A cloud-native application protection platform (CNAPP) is a comprehensive security solution to safeguard cloud-native applications (apps) and environments. We’ll explore the fundamental aspects of CNAPPs, understanding how they function, their core features, benefits, disadvantages, implementation strategies, and their popularity in the market.
How Do CNAPPs Work to Improve Cloud Security?
CNAPPs serve as enhanced security platforms designed to protect cloud environments against many kinds of attacks and vulnerabilities. They incorporate key cloud protections such as cloud security posture management (CSPM), cloud infrastructure entitlement management (CIEM), Infrastructure-as-Code (IAC) scanning, cloud service network security (CSNS), and cloud workload protection (CWPP) into one integrated solution.
Organizations that rely significantly on cloud-native apps and environments should consider installing a CNAPP solution. CNAPPs’ major purpose is to restrict and monitor cloud resource access, ensuring that only authorized users have access to sensitive data and applications.
CNAPPs handle the various issues of protecting containerized environments, from effective identity and access management systems to encryption, network segmentation, and real-time threat detection. These approaches work together to provide a complete security architecture that protects data, resources, and applications from a wide range of possible attacks. CNAPPs use various approaches to improve cloud security such as:
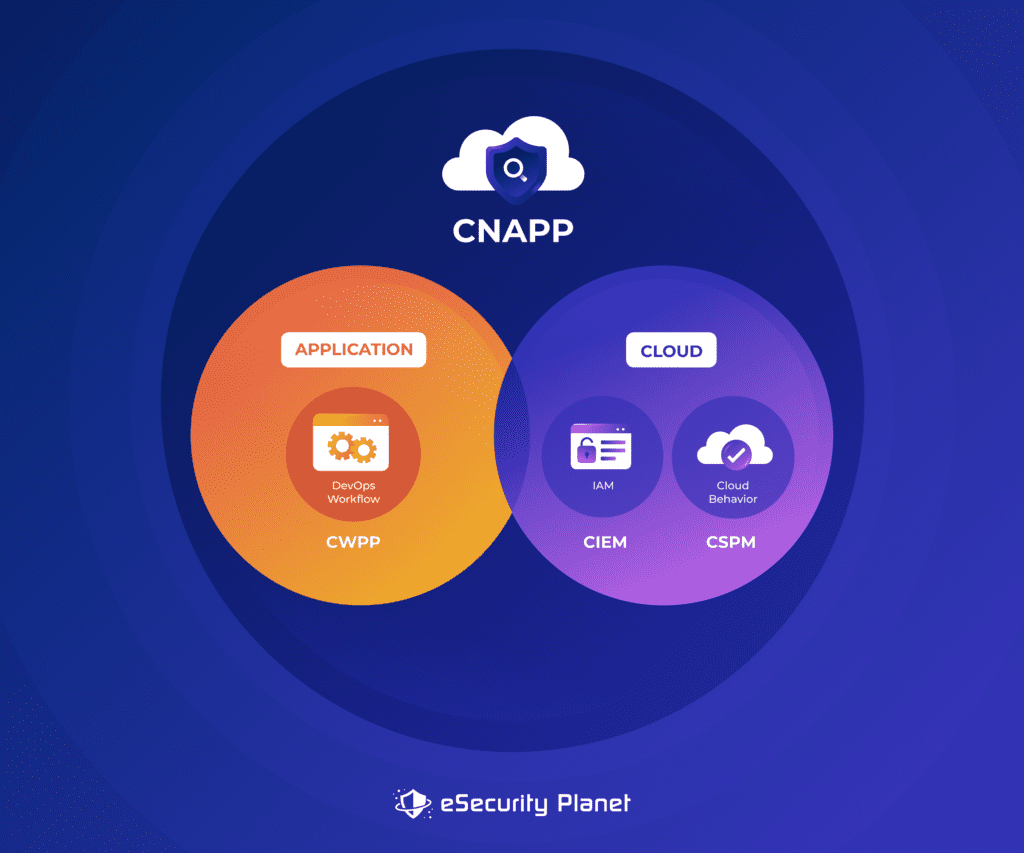
Identity and access management (IAM)
IAM systems play an essential part in any CNAPP. In a cloud environment, these systems control user identities, access rights, and roles. Strong IAM makes sure that only those with the proper authorization may access resources and carry out certain tasks. Multi-factor authentication (MFA) adds a higher degree of protection and requests additional proof of identification from users before giving access. While MFA focuses on extra layers of verification, single sign-on (SSO) technology simplifies login procedures while enabling the users to access several systems and apps using a single set of credentials. Thanks to SSO, users no longer need to memorize many sets of credentials and can enjoy a type of MFA access that ensures better security and user experience.
Encryption and data protection
Encryption is crucial for safeguarding sensitive data. Data is converted into an unreadable format both during transmission and while at rest, thanks to encryption methods. Unauthorized parties are prevented from understanding intercepted data by employing robust encryption algorithms and sound key management procedures. This protects data even if it is accessed by malicious parties, guaranteeing its secrecy and integrity.
Network segmentation and micro-segmentation
CNAPPs use network segmentation to partition cloud systems into several segments or zones. By isolating key resources and restricting lateral mobility within the environment, this strategy makes it difficult for attackers to move from one area to another. This idea is further developed by microsegmentation, which divides the network into increasingly smaller sections. The attack surface may be reduced and the potential consequence of a breach can be lessened by allowing each segment to have its own security measures.
Threat detection and response
Proactive security measures used by CNAPPs include tools for real-time threat identification and reaction. These systems use artificial intelligence and machine learning to analyze massive volumes of data and find patterns suggestive of possible risks. CNAPPs can quickly identify potentially dangerous actions by continually scanning for irregularities. Rapid risk mitigation is made possible by automated actions like isolating infected containers or sending alarms to security personnel.
Enforcement of security policy
To maintain a uniform and compliant security posture, CNAPPs create and implement security policies. Access restrictions, data processing, and communication protocols are only a few of the security measures covered by these policies. Security controls are uniformly implemented throughout the whole container environment thanks to automated policy enforcement. This lowers the possibility of a human mistake and guarantees that the environment complies with industry standards and internal security guidelines.
8 CNAPP Core Features
CNAPPs have evolved as vital assets for securing containerized environments. CNAPPs address the unique security challenges posed by the development of modern applications by providing features such as real-time protection, threat intelligence, automated remediation, and compliance assistance. As container adoption grows, investing in a robust CNAPP becomes critical for guaranteeing the security and integrity of applications in dynamic and ever-changing IT landscapes.
Here are the eight core features that make CNAPP an essential component of any successful security approach for containerized systems:
Container security and runtime protection
CNAPPs detect vulnerabilities, enforce safe setups, and provide runtime defensive measures by continually monitoring containers. It offers real-time security for containers in use, protecting them from a variety of attacks. With thorough visibility into container activities, CNAPPs can detect and prevent vulnerabilities, malware, and unauthorized access attempts. By interfacing with container orchestration platforms such as Kubernetes, CNAPPs ensure that security protections are uniformly applied across the whole container ecosystem.
Advanced threat intelligence capabilities
CNAPP employs advanced threat intelligence approaches such as machine learning algorithms and behavioral analytics that constantly evaluate security data from many sources to identify trends and indicators of compromise (IoC). As a result of this proactive approach, the systems can identify and block complex threats in real time. CNAPP systems identify possible security concerns and take proactive actions to stay ahead of attackers and respond successfully to zero-day vulnerabilities, reducing the risk of data breaches and service outages.
Automated remediation
CNAPPs employ automation to respond fast to security-related incidents. Automated remediation shortens the period between detection and resolution, reducing the potential impact of an attack. With the fast developments of containerized apps, manual intervention is usually impractical. CNAPPs automate the response to security concerns, making the remediation process easier. When a threat is detected, the platform may perform predefined actions such as isolating compromised containers, prohibiting malicious network activity, or even performing automated rollbacks to a secure state.
Comprehensive logging and auditing
CNAPPs support comprehensive logging and auditing, recording specific information on container activity and security incidents. This data is particularly important for incident investigation, compliance audits, and regulatory reporting. By establishing a complete audit trail, CNAPPs assist organizations in comprehending the chain of events, detecting hazards, and demonstrating compliance with industry rules.
Centralized management
CNAPPs provide centralized management consoles that present a unified view of and control over security measures. Having a single view enables security teams to establish policies, track events, and uniformly deploy updates across all containers, creating a consistent security posture.
DevOps integration
Integration with DevOps operations should be a significant component of CNAPP systems. Security must be included into the DevOps pipeline to provide a continuous and secure application delivery process. Leading CNAPPs also seamlessly integrate with major cloud service providers, enabling enterprises to extend their security policies across several clouds.
CNAPP solutions guarantee that security measures are incorporated from the beginning of the software development lifecycle, allowing enterprises to create safe applications while preserving development pace. This strategy ensures that security issues are handled as quickly as possible, reducing the danger of vulnerabilities making their way into production settings.
Microservices and serverless application security
Traditional security solutions may struggle to keep up with the adoption of microservices and serverless architectures in businesses. CNAPPs are intended to safeguard these ephemeral and dynamic workloads by offering the same degree of security for microservices and serverless operations as they do for regular containers. This flexibility is critical for ensuring the security of current, complex application architectures.
Traffic encryption, identity and access management, and runtime defense mechanisms are all part of end-to-end security for microservices-based architectures and runtime defense. By combating against function-level vulnerabilities, API abuse, and data disclosure risks, CNAPP solutions also safeguard the integrity and confidentiality of serverless environments.
Compliance and governance
CNAPP solutions help enterprises maintain a strong security posture and adhere to industry-specific standards by automating compliance testing for governance frameworks. Meeting regulatory and industry standards is very important to many firms. CNAPPs help with compliance by aiding in developing the businesses’ security policies, generating audit reports, and ensuring that containers adhere to security best practices. By automating compliance checks and providing documentation, CNAPPs lessen the difficulty of demonstrating security measures to auditors.
What Are the Benefits of CNAPPs?
CNAPPs provide several advantages, ranging from improved security and compliance adherence to streamlined management procedures and increased workplace productivity:
- CNAPPs amplify security by giving you more visibility and control over your cloud-native apps and infrastructure.
- CNAPPs are specifically designed to improve security protocols in cloud-native environments such as containers and serverless systems.
- CNAPP solutions continuously monitor cloud workloads, Kubernetes clusters, and other cloud environments for misconfigurations, code vulnerabilities, and security problems. This careful assessment improves security and eliminates hazards.
- CNAPPs significantly improve the security posture of cloud ecosystems, reducing the likelihood of data breaches and cyberattacks.
- The adoption of CNAPPs aids businesses in achieving the compliance requirements set by industry regulations and data protection laws.
- CNAPPs combine an extensive range of security capabilities onto a single platform, reducing the financial and operational difficulties associated with managing diverse security solutions.
- The centralized management of security rules and events facilitates efficient administration by allowing for quick reactions to possible risks.
- The rigorous security measures employed by CNAPPs promote an environment of trust for employees, ensuring the safety of their data and applications. This certainty leads to increased productivity.
What Are the Disadvantages of CNAPPs?
There are several cons to consider when deciding whether to use a CNAPP:
- CNAPP implementation may need specialized expertise and training, resulting in a longer learning curve for IT staff.
- Some CNAPPs are strongly connected with specific cloud service providers, thereby restricting alternatives for multi-cloud enterprises.
- If not properly tuned, CNAPPs could consume system resources, compromising the overall performance of cloud-based applications.
- Overzealous threat detection systems in CNAPPs may result in false positives, causing IT teams to examine unneeded alarms and alerts.
How to Implement CNAPPs for Your Organization
Implementing CNAPPs requires thorough planning and execution. The following are the main steps to consider:
- Conduct an in-depth evaluation of your organization’s cloud infrastructure and security requirements. Determine the CNAPP’s essential characteristics and capabilities by identifying potential risks and vulnerabilities.
- Investigate and assess CNAPP suppliers to identify the solution that best meets your organization’s needs, budget, and long-term security plan.
- Consider testing the CNAPP’s efficacy and compatibility with current systems with a trial implementation in a controlled setting.
- Ensure that the CNAPP integrates seamlessly with your cloud environment and that security rules are tailored to your organization’s needs.
- Make sure your IT team and stakeholders receive training on how to administer and use the CNAPP efficiently. Transferring knowledge is essential to realizing the platform’s advantages.
- Continuously monitor CNAPP’s efficiency and security on a regular basis. Use feedback loops to keep the platform’s efficiency up to date.
Are CNAPPs Popular?
Due to the increased prevalence of cloud computing and the rise in cybersecurity concerns, CNAPPs have become incredibly popular in recent years. Both large and small businesses understand how crucial it is to protect their cloud environments, and they are actively looking for reliable solutions like CNAPPs to improve their security posture. The ability of CNAPPs to simplify security administration and offer thorough security across various cloud infrastructures is another factor contributing to their appeal.
Featured Cybersecurity Software
Bottom Line: Optimize Cloud Security Through CNAPP
Organizations looking to defend their cloud environments from cyberthreats and data breaches should consider adding CNAPPs to their system’s arsenal. CNAPPs improve the security posture of cloud infrastructures by integrating several security methods into a unified suite, enabling enterprises to fully utilize cloud computing while lowering risks. Investing in CNAPPs is a smart decision to ensure a safe and secure digital future for enterprises of all sizes as the cloud computing landscape continues to change.
This updates an October 2021 article by Devin Partida.











