Log monitoring is the process of analyzing log file data produced by applications, systems and devices to look for anomalous events that could signal cybersecurity, performance or other problems.
As just about every device and system produces logs, monitoring and analyzing log data is typically best done by a SIEM system, log management, or IT management tool. Log monitoring and threat intelligence are at the core of many cybersecurity tools, as they offer rich sources of data for the tools to use and learn from.
We’ll look at how log monitoring works, its benefits, challenges, best practices, security use cases, and some log monitoring and management tools to consider.
Also see our picks for the Top SIEM Systems
Importance of Log Monitoring for Security
Logs contain extensive documentation of system activity and are produced by a wide range of important software and systems, including databases, servers, network devices, endpoints, cloud environments, and security systems such as firewalls and intrusion prevention systems.
While logs are also used by developers and IT teams to address performance and operations issues, our focus is on the security uses of log data. Log monitoring is a fundamental aspect of network and cloud security, helping organizations protect against threats, maintain regulatory compliance, and respond effectively to security incidents.
- Access Control: Unauthorized access attempts can be identified and blocked, helping to ensure that only authorized users have access to key systems and data.
- Adaptation to Cloud Environments: Because cloud applications are remote and dynamic, robust log monitoring is a critical cloud security practice.
- Anomaly Detection: Unusual patterns or behaviors can be detected, helping to identify insider threats and advanced persistent threats.
- Compliance: Log monitoring ensures that firms follow industry norms and compliance standards, lowering the risk of legal and financial ramifications.
- Customer Loyalty and Trust: Effective log monitoring promotes an uninterrupted user experience, helping to ensure customer trust and loyalty.
- Data Leak Prevention: Log monitoring assists in identifying instances of data leakage, thus protecting sensitive information.
- Incident Response and Forensics: Logs provide vital information for incident response and post-incident investigations, assisting in understanding how security breaches happened and tracking their origins.
- Real-Time Threat Detection: Log monitoring detects possible threats and vulnerabilities in real-time, enabling organizations to respond quickly to security breaches.
How Log Monitoring Works
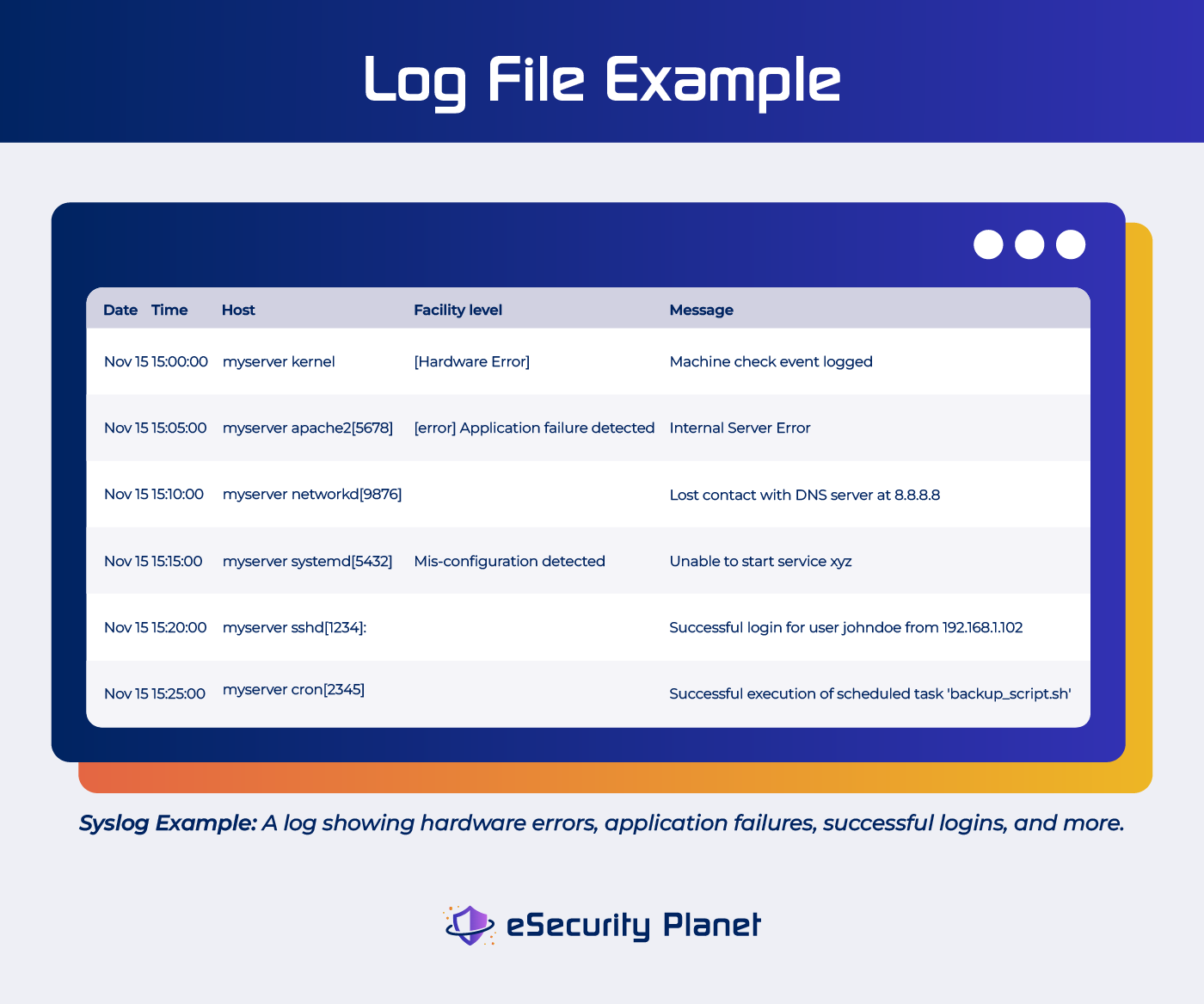
Log monitoring is the process of ingesting log files and parsing them for security and operational issues. Logs come in a range of formats like JSON, key value pairs, common event format (CEF) and CSV files, adding to the need for a monitoring tool that can make ingest a wide range of data sources and types.
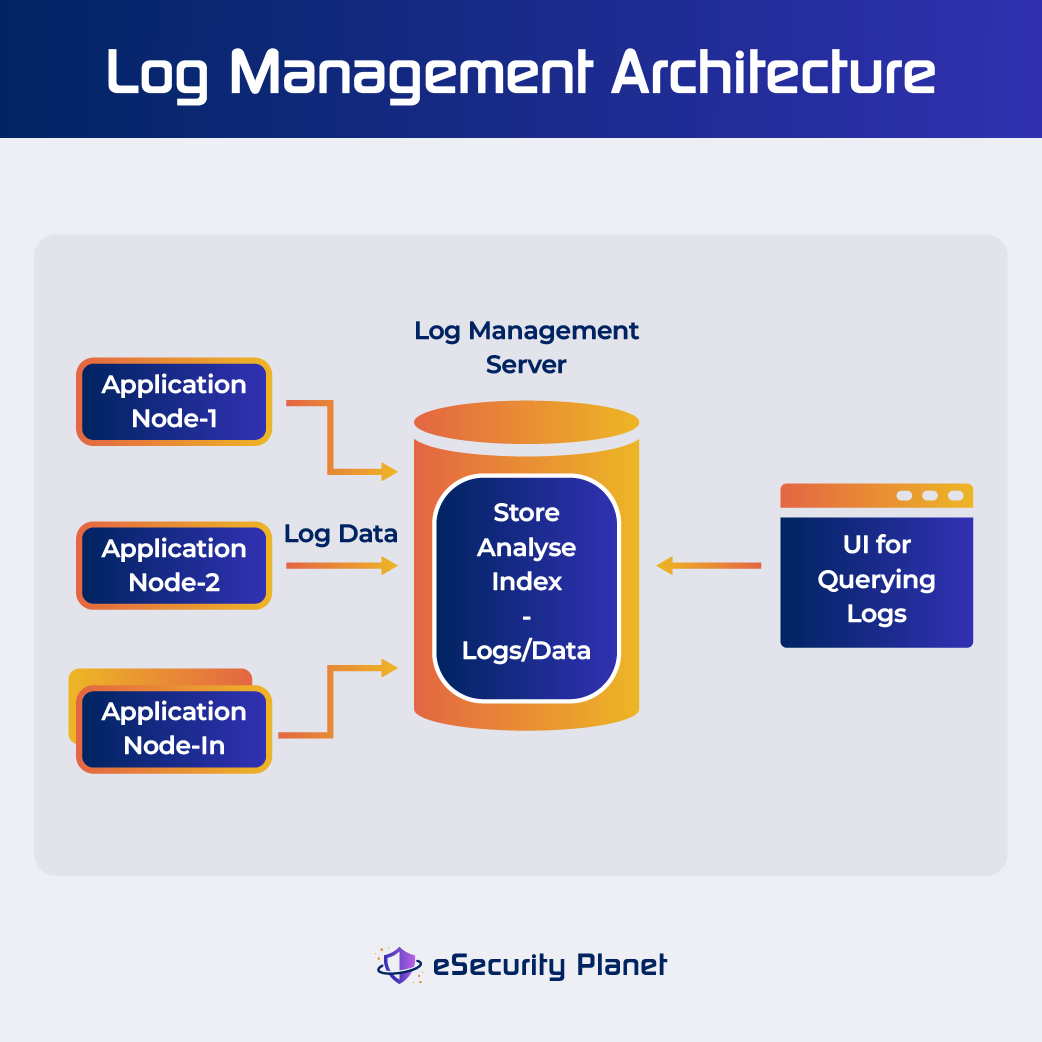
The log monitoring process typically involves the following steps:
Step 1: Data Collection
Applications, operating systems, and network devices all create log data on a network. These security logs document the events and actions, when they happened, and the causes of errors. Common types of log sources include:
- Endpoint logs are logs from devices such as PCs, laptops, and smartphones that aid in the monitoring of user activity, the detection of malware, and the adherence to business standards.
- Application logs assist in troubleshooting and monitoring activities such as database queries and illegal access attempts. App logs provide information on user and system activities by disclosing specifics such as resource access and user behaviors.
- Windows system logs, which include application, security, system, directory service, DNS server, and file replication service logs, give information on system activities and security incidents.
- Database logs record query execution and access data from applications and servers.
- System logs include information about user activity. These include operating system logs that keep track of user session data such as login times, commands executed, file access, and system processes; firewall logs that disclose approved or refused connections, as well as time and traffic information; and router logs that reflect route use and traffic flow.
- Cloud logs from services like AWS, Azure, and Google Cloud include logs from cloud infrastructure components such as virtual machines, storage, networking, databases, and identity and access management (IAM). Cloud logs offer visibility into cloud-related operations and security, as well as ensuring the security and compliance of cloud-hosted applications and data.
Step 2: Log Consolidation and Centralization
Log data is collected from several sources and consolidated into a log management system or repository. Centralization streamlines analysis and offers an extensive overview of system activity. SIEM tools can provide a consolidated picture of security by aggregating data from sources like firewalls, operating systems, intrusion detection systems, and user activity logs. Many SIEM vendors charge based on storage and volume, such as events per second, so some have turned to SIEM data lakes to lower costs.
Step 3: Data Parsing and Filtering
Structured information such as timestamps, event kinds, and user data are extracted from log entries. Filtering is then used to focus on log entries of interest and reduce noise.
Step 4: Real-Time Data Analysis
Log monitoring systems continually evaluate incoming log data in real time. They examine log entries according to established criteria or patterns in order to discover abnormalities, security risks, and other significant occurrences. When a log entry matches a rule (for example, a suspicious login attempt), an alert is created.
Step 5: Alert and Notification
When log monitoring tools discover possible issues, they generate warnings or notifications. These notifications can be delivered to security personnel, administrators, or a centralized monitoring system. Actions depend on the severity of the alert. Incident response methods are initiated to investigate and resolve the problem.
Step 6: Incident Response
An incident response team is dispatched in the case of a security issue or unusual activity. This team analyzes the problem, eliminates the threat, and seeks to minimize damage. Log data is essential for determining the extent and type of an event as well as pinpointing its origin.
Step 7: Forensics
Log data gives a complete historical record of events. Logs are utilized during post-incident investigations to recreate the sequence of events, establish the assault vector, and gather evidence. This data assists in learning from security events and fortifying defenses.
Step 8: Compliance Documentation
It is important for organizations to keep and analyze records for compliance considerations. Log monitoring tools can help create reports that indicate adherence to security and compliance requirements, lowering legal and financial risks.
7 Benefits of Log Monitoring
Log monitoring improves not just performance and security, but also operational efficiency and resource optimization. Some benefits include:
- A consolidated platform for developers to manage all system and application logs. The centralized approach simplifies processes by providing instant visibility without the need to analyze different systems, resulting in faster and more efficient responses.
- Security alerts. When security breaches, unauthorized access attempts or other anomalies are identified, log monitoring solutions provide alerts. These notifications enable immediate responses to events, mitigating potential threats.
- Rapid detection and response to threats and issues. Response time is critical for both end users and security. Risk can be mitigated by rapidly diagnosing and fixing breaches or vulnerabilities with the help of guidance from log monitoring tools.
- Automating the process of monitoring, alerting, and even fixing problems. This automation is extremely useful when log data volume increases, sparing busy teams a substantial amount of time. SOAR solutions are a more automated type of SIEM system.
- Enabling multi-purpose logs. Enterprises may utilize the same logs for observability and security operations with centralized log monitoring, simplifying processes and minimizing the need for separate solutions.
- Facilitating incident investigation. Log data is a crucial resource for investigating security events, allowing for a better knowledge of the type and breadth of security breaches.
- Ensuring compliance and auditing. Log monitoring helps businesses comply with regulations and standards, and can provide reports that confirm adherence to security requirements.
9 Challenges of Log Monitoring
While log monitoring performs a vital function in modern networks and systems, it is important to note that like any tool or approach, it has limitations and potential challenges that companies must anticipate. Addressing these challenges in log monitoring is essential to ensure efficient and effective log management, security, and compliance.
- Alert Fatigue: A high volume of alerts can overwhelm a security team, making it difficult to distinguish between severe threats and noise. Use intelligent alerting techniques to prioritize key warnings, reduce noise, and ensure timely reaction.
- Complexity: As technology advances, new systems and log formats emerge, increasing the complexity of log monitoring. Invest in log management solutions that provide log normalization and parsing in order to properly handle a variety of log types.
- Cost Management: To achieve security and compliance needs without spending too much, log monitoring tool costs must be carefully handled. Likewise, cloud service providers often charge to activate logging features, adding to that cost. To reduce operating costs, use log monitoring tools that offer scalable pricing structures and fine-grained control over log data processing and storage. Investigate SIEM data lakes too.
- Data Retention: Compliance with data retention standards mandated by numerous bodies is a difficult and time-consuming task. Use automated log retention strategies to ensure effective data management while adhering to regulatory standards. Read how one financial firm saved big by building its own SIEM system.
- Decentralized Data Repositories: Decentralized data systems increase costs and inefficiencies, requiring centralized data administration for optimization. Use lower-cost centralized log repositories wherever possible.
- Integration and Standardization: Merging logs from several sources and standardizing formats for unified analysis is critically important for log management success. Ensure consistent log analysis by using log management platforms that allow log aggregation, transformation, and standardization.
- Outdated Manual Approaches: Outdated and manual log monitoring methods compromise security, waste effort, and likely overlook key issues. Automate log monitoring methods to reduce security risks and save time.
- Performance Overhead: Comprehensive log monitoring can tax system resources, thereby compromising performance. Choose resource-efficient log monitoring systems that strike a compromise between thorough monitoring and system performance.
- Data Privacy Concerns: Logs can contain sensitive data and personally identifiable information (PII). To address privacy issues while managing sensitive log data, ensure that rigorous data protection procedures and anonymization techniques are in place.
What Are the Best Practices for Log Monitoring?
To fully optimize the value of log data, use best practices for effective log data capture, storage, analysis, anomaly detection, and rapid threat response.
- Determine the goals and outcomes you want to achieve with log monitoring to efficiently focus your efforts.
- Determine which log sources and data are critical to your goals and prioritize them to reduce noise.
- Add labels or unique IDs to log entries to improve troubleshooting and debugging. Labels facilitate sorting and filtering of log entries.
- Log data should be collected and stored in a single repository for simple access, analysis, and reporting.
- Use structured logging to work with log files for faster and more accurate log analysis.
- Use automation to reduce manual labor and reaction times by streamlining log collecting, processing, and alerting. A SIEM or SOAR solution can help you collect and analyze log data from various sources and make your network security process more efficient.
- Set performance and security baselines that will help in the detection of abnormalities and deviations.
- Review log data on a regular basis to discover anomalies, identify patterns, and maintain a proactive approach to system health and security.
- Set up notifications to warn you as soon as critical events or security breaches occur — but don’t make alerting so sensitive that your security team is overwhelmed by false positives.
- Define data retention standards to ensure compliance, and securely preserve important logs for future use.
- Use log correlation techniques to connect relevant log entries, assisting in the discovery of complicated issues and security concerns.
- Keep log monitoring tools and configurations updated to fully utilize the most recent features and security advancements.
Also read:
- Implementing and Managing Your SIEM Securely: A Checklist
- 5 Ways to Configure a SIEM for Accurate Threat Detection
Top 7 Security Use Cases of Log Monitoring
Risk assessment, regulatory demands, historical threat trends, resource allocation, and real-time threat information all play a role in determining the priority of these use cases. Ultimately, prioritizing these security use cases in line with your organization’s security objectives and risk tolerance improves overall security and incident response capabilities.
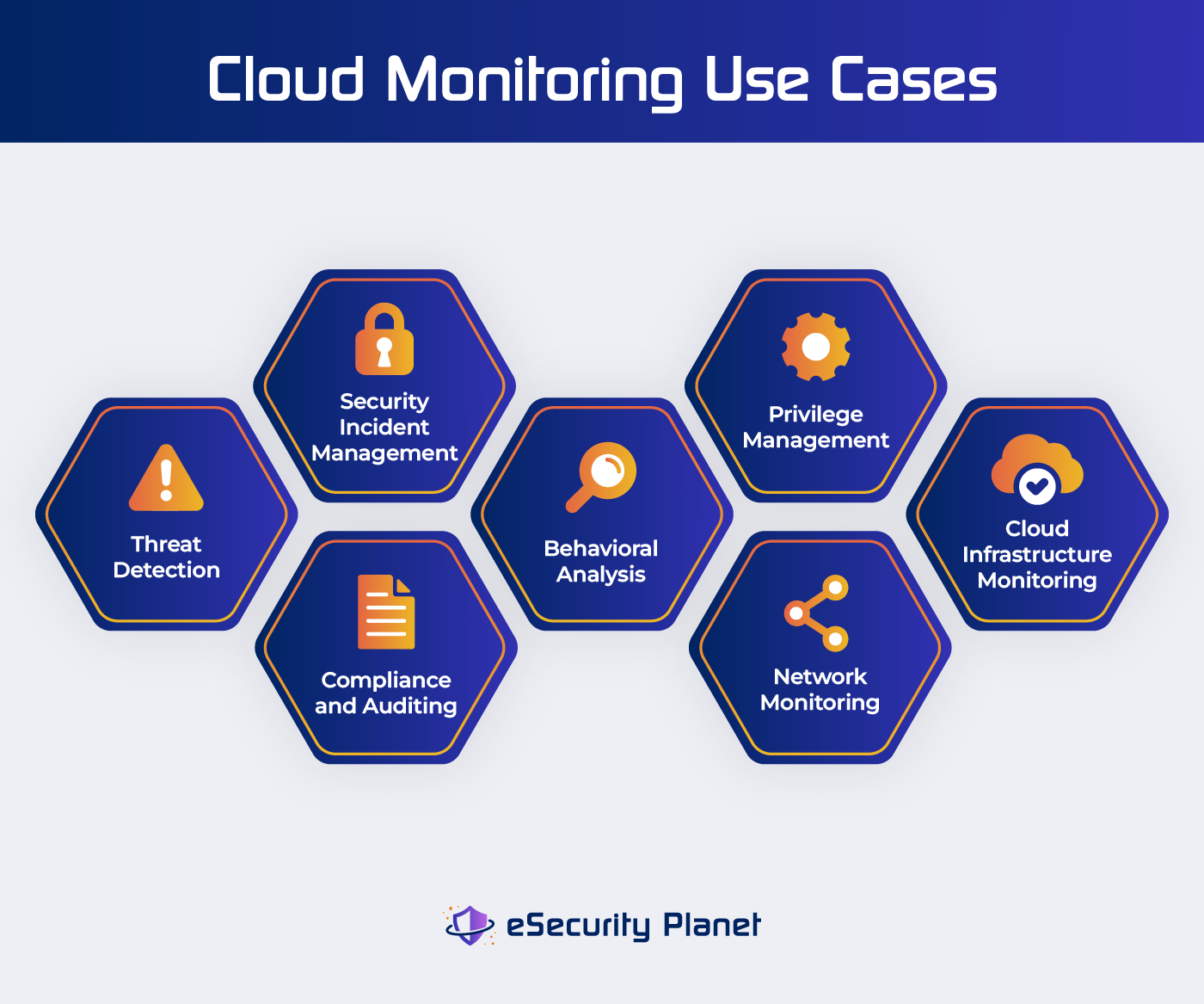
1. Threat Detection
To avoid breaches and cyber attacks, it is critical to identify and mitigate urgent security concerns. Security log monitoring continually searches for possible threat indicators such as established attack patterns, malware signatures, or anomalous network activity.
2. Security Incident Management
Security log monitoring supports the detection and management of security incidents like breaches, data leaks, and unwanted access attempts. It is critical to respond quickly in order to limit harm and comply with legal standards.
3. Compliance and Auditing
For businesses subject to legal and regulatory requirements, ensuring regulatory compliance and storing log data for auditing reasons is a top responsibility. Compliance-focused log monitoring guarantees that log data is saved and auditable for regulatory compliance.
4. Behavioral Analysis
Analyzing user and system behavior for anomalies, discovering unexpected patterns, and deviations from established baselines are another log monitoring benefit. This is particularly useful for identifying insider threats, advanced persistent threats, and undiscovered attack vectors.
5. Privilege Management
Tracking access rights and user behaviors can help detect unapproved privilege escalation and maintain proper access management controls.
6. Network Monitoring
Monitoring network device logs to ensure network security and performance is a critical responsibility for enterprises that rely on network infrastructure. Network monitoring can help detect network security risks such as intrusions, anomalous patterns, lateral movement, and performance issues.
7. Cloud Infrastructure Monitoring
Monitoring the availability, performance, and security of cloud infrastructure components, including containers, is a best practice for cloud security. The cost of enabling and monitoring cloud service provider logs is worth it.
Are There Tools to Help With Log Monitoring?
There are plenty of tools available to help you with log monitoring. Automation is a critical consideration for resolving issues quickly in complex, interconnected systems. SIEM includes tools like Security Event Management (SEM), Security Information Management (SIM), and Security Compliance Management. These tools collect and analyze data from a variety of sources in order to identify security risks, ensure regulatory compliance, and improve an organization’s security posture.
If you’re looking for a log monitoring or management solution that matches the unique demands of your organization, particularly in securely storing and analyzing logs and providing historical insights and correlation, here are some log management solutions to help get you started.

Sumo Logic
Sumo Logic is a log monitoring system that integrates logs, metrics, traces, SIEM, and business analytics into a single solution. Sumo Logic’s LogReduce Algorithm is notable for its ability to efficiently cluster and reduce comparable log messages. It not only streamlines log data but also improves log analytics by removing redundancy and focusing on the most important information.

Sematext
Sematext Logs is a cloud-based log management solution that specializes in centralized log management, structured visualization, real-time monitoring, and powerful alerting. It has the ability to configure alerts based on thresholds and abnormalities, with notifications routed to destinations such as Slack and PagerDuty, to help improve real-time incident response and proactive monitoring.

SolarWinds Loggly
SolarWinds Loggly is a cloud-based log monitoring solution that includes automatic data indexing, a powerful query language, and Live Tail for real-time log monitoring. It provides broad system visibility, allowing users to quickly discover trends or concerns in logs from numerous sources.
Bottom Line: Optimize Log Monitoring for Strong Security
Logs are some of the most useful information produced by IT environments, helping organizations fine-tune performance and security. Log monitoring tools like SIEM and SOAR offer immediate benefits like threat and anomaly detection and quick incident response. Organizations can use log data to obtain a more thorough understanding of their systems, determine areas for modification, and adjust their operations. The biggest challenge is choosing the tools and data settings that will help you meet your goals within your budget.
Read next:




