Secure access service edge (SASE) provides an integrated service solution to secure large virtual networks that encompasses users and resources no matter where they are or how they access each other. Large, sprawling organizations need this type of technology because they often struggle to apply consistent security policies outside of their network to remote workers accessing cloud-hosted resources, branch offices, and edge computing.
We will explore SASE in more detail through the following topics:
- What Problem Does SASE Solve?
- What Is SASE?
- How Does SASE Work?
- Top 6 Capabilities of SASE
- What Are the SASE Benefits?
- What Are the SASE Challenges?
- Implementing SASE
- Bottom Line: Implement SASE to Improve Security and Operations
What Problem Does SASE Solve?
Traditional networking either causes operations bottlenecks by forcing all traffic to route through centralized firewalls or exposes remote assets and cloud resources to attack. The trends to adopt Internet of Things (IoT) devices, remote work, and cloud resources drastically increase the amount of communication outside of the traditional network that needs to be secured.
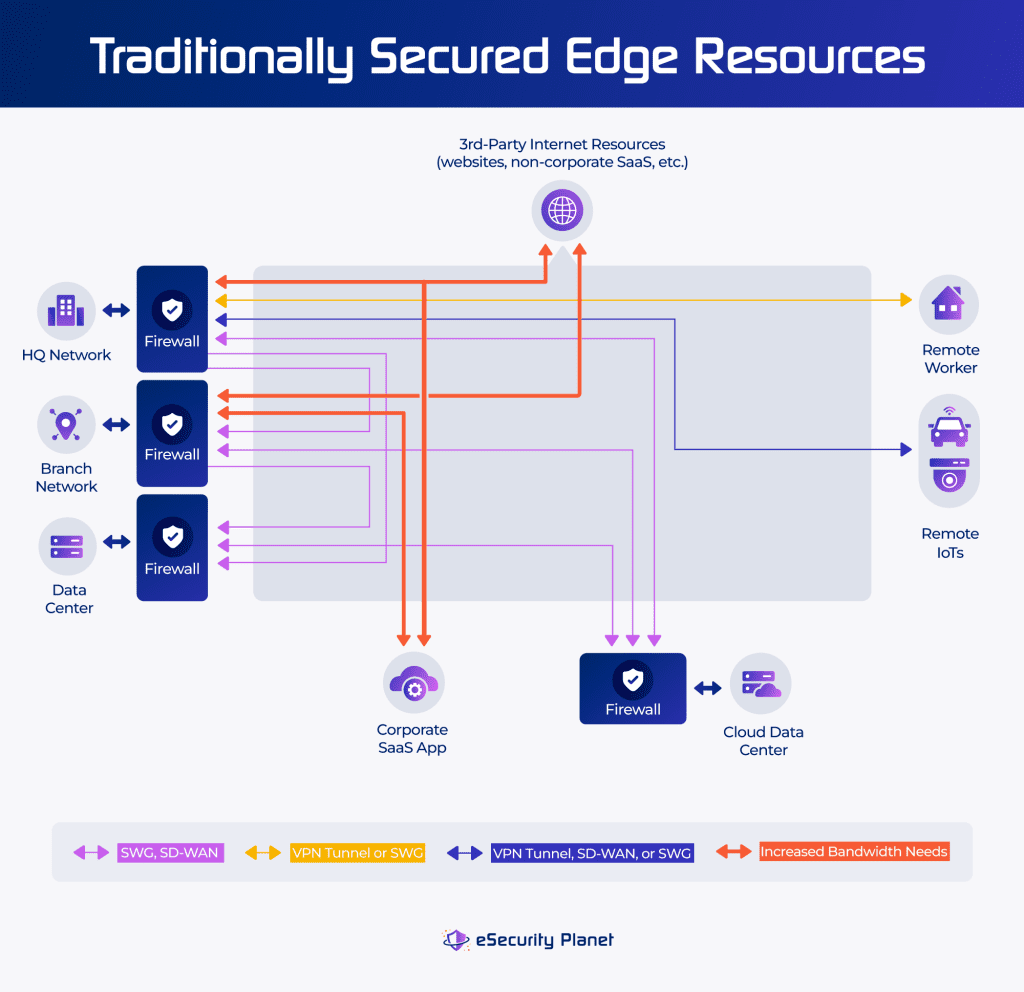
Additionally, operations bottlenecks lead IT departments to move storage and processing functions closer to the edge of the network to avoid performance hits for users or data center overload. This trend spreads out data center risk over the internet and increases the potential vectors for attack. SASE provides an edge security solution that addresses these challenges without the bottlenecks of traditional virtual private network (VPN) solutions.
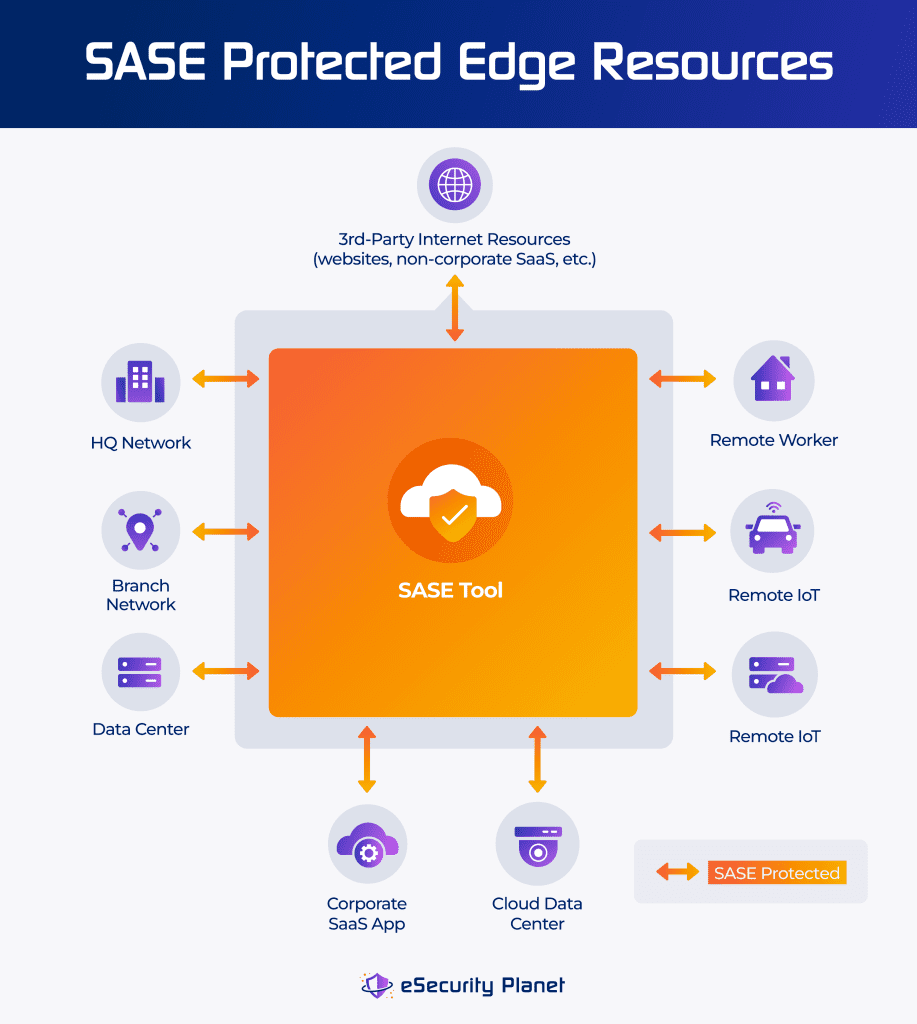
What Is SASE?
Gartner coined the term SASE (pronounced ‘sassy’) in its Future of Network Security in the Cloud report published in 2019 and defines SASE as converged network and security capabilities that incorporate technologies such as software defined wide area networking (SD-WAN), cloud access security brokers (CASBs), secure web gateways (SWGs), next generation firewalls (NGFWs), and zero-trust network access (ZTNA). The “edge” refers to the hardware device (data center server, laptop, IoT) directly connected to the internet where it might be exposed to attack.
In practice, various SASE vendors will emphasize their specialty, such as networking or cloud access, in their definition of the technology to provide their solution with advantages. For example:
- Cloudflare excludes SD-WAN from their core security components of SASE because they do not offer a SD-WAN technology
- Fortinet excludes CASB from their definition of SASE because they do not offer a CASB solution
These variances can cause confusion regarding the definition of SASE, yet the core definition remains intact: SASE secures remote resources through integrated management services hosted in the cloud.
6 Key Capabilities of SASE
To be considered a SASE solution, the vendor must provide the following solutions:
- Centralize control through a cloud-hosted, centrally managed solution and a single software interface
- Monitor network status and provide reports on performance and security
- Monitor user activity and provide data loss prevention (DLP) analysis; usually through CASB or NGFW capabilities
- Inspect traffic to block malware and malicious URLs through a centralized control and filtering; usually through a SWG or Firewall-as-a-Service (FWaaS) capabilities
- Control access to data and resources based upon user, device, and permissions; usually using ZTNA, SD-WAN, or CASB capabilities
- Secure cloud-based assets such as applications, websites, and Software-as-a-Service (SaaS) resources; usually using SWG, FWaaS, or web application firewall (WAF) capabilities
How Does SASE Work?
SASE vendors provide points of presence (PoPs) worldwide using the cloud or SD-WAN technology. The distributed access points avoid latency problems through short-distance connections to high-speed networks.
SASE secures each device and performs networking decisions to direct traffic from different applications to different users as efficiently and securely as possible. SASE can dynamically allow or deny connections to services and applications based on an organization’s defined security policies and access rules. Although the goal will be to provide continuous assessment to enable zero trust access control, an organization should double-check the current capabilities of the vendors under consideration.
SASE manages the internet exchange connections and ensures that the connection to cloud applications remains stable, aiding in low latency. The single management console provides centralized control and monitoring for the organization and ensures consistent security policies applied throughout the organization.
What Are the SASE Benefits?
When compared with traditional network security technologies, SASE provides distinct advantages for operations and security, including:
- Adaptive agility: Using centralized, cloud-based architecture, SASE enables direct-to-network or direct-to-cloud access for a huge range of devices over a broad geography; deployment of the service, scaling users, or adding new branch offices can be quick and simple compared to on-site infrastructure
- Consistent security: Centralized control and management enables consistent application of security and compliance policies across all branch offices, remote workers, cloud resources, and connected devices
- Data protection: Apply consistent data protection policies and data categorizations across all devices, applications, and users to prevent unauthorized access and abuse of sensitive data
- End-to-end security: SASE tools seek to deploy the granular control of zero trust to ensure complete session protection regardless of whether a user is connected to the organization’s network; SASE also deploys additional security features such as web filtering, domain name service (DNS) security, data loss prevention, and malware detection and blocking
- Improved performance: SASE enables high volumes of devices to connect to networks securely and reliably by routing network traffic across a global edge network, and traffic is processed as close to the user as possible and reduced by spreading it out across many different access points; SASE also monitors traffic and can reduce the occurrence or severity of distributed denial of service (DDoS) attacks
- Improved security: SASE can upgrade traditional network connections such as legacy VPNs or firewalls with cloud-hosted and cloud-maintained services that provide more technologically advanced capabilities — especially for remote and mobile users
- Potential financial savings: Investing in SASE eliminates the need to buy and maintain different security equipment or tools that would otherwise have to be purchased to obtain the capabilities of a single SASE implementation; engaging SASE also converts any potential capital expenditures (CapEX) into operational expenditures (OpEx) which helps predictability and cash flow
- Reduced complexity: SASE deployment reduces the need to manage, maintain and update many different tools or to monitor many different networks and connections because SASE consolidates the security and operations management into a single tool
- Threat exposure insight: SASE tools use monitoring features similar to Intrusion Detection and Prevention Systems (IDPS), firewalls, and DLP to detect threats, analyze user behavior, and block potential instances of data exfiltration — even from SaaS or public cloud resources outside of the corporate network
What Are the SASE Challenges?
When considering a SASE implementation, an organization may need to overcome challenges such as:
- Concentrated risk: Adopting SASE eliminates many other solutions and puts the entire risk of failure on the capabilities of the SASE tool and vendor; additionally, by centralizing all capabilities worldwide, the failure of the SASE vendor results in a potential global work stoppage for the organization
- Dramatic transition: When adopting SASE, many existing solutions can become redundant, but an organization may need to maintain those solutions until the security team is confident that the SASE solution is properly implemented and integrated; teams accustomed to other vendor reporting and control software will need training on the new solution
- Increased costs: Although larger companies replacing many security tools may see cost reductions, smaller organizations that had never previously secured assets outside of the network may experience increased costs
- No industry standard: As a newer technology standard, implementation of SASE can mean different things to different vendors, so buyers need to carefully review each option
- Reduction of features: As a generalist tool, SASE will deliver the broad capabilities of component tools such as CASB, DLP, NGFW, or SD-WAN; however, many of the advanced capabilities and features of specialty tools may not be available in the SASE solution
- Tedious setup: IT teams previously set up tools one-by-one and now must set up all users, data categories, and devices simultaneously in a new tool; security and operations teams will need to coordinate to avoid conflicts related to local compliance requirements in various geographical areas; and organizations that had never set up the granular controls for zero trust will need to classify employees and data or risk undermining security
Implementing SASE
Moving to SASE requires an organization to understand its resources and needs:
- Asset management: What assets (user devices, cloud infrastructure, IoT, SaaS, etc.) exist outside of the traditional network, and to what other resources do they need to connect?
- Equipment and tool reduction: Which existing SD-WAN, firewall, and network security tools will be made redundant by SASE and can be eliminated?
- Network adaptation: Placing branch offices behind the SASE perimeter can simplify infrastructure, but what network segments need to remain segregated?
- Remote users: Which users work remotely, and what assets do they need to access as part of a group or as an individual?
Once these questions are answered, the organization can contract with the SASE provider and begin the process of integrating SASE with existing infrastructure and tools. Redundant architecture and tools should not be eliminated until the SASE solution has been thoroughly tested.
Bottom Line: Implement SASE to Improve Security and Operations
Sprawling organizations with many cloud-based or remote resources will greatly benefit by adopting SASE solutions. Security will become centralized, integrated, and simplified and operations can improve by removing any VPN and local firewall bottlenecks. As SASE continues to evolve and improve, the cloud-based SASE solutions will quickly deploy upgrades and enable artificial intelligence (AI) enhancement as well.
For additional reading:
This article was originally written by Paul Shread on November 24, 2020 and revised by Chad Kime on August 11, 2023.








