DNS security protects the domain name system (DNS) from attackers seeking to reroute traffic to malicious sites. Since a majority of business IT traffic now accesses or passes through the internet, DNS plays an increasingly important — and vulnerable — role.
This article will provide an overview of DNS Security, common attacks, and how to use DNS security to prevent DNS attacks and manipulation.
Featured PartnersFeatured Partners
eSecurity Planet may receive a commission from merchants for referrals from this website
Why DNS Security is Important
DNS security is important because all computers use DNS whenever they try to communicate with websites and applications hosted on the internet. DNS converts URL domain names, such as www.esecurityplanet.com, into a machine-understandable IP address, such as 146.75.93.91, that will be used by routers to actually make the connections.
The DNS protocol was designed for use within a firewall on a secure network, and by default will communicate in plain text. The DNS protocol is installed on servers and typically will store the most frequently requested sites — such as Google.com, Outlook.com, etc. — in the DNS cache for more efficient delivery of information to users.
A modern computing environment includes branch offices, remote workers, and mobile devices that must reach DNS servers from outside the firewall. This additional and unsecured traffic can cause traditional DNS servers to struggle to meet the security standards for any organization to prevent attacks.
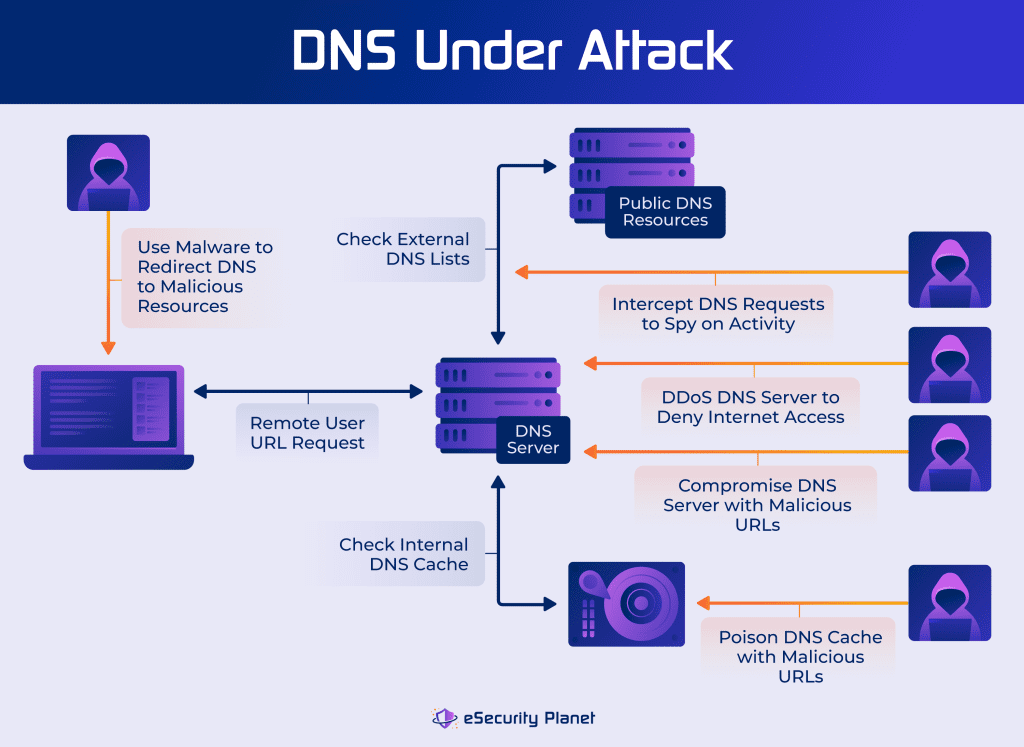
Hackers will attempt to compromise the DNS process by:
- Intercepting plain text DNS communication for espionage
- Poisoning the DNS cache with false information to redirect communications to malicious websites
- Compromising DNS servers to redirect traffic to malicious websites
- Denying DNS services through distributed denial of service (DDoS) attacks to halt communications
Without a functioning DNS solution, organizations will be unable to reach web-based resources or provide internet-based services to clients. Additionally, some attackers will use DNS disruptions to conceal more dangerous cyberattacks such as data theft, ransomware preparations, or inserting backdoors into other resources. To prevent a DNS attack, organizations need to secure their DNS processes for both local and remote users.
5 Common DNS Attacks
Hackers continuously probe discovered DNS systems because these systems will touch all users in a network. The most common DNS attacks include:
- DNS cache poisoning hacks a local DNS server to replace the IP addresses for legitimate sites in the cache with malicious IP addresses to be delivered to users for future DNS queries
- DNS domain lock-up DDoS attacks overwhelm legitimate DNS servers by abusing the DNS protocol with:
- Slow TCP connections = domain lock-up DDoS
- Overwhelming requests = flood DDoS
- Non-existent records = NXDOMAIN (no existence domain) DDoS
- Queries with spoofed IP addresses = reflection-amplification DDoS
- Non-existent URL subdomains = subdomain DDoS
- DNS hijacking redirects queries to a malicious DNS server by replacing information in the DNS record through malware, a compromised equipment (DNS server, router, etc.), or a compromised domain registrar account
- DNS spoofing impersonates a legitimate website to harvest credentials, infect visitors with malware, or other attacks; this attack often benefits from successfully conducted DNS poisoning attacks that redirect cached DNS queries to the DNS spoofed website
- DNS tunneling delivers malware to users, runs botnets such as DNS Beaconing, or exfiltrates data through trusted but compromised DNS communication on port 53 or through encrypted DNS queries over SSH, TCP, or HTTP protocols
For more information on DDoS protection, see our list of the top DDoS protection vendors and our guides to stopping and preventing DDoS attacks.
How DNS Security Works
DNS security protects against compromise through layers of security and filtering similar to the way next generation firewalls (NGFW) protect communication data flows. Typical security measures include:
- Communication channel encryption using DNS over TLS (DoT) or DNS over HTTPS (DoH) authenticated and encrypted communication
- DNS logging and log analysis to check for signs of compromise or malicious access and communication
- Hide main DNS servers from public or low-level security access and use secondary DNS servers to handle requests from end-users instead
- Protocol strengthening using the additional DNS Security Extension (DNSSEC) or DNSCrypt protocols to authenticate and encrypt DNS communication to known-good DNS resources
- Reputation filtering blocks or redirects DNS requests for known-malicious domains and IP addresses directly by using whitelisting/blacklisting or through recursive DNS services
- Server load protection reduces the effectiveness of DDoS attacks with typical server-strengthening techniques such as dedicated servers, load balancing, redundancy, and over-sizing capacity for the servers providing DNS services
- Traffic inspection for DNS no longer assumes the protocol is trusted and checks for malware and other malicious traffic within DNS inquiry traffic using NGFW or DNS firewalls
Using a strong mix of these DNS security solutions can provide additional security protection for the entire organization against malware, phishing, and botnets. Of these options, one of the most important is DNSSEC, which should be incorporated by organizations of all sizes.
What Are DNS Security Extensions (DNSSEC)?
Domain Name System Security Extension (DNSSEC) protocols authenticate DNS traffic by adding support for cryptographically signed responses. DNSSEC can be implemented without cost and will typically be the first step taken to improve DNS security. Most commercial DNS security solutions incorporate DNSSEC as a fundamental offering to all customers.
DNSSEC offers features and benefits that directly address major weaknesses in the DNS protocol, but can be easily confused with other DNS solutions since they are so similarly named. To help clarify DNSSEC, we will explore both the DNSSEC features and benefits and compare it against DNS Security, DNS Crypt, and Encrypted DNS.
DNSSEC Features & Benefits
When an unprotected DNS server makes a request to resolve a URL into an IP address, it sends out a request. When the answer is received, it can be difficult to determine the authenticity of the answer. DNSSEC adds data origin authentication and data integrity protection through the publishing of public encryption keys along with the IP address and URL directory.
The DNSSEC features include:
- Authenticated denial of existence (DoE) provides authoritative information to DNS resolvers — DNS servers responsible for translating domain names into IP addresses — that a domain does not exist so that requests for that domain can be resolved quickly
- Authenticated NODATA provides authoritative information to DNS resolvers that a domain exists, but that the requested data, such as an IPv6 address, does not exist for that domain
- DNS Zones publish public encryption keys to validate domains and addresses published by domain registrars in that zone
- DNS resolvers validate signatures for DNSSEC-signed domains to verify that the addresses are authentic and accurate
These features directly protect against:
- DNS cache poisoning, because delivered DNS results can be checked against the digital signature to check for authenticity
- DNS NXDOMAIN and subdomain DDoS attacks, because authenticated DoE and NODATA results can eliminate non-existent queries more efficiently
DNS Security vs. DNSSEC vs. DNSCrypt vs. Encrypted DNS
While DNSSEC provides powerful protection, it does not provide comprehensive security or protection. A DNS server or service enabling DNSSEC protocols alone still sends requests in plain text and remains vulnerable to other types of DNS attacks.
To understand how other DNS security components complement DNSSEC, let’s compare against the terms DNSCrypt, Encrypted DNS, and DNS Security:
- DNSSEC provides source authentication and integrity validation for DNS inquiries
- DNSCrypt uses elliptic-curve cryptography to provide open-source and free end-to-end encryption between servers and endpoints for DNS inquires
- Encrypted DNS uses authenticated and encrypted protocols for DNS inquiries through DNS over TLS (DoT) or DNS over HTTPS (DoH)
- DNS Security is a catch-all term that encompasses all methods used to protect DNS security from specific protocols (DNSSEC, DNSCrypt, etc.), encryption, methods used to improve DNS server security, and services purchased to protect DNS
Can You Prevent DNS Attacks?
DNS Attacks can be prevented or reduced in impact. Our article on How to Prevent DNS Attacks goes into more detail, but at a high level, different solutions will be more effective against certain types of DNS attacks and less effective against others.
For example, DNSSEC improves resistance against DNS cache poisoning, but does not address DNS tunneling or any of the DNS DDoS attacks. Similarly, a firewall that performs DNS packet inspection will directly address DNS tunneling and some DDoS attacks, but cannot protect against DNS cache poisoning.
As with all cybersecurity vulnerabilities, security is best improved through layers of defenses, improved protocols, and network security best practices such as regular patching, access management, and monitoring for attacks. Each IT environment is distinct, so the specific security that provides the best solutions for each organization may be different; however, all DNS attack prevention solutions should provide protection against DDoS attacks, DNS result verification, and DNS traffic monitoring.
3 Top DNS Security Solutions
In a practical sense, an organization can accomplish a lot by focusing effort on how to secure DNS on their existing DNS Server without big investments in services or tools. However, DNS plays such a critical role in our internet-dependent IT infrastructure that extra investments can dramatically reduce attack risks throughout the organization.
When selecting a security solution, the main points to consider are:
- Protecting the DNS process to protect against receiving compromised DNS information
- Protecting the DNS server to keep the integrity of the DNS data and mitigate against DNS DDoS attacks
- Protecting the DNS traffic against DNS tunneling attacks that use the DNS traffic as cover for other activities
The three top solutions directly address these issues:
- Recursive DNS Lookup Services (Google Public DNS, Quad9, etc.) enable integrity of the DNS process by providing authoritative and authenticated DNS sources.
- Cloud-based DNS Filtering and Security (Cisco Umbrella, Palo Alto DNS Security, NS1, etc.) protect the DNS process similar to lookup services, but also block known-malicious sources to help protect DNS traffic and isolate the DNS server against DDoS attacks.
- DNS Service with Proprietary DNS Servers (Google Cloud DNS, Cloudflare DNS, F5 Distributed Cloud DNS, etc.) outsource the entire DNS to a provider that provides global access and broad security for the DNS process, server, and traffic.
In addition to the dedicated DNS solutions above, DNS security will often be included as a feature in many other integrated security solutions such as next generation firewalls (NGFW), secure web gateways (SWG), Secure Service Edge (SSE), and Secure Access Service Edge (SASE). Some vendors even offer onsite tools to integrate DNS, dynamic host configuration protocol (DHCP), and IP address management (IPAM) into an integrated DDI solution for local and cloud-based servers to manage these fundamental network protocols.
Bottom Line: Pursue DNS Security Sooner Than Later
With so many options that suit a wide range of capabilities and budgets, organizations should take action to secure DNS servers and communications today. Attackers already seek vulnerable DNS solutions and abuse them on a daily basis.
A modest investment in time can improve basic DNS security, and more aggressive investments can dramatically reduce risk. After all, with most processes now touching the internet, a secure DNS solution can block threats beyond DNS processes and help secure email, endpoints, remote users, and more.
Read next: Network Protection: How to Secure a Network




