Firewall-as-a-service (FWaaS) is a cloud-based product that delivers firewall capabilities through a subscription to the entire service. Unlike traditional firewalls, which rely on physical or virtual devices located at the network’s perimeter, FWaaS leverages the capabilities of next-generation firewalls (NGFW) and makes them available via the cloud. FWaaS deployments present both benefits and challenges for businesses moving to a cloud-based firewall.
Featured Partners: Next-Gen Firewall (NGFW) Software
Table of Contents
How Firewall-as-a-Service (FWaaS) Works
FWaaS serves as a filter between your network and the internet, identifying and blocking potential threats. This real-time filtration process ensures that only authorized and safe data reaches your network and helps protect your systems from malicious or suspicious activities.
Traditional firewalls are deployed as on-premises appliances or software, but that won’t do much to protect remote offices or mobile workers accessing cloud resources. But by moving firewall protections to the cloud through FWaaS and delivering them as a service, an organization can apply security policies and protections uniformly to assets regardless of where they reside. FWaaS typically uses agents on endpoint devices to deploy the firewall.
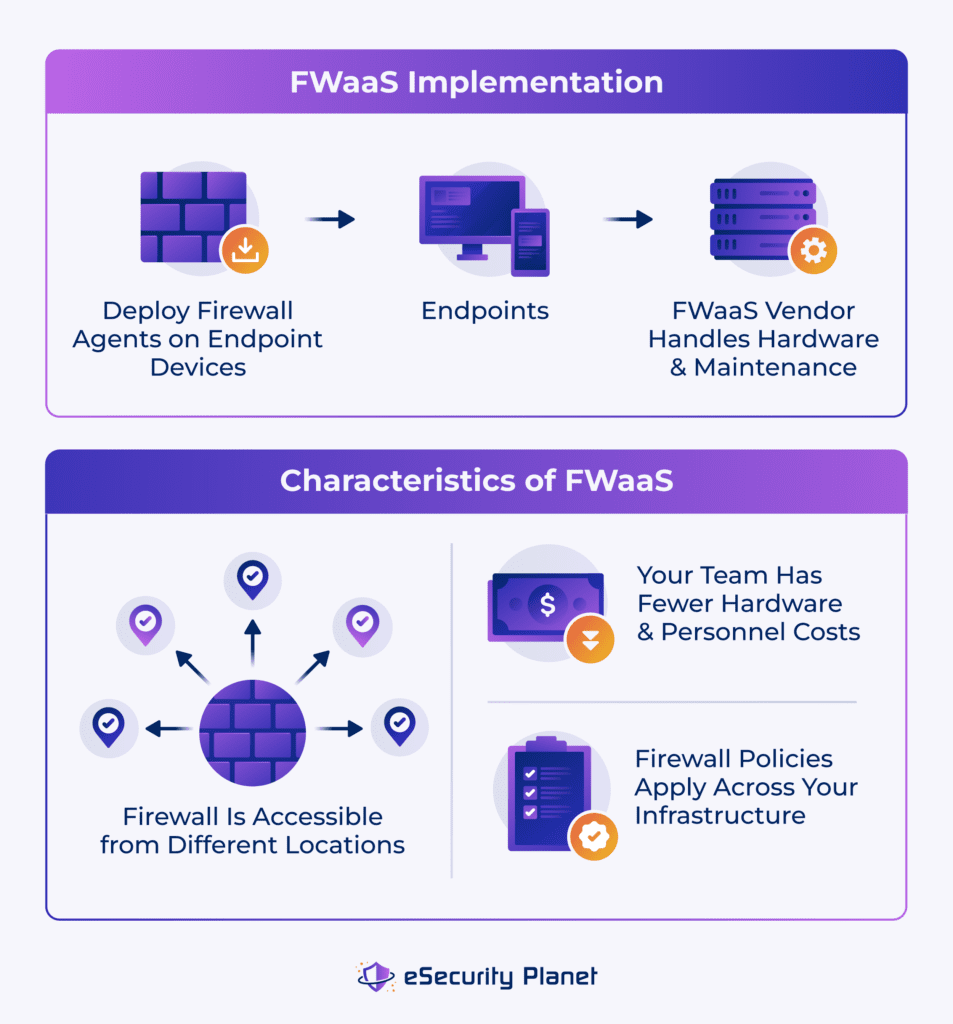
A firewall-as-a-service model has the following characteristics:
- Vendor management: The firewall vendor takes care of the back-end technology and intricacies of firewall management.
- Cloud-based structure: Cloud firewalls allow geographically scattered teams to benefit from network protection without needing a lot of on-premises hardware.
- Lower maintenance costs: Teams don’t have to buy as much hardware, and they also don’t have to hire personnel if they can’t afford to yet.
- Uniform policy enforcement: Protecting a business’ network assets in one cloud solution helps reduce firewalls’ typical rule and policy sprawl.
Before deploying agents on your organization’s devices, you’ll need to make sure your network can fully support FWaaS. Additionally, consider the relative importance of a FWaaS deployment for your specific organization, as well as its benefits and disadvantages. FWaaS is slightly different from other firewall deployments, like next-generation firewalls, and your business has multiple vendors to choose from and service costs to consider when buying a FWaaS solution.
Why Do Businesses Need FWaaS?
The cloud, remote workforces, Internet of Things (IoT), and mobile devices blur network boundaries and reduce the effectiveness of traditional perimeter security. Technologies like FWaaS, SD-WAN, and secure access service edge (SASE) have evolved to protect these expanding virtual networks. Both FWaaS and SD-WAN are part of broader SASE solutions, which also include cloud access security brokers (CASBs) and zero-trust network access (ZTNA).
To combat these constantly changing threats and growing attack surfaces, FWaaS adjusts its defenses to new attack vectors and threats by utilizing real-time data analysis and machine learning. It’s a seemingly simple change in traditional security models that increases network protection.
FWaaS also helps organizations by offering an easier way to scale security protections and keep up with firewall technical advancements, updates, and maintenance. A single vendor takes care of those maintenance tasks, like patching and audits, and smaller teams have reduced workloads and streamlined network security processes.
FWaaS Network Requirements
While firewalls as a service are simpler to implement and manage than traditional firewalls, your business still needs to meet a few requirements for an FWaaS deployment to succeed. If your IT team is considering FWaaS, use the following items as a checklist. You need to ensure that your existing network can support a cloud-based service, integrate with the FWaaS, be regularly maintained, and have reliable and logical firewall policies.
Networks Must Support Cloud-Based Services
Before your team jumps on the FWaaS bandwagon, ensure your networks can support it. If upper leadership approaches your IT or networking teams requesting a cloud-based firewall, ask them for time to research options and warn them that not all networks can successfully support FWaaS. Todd Thanhauser, president and CEO of Upper Echelon Technology, talked about the importance of this process before the deployment process ever begins.
“It’s essential to assess your organization’s Internet infrastructure, consider the bandwidth requirements, and ensure that your network connectivity can support the demands of a cloud-based firewall service,” he said. “Additionally, having a backup or redundant Internet connection can provide resilience and ensure continuous protection even in the event of a primary connection failure.”
Network requirements for an FWaaS deployment aren’t just about cybersecurity controls — your infrastructure has to be able to support a firewall in the event of natural problems, too. The ability to back up your firewall helps protect it from natural disasters and outages, as well as calculated attacks.
Existing Network Components Should Integrate with FWaaS
If your team is transitioning from a hardware-based firewall and planning to keep any existing systems, you’ll need to ensure that network components integrate well with the new FWaaS deployment.
Stefan Keller, the chief product officer at Open Systems, spoke about the importance of simple integration technologies for firewall services and old network systems. “This allows seamless activation of FWaaS without touching any on-site endpoint,” he said. “A gateway at the perimeter can be that integration point and forward all the traffic to the cloud.”
Keller also highlighted the difficulty of deploying FWaaS at branch offices. “A branch may have multiple VLANs or other network segments with east-west traffic.” According to Keller, this traffic isn’t ideal in the cloud, potentially for latency or regulatory compliance reasons.
“Relying on FWaaS for branches where you still have a lot of on-prem systems, applications, and IoT, is not the most effective approach,” he said. According to Keller, teams may be more successful if they deploy FWaaS and an on-premises firewall in a hybrid environment.
Your Team Must Continuously Maintain Networks
Don’t forget network maintenance after your firewall service has been deployed. Although “set it and forget it” is a popular term in the as-a-service world, it’s not the best idea in practice, especially for IT infrastructure.
You’ll need to regularly adjust firewall configurations, ensuring that the firewall can protect your business from new cyber threats, according to Anurag Gurtu, chief product officer at StrikeReady. “This involves updating security protocols, reviewing firewall rules, and monitoring system performance,” Gurtu said.
Firewall configurations shouldn’t just suit your business’ needs, either — they should also meet industry standards, something you’ll have to rigorously ensure on a consistent schedule. “Routine audits and compliance checks also play a significant role in maintaining the effectiveness of FWaaS over time,” Gurtu said.
Firewalls that protect healthcare or financial systems and data, for example, need to comply with any relevant data protection standards. If they don’t, your business could be fined.
You Need Clearly Developed & Consolidated Firewall Policies
Evin Safdia, the director of product marketing at Cato Networks, emphasized the importance of developing a consistent set of policies that are applied globally. “Most organizations that adopt FWaaS see a significant reduction in total policy rules, resulting in easier ongoing management and a consistent experience for end users,” he said.
But according to Safdia, moving and adjusting your business’ old firewall policies within a new FWaas architecture can feel overwhelming. He recommends taking a broad, organization-wide approach to firewall policies, outlining rules and exceptions from a high level.
“Once you’ve built this, compare it against your existing policies to ensure no gaps, and you will be ready to build these policies in any FWaaS platform. Put simply, don’t necessarily try to recreate the legacy policies from your new FWaaS provider — create what best fits your organization at present,” he said.
Don’t skimp on this part of the process. Before any firewall services are deployed in your existing infrastructure, your IT or network admins should list all firewall policies and create any necessary blocklists and allowlists. If you know exactly what policies you need, you’ll set your team up to better combine old and new policies from the vendor. Feel the freedom to drop old policies if they’re no longer what your business needs.
8 Benefits of FWaaS
The primary advantage of FWaaS is that it makes the term “outside the firewall” obsolete by adding firewall protections to everything that could be considered part of a broader virtual enterprise network. More specifically, the key benefits of firewall services include cloud security and growth, remote management, network architecture improvements, and clearer policy enforcement, visibility, and reliability.
Security at Cloud Speed
FWaaS offers robust security in remote environments without slowing things down. With FWaaS, your data and applications stay protected without affecting performance because your security is decentralized from your organization’s premises. FWaaS integrates with your cloud system and virtual networks, ensuring that security doesn’t hinder operations and makes growth and changes more secure.
If you choose to integrate FWaaS with your existing cloud applications, make sure your business is following cloud security best practices, including training employees and securing endpoint devices.
Flexible Cloud-Based Scaling
As your organization grows, security needs to keep up. FWaaS removes concerns about inadequate protection during expansion. Whether you’re entering new markets, launching products, opening new data centers or offices, or seeing a surge in users, FWaaS is designed to scale. This flexibility provides security even during rapid growth.
Global Security Management
Maintaining consistent security across locations is challenging. FWaaS empowers you with centralized control of large virtual environments. Regardless of your operational reach, you can manage and enforce security policies from one place. This global reach and control ensure effective security measures wherever your data goes.
Support for Modern Network Architecture
FWaaS integrates with modern networks, supporting recent tech and protocols. Whether your business is transitioning to microservices or exploring edge computing, well-designed, modern FWaaS adapts, ensuring robust and future-proof security.
Simplified Network Architecture
FWaaS simplifies network architecture and security, removing confusing and disparate setups that invite vulnerabilities. Because one vendor is responsible for everything, technology better integrates, and vendor-managed architecture lightens the burdens on the customer’s networking and security teams.
Streamlined Policy Enforcement
FWaaS automates policy enforcement across distributed networks. By ensuring consistent, efficient security, FWaaS lowers risks, improves agility, and increases compliance with government regulations and industry rules. And eliminating the need for local security solutions can save money, too.
Increased Network Visibility
FWaaS improves network visibility with a broader view of traffic patterns, potential threats, and anomalies. Better visibility means you can detect and respond to suspicious activity faster, too, potentially keeping small security incidents from becoming major ones.
Enhanced Infrastructure Reliability
With greater insight into threats and vulnerabilities, FWaaS improves the reliability of networks and operations. If they’re secure, they’re more likely to process traffic in a safe, consistent way. Proactive security protections reduce the interruptions brought on by malicious activity.
8 Challenges of Firewall-as-a-Service
Whether FWaaS is suitable for your organization will depend on your specific needs, security requirements, and existing infrastructure. It’s important to evaluate potential disadvantages, as well as benefits when considering FWaaS. While firewalls as a service offer numerous benefits, you should also consider potential disadvantages like lack of customization, privacy issues, vendor concerns, and a decreased ability to manage local security and technology.
Dependence on Internet Connectivity
FWaaS heavily relies on a consistent internet connection. If your organization faces internet outages or slowdowns, the network security provided by FWaaS could be compromised. During such instances, your network might be vulnerable to cyber threats due to the reliance on connectivity for protection. If the provider’s cloud infrastructure goes down, the same problem applies.
Limited Control Over Customization
Unlike traditional on-premise firewalls, FWaaS might restrict customization options. This can be challenging for organizations with specific security needs or unique network setups. The predefined settings might not align with your organization’s requirements, which could affect your desired level of protection.
Data Privacy Concerns
The use of third-party cloud servers for routing network traffic raises concerns about data privacy and compliance. Organizations handling sensitive data might hesitate due to potential exposure to data breaches. Complying with regulations becomes more complex when data processing occurs outside the organization’s premises, requiring you to carefully evaluate a potential FWaaS provider’s data handling practices.
Uncertain Vendor Reliability
The effectiveness of FWaaS is tied to the reliability of the chosen vendor. Downtime, technical glitches, or breaches on the vendor’s end could compromise your network’s security. Vetting the vendor’s track record and security measures is essential to mitigate this risk.
Initial Migration Complexity
Implementing FWaaS involves modifying existing network structures and configurations. Migrating from traditional firewalls might require IT teams to acquire new skills, and you’ll need to implement your organization’s policies on a new firewall configuration. This initial deployment curve can take significant time, though it’s a natural part of implementing any new technology.
Ongoing Costs
FWaaS eliminates upfront hardware expenses but introduces continuous subscription-based costs. Over time, these costs could surpass the investment of traditional firewalls. Organizations must weigh the long-term convenience and improved security against the accumulating expenses.
Limited Local Inspection
Traditional firewalls enable detailed local network traffic inspection. However, FWaaS might perform some inspection in the cloud, reducing visibility into local network activities. This could impact threat detection within your organization’s network.
Integrating with Existing Systems
Integrating FWaaS with existing network structures and tools can be complex, especially if you have a lot of legacy networking equipment. The firewall integration process requires careful planning and potential custom development. Misaligned integration could lead to disruptions or security vulnerabilities.
How Much Does FWaaS Cost?
Costs for firewall services vary widely between vendors, but they also vary depending on your business’s environment — how many applications you need to protect, any subscription fees, and vendor-side maintenance costs. Since your business isn’t paying for hardware, FWaaS costs rely largely on deployment and management the vendor has to perform.
Microsoft Azure and Amazon Web Services both offer cloud-based firewalls that they only price based on policies and deployments — each costs $100 per policy per month. Azure also gives the option to pay $0.40 per hour for each firewall deployment. Generally speaking, firewall services can cost anywhere from $40 a month (or fewer) to a few hundred dollars a month. But very expensive solutions can go into the thousands of dollars per month.
Top 3 FWaaS Solutions
While there are a number of standout FWaaS solutions, three stand out in our analysis. Perimeter81, Cisco Secure Firewall, and Zscaler offer distinctive methods for safeguarding networks and data tailored to meet the demands of complex enterprise environments.

Perimeter 81
Perimeter 81 is an FWaaS vendor that focuses on providing secure access to on-premises and cloud resources. Its zero trust network access (ZTNA) strategy allows users to access resources based on their identification. Perimeter 81’s user-centric architecture allows businesses to specify and control security rules based on people, groups, and apps. The Premium Plus plan costs $16 per user per month and $40 extra per month for each gateway.


Cisco Secure Firewall
Cisco offers a range of firewalls that encompass hybrid, cloud, and SASE use cases. Secure Firewall is an NGFW solution known for its strong security features and all-encompassing threat defense capabilities. To defend networks from both known and new threats, it incorporates powerful intrusion prevention, application control, URL filtering, and malware protection. Contact Cisco to receive a custom quote for your business.


Zscaler
Zscaler’s cloud firewall is part of the company’s Security Services Edge (SSE) platform and provides a comprehensive solution particularly suited for hybrid environments. Zscaler uses advanced security technologies to focus on real-time threat prevention, like sandboxing and threat intelligence. It inspects all communication, including encrypted traffic, for possible threats, malware, and phishing attempts. Contact Zscaler for a custom quote.
What Are the Differences & Similarities Between FWaaS & NGFW?
FWaaS is a cloud-based service that provides firewall functionality as part of a cloud computing environment. An NGFW is a type of firewall that typically goes beyond traditional network firewall functionality by adding advanced features like application awareness and intrusion prevention. The two terms measure slightly different things, but they can overlap — some FWaaS solutions offer advanced NGFW functionality, while some NGFWs are cloud-based.
FWaaS offers the same protection as traditional on-premises firewalls but is delivered as a service over the Internet. FWaaS is a larger category that can contain both simpler firewalls and NGFWs.
FWaaS & NGFW Differences
The following chart highlights the differences between FWaaS and NGFW deployments, including how they’re managed and how customizable they are.
| FWaaS Features | NGFW Features | |
|---|---|---|
| Deployment Approach | Operates through cloud-based management by a third-party provider | Utilizes physical or software appliances deployed either on-premises or virtually |
| Management Structure | Managed externally by a provider using web interfaces or APIs | Internally managed, offering greater control over setup and configuration |
| Functional Range | Offers fundamental firewall features and limited supplementary security services | Provides advanced capabilities, such as deep packet inspection and threat detection |
| Customization Options | Limited customization due to cloud-centric design | Allows more tailored customization for security policies |
| Scalability | Achieves scalability through cloud resources and infrastructure | Scalability depends on available hardware and resources |
| Cause of Latency | Can cause potential latency due to reliance on cloud-based processing | Demonstrates lower latency because data processing happens within the organization’s premises |
| Compliance & Data Privacy Implications | Raises data privacy concerns because network traffic is routed through third-party cloud servers | Provides control over compliance because data is processed within the organization’s environment |
FWaaS & NGFW Similarities
FWaaS and NGFW share many common firewall characteristics:
- Security policy implementation: Both solutions enforce security policies to ensure network safeguards.
- Threat detection capability: Both FWaaS and NGFW can identify and respond to a wide range of threat types.
- Application control features: Both encompass application control features, regulating user access.
- Management console: Both offer centralized management interfaces for handling firewall-wide policies.
- Packet filtering functionality: Both execute packet filtering, permitting or blocking specific data packets.
- Access management: Both manage incoming and outgoing data traffic through access controls.
If an NGFW also sounds like a good option for your team, check out the top NGFW vendors next, as well as the most important features to look for in NGFWs.
Bottom Line: Improve Security & Flexibility with FWaaS
FWaaS is a flexible cybersecurity solution specially designed to manage the complexities of the contemporary digital ecosystem. By utilizing cloud technology, FWaaS greatly expands the utility of firewalls to encompass cloud, hybrid, and virtual network environments. It’s also beneficial for smaller organizations or limited networking and security teams with more time to do complex tasks when their firewall is externally managed.
Is your business considering other cloud security solutions aside from firewalls? Learn more about Zscaler, Palo Alto, Tenable, and our other picks for top cloud security providers.
Sam Ingalls and Jenna Phipps contributed to this article.









