Penetration testing is a powerful method for testing the posture of a security system. It shines a light on vulnerabilities that can lead to disastrous data breaches.
There are services that offer white-hat hackers who will simulate attacks. However, these services can be costly and typically only simulate some of the possible attacks. New vulnerabilities can arise at any time, meaning they may go unnoticed until the next time a white-hat hacker service is brought in. So how do you ensure vulnerabilities are discovered as they arise? A number of security tools can help make that process easier, including vulnerability management and breach and attack simulation (BAS).
About XM Cyber
XM Cyber is a security platform that continuously simulates attacks on an organization’s business-critical assets to discover new vulnerabilities as they arise, and provides prioritized remediation efforts. The platform instantaneously crawls an organization’s infrastructure, immediately identifying attack paths and the business-critical assets that are at risk. XM Cyber scans all assets on a network so it can identify vulnerabilities across multiple workloads and servers.
The tool was developed with the help of more than 30 cybersecurity researchers from the Israel Security Agency, the Mossad. They also recruited the help of the Israeli Intelligence Corps’ elite Unit 8200.
In 2020, XM Cyber received $17 million in series B funding with contributions from Macquarie Capital, Nasdaq Ventures, Our Innovation Fund and Swarth Group. XM Cyber is using that money to grow and enhance its Research and Development department. This latest series brings their total funding to $49 million.
Notable features
The notable features of XM Cyber are primarily focused on providing visibility into vulnerabilities and assisting in prioritizing which vulnerabilities security teams should try to resolve first.
Breach, attack and vulnerability management
The XM Cyber breach and attack feature continuously simulates attacks to identify vulnerabilities, including misconfigurations and human error, in a network. It offers context for these vulnerabilities by showing all the attack paths and the specific critical assets each path puts in jeopardy.
XM Cyber combines vulnerability scanning with patch management to further assist with remediation efforts. By offering context, it justifies where and why patches should be implemented. These simulations can run continuously without impacting a network or production environment so all business processes can carry on as usual.
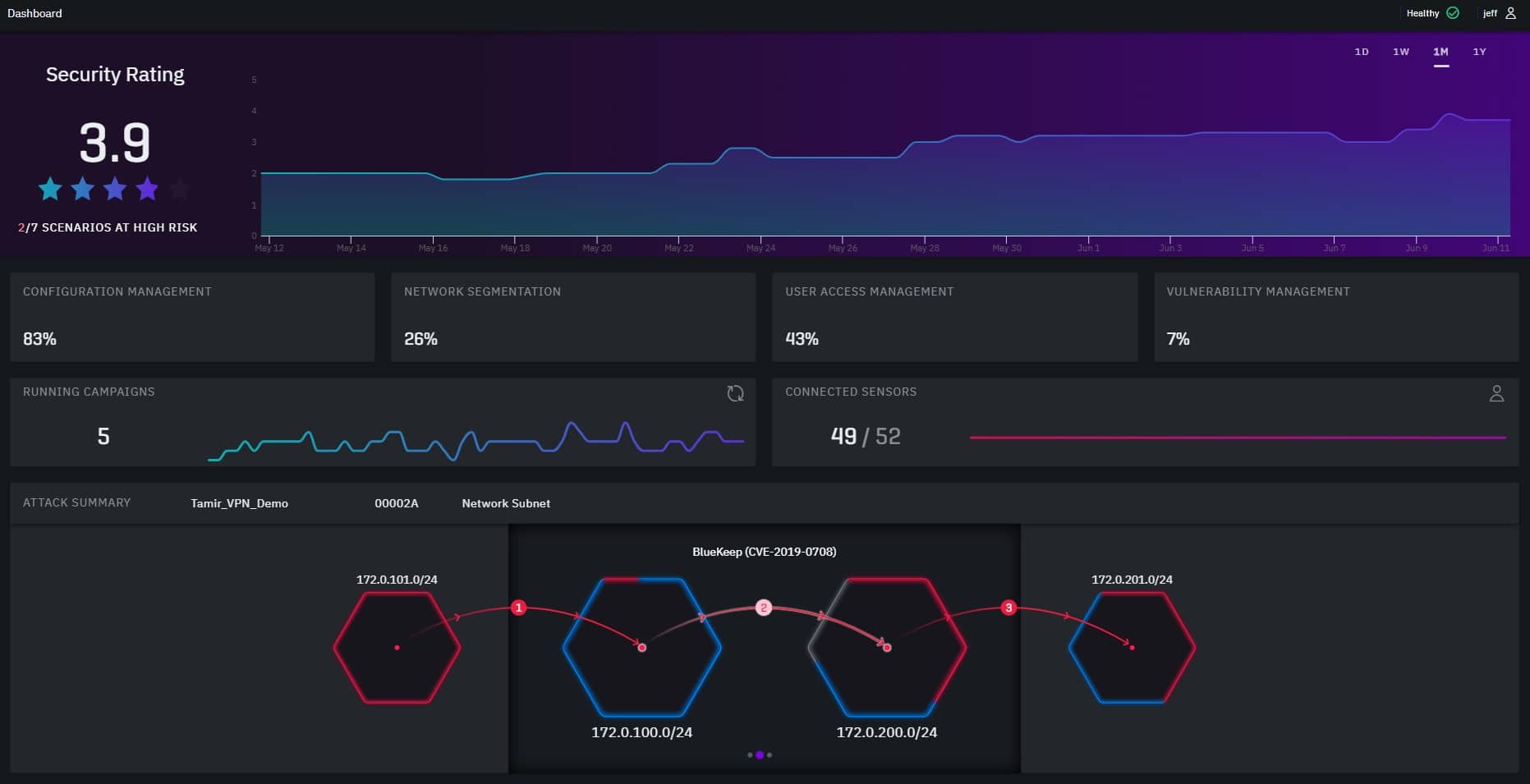
Image courtesy of XM Cyber
Security posture visibility
After vulnerabilities are identified, XM Cyber assesses the level of risk and prioritizes remediation based on several factors. The first is determining what are the most critical assets that are at risk. It also offers detailed information on each attack technique being used to determine how difficult each will be to execute for cybercriminals. XM Cyber uses these factors to assign a vulnerability risk score for prioritization. The platform then validates that each attack path has been eliminated with each continuous scan.
XM Cyber plans
XM Cyber does not disclose pricing for its platform on its website. Interested parties will need to contact the vendor for a custom quote. But they do offer a free trial and a number of demos for those who want to see it in action.




