Public cloud security refers to protections put in place to secure data and resources in cloud environments shared by multiple users or organizations.
Security responsibilities in public cloud environments are typically shared by the cloud services provider and customer under the shared responsibility model, with the cloud provider responsible for securing the cloud infrastructure and the customer responsible for access management, application connections and security, and the storage, transfer and backup of data used in the cloud.
Major cloud service providers have generally had good security, so cloud users can be pretty confident in the security of their data and applications if they get their part right. In this article, we’ll look at public cloud security, including how it works, who is responsible for securing what, relevant standards, security methods, common risks to consider, and how public cloud security differs from private cloud security.
Also read: 13 Cloud Security Best Practices & Tips
How Public Cloud Security Works
Organizations may greatly improve the security of their data and applications in the cloud by addressing six key aspects of public cloud security: data encryption, access control, firewalls and network security, security monitoring, and security patching and upgrades. These safeguards, when combined with adherence to security best practices and standards, establish a strong security architecture for public cloud environments.
Data Encryption
Public cloud providers implement strong encryption mechanisms to protect data at rest, and users should enable encryption for data in transit as well.
- Data encryption in transit guarantees that information stays private while being sent across networks. It keeps unauthorized parties from intercepting and accessing sensitive data while it is being sent. For this purpose, strong encryption methods such as AES-256 are often utilized.
- Data encryption for data at rest ensures the security of information stored in the cloud. Even if someone obtains access to the cloud server or storage devices, they will be unable to access the data until the encryption keys are provided. Cloud services often provide strong encryption technologies to protect stored data.
Access Control
- In the public cloud, access control entails determining who has access to which resources. Organizations may use IAM systems to design and enforce access controls. Permissions are assigned to users depending on their jobs and responsibilities. The concept of least privilege is observed, which means that users are only granted the minimal degree of access required to do their jobs.
- Authentication guarantees that users are who they say they are, typically through usernames and passwords or multi-factor authentication (MFA).
- Authorization governs what activities users are permitted to take after being authenticated.
Firewalls and Network Security
- Firewalls serve as a barrier between cloud resources and external networks in a public cloud environment. They filter incoming and outgoing network traffic, permitting or prohibiting it depending on established security criteria. Firewalls are used to safeguard cloud resources from unauthorized access and possible dangers like Distributed Denial of Service (DDoS) assaults.
- Virtual Private Clouds (VPCs), which are logically separate networks within the cloud environment, are frequently offered by public cloud operators. VPCs allow enterprises to segregate their cloud resources, which improves cloud network security by managing traffic flow between them and creating an extra degree of isolation.
Security Monitoring
- Continuous monitoring entails observing activity in the cloud in real time. Monitoring user logins, resource access, and traffic are all part of this. Security events and incidents are recorded and evaluated in order to discover and respond to potential security risks as soon as possible.
- Intrusion detection systems (IDS) can scan traffic for indications of suspicious or malicious activities.
- SIEM tools gather and correlate security data from a variety of sources to offer a comprehensive picture of security and enable quick reaction to security occurrences. SIEM can be fairly easy to use in the cloud, as cloud service providers offer logs that SIEM systems can ingest and analyze, typically at an added cost.
Security Patching and Updates
- The security of the underlying infrastructure, which includes servers, hypervisors, and networking equipment, is the responsibility of public cloud providers. Regular patching and upgrading of these components is required to address known vulnerabilities and guarantee the cloud environment’s security.
- While the infrastructure is managed by the cloud provider, users are responsible for keeping their virtual machines (VMs) and apps up to date. Failure to update virtual machines and programs might expose them to known security vulnerabilities.
Who Is Responsible for Securing the Public Cloud?
The cloud provider and the customer share responsibilities for public cloud security as follows:
- Cloud Provider: The provider is responsible for safeguarding the underlying infrastructure, providing physical security, and assuring service availability. Data center security, hardware maintenance, and network security are all included.
- Customer: It is the responsibility of the customer to secure their data and applications within the cloud environment. This includes establishing security settings, controlling access limits, and encrypting data.
Public Cloud Security Standards
Security standards and certifications are critical for ensuring that cloud providers maintain high levels of security, follow best practices, and give consumers transparency. Organizations should consider the provider’s compliance with these criteria as a critical consideration when selecting a public cloud provider to safeguard their data and maintain regulatory compliance.
To show their dedication to security, public cloud providers comply with numerous security standards and certifications, such as ISO 27001, SOC 2, and PCI DSS. These standards provide policies for data security, compliance, and risk management.
- ISO 27001 is a global standard that establishes and maintains an information security management system (ISMS) to safeguard data and assets in public cloud settings.
- SOC 2 (Service Organization Control 2) is a collection of criteria used to examine the security, availability, processing integrity, confidentiality, and privacy of data in public cloud services. It is frequently used to evaluate the security measures of cloud service providers.
- PCI DSS (Payment Card Industry Data Security Standard) is a set of security requirements that must be followed by businesses handling payment card data, particularly those employing public cloud environments, in order to secure sensitive cardholder information.
Public cloud providers align their security measures and processes with the criteria outlined in these standards. ISO 27001, for example, needs detailed risk assessments, whereas SOC 2 requires rigorous access restrictions and incident response processes. Third-party auditors audit and analyze providers to ensure they are in compliance with these criteria. Customers are frequently given access to the results of these audits, exhibiting openness and responsibility.
Compliance with these requirements is a continuous process. To keep their certifications, public cloud companies must constantly review and enhance their security policies. This guarantees that security continues to be a key focus. Compliance with established standards and certifications offers consumers confidence that their data and applications stored in the public cloud are being maintained in a secure and compliant way. It also makes regulatory compliance easier for customers in highly regulated sectors.
Benefits of Adopting Public Cloud Security Standards
- Compliance with industry standards lowers the risk of security breaches and data disclosure.
- Many firms are subject to industry-specific rules (e.g., healthcare, finance) that impose strict security standards. Using a compliant cloud provider can help regulated businesses streamline regulatory compliance processes.
- Customers can assess a cloud provider’s security measures before committing to their services by having access to audit reports and certification paperwork.
- Knowing that a cloud provider has met high security requirements gives enterprises peace of mind when committing their data to the cloud.
Public Cloud Security Best Practices
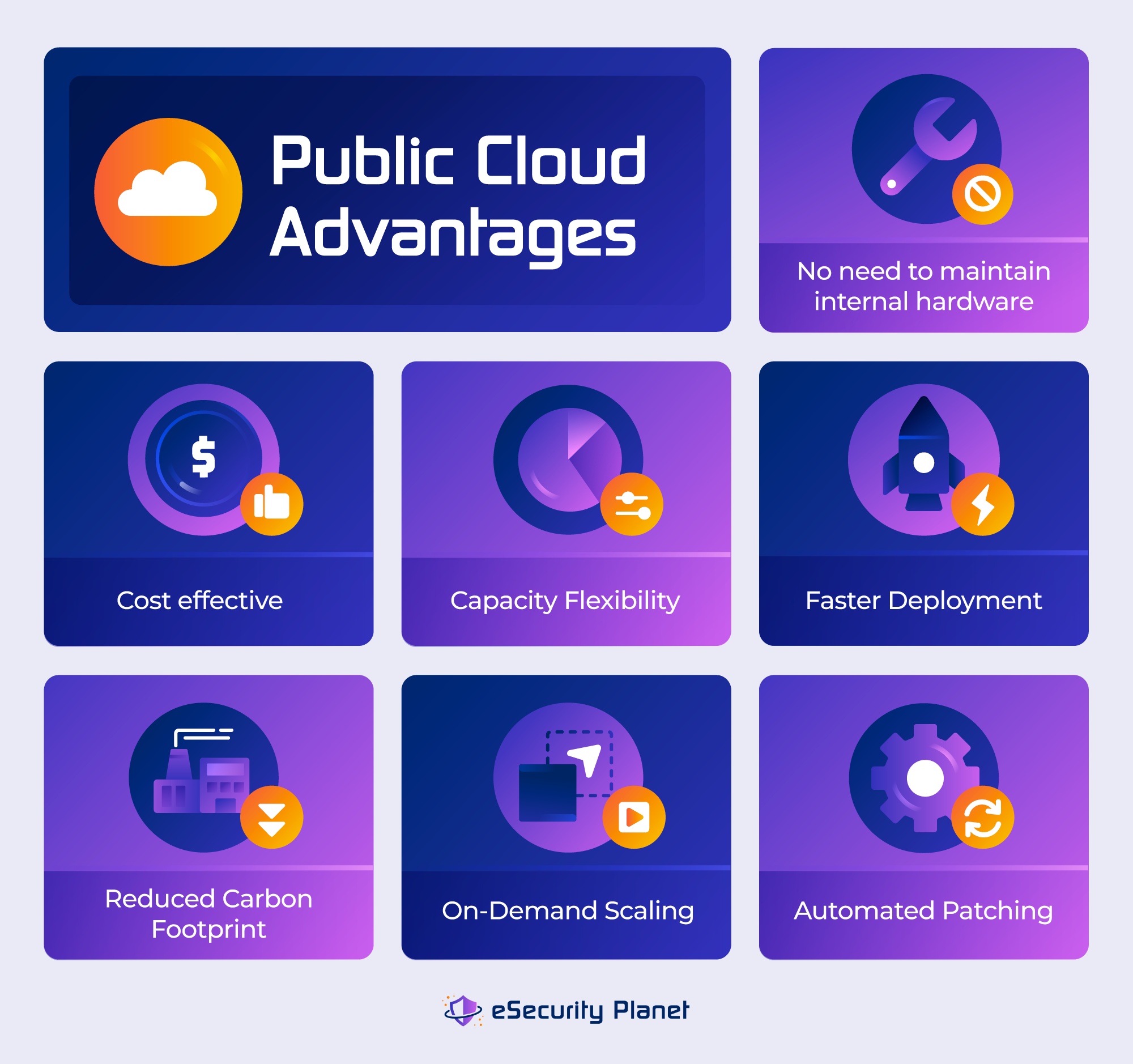
A cloud provider’s infrastructure hosts public cloud environments, often in data centers located across the world. Physical security measures, rigorous access restrictions, data isolation, shared infrastructure with logical separation, encryption, compliance adherence, and constant monitoring all contribute to the security of a public cloud environment.
To enhance security in a public cloud environment:
- Use strong authentication. Add an extra layer of protection to user logins by using multi-factor authentication (MFA).
- Update and patch on a regular basis. To guard against known vulnerabilities, keep all software and apps up to date.
- Monitor your cloud resources for suspicious behavior on a continuous basis and set up warnings for potential security breaches.
- Create and implement security rules and processes that regulate your organization’s cloud usage.
- Classify data and apply relevant security rules based on sensitivity.
- Educate staff on cloud security best practices and risks that may exist.
Cloud security tools have evolved greatly over the years. To learn more, read CSPM vs CWPP vs CIEM vs CNAPP: What’s the Difference?
Top 7 Public Cloud Security Risks
Here are seven of the top public cloud security risks — and steps you can take to prevent them.
1. Data Breaches
When unauthorized persons or entities get access to sensitive or secret data stored in the public cloud, a data breach occurs. This might include the theft or disclosure of sensitive data, such as client information, financial records, or intellectual property. Here are some techniques for dealing with data breaches:
- Encrypt data while it is in transit and at rest to prevent unauthorized access even if a breach happens.
- Strong access restrictions and user authentication techniques can help ensure that sensitive data is only accessed by authorized individuals.
- Continuously monitor and audit cloud resources in order to detect and respond to questionable activity as soon as possible.
- Data should be classified depending on its sensitivity, and extremely sensitive information should be subject to tougher security restrictions.
- An incident response strategy should be created to manage and reduce the effects of data breaches when they occur.
2. Inadequate Access Controls
Inadequate access controls entail improper permissions or user roles that offer persons or apps greater access than is necessary, possibly exposing data or allowing illegal actions. Some solutions include:
- Use least privilege to ensure that users and programs have only the access required to complete their responsibilities.
- Audit access restrictions on a regular basis to discover and remedy misconfigurations.
- Use identity and access management (IAM) systems to enforce consistent access rules.
- Train employees and users to understand and apply access control principles and policies.
3. Insecure APIs and Cloud Interfaces
Attackers can use insecure cloud interfaces and APIs to obtain unauthorized access to cloud resources, modify data, or launch attacks.
- Test APIs for vulnerabilities on a regular basis and follow security best practices.
- Use an API gateway, which serves as a security and monitoring layer for your APIs.
- Implement API rate limits and throttling to avoid API misuse.
- Authentication and access restrictions should be used to safeguard APIs and cloud management interfaces.
4. Account Hijacking
Account hijacking happens when an attacker gets unauthorized access to a user’s cloud account by stealing or guessing login credentials. Here’s how to avoid it:
- Make MFA mandatory to give an extra degree of protection to user accounts, and complex unique passwords should also be used.
- Educate users on the value of strong passwords and the dangers of phishing attempts.
- Monitor user accounts for suspicious behavior and unwanted access on a continuous basis.
5. Insufficient Logging and Monitoring
Insufficient logging and monitoring make detecting and responding to security events and anomalies in a timely way difficult. Here’s how to handle it:
- Use SIEM systems to consolidate and analyze security logs.
- Monitor network and system activities for abnormalities.
- Set up security incident notifications and automate responses where possible.
6. Distributed Denial of Service (DDoS) Attacks
DDoS attacks flood cloud services with traffic, making them inaccessible to genuine users. To prevent this, perform these steps:
- Use DDoS mitigation services offered by your cloud provider.
- Set up traffic filtering and rate limiting to prevent malicious traffic.
- Use a content delivery network (CDN) to disperse traffic and absorb DDoS assaults.
7. Data Loss
Data loss refers to the unintended deletion, corruption, or loss of data stored in the cloud. Here’s how you can avoid it:
- Backup data on a regular basis to avoid irreversible loss.
- Create data retention policies that govern how long data is stored.
- Use versioning features to recover from unintentional modifications or deletion.
- Use data loss prevention (DLP) tools and train staff to handle data with care and adhere to policies.
How is Security Handled Differently for Public and Private Cloud?
Public cloud security is based on a shared responsibility approach, in which the cloud provider is responsible for infrastructure security and the client is responsible for safeguarding their data and applications within the cloud. Public clouds provide scalability and flexibility, but they must be carefully configured.
Private cloud security, on the other hand, gives enterprises greater flexibility and customization, but at the expense of increased security responsibilities and perhaps higher expenses. The decision between public and private clouds should be based on an organization’s unique demands, risk tolerance, and compliance requirements.
| Aspect | Public Cloud Security | Private Cloud Security |
|---|---|---|
| Control | Control over the underlying infrastructure is limited, with more emphasis on safeguarding data and applications. | Greater command over the whole infrastructure stack. |
| Cost and Complexity | Pay-as-you-go pricing is generally cost-effective, but there may be hidden charges if not managed effectively. | Can be more costly due to the initial capital investment and continuing operational expenditures. |
| Data Protection | Data encryption and protection are managed by cloud providers, but consumers have to configure them appropriately. | Users have direct access to data encryption and security methods. |
| Infrastructure Maintenance | Cloud providers handle infrastructure maintenance. | Full responsibility for infrastructure maintenance. |
| Infrastructure Ownership | Cloud providers own and manage hardware. | The user or third-party provider owns and manages hardware. |
| Network Security | Cloud provider offers network security features and services. | Users are responsible for configuring and managing network security measures. |
| Physical Security | Cloud providers ensure physical security of data centers. | Users are responsible for physical security measures, including data center access control. |
| Regulatory Compliance | Compliance efforts may be influenced by the cloud provider’s certifications. | Allows for the implementation of certain security controls in order to fulfill regulatory standards. |
| Resource Isolation | Relies on the isolation methods of the cloud provider, plus extra customer setup. | Provides stronger isolation between different parts of the infrastructure. |
| Responsibility Model | Shared responsibility model with cloud provider handling infrastructure security. | Users are more responsible for security, including infrastructure. |
| Scalability and Flexibility | Scalability and flexibility are provided, allowing resources to be easily scaled up or down as needed. | Scalability in the private cloud environment is often restricted to the resources allocated. |
| Security Configuration | Security configurations need careful customer setup and configuration. | Security setups may be adjusted based on the demands of the company. |
| Security Updates and Patch Management | Cloud provider manages security patching for underlying infrastructure. | The user is responsible for installing security updates and patches. |
Bottom Line: Making Public Clouds Secure
Public cloud security is a dynamic and constantly evolving field that needs continuous attention and adaptability to new threats. Organizations may embrace the public cloud with confidence if they understand the notion of shared responsibility, apply security best practices, and keep up to date about emerging security requirements. As technology advances, so must our cloud security measures, ensuring that our digital assets are safeguarded in an ever-changing context.
Read next:




