The LAPSUS$ threat group has had an attention-grabbing month, snaring high-profile victims like Microsoft, Okta, NVIDIA, Samsung and others.
On March 22, Microsoft confirmed a substantial breach by the LAPSUS$ hacking group. In a blog post detailing its efforts to track and contain the breach, Microsoft described LAPSUS$ as a “large scale social engineering and extortion campaign.”
In a short amount of time, LAPSUS$ has collected a substantial number of victims — and shows no signs of stopping.
Among cybercriminals, LAPSUS$’s attacks are uniquely public and technologically blunt — the equivalent of striking a digital infrastructure with a baseball bat. This simple approach has proven extraordinarily effective, although it’s unknown how much the LAPSUS$ group has profited from its exploits.
The Victims: Microsoft, Okta, and Many Others
LAPSUS$ has racked up a substantial number of victims — all large organizations with source code and proprietary information to protect. LAPSUS$ doesn’t appear to be using overtly sophisticated intrusion methods but instead relying on social engineering and purchased accounts.
In a very active month, the South American threat group has racked up an alarming list of victims:
- In late February, LAPSUS$ hacked and then released NVIDIA’s DLSS source code while claiming it had maintained access to NVIDIA’s servers for an entire week. NVIDIA confirmed the attack and indicated that a LAPSUS$ operative had gained access through employee credentials. NVIDIA’s DLSS codebase is said to include next-generation AI-powered image rendering technology, so the hack of the leading chipmaker could potentially lead to widespread damage.
- A week later, Samsung released a statement stating that it had also experienced a cybersecurity breach, including source code for its Galaxy Smartphones. While it did not identify LAPSUS$ as its attacker, LAPSUS$ later posted 190 GB of Samsung data, including Samsung’s biometric authentication and bootloader source code.
- Mid-March, popular game developer Ubisoft reported a data breach. It’s unknown what data was compromised. Though the attack hasn’t been directly attributed to LAPSUS$, there was chatter on the LAPSUS$ Telegram regarding the attack.
- On March 22, Okta, a Single Sign-On service provider, confirmed that attackers had breached its system – an attack that occurred in January. The investigation is ongoing. According to Okta, at least 366 customers have been impacted by the breach. Screenshots released by LAPSUS$ indicated that they acquired access to customer support tickets, Slack messages, and internal user management tools. Approximately 15,000 organizations use Okta services.
- As of March 23, LAPSUS$ has leaked 37 GB of Microsoft’s internal source code through torrents. The breach includes partial code from Bing, Cortana, and Bing Maps. Microsoft has stated that it does not rely upon the secrecy of its source code for its security.
Other potential victims of LAPSUS$ include Vodafone Portugal (Feb 2022) and Mercado Libre (March 2022).
Who is the LAPSUS$ Hacking Group?
According to Kari Walker of Flashpoint, surprisingly little is known about the LAPSUS$ hacking group. They have swiftly made a name for themselves by targeting numerous high-profile companies in swift succession. Though their attacks accelerated in March, LAPSUS$ first became active in 2021. Based on their use of Spanish and Portuguese and their early targets, they are believed to be a South American group.
Until LAPSUS$, most recent hacker groups focused on ransomware. Ransomware attacks encrypt data and require that the victim pay a ransom for the data’s release. Just between January and February, ransomware attacks rose by 53%, according to NCC Group. The Colonial Pipeline attack of 2021 made significant waves when it revealed how vulnerable even critical infrastructure could be.
However, LAPSUS$ isn’t a ransomware group — it’s an extortionist group. Rather than encrypting data and holding it for ransom, LAPSUS$ collects data and blackmails organizations to prevent its release. LAPSUS$ appears to coordinate through Telegram to execute their cyber extortion campaigns.
New broke today of the arrest of several LAPSUS$ members in the U.K., but it remains to be seen if the arrests put a dent in the group’s operations.
Also read: SANS Outlines Critical Infrastructure Security Steps as Russia, U.S. Trade Cyberthreats
Social Engineering and Cyber Crime
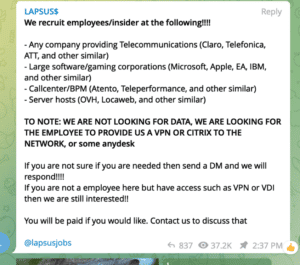
It’s not known how LAPSUS$ is breaching high-profile systems, but it appears they are primarily relying on social engineering techniques. Microsoft’s blog post noted that LAPSUS$ readily discloses its targets and openly offers to purchase employee credentials. Other strategies in use include phone-based social engineering and personal email breaches.
For a security officer, these threats are a nightmare to counter. But they also require malicious or negligent actors within the organization. Companies can take action to shore up their systems by identifying the hallmarks of potential intrusion, such as employees logging in from unknown locations or performing suspicious activities.
UEBA and employee cybersecurity training could address both suspicious activity and employee mistakes.
The Threat of Cyber Extortion
Blackmail inherently requires that an organization have data that it doesn’t want to be exposed. Following the Microsoft hack, LAPSUS$ released torrents containing partial source code for Bing Maps, Cortana, and Bing. During the NVIDIA attack, LAPSUS$ released confidential and potentially ground-breaking IP.
Microsoft’s major concern would be that revealing this source code could open them up to security vulnerabilities. However, proponents of open source development would likely note that the release of source code does not have to be inherently damaging.
“[The hack] highlights the need for secure development processes, SAST and DAST scans, secret scans, etc. It is also a good reminder that organizations should treat their code as if it were open source, and if their code is exposed, then minimal damage will occur,” according to Yakir Kadkoda, Lead Security Researcher at Aqua Security.
NVIDIA’s case is a little more complex, as it opens the company up to potential infringements of their new technology.
Also read: Best DevSecOps Tools
Okta LAPSUS$ Protection
SecurityScorecard’s Chief Information Security Officer, Mike Wilkes, outlined a few critical ways that Okta customers, in particular, should secure their environments:
- Check admin events/logs for suspicious activities
- Verify that “Give Access to Okta Support” is disabled
- Disable “Give Directory Debugger Access to Okta Support”
- Check to see if any unidentified API tokens have been created
In general, to avoid these forms of attack, organizations must:
- Treat their source code as though it is already open source
- Ensure that their environments are frequently monitored and scanned for intrusion
- Encrypt and protect their most critical data (and their data backups) through zero-trust policies
- Assume that their data and their systems will be breached
Cybercriminals are not only becoming more advanced; the resources that enable them to commit high-profile crimes are becoming more readily accessible. Hacker groups such as LAPSUS$ can easily coordinate through Telegram and receive blackmail payoffs through cryptocurrency — with minimal threat to themselves. Further, the proliferation of work-from-home infrastructure and easy access SaaS solutions creates networks with increasingly exposed attack surfaces. For most organizations, it isn’t a question of whether they will experience a data breach, but when they will experience a data breach.
Read next: Best Network Monitoring Tools




