As cloud computing evolves, so has cloud security, and buyers in the market for cloud security solutions may find themselves facing a dizzying array of acronyms, like CNAPP, CWPP, CSPM, and CIEM.
We’ll examine each of those cloud security technologies — along with CASB too — and their uses, and direct you to some of the top cloud security solutions. But first, here’s a quick overview before we explore each in-depth:
- Cloud Security Posture Management (CSPM): Best used to maintain a robust security posture across your cloud infrastructure by instantly discovering configuration errors and compliance violations.
- Cloud Workload Protection Platforms (CWPP): Best used for securing specific workloads and applications, with a particular focus on runtime safety and vulnerability management.
- Cloud Infrastructure Entitlement Management (CIEM): Best used to effectively manage cloud resource entitlements, reduce access risks, and maintain compliance.
- Cloud Native Application Protection Platforms (CNAPP): CNAPP solutions have evolved to encompass all that, and are best used to secure cloud-native apps and for specialized protection of containerized and serverless environments.
Jump ahead to:
- Evolution of Cloud Security Solutions
- CWPP (Cloud Workload Protection Platforms)
- CSPM (Cloud Security Posture Management)
- CIEM (Cloud Infrastructure Entitlement Management)
- CNAPP (Cloud Native Application Protection Platform)
- Should You Use CSPM, CWPP, CIEM, or CNAPP?
- Another Solution to Consider: CASB (Cloud Access Security Broker)
- Bottom Line: Improve Your Organization’s Cloud Security
Evolution of Cloud Security Solutions
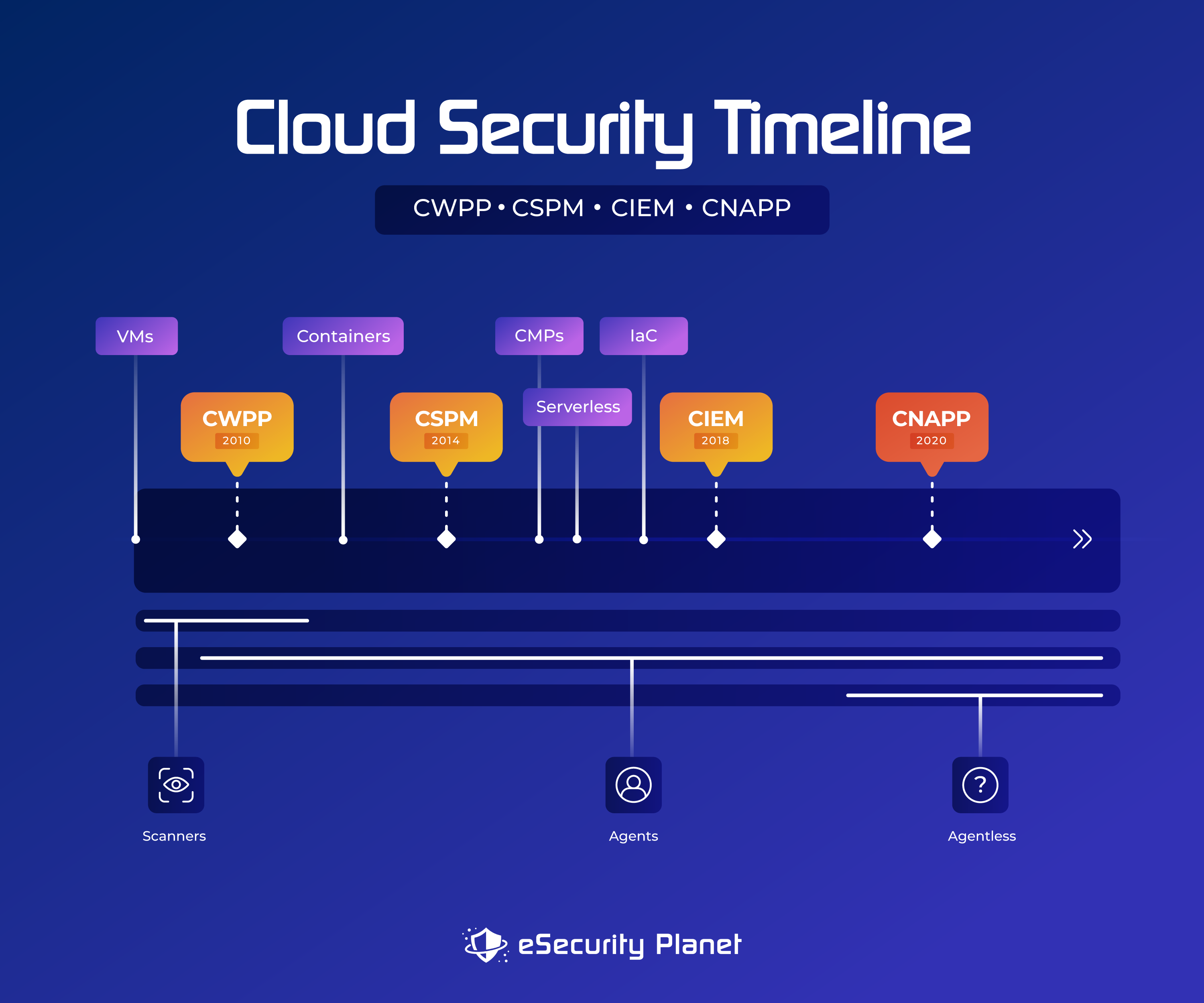
The cloud computing era began in 1999, when Salesforce proved the utility and popularity of SaaS (software as a service) applications with the launch of its CRM service. Amazon did the same thing for cloud infrastructure (IaaS) with the launch of AWS in 2006, and platform as a service (PaaS) offerings began to appear around the same time.
Securing all those new cloud environments and connections became a job for cybersecurity companies. Gartner played a big role in the development of cloud security terminology, coining the term “Cloud Workload Protection Platform” in 2010 to describe a tool used for safeguarding virtual machines and containers. In 2012, Cloud Access Security Brokers (CASB) began to emerge to monitor user access of cloud services.
Cloud Security Posture Management services (CSPM) began to appear in 2014 to manage cloud service configurations as cloud service providers like AWS, Microsoft Azure, and Google Cloud grew more prevalent. Identity discrepancies in account entitlements led to the rise of Cloud Infrastructure Entitlement Management (CIEM) a few years later, and in the last two years Cloud Native Application Protection Platforms (CNAPP) have emerged to tie together CWPP, CSPM and CIEM into a comprehensive cloud security platform.
We’ll take an in-depth look at each below.
CWPP (Cloud Workload Protection Platforms)
Cloud Workload Protection Platforms are a great option for companies looking to secure specific workloads and applications in the cloud. CWPP provides strong defenses against a wide range of risks such as malware, ransomware, DDoS attacks, configuration errors, insider threats, and data breaches. To ensure security for cloud-based resources, CWPP solutions offer unified visibility and administration for physical machines, VMs, containers, and serverless workloads.
Key CWPP features
- Checks conformity with industry standards and regulatory requirements by carrying out security configuration evaluations, audits, reporting, and creating compliance reports.
- Effective security monitoring and threat detection are made possible by comprehensive insights into cloud workloads, including configuration, software inventory, network connections, and user access rights.
- Enhances visibility, administration, and security control using native cloud security services and APIs across cloud platforms such as AWS, Azure, and Google Cloud.
- Ensures encryption, data loss prevention (DLP), and access restrictions to protect data from unwanted access, data leakage, and exfiltration.
- Improves security by assisting in the isolation of tasks and limiting communication between them.
- Shields cloud workloads from dangers during operation by providing runtime protection.
- Reduces human labor, speeds up security operations, and maintains uniform security across workloads with automated vulnerability detection, incident response processes, and unified security policy administration.
- Secures server workloads across a range of public cloud settings and hybrid data center architectures.
- Supports application architectures built on containers.
- Utilizes incident response and management capabilities, including real-time alerting and threat intelligence integration to identify and reduce security breaches.
CWPP Benefits
- By focusing security on unique vulnerabilities and threats for each workload, CWPP improves the overall security of cloud applications.
- Continuous monitoring makes sure that suspicious behaviors and abnormalities are promptly discovered, enabling quick reaction to any security problems.
- Provides detailed insights into each task.
- The best CWPP products are scalable, flexible, and responsive to changing demands in dynamic cloud settings.
CWPP Limitations
- Certain facets of the overall cloud architecture may not be as well-covered due to CWPP’s primary focus on securing specific workloads.
- Complexity can become an issue when configuring and administering separate workloads, particularly in large-scale cloud installations.
- Integrating additional solutions may be necessary to provide comprehensive security.
- Limited visibility into the cloud control plane, inaccuracies in alert prioritization, and incomplete coverage brought on by agent-based deployment.
- Some CWPP products could have difficulty scaling.
- Maintenance could lead to increased overhead expenditures.
- The performance of cloud workloads may be impacted by monitoring and real-time threat detection.
See the Top Cloud Workload Protection Platforms (CWPP)
CSPM (Cloud Security Posture Management)
Cloud Security Posture Management is a strategic approach for managing security and compliance in cloud computing environments. CSPM identifies, assesses, prioritizes, and manages risks at both the infrastructure and configuration levels within the cloud. For businesses seeking to secure their cloud infrastructure, CSPM is the best option.
Key CSPM features
- Advanced data governance and compliance management are included, as are customized or prebuilt rules based on regulatory frameworks such as HIPAA, GDPR, NIST, PCI-DSS, CIS, ISO, and SOC 2.
- Compatible with third-party threat intelligence.
- Conducts risk assessments on cloud assets and setups to uncover vulnerabilities and security flaws.
- Detects problems with misconfiguration and compliance hazards in cloud infrastructures.
- Provides multi-cloud configuration management as well as compliance reporting.
- Provides detailed advice and enables for manual or automatic remediation.
- Offers real-time monitoring and automated assessments for compliance with cloud security best practices.
- Risk monitoring and evaluation at the infrastructure level, with risk rating and visualization for simpler detection.
- Uses automation for policy enforcement, categorization, and remediation, reducing security and compliance concerns caused by misconfigurations.
- Uses industry benchmarks, regulations, behavioral analytics, and machine learning for automated threat intelligence to detect and mitigate cloud security risks.
CSPM Benefits
- Checks for compliance standards and enforcement that are in line with corporate, regional, and industry-specific requirements, reducing the strain on cybersecurity teams.
- Identifies possible risks and makes recommendations for enhancing security posture.
- Provides real-time security and compliance monitoring, giving stakeholders with varied degrees of cybersecurity experience increased visibility.
- Simplifies risk detection and remediation efforts in complex cloud environments through automation.
- Supports multiple cloud environments like AWS, Azure, and GCP.
Limitations
- Difficulties in integration with some cloud platforms or outside tools.
- Inadequate support for certain specialized or niche cloud services.
- Lacks insights into workloads.
- Limited application-level security coverage.
- Managing cloud systems that are complicated and evolving quickly may be challenging.
- Requires highly skilled employees to successfully understand and use the tool’s findings.
- Lacks lateral movement risk detection.
- Poorly prioritized notifications, excessive alerts, and false positives that may need manual review.
- Possible weaknesses in protecting against dynamic and evolving threats.
- Potential performance effects during ongoing cloud installations at scale.
- Relies thoroughly on accurate and current cloud provider APIs for assessments.
- Relies on correct deployment and configuration for efficient risk detection.
See the Top Cloud Security Posture Management (CSPM) Tools
CIEM (Cloud Infrastructure Entitlement Management)
With a special focus on identity and access management (IAM) in the cloud, CIEM (Cloud Infrastructure Entitlement Management) is appropriate for enterprises that need to manage and protect access to cloud resources. CIEM stops unwanted access and potential data breaches caused by compromised or over privileged accounts as cloud environments become more sophisticated and the number of users and permissions increases. CIEM helps businesses improve the visibility, management, and governance of their cloud infrastructure while reducing the risk of external and internal assaults.
Key CIEM features
- Examines permissions for multi-cloud access and makes recommendations for entitlements.
- Implements compliance reporting and least-privilege access.
- In order to find abnormalities and possible security concerns, CIEM tools analyze user behaviors and access patterns. By identifying suspicious activity, such as erratic login attempts, they may send out alerts to initiate rapid response.
- Offers strong identity governance features, managing user identities, roles, and permissions across cloud resources to provide access in accordance with the least privilege principle and lowering the risk of illegal access.
- Regular CIEM review of entitlements aids in identifying and fixing over privileged accounts or underused entitlements to reduce the attack surface, as well as detecting and mitigating any security issues connected to access rights.
- To make sure that users adhere to compliance standards and security best practices, CIEM enforces access restrictions and rules for cloud resources.
CIEM Benefits
- Assures adherence to best practices and helps firms maintain compliance with compliance requirements and internal security standards.
- By lowering the possibility of data breaches and illegal access to vital resources, CIEM dramatically improves cloud security.
- Helps in countering insider threats and potential data exfiltration by applying the least privilege principle and keeping track of user access patterns.
- Streamlines access management to give security teams centralized control and visibility over cloud entitlements.
Limitations
- Full IAM features may be lacking in some CIEM solutions, and there may be gaps in full context and visibility.
- CIEM systems may provide false alerts.
- Implementing CIEM in large-scale, complicated cloud settings can be difficult; it may also require careful design and interaction with current IAM solutions.
- Lateral movement concerns are not addressed by CIEM.
- To set up and administer access controls using CIEM systems, administrators and security teams may need specialized training.
CNAPP (Cloud Native Application Protection Platforms)
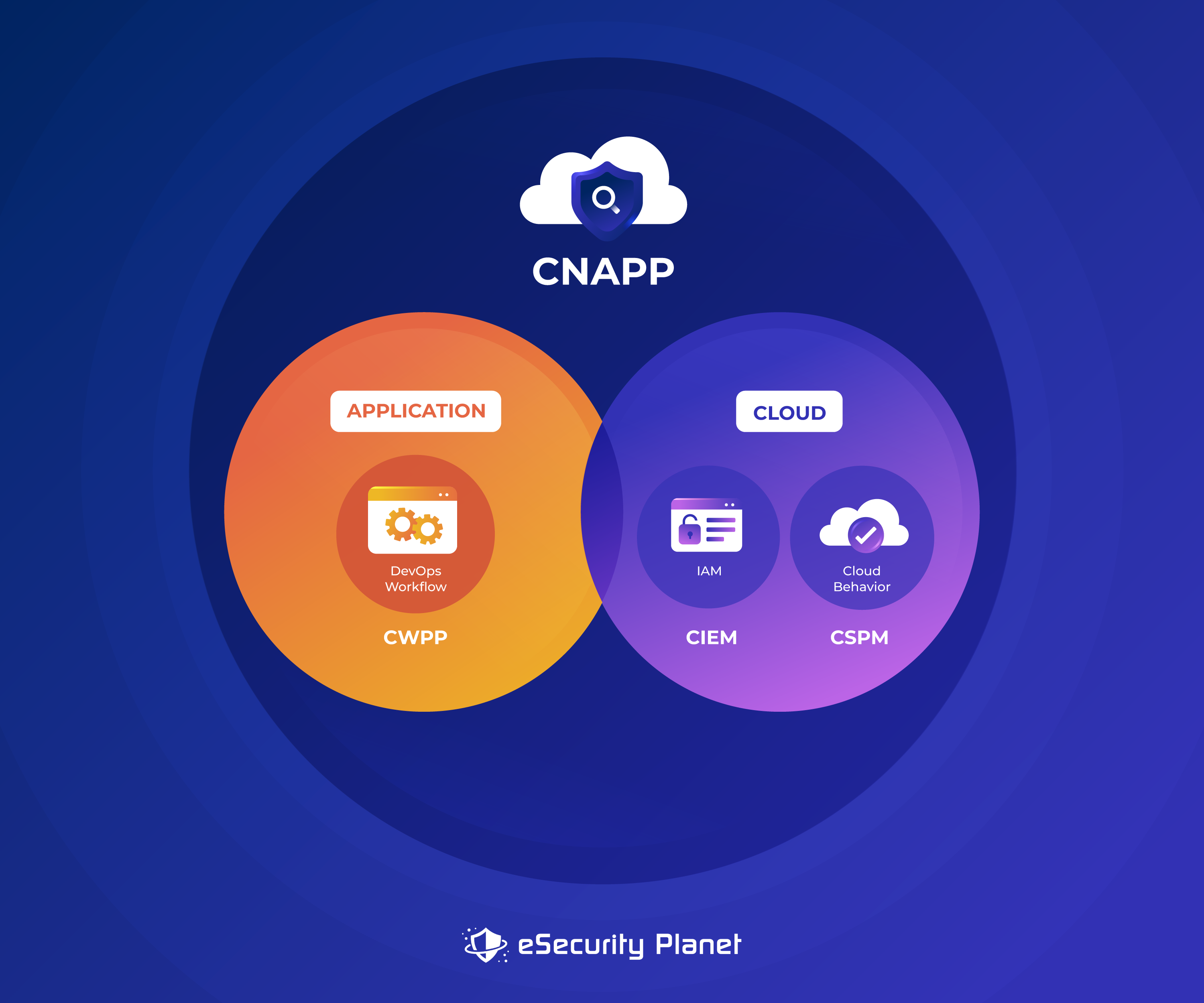
Cloud Native Application Protection Platforms combine CSPM, CIEM, CWPP, Infrastructure as Code (IAC) scanning, and more to provide comprehensive protection for cloud workloads, apps, identities, access management, and development environments against vulnerabilities and cyber attacks.
CNAPP solutions offer targeted security for containerized and serverless environments, particularly for cloud-native apps and the infrastructure that supports them. It offers comprehensive tools to protect cloud workloads and applications from a variety of security risks, addressing challenges of microservices, serverless architectures, and containerized environments.
While CSPM, CIEM, and CWPP are crucial elements of total cloud security, CNAPP complements and extends security measures, making it a great option for businesses with workloads including cloud-native applications.
Key CNAPP features
- Provides complete protection and awareness of cloud environments, combining major cloud security tools for comprehensive cloud security.
- Analyzes cloud paths to find probable attack points.
- Protects against function-level vulnerabilities, API abuse, and data exposure risks to ensure the integrity and confidentiality of serverless environments.
- Enables the real-time detection and mitigation of sophisticated assaults and suspicious behavior by utilizing cutting-edge threat intelligence tools like behavioral analytics and machine learning algorithms.
- Automates compliance assessments and offers governance frameworks.
- Microservices-based architectures are protected from vulnerabilities and threats by end-to-end security, which includes encryption, identity and access management, and runtime protection.
- Offers seamless interaction with DevOps procedures, encouraging secure application development without slowing development time.
- Strong container security features continually monitor containers to find and fix threats and vulnerabilities. These capabilities include vulnerability scanning, security configuration management, and runtime protection.
CNAPP Benefits
- CNAPP goes beyond the individual focus of CSPM, CIEM, and CWPP to offer a holistic approach to security, particularly built for cloud-native applications.
- Compared to CSPM, CIEM, and CWPP, which may have a larger reach, CNAPP is purpose-built for cloud-native settings, making it more specialized and tailored for protecting cloud-native applications and workloads.
- Employs sophisticated threat intelligence techniques such as machine learning algorithms and behavioral analytics to provide real-time detection and mitigation of complex threats, going beyond CSPM, CIEM, and CWPP.
- Integrates smoothly with DevOps methods, ensuring security measures are incorporated from the start of the software development lifecycle.
- Offers increased visibility and governance capabilities tailored to the specific needs of cloud-native apps.
- Provides end-to-end security for microservices-based architectures and containerized and serverless applications, addressing particular security concerns in these contexts.
Limitations
- Administrators and security teams may need to receive training and become familiar with CNAPP tools in order to properly use and configure the platform’s full range of functionalities.
- Advanced threat intelligence features may require extra system resources and affect performance.
- Careful planning and integration with current systems and processes may be necessary when implementing CNAPP solutions in complex cloud-native settings.
- Limited coverage of additional workloads that are not cloud-native.
- Organizations should carefully evaluate their budget and security requirements since they can incur additional charges.
- The effectiveness of CNAPP systems against evolving threats heavily depends on routine upgrades and maintenance.
See the Best Cloud Native Application Protection Platforms (CNAPP)
Should You Use CSPM, CWPP, CIEM, or CNAPP?
Your unique requirements will determine which cloud security solutions are best for your environment. Each of these solutions address specific areas of cloud security and will fit certain use cases better than others.
- Use CSPM (Cloud Security Posture Management) when you want to have a solid security posture throughout your cloud architecture. CSPM assists in detecting configuration and compliance error in real-time, ensuring that your cloud environment adheres to security best practices. CSPM offers ongoing monitoring and automated testing to effectively reduce security concerns.
- Use CWPP (Cloud Workload Protection Platform) to safeguard specific cloud workloads and apps. CWPP focuses on runtime security and vulnerability management, offering a range of protection approaches such as vulnerability scanning, security configuration management, and file integrity monitoring. With these, each workload is shielded from evolving threats like malware, ransomware, and data breaches.
- Use CIEM (Cloud Infrastructure Entitlement Management) to manage cloud resource access and entitlements effectively. By enforcing the least privilege principle, CIEM solutions lower access risks and guarantee that users—both human and non-human—have adequate access to cloud resources. It offers compliance reporting for cloud infrastructures and assists enterprises in reducing the risk of data breaches brought on by excessive entitlements.
- Use CNAPP (Cloud Native Application Protection Platform) when protecting cloud-native apps and the containerized and serverless environments that go with them. CSPM, CWPP, and CIEM are just a few of the cloud security capabilities integrated within CNAPP to give an expansive view of cloud security. It provides customized security for cloud-native workloads and automates security controls to efficiently identify, prioritize, and address security issues.
Another Solution to Consider: CASB (Cloud Access Security Broker)
It’s worth noting that CASB (Cloud Access Security Brokers) is also a critical cloud security solution, as it focuses on gaining visibility and control over cloud services utilized by an organization while providing capabilities for threat detection, access control, and data protection. CASB tools also opened the door for an entirely different type of cloud security solution called SASE (Security Access Service Edge) that attempts to address security beyond the network perimeter. CASB is a user-based control, in contrast to CNAPP and its other infrastructure controls. CASB focuses on the protection of user access to the cloud and SaaS apps rather than an organization’s cloud-based applications and infrastructure. CASB solutions give businesses visibility and a certain amount of control over how employees use outside services.
CASB vs. CWPP
For people and devices accessing cloud applications, CASB focuses on protecting access to the cloud, providing visibility into that use, and enforcing security regulations and policies. By delivering runtime protection, vulnerability detection, and configuration management, CWPP focuses on safeguarding specific cloud-based workloads. While CWPP protects workloads from threats and vulnerabilities inside cloud settings, CASB assures data security throughout user cloud access and consumption. To fully address access control and workload protection, organizations should take into account both solutions when developing their cloud security strategy.
CASB vs. CSPM
While CSPM emphasizes detecting errors and compliance breaches in cloud infrastructures, CASB focuses on protecting cloud access and monitoring user behavior within cloud applications. Assuring data security during cloud access, CASB gives visibility into user actions and data movement, while CSPM aids in upholding a robust security posture and industry requirements. Organizations may improve their cloud security approach by concurrently covering access control and infrastructure protection with CASB and CSPM. CSPM has a stronger emphasis on infrastructure-level security, compliance, and configuration management, whereas CASB technologies are devoted to data-level security and user access restrictions.
CASB vs. CIEM
The main functions of CASB include monitoring user behavior and implementing security policies for cloud applications while ensuring data protection during cloud access. The least privilege approach is enforced by CIEM, which focuses on managing identities and access rights in public and multi-cloud systems in order to reduce the risk of data breaches. While CIEM controls access to cloud resources, CASB controls SaaS application access and secures data while it is in transit and at rest within cloud applications. Both user access and identity entitlements are addressed by integrating both systems.
CASB vs. CNAPP
While CASB has a focus on user access and data protection, CNAPP tackles the risks and vulnerabilities specific to cloud-native applications, strengthening the overall cloud environment. A thorough solution to cloud security that efficiently addresses access control and application protection is provided by combining CASB with CNAPP. To ensure data safety, CASB focuses on protecting cloud access and tracking user activity within cloud apps. To defend cloud-native applications and workloads, CNAPP offers a comprehensive view of cloud security threats and incorporates several cloud security capabilities, such as CSPM, CWPP, and CIEM. CASB and CNAPP would thus offer the greatest security together.
Featured PartnersFeatured Cybersecurity Software
eSecurity Planet may receive a commission from merchants for referrals from this website
Bottom Line: Improve Your Organization’s Cloud Security
As cloud environments have evolved and matured, cloud security tools have evolved along with them, giving organizations a range of choices for securing their cloud environments. To identify the best use of CSPM, CWPP, CIEM, and CNAPP for your cloud security strategy, evaluate your cloud infrastructure and applications along with your security and compliance requirements. Implementing well-targeted security strategy and defenses will help you properly protect your sensitive data and valuable assets in the cloud.




