About the only consensus on cybersecurity in 2022 is that things will get uglier, but in what ways? Third-party security, ransomware, artificial intelligence (AI) and decentralized finance (DeFi) are some of the threats you can expect to see more of this year – with the potential for far worse results than we’ve seen in the past.
Here are some of the more interesting predictions for 2022 we’ve seen from cybersecurity researchers. While many are dour, there are some optimistic views that suggest progress. The one thing they have in common is they’re thought-provoking and will prepare you for new challenges in 2022 and beyond.
Third-party Risks Take Center Stage
Third-party risks are at the forefront of security concerns, with identity risk management provider SecZetta predicting that “supply chain paranoia” will take over the cybersecurity world this year.
The software supply chain is at the heart of those concerns, as continuous integration and deployment (CI/CD) development methods create vulnerabilities exploited in attacks like those on SolarWinds and Kaseya.
One of the more interesting predictions comes from Moshe Zioni, vice president of security research for application risk management startup Apiiro, who says that software supply chain attacks will peak this year – and then begin to improve as better security measures are adopted.
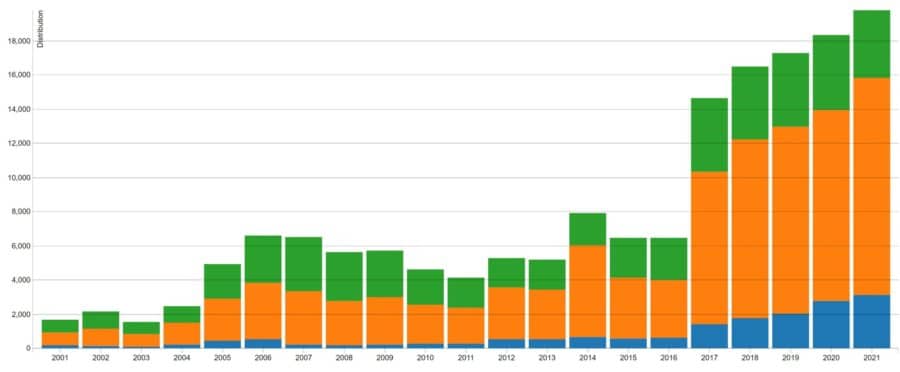
One possible data point in favor of that view comes from Pravin Madhani, CEO and cofounder of K2 Cyber Security, who notes that even though 2021 was the fifth straight record year for vulnerabilities recorded in the US-CERT Vulnerability Database, the number of high-severity vulnerabilities actually declined (image below).
Madhani said “it’s likely the lower numbers of high-severity vulnerabilities is due to better coding practices by developers. Many organizations have adopted ‘shift left’ in recent years, seeking to put more of an emphasis on ensuring security is a higher priority earlier on in the development process.”
Still, Madhani notes that the COVID-19 pandemic “has continued to push many organizations to rush getting their applications to production as part of their digital transformation and cloud journeys, meaning the code may have been through less QA cycles, and there may have been more use of third party, legacy, and open source code, another risk factor for more vulnerabilities. So while companies may be coding better, they’re not testing as much, or as thoroughly, hence more vulnerabilities made it to production.”
Also read: Best Third-Party Risk Management (TPRM) Tools
Ransomware and Critical Infrastructure Attacks Get Worse
After a number of high-profile attacks last year, ransomware certainly won’t be going away anytime soon. And Derek Manky, chief of Security Insights & Global Threat Alliances for Fortinet’s FortiGuard Labs, expects ransomware attacks to get even more destructive.
Ransomware has already been combined with distributed denial-of-service (DDoS) attacks, and Manky notes that ransomware could see the addition of wiper malware, “which could not only wreck data but destroy systems and hardware. … This could be a concern for emerging edge environments, critical infrastructure, and supply chains.”
SecurityScorecard CISO Mike Wilkes also noted the potential for malware and ransomware attacks to become much worse.
“As malware attacks increase, the likelihood of something going wrong inside of the malware code increases as well,” Wilkes said. “A near-future event could cause a massive depopulation of internet-connected devices. Or even worse, widespread corruption of medical devices. An attack like this could disable circuit boards with embedded operating systems and prevent them from having the ability to be reset. This is a possibility in 2022.”
As critical infrastructure becomes a more frequent target – a possibility as such capabilities get added to attack kits available on the dark web and Linux and the Edge increasingly become targets – the consequences could indeed become dire.
Fortinet notes that with the growing convergence of operational technology (OT) and IT at the network edge via remote access and IoT devices, “holding such systems and critical infrastructure for ransom will be lucrative but could also have dire consequences, including affecting the lives and safety of individuals. Because networks are increasingly interconnected, virtually any access point could be a target to gain entry to the IT network.”
Unpatched critical vulnerabilities will remain a top attack vector, as organizations remain slow to patch known vulnerabilities like the Apache Log4j flaws that surfaced last month.
See also: Best Backup Solutions for Ransomware Protection
AI Attacks Lead to Regulation
Expect to see increasingly sophisticated AI and machine learning-based attacks – and a growing regulatory response from governments around the world.
Michael Davis, Chief Architect at MDR and SASE vendor Open Systems, predicts that attackers will “embrace AI to evade detection,” using adversarial techniques and defensive responses to develop malware that can rewrite itself to evade security systems.
AI is already used by security tools to detect unusual behavior, and Fortinet expects cybercriminals to use deep fakes and AI to mimic human activities to enhance social engineering attacks and bypass secure forms of authentication such as voiceprints or facial recognition.
The growing use – and misuse – of AI will lead to new regulations, predicts Okera CEO Nick Halsey, who notes that the EU has already drafted AI regulations. Along with China’s new data privacy law, companies can expect scrutiny of data uses and protection to continue to grow.
HackerOne Hacker Dawn Isabel says white-hat hackers have important skills to bring to the AI debate.
“Hackers have a unique mix of technical skill and creativity that’s essential for finding workarounds to break systems,” Isabel says. “I expect as the ethical hacking industry matures, we’ll see the skill set of hackers also applied to other challenges we’re facing with technology. Disinformation, AI and ML, and data privacy are all areas where hackers could help identify problematic biases or weaknesses. … The creativity and global diversity of the hacker community makes them ideal for manipulating the decision paths of AI and ML systems and identifying problematic outputs from these systems.”
DeFi Security to Face Greater Scrutiny
As decentralized finance becomes more mainstream, so will efforts to secure it.
The role of cryptocurrency in ransomware payments is already facing scrutiny, but as business crypto payments become more commonplace, “there will be an increased emphasis on the security aspects of these new technologies,” says ReliaQuest Enterprise Architect Marcus Carey.
“CISOs and security teams will need to have an understanding of all of the facets of cryptocurrencies, including different blockchains like Ethereum and Solana, smart contracts, and hot and cold storage,” says Carey. “Just as cybersecurity teams audit code now, they will have to audit smart contracts… Cybersecurity teams and IT teams will need to manage hot wallets, which are used for transactions, and cold wallets, which are used for long-term storage. There are various aspects and implications that CISOs and their teams will need to understand in order to keep money secure. Cryptocurrency is the Wild West of the digital world today. Companies need to prepare now for the impact it will have in the year ahead.”
Also read: The State of Blockchain Applications in Cybersecurity
Measuring Cybersecurity Progress
The decentralized, distributed nature of modern enterprises, with its emphasis on the Edge, remote access, IoT devices and more, have security vendors discussing sophisticated new defenses like cybersecurity mesh and decentralized identity, but one industry official says a basic focus on risk and outcomes is lacking.
Ashok Sankar, ReliaQuest’s VP of Product & Solutions Marketing, cites a Ponemon study that found nearly two-thirds of organizations lack standardized metrics to measure the progress of their IT security risk management programs – and that lack of a well-defined security and risk management program is what makes their organization most vulnerable to attacks.
“In 2022, it’s expected that organizations will prioritize standardizing key security metrics and tracking them more effectively,” Sankar says. “We will see security leaders realize the value of these programs and shift to make these a top priority as we move into 2022.”
Also read: Best Risk Management Software
And a Worry for the Future: Quantum Cryptography
Not that IT security pros don’t have enough to worry about for 2022, but one firm is already looking ahead to the eventual threat posed by quantum computing.
Jennifer Fernick, global head of research at cybersecurity consulting firm NCC Group, says the race to build “arbitrarily scalable general-purpose quantum computers may dramatically shift the geopolitical balance of power through the decryption and thus data-collection abilities achievable through quantum cryptanalysis.”
Quantum computers will be capable of breaking (or, in the case of symmetric ciphers, significantly weakening) almost all widely-used cryptographic algorithms, she notes.
“While work to develop quantum-resistant cryptography is underway, global scientific and intelligence communities are racing to gain first-mover advantage, and we might not know when the first government cracks RSA2048,” she said. “Whoever gets there first will wield power in ways that cannot be overstated, but we can partially mitigate the impact by deploying high-quality implementations of well-cryptanalyzed quantum-safe cryptographic algorithms.”
Also read: Homomorphic Encryption Makes Real-World Gains, Pushed by Google, IBM, Microsoft








