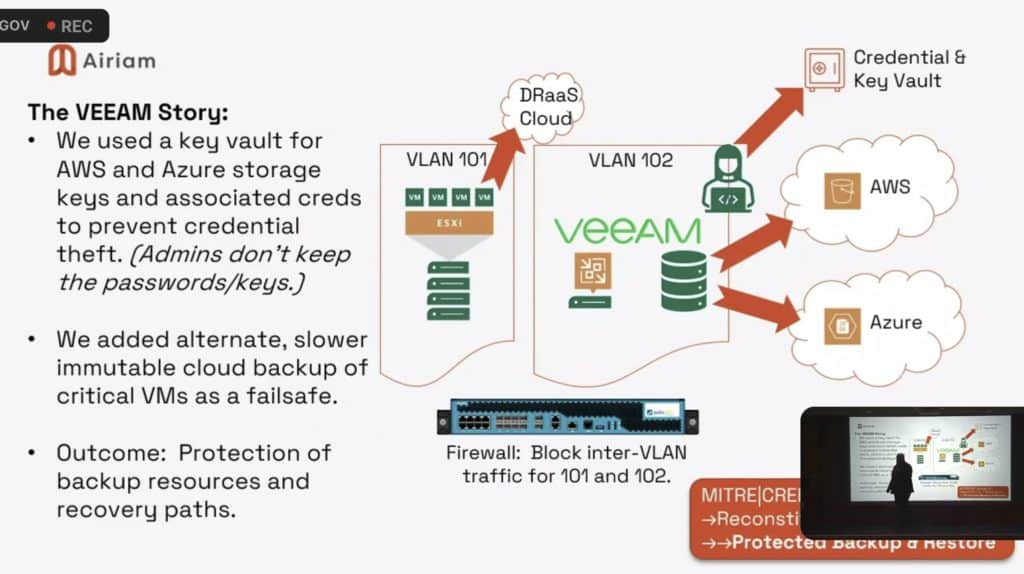
Continuous pentesting and ransomware simulations are among Airiam’s many controls. As Ocain put it, the company’s evolution “from good MSP to good resilience provider” was borne of necessity, and the company is now called in to consult on high-profile ransomware cases.
Also read: Building a Ransomware Resilient Architecture
Prepare Now
The conference — held in McLean, Va., and virtually — had a strong government and financial services focus, two sectors with high security needs that understand the limits of security tools and the need for resilience. That element gave the conference an air of realism: No one was claiming that they could stop every threat, and the focus was on the layers of defense that can keep an attack from spiraling out of control.
Government agencies and industries with high security needs have faced attacks and know they will continue, but most smaller businesses and non-IT companies don’t have the time or money to focus on cyber attacks until they happen. ResilienCyCon showed the error of that thinking. Those secondary layers of defense and response are critical, and are far cheaper than dealing with the consequences of an attack. They can make the difference between bending and breaking, so businesses would be wise to prepare now.
Read next: Best Incident Response Tools and Software








