Rainbow table attacks are an older but still effective tactic for threat actors targeting password database vulnerabilities.
Today’s advanced persistent threats might elect for more sophisticated methods like remote desktop protocol (RDP) attacks, but cryptanalytic attacks – the inspection of cryptographic systems for vulnerabilities – remain a legitimate concern in the landscape of cybersecurity threats.
Rainbow table attacks are an effective tactic for threat actors targeting password database vulnerabilities presenting inadequate privacy and security functionality. Practices like password salting and patching hash algorithms are crucial for combatting rainbow table attacks.
This article looks at rainbow table attacks, how rainbow tables work, best practices for defending against cryptanalytic attacks, and more.
Jump to:
- What are Cryptanalytic Attacks?
- What is a Rainbow Table?
- What is a Rainbow Table Attack?
- Defending Against Rainbow Table Attacks
- History of Rainbow Tables
- Are Rainbow Tables Still A Threat?
What are Cryptanalytic Attacks?
A cryptanalytic attack is one where unauthorized actors breach a cryptographic security system through exhaustive searches for information related to the encryption scheme. Cryptanalytic attacks target operating systems that purposely avoid storing passwords in plaintext – and, instead, store a cryptographic hash of the password.
Cryptanalysts or malicious actors can use basic information about the cryptographic scheme, plaintext, or ciphertext to decipher encrypted communications.
Cryptology: Cryptography vs Cryptanalysis
Cryptology is the computer science discipline concerning the secret storing and sharing of data. The development of cryptology has been critical to safeguarding data for government agencies, military units, companies, and today’s digital users. The study of codes divides into:
- Cryptography: the methodology and applications for encrypting data.
- Cryptanalysis: the processes and methods to break codes and decrypt messages.
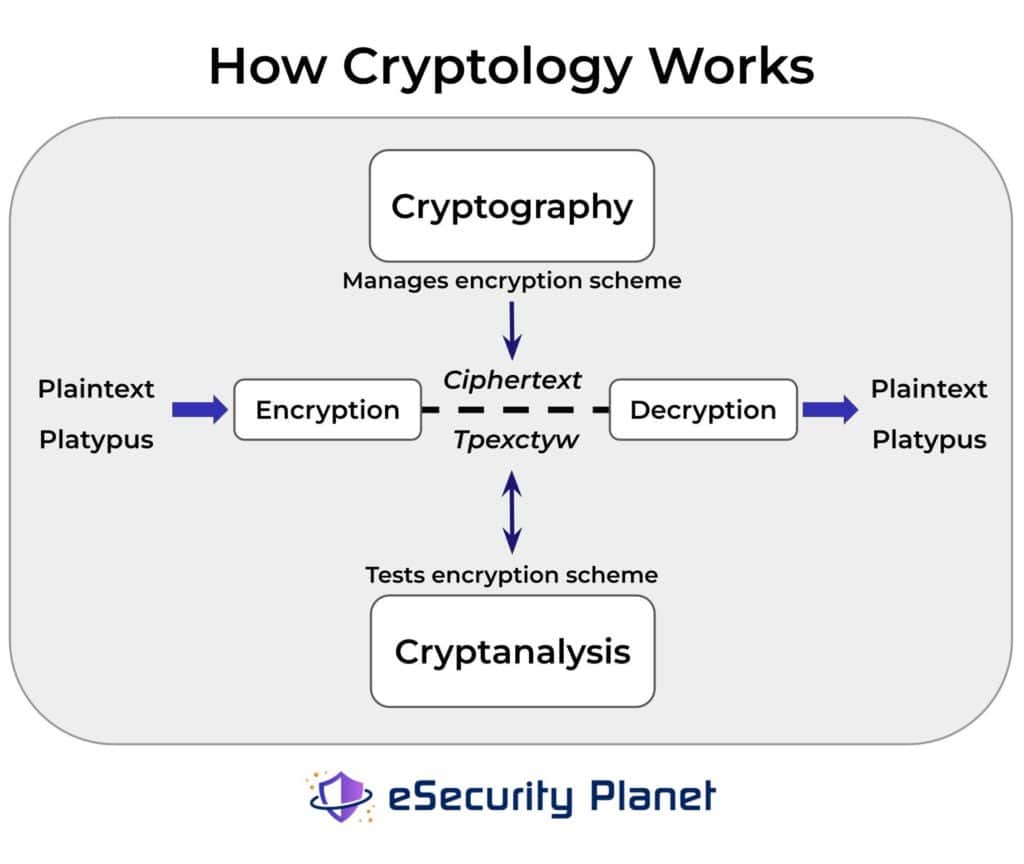
What are Cryptanalysts?
Cryptanalysts are commonly responsible for penetration testing cryptographic systems like deriving plaintext from the ciphertext. Enterprises often hire cryptanalysts to develop encryption algorithms (ciphers) and analyze cryptographic security systems.
Read more: Best Internet Security Suites & Software
Common Types of Cryptanalytic Attacks
| Type of Attack | Cryptanalyst Task |
| Ciphertext Only (COA) | Decrypt message(s) with no additional information |
| Known-Plaintext (KPA) | Find the encryption key with some information |
| Chosen Plaintext (CPA) | Evaluate encryption key with chosen plaintext inputs |
| Adaptive Chosen Plaintext (ACPA) | Evaluate encryption key with advanced CPA method |
| Chosen Ciphertext (CCA) | Evaluate encryption key with chosen ciphertext inputs |
| Meddler-in-the-Middle (MITM) | Manipulate encryption of a communication channel |
| Dictionary Attack | Test password files by encrypting dictionary words |
What is a Rainbow Table?
Rainbow tables are key-value tables of known hashes for a cryptographic security system. These pre-computed datasets allow a password-cracking actor to work backward from the ciphertext. Though this process can be time-consuming, the key-value table enables cryptanalysts and threat actors to execute a rainbow table attack.
What is a Rainbow Table Attack?
Rainbow table attacks expose cryptographic hash functions to breach authorized account access. Threat actors capable of obtaining an organization’s password database can use hash information for passwords to craft a rainbow table. From there, the rainbow table gives the hacker or cryptanalyst a map to decrypt password hashes.
Also read: Top Vulnerability Management Tools
Defending Against Rainbow Attacks
Moving Away from the Password
Multi-Factor Authentication
A critical feature offered by most services today for combatting password attacks is the ever-encouraged two-factor authentication (2FA) and multi-factor authentication (MFA). Going beyond just a password, 2FA and MFA add at least one more form of authentication and prevent standalone rainbow table attacks.
Passwordless Authentication
Passwordless authentication continues to be an important trend in the fight to secure the accounts of clients, personnel, and users at large. Examples of popular passwordless methods include:
- Biometric Authentication
- Email-Based Authentication
- Identity and Access Management (IAM)
- Single Sign-On (SSO)
Password Salting
Before a password takes on its hash form, a standard security hardening policy adds a unique string of characters to the plaintext password known as “salting.” These strings, or salts, are stored and known to the web application service provider and give accounts an additional layer of security beyond the user’s intended password.
Using the same salt across account passwords is better than no salting; however, using unique salts for each password provides even more robust security. This salting and hashing of passwords further complicates an actor’s effort to gain access.
Eyes on Hashing Algorithms
Cryptographic hashing algorithms are the mathematical processes transforming user input data into ciphertext, making the framework of choice an essential part of the password security formula. Examples of hashing algorithms like SHA, RSA, BLAKE, and MD offer cryptographers efficient and reliable computation where the same input will always receive the same output.
Though hashing algorithms are immune to reverse engineering, including rainbow table attacks, this is only the case with secure policies in place for password databases.
Read more: 1Password vs LastPass: Compare Top Password Managers
History of Rainbow Tables
Early Development by Hellman and Rivest
Cryptanalytic attacks required exhaustive compute power, and storing the complete search in memory wasn’t feasible before 1980. In 1976, Martin Hellman was a part of the computer science researchers breaking ground on public-key cryptography with the Diffie-Hellman-Merkle key exchange. Four years later, cryptographer Ron Rivest – the R in RSA – worked on a similar cryptanalytic method reducing time to breach through distinguished points and pre-calculated data stored in memory.
Oechslin’s Cryptanalytic Time-Memory Trade-Off
In 2003, Swiss computer scientist Phillppe Oechslin published Making a Faster Cryptanalytic Time-Memory Trade-Off, building off of Hellman and Rivest’s original application to develop what we know today as rainbow tables. Oechslin’s proposed method reduced the number of calculations needed during cryptanalysis by two, making rainbow tables an advanced form of time-memory trade-off methods and resulting in a swifter password cracking process.
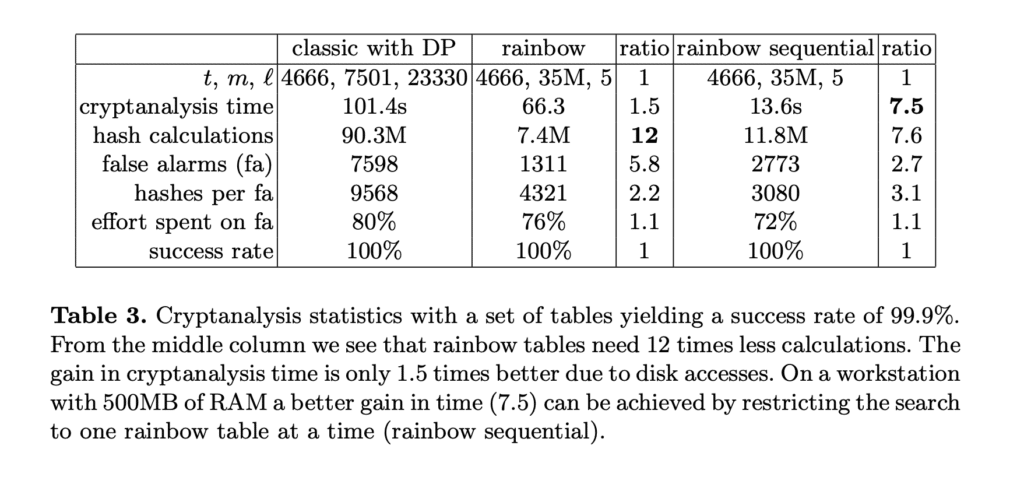
Are Rainbow Table Attacks Still A Threat?
Yes. Though attack tactics, techniques, and procedures (TTPs) evolve, rainbow attacks remain a threat to organizations failing to practice adequate password security. Security administrators must be aware of their cryptographic scheme to ensure continued data privacy.
Rainbow tables bring up the broader question about the future of cryptanalysis and cryptanalytic attacks from quantum computers. The development of post-quantum cryptographic algorithms is a significant development and crucial to securing future communications and data.
Also read: Cybersecurity Outlook 2022: Third-Party, Ransomware, and AI Attacks Will Get Worse




