Critical infrastructure security has moved to the forefront of cybersecurity concerns amid the Russian invasion of Ukraine – and in at least one case has led to some pretty unique cybersecurity advice.
Despite Russia and the U.S. trading cyber threats – and one disputed NBC News report that outlined possible options presented to U.S. President Joe Biden for “massive cyberattacks” aimed at disrupting the Russian invasion – initial reports of cyber attacks have in some cases been destructive and damaging, but not anywhere near anyone’s worst-case fears of utility system attacks, for example.
A SANS webcast today outlined some of the cyber attacks seen in the conflict so far. Kevin Holvoet of the Centre for Cybersecurity Belgium (CCB) said Russian-sponsored attacks in recent months against Ukraine and other targets have included:
- DDoS attacks on government, military, finance and communications
- Wiper malware, including the latest HermeticWiper identified by ESET and Symantec
- Espionage, which has included targeting U.S. defense firms, and Palo Alto Networks reported the new “SockDetour” threat yesterday
- Defacement of websites
- A software supply chain attack (Kitsoft)
- Influence and disinformation operations
U.S. and UK cyber agencies this week also reported a new network device threat called Cyclops Blink from the Russia-connected Sandworm group.
While the worst fears have so far gone unrealized, Tim Conway, technical director of ICS and SCADA programs at SANS, said the worst outcome from a critical infrastructure cyber attack would be long-term crippling damage.
“The worst thing that could happen is not an outage,” Conway said. “The worst thing that could happen is the system is kept up so it can be used to damage itself or damage load, and those are much longer-term issues that would take a much longer time to recover from.”
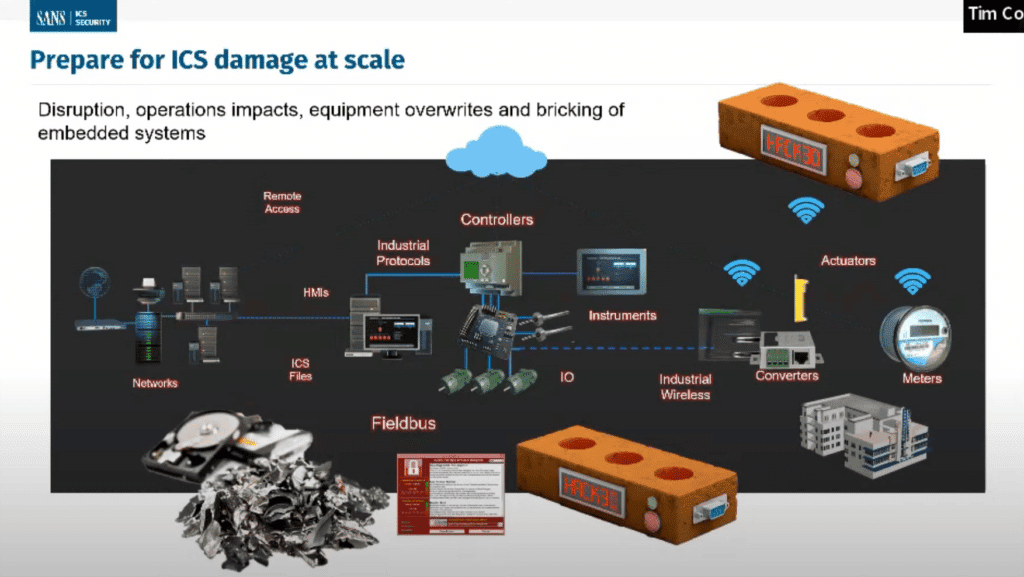
Protective Steps to Take
SANS Senior Instructor Jake Williams urged viewers to keep some perspective about the relative likelihood of experiencing a nation-state cyber attack.
“It is far more likely right now in most organizations that you will suffer an outage due to a self-inflicted injury responding to FUD (fear, uncertainty and doubt) than a Russian government cyber attack,” Williams said.
Williams urged viewers to focus on the basics, like phishing, passwords and patching/updating, as those are still the entry point of many attacks. He also recommended a number of additional protection steps:
- Tactical and effective logging strategies
- Outbound traffic control, including geoblocking
- Plan for rapid containment
- Implement application control
- Inventory B2B VPNs and block all high-risk protocols (see slide below)
- Implement NetFlow monitoring at all egress points
- Have contingency plans in place for disconnecting all B2B VPNs, especially high-risk ones
- Consider preventing the downloading of unknown drivers
Williams said viewers should follow the SANS Ukraine crisis web page for updates.

Also read: Top Vulnerability Management Tools
Security Measures to Take ‘Right Freaking Now’
SANS Principal Instructor Mick Douglas posted some advice on Twitter for security steps to take “right freaking now” that generated a lot of interest and will soon be the subject of a SANS blog.
Douglas said “tighter egress” – data leaving your network – is the one thing he’d focus on “right freaking now.”
“Watch your egress. Firewalls work both ways. Carefully monitor outbound traffic. DMZ servers RESPOND to external requests. Look for DMZ systems initiating outbound. This is what ‘phoning home’ [command and control, or C2] looks like.”
He said geo blocking isn’t as important a control. “Don’t get too hung up on IP address blocks. Geo blocking has some advantages, but the only time Russian groups come from Russian IP space is when they want to rub it in. Start treating the entire internet as hostile… because it is.”
See the Best Network Monitoring Tools
Whitelisting, ‘Living off the Land’ Controls
He urged users to implement whitelisting, or allowlisting, for apps. “App control (used to be called white listing) is no longer a ‘nice to have,’” he said, calling it “table stakes. Anyone who claims otherwise is giving dated & dangerous advice.”
He said an app control list doesn’t need to be hard. “Use native logging functions to know the apps that are running on systems,” he wrote.
If you don’t have an EDR system, he recommended Windows SRUM, which has a 30-day rolling view of every .exe file run. He shared links for single host and multiple host SRUM/ESE tools.
For monitoring normal application usage on Linux hosts, he said to use auditd or sysmon for Linux “if you don’t have a fancy EDR or something that can track this info.”
“You *must* know how your systems are being used for two reasons,” Douglas said.
The first is for blocking any app not on your accepted list. “[S]et block alerts at highest priority. It might be legit need, and you’ll want to fix that right away.”
The second reason is for “living off the land” (LOL) attacks, or using native functionality such as PowerShell to bypass security controls. “They are what state sponsored attackers use when pressured to do so,” he said. “They allow attackers to bypass your AV, and yes likely your EDR.”
“Because many orgs over rely on EDR and SIEM now, LOL attacks are highly successful. Attackers blend in. They are using core parts of the OS against you. None of your tools will stop these. You likely already have exclusions for the ports and protocols these tools use.
“Do NOT believe your heuristics or ML/AI based tool will save you either,” he said, recommending a talk by TrustedSec founder David Kennedy.
Note: Symantec last year added a “living off the land” protection feature to its EDR offering to turn off unused system tools.
Bypassing ‘Every Single Control’
Douglas said his small five-year-old company has bypassed “every single control” in a $17,000 lab with a three-node Proxmox cluster and a 14TB NAS system.
“I can emulate most orgs, or a significant portion of them,” he said. “If my boutique infosec consultancy has these resources…what does a state sponsored one have?”
Incident response plans should have raid host- and network-level isolation workflows based on his recommended controls. “Drill it,” he said. “You’re going to need to work at a speed you likely haven’t before.”
Security teams should increase logging while filtering out non-essential things and shortening the retention length for the data you don’t need long-term. “Many logs age like milk,” he said, adding, “looking at you DNS logs.”
“Once the attackers are in, you only need to detect them once,” he said. “You have the best CTI [cyber threat intelligence] at your fingertips. Leverage CTI feeds if you have them. Your hosts tell you how they’re being used and abused. Start listening.
“Prevent isn’t possible. Try anyway. Move to a detect and respond model. That’s our path to victory.”
‘It’s an awful choice, but if I only get one network change right now, I’m taking tighter egress’
One follower asked about “dropping bogons, route filtering, dropping unsolicited traffic right at the edge routers, IPv6 security measures, stateful firewalling to accept only established, related & intentionally exposed ports.”
Douglas said those are all things security pros should do, but he added: “This list is a triaged set of stuff an org should do *right freaking now* if they’ve not done so already. It’s an awful choice, but if I only get one network change right now… I’m taking tighter egress.”
Further reading: Best Incident Response Tools and Software




