Spear phishing is a more targeted and effective phishing technique that attempts to exploit specific individuals or groups within an organization.
While phishing uses a broader range of tactics, such as mass emailing to random recipients, spear phishing is often well-researched and tailored to high-value targets. A typical spear phishing attack follows a familiar pattern of emails with attachments.
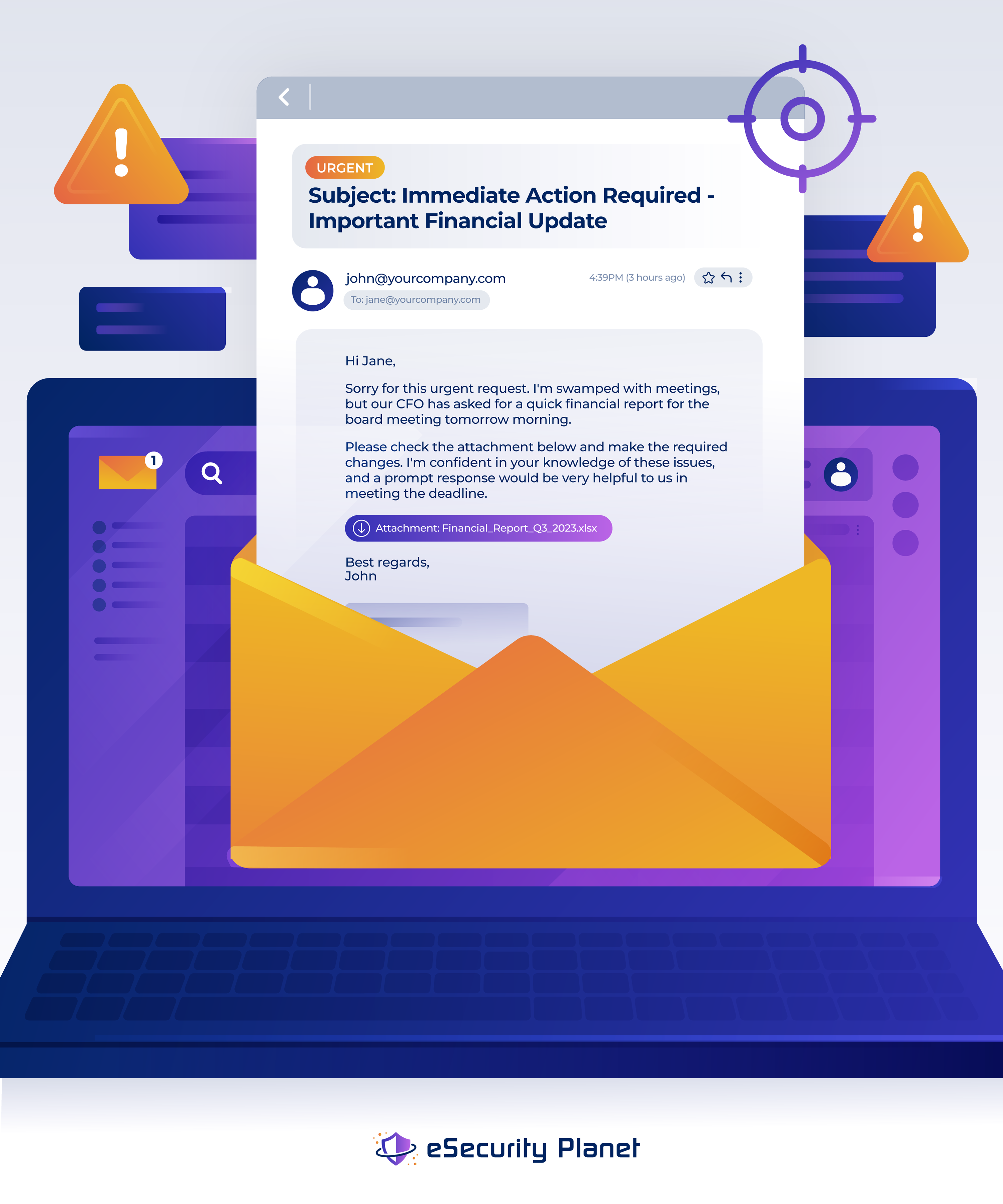
What sets spear phishing apart is the level of personalization included in the email content, catering to the recipient’s name, position, or rank within the company. This method involves using emails, social media, instant messaging, and other platforms to manipulate users into revealing personal information or performing actions that can lead to network compromise, data loss, or financial harm.
Spear phishing is a highly effective technique as it uses personalization, mind manipulation, and social engineering to exploit human vulnerabilities. Individuals and organizations should prioritize security awareness training, implement email security measures, and encourage vigilance when dealing with unusual or urgent requests.
How Spear Phishing Works
Spear phishing requires significant research on the part of the attacker for it to be successful.
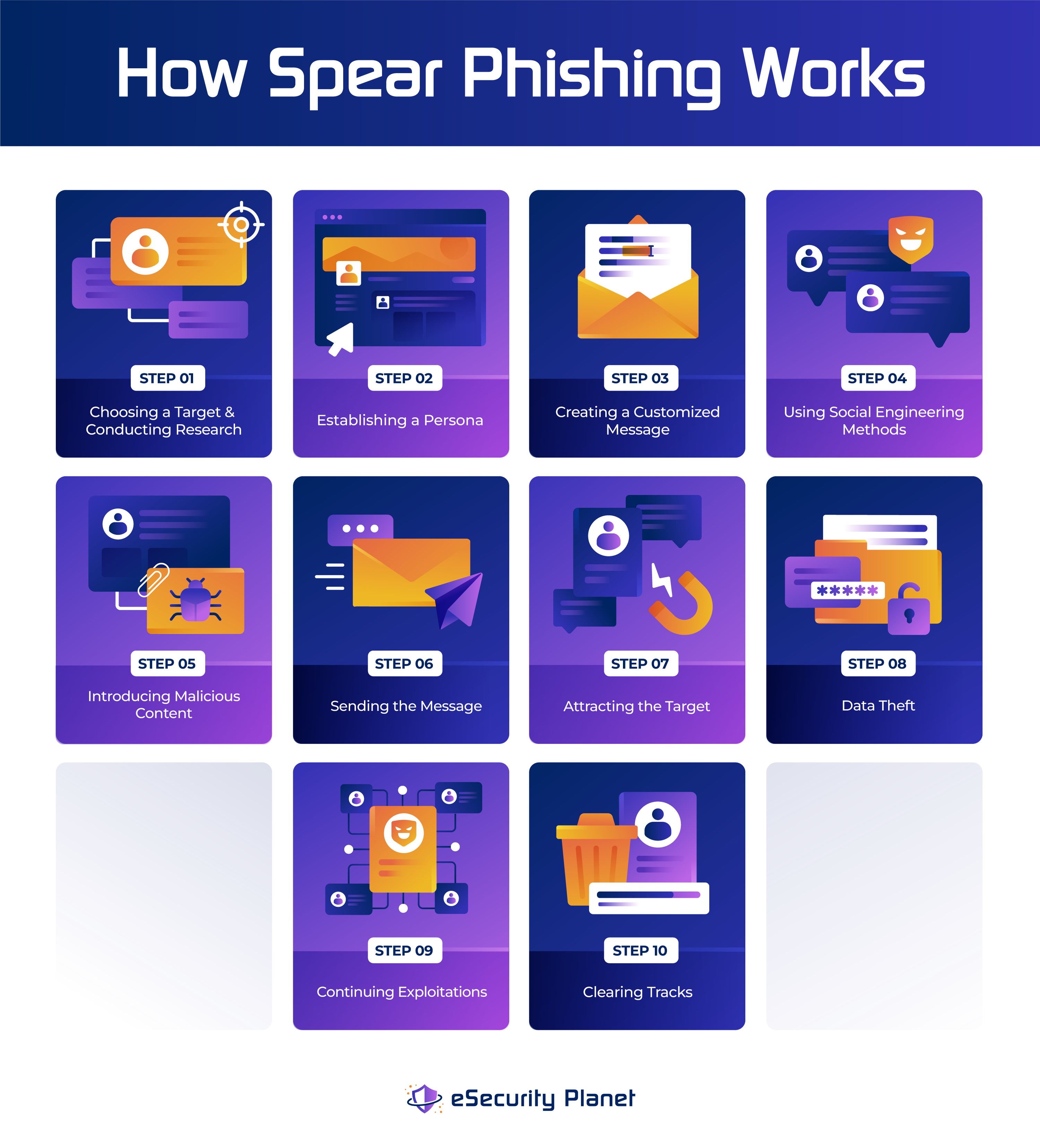
Choosing a Target and Conducting Research
The first step in spear phishing is to select specific individuals or groups as targets. High-ranking staff, people with access to sensitive information, or those involved in confidential projects are often targeted by attackers. Further research involves collecting personal information from sources like social media, company websites, and public records. These details allow attackers to assess their target’s roles, relationships, and behavior.
Establishing a Persona
An attacker will create a fake identity or persona on the basis of collected information that appears plausible to the target. This persona may be similar to that of a colleague, supervisor, business partner, or other trusted person. The aim is to establish a reputation and trust through personalization.
Creating a Customized Message
Attackers create an email or a message sent by the persona they have created. They may tailor their messages and emails to the interests of the target, his or her responsibilities, as well as current projects. The likelihood that the target will respond to a message is increased by this personalization.
Using Social Engineering Methods
Social engineering involves the manipulation of people’s psychology so that they respond in a specific way. The attackers may use emotions such as urgency, fear, curiosity, or trust to drive the target to take action in spear phishing. For the purpose of establishing connections, they may refer to past events, colleagues, and shared experiences.
Introducing Malicious Content
A malicious element (e.g., contaminated attachments, links to counterfeit websites, or instructions for performing activities that could pose a security risk) is commonly included in the message. The purpose of these elements is to attract the attention or confidence of the intended audience, leading them to become involved in the content.
Sending the Message
The attackers employ various methods to make it appear that the message is legitimate. In order to send a message, they could be using spoof email addresses, making use of compromised accounts, or exploiting weak security measures. This is done so the message will not require an initial inspection.
Attracting the Target
The message’s content, along with its social engineering tactics, aims to attract the attention of the target so that they can interact with these malicious messages. With this, the target is urged to take the necessary action through urgent appeals, attractive offers, or references to common interests.
Data Theft
The attackers could achieve their objective if the target falls for the ruse and engages in the malicious content. Downloading an attachment would, for example, infect the target device with a virus, which could enable hackers to gain access to confidential data, credentials, and networks.
Continuing Exploitations
When an attacker has initial access, they can exploit the organization in a variety of ways. This might entail moving laterally through a network, increasing their privilege level, and launching more widespread attacks, which could result in further damage.
Clearing Tracks
Advanced attackers can also take steps to erase traces of their activities, which makes it more difficult for cybersecurity experts to identify and respond to a breach. It may include deleting records, blocking their activities, or hiding their presence so as to maintain access.
10 Spear Phishing Prevention Techniques
Organizations can significantly reduce their susceptibility to attacks from spear phishing and improve overall cybersecurity resilience by combining these strategies with the promotion of a culture of security consciousness.
1. Email Authentication and Security Methods
Organizations can combat spear phishing through email authentication protocols and security strategies. These methods can improve email security, reduce the risk of successful spear phishing attacks, and increase overall email deliverability.
Sender Policy Framework (SPF)
SPF is an authentication protocol that allows domain owners to specify the IP addresses they are allowed to send on their behalf. The recipient email server checks the SPF record of the sender’s domain when receiving an email to verify that the sending server is authorized to send a message on this domain. The email can be reported as suspicious or denied if the IP address of the sender is not entered in the SPF record.
DomainKeys Identified Mail (DKIM)
DKIM is a digital signature authentication method used to verify that an email’s sender and content are authentic. This entails the use of your recipient’s private key to insert a Digital Signature into an email header. In order to verify the signature, the recipient’s email server will then use the sender’s publicly available key that is provided in DNS records for this domain. The email shall be treated as genuine unless the signature is invalid and the content has not been modified.
Domain-Based Message Authentication, Reporting, and Conformance (DMARC)
DMARC is a policy email authentication protocol derived from SPF and DKIM. In case an incoming email is not authenticated with SPF or DKIM, the domain owner will be able to determine what actions need to be taken. For the purposes of checking, quarantining, or rejecting suspicious emails, organizations may set up DMARC policies. DMARC shall also provide reporting tools to enable domain owners to identify the use of their email domains and whether they are being exploited for unauthorized or malicious purposes.
Secure Email Gateway (SEG)
The deployment of specialized email security solutions that actively scan incoming and outgoing emails for potential threats is part of the implementation of a secure email gateway against spear phishing. In order to detect malicious attachments, links, and contents of emails, these gateways employ a combination of the signature-based technique with modern threat detection techniques. To identify patterns suggestive of spear phishing attacks (e.g., social engineering tactics and strange sender behaviors), they also use artificial intelligence algorithms. To reduce the risk of successful spear phishing attacks, SEGs may block, quarantine, or flag suspicious messages before they reach the recipient’s mailbox.
Endpoint Security
To prevent, identify, and respond to assaults, endpoint security solutions employ a variety of methods, including antivirus software, firewalls, intrusion detection systems, and behavior monitoring. Endpoint security tools like EDR typically include security software capable of detecting and blocking dangerous attachments, links, and downloads. Real-time scanning is used in these systems to detect and remove malware from emails and attachments before they reach the user’s device. Unusual patterns that may suggest spear phishing efforts, such as unexpected email forwarding or bulk dissemination, can be identified using behavior-based analysis. Through regular updates and fixes, endpoints are safeguarded against known vulnerabilities that attackers may exploit.
Secure Access Service Edge (SASE) Tools
SASE tools, also known as security service edge (SSE) solutions, utilize built-in security capabilities such as web filtering, URL analysis, threat intelligence, and identity-based access restrictions. SASE platforms can detect spear phishing attempts by analyzing incoming and outgoing network data, including email conversations. They can prevent access to harmful websites, detect suspicious URLs, and impose identity and context-based user authentication and authorization.
Multi-Factor Authentication (MFA)
MFA is a security solution that requires users to supply multiple levels of authentication before being granted access to a system or account. It provides an additional degree of security beyond just a login and password. MFA normally consists of a password, a physical device such as a smartphone, and biometric data such as a fingerprint.
When accessing critical systems, apps, or data, MFA requires users to submit extra authentication factors in addition to their passwords. Even if attackers get the user’s credentials through spear phishing or other ways, this stops them from gaining unauthorized access. For example, even if an attacker has a user’s password, access to the user’s physical device or biometric data is still required to complete the authentication.
2. Incident Response Plan
An efficient incident response strategy for spear phishing entails creating a well-structured framework to address and mitigate any breaches as quickly as possible. An incident response plan includes defining clear roles and responsibilities, establishing communication channels, establishing escalation protocols, and establishing incident severity classifications. It is also important to conduct tabletop exercises that simulate response scenarios, consistently update contact lists, set up forensic procedures for analyzing compromised emails, and maintain seamless collaboration between IT, security teams, legal, and communication departments. Organizations may efficiently contain, investigate, and recover from spear phishing attacks by implementing a thorough incident response strategy, reducing possible damage, and guaranteeing a prompt and coordinated response.
3. Phishing Simulation and Testing
Simulation and testing against spear phishing is an organized implementation of simulated spear phishing attempts that aims to evaluate and improve an organization’s resilience. This technique includes creating realistic spear phishing emails, modifying them to imitate the strategies of possible attackers, conducting controlled campaigns across several departments, monitoring employee responses and susceptibility, and providing rapid training and feedback depending on their actions.
4. Web Filtering and URL Analysis
Defending against spear phishing with web filtering and URL analysis entails implementing tools and technologies to monitor and manage users’ access to websites and online information. This involves the use of web filtering systems that scan URLs in real time and compare them to databases of known harmful websites and banned domains. Users can be protected from accessing malicious sites that could be utilized in spear phishing attacks by blocking suspicious or possibly hazardous URLs. Organizations may also use URL analysis services, which examine links inside emails and offer thorough information on the reputation and possible hazards of the destination site. By implementing these safeguards, companies may proactively protect their users from spear phishing attempts, which frequently feature links to bogus login pages or malware-infected sites.
5. Security Information and Event Management (SIEM)
SIEM is a centralized system that monitors, detects, and responds to security incidents across a network. In order to detect abnormalities, suspicious behaviors, and possible spear phishing attempts, SIEM collects and correlates data from numerous sources. Analyzing email traffic patterns, user activity, and system logs to detect anomalous email activities, illegal access attempts, or compromised accounts is part of this. SIEM tools create alarms, allowing for immediate response and investigation. SIEM boosts an organization’s capacity to identify and mitigate attacks by giving real-time information on possible spear phishing occurrences, hence increasing overall security posture.
6. Security Policies and Procedures
Implementing strong security policies and procedures to combat spear phishing requires the development of definitive standards for email and online activities. This involves defining appropriate email usage habits, enforcing password hygiene, describing processes for confirming sender identities, developing mechanisms for reporting suspicious emails, and prescribing measures to be performed if possible spear phishing efforts are encountered. Updating, along with clarifying these rules frequently and providing continuing security awareness training, helps individuals make calculated choices and develops a proactive security culture that actively combats the threat of tailored assaults.
7. User Access Control
User access control refers to the practice of limiting user rights to only the resources and data required for their specific jobs inside an organization, ideally following “zero trust” principles. User access control is used to protect against spear phishing attempts by allocating users the least amount of permission necessary for their activities, ensuring they do not have access to sensitive data or systems beyond their responsibilities. This minimizes the effect of a successful spear phishing assault by limiting the possible harm attackers might perform even if access is gained. Furthermore, mandating multi-factor authentication and demanding robust authentication methods for accessing vital systems increases user access control measures against unauthorized access made by spear phishing attempts.
8. Vendor and Third-Party Risk Management
To make sure that your partners’ and suppliers’ security procedures are in line with the organization’s, implement vendor and third-party risk management security policies against spear phishing. This includes evaluating the personnel training, incident response capabilities, and email security policies. Contracts should include sections addressing data protection and incident reporting, as well as security expectations and roles. The effectiveness of their cybersecurity measures, particularly their vulnerability to spear phishing assaults, should be regularly audited and evaluated. You reduce the possibility that attackers would use their vulnerabilities to spear phish your company by extending your security requirements to your vendors and third-party partners.
9. Employee Training and Awareness
In order to protect employees from spear phishing, organizations must implement thorough training strategies that provide employees with the knowledge and competencies they need to recognize and respond to risks in targeted emails. Training sessions should cover the anatomy of spear phishing assaults, the methods employed by attackers, identifying suspicious emails, confirming the sender’s legitimacy, handling links and attachments with caution, and swiftly reporting suspected occurrences. Organizations may greatly lower their risk of falling victim to these individualized cyberattacks by developing a culture of increased security awareness and enabling workers to serve as the first line of defense.
10. Regular Monitoring, Updates, and Patching
Implementing proactive ways to regularly examine email security controls, worker behavior, and new threat patterns is necessary for continuous spear phishing monitoring and evaluation. This entails routinely reviewing email security setups, running simulated spear phishing tests to determine employee vulnerability, looking for abnormalities in real-time email traffic patterns, keeping up with new phishing tactics, and adjusting defensive measures as necessary. Organizations may quickly discover weaknesses and strengthen their resilience against targeted spear phishing assaults by maintaining an ongoing cycle of assessment, detection, response, and improvement.
It is crucial to come up with a systematic strategy for managing the security of software, operating systems, and applications. Keep up with the most recent security patches and updates made available by software vendors, thoroughly test updates prior to deployment, prioritize critical flaws, create a dependable patch deployment schedule, and utilize automated tools for effective patch distribution.
What Do Spear Phishing Attackers Look For?
Attackers can now easily create very convincing and individualized communications to entice targets into doing actions that undermine security or divulge private information. To reduce the likelihood of successful spear phishing attacks, businesses should be diligent in protecting the data of their employees and raising security awareness. Here’s what spear phishing attackers often do:
- Steal proprietary data, trade secrets, highly sensitive information, or intellectual property that can be used or sold.
- Imitate the target’s typical communication style and structure by analyzing email communication trends, which makes their emails look more trustworthy.
- Research the target’s name, position, responsibility, contact details, and relationships.
- Utilize colleague and professional relationship information to assume a well-known persona and build trust.
- Become aware of ongoing tasks, deadlines, and efforts to be able to write seemingly urgent emails.
- Use recent news, events, or announcements to persuade recipients and make your emails seem timely and relevant.
- Create convincing scam emails by using their knowledge of your financial transactions, bills, or payment procedures.
- Use known vulnerabilities in software, tools, or systems by becoming familiar with the organization’s technological environment.
- Create plausible situations by knowing the target’s physical location and travel intentions.
- Pose as coworkers, superiors, or business partners.
- Leverage security weaknesses, including weak passwords, out-of-date software, and a lack of staff security awareness.
- Use social media profiles to gather connections, hobbies, and personal and professional information to help create believable personas.
- Access employee directories to gather useful facts about positions, offices, and contacts.
- Increase the attack surface and send harmful emails to more people using the target’s contacts.
Identifying a Spear Phishing Attempt
The ability to spot a spear phishing effort demands vigilance and attentiveness. Here are some of the signs of spear phishing attempts and how you can identify them:
- Examine the sender’s email address for misspellings, subtle modifications, or domains that do not correspond to the actual organization.
- Be wary of emails that begin with generic salutations such as “Dear Customer” rather than addressing you by name.
- Be wary of communications that instill a sense of urgency, panic, or pressure, asking you to act immediately.
- Be cautious of requests for sensitive information, money transactions, or attachments from unfamiliar or unexpected sources. Verify any money or payment request, especially if it comes from an odd source.
- Poor spelling, syntax errors, or inappropriate phrasing can all be indicators of a bogus email, especially if it comes from a seemingly authoritative source.
- Hover over links to see their full URL. If the destination does not match, do not click.
- Examine attachments from unfamiliar sources with caution, especially if they ask you to activate macros or scripts.
- Legitimate companies will never request passwords, account information, or login credentials through email.
- Be wary of emails that promise huge prizes, lottery winners, or bargains that appear to be too good to be true.
- If the email does not reflect the sender’s communication style, this might be a red flag.
- Check for irregularities in the organization’s branding, logos, and formatting.
- Be wary of emails received from time zones or areas that do not correspond to the sender’s typical location.
- If the email covers messages unrelated to your function, initiatives, or duties, take caution.
If in doubt, contact the alleged sender via an alternative communication channel to confirm the message’s validity.
Bottom Line: Protect Yourself from Targeted Attacks
In today’s wide-open digital environment, spear phishing is a major threat to an organization’s security. To build your defenses against these targeted and deceptive assaults, it’s critical to maintain vigilance, keep educated, and implement good security measures. Understanding the techniques of spear phishing and its proper defenses allows individuals and organizations to recognize the telling signs of these targeted and manipulative attacks. Armed with this knowledge, you may take preventive measures to limit potential risks and avoid falling victim to these sophisticated attack methods.
Read more: What is Network Security? Definition, Threats & Protections








