AT&T is working to stop a botnet that has infected at least 5,700 network edge servers inside its networks and appears designed to steal sensitive information and launch distributed denial-of-service (DDoS) attacks.
Researchers at Netlab, the network security unit of Chinese tech giant Qihoo 360, wrote in a report this week that the rapidly updated botnet was attacking voice-over-IP (VoIP) servers from Edgewater Networks that are housed within AT&T’s network and are designed to route traffic from enterprise customers to upstream mobile providers (in this case, AT&T).
The botnet was able to exploit an older vulnerability in unpatched EdgeMarc Enterprise Session Border Controllers (ESBCs) that is tracked as CVE-2017-6079. Once inside the appliances, the botnet installed a modular malware strain that the Netlab researchers dubbed EwDoor.
The researchers initially detected the botnet on Oct. 27, observing it attacking the ESBCs through the four-year-old vulnerability. They wrote that the botnet uses a “relatively unique” mount file system command in its payload.
A Short Window of Visibility
The initial version of EwDoor used a multiple command-and-control (C&C or C2) redundancy mechanism, but after having problems with the main C&C network, the botnet operators reconfigured the communication model and the researchers lost track of the botnet. However, during the short time they had sight of it, they confirmed that the targets were the Edgewater devices within the AT&T network and that all 5,700 appliances were located in the United States.
“So far, the EwDoor in our view has undergone 3 versions of updates, and its main functions can be summarized into 2 main categories of DDoS attacks and Backdoor,” they wrote. “Based on the attacked devices are telephone communication related, we presume that its main purpose is DDoS attacks, and gathering of sensitive information, such as call logs.”
The three updates occurred during November.
Also read: Top Vulnerability Management Tools
Exploiting the Edgewater Devices
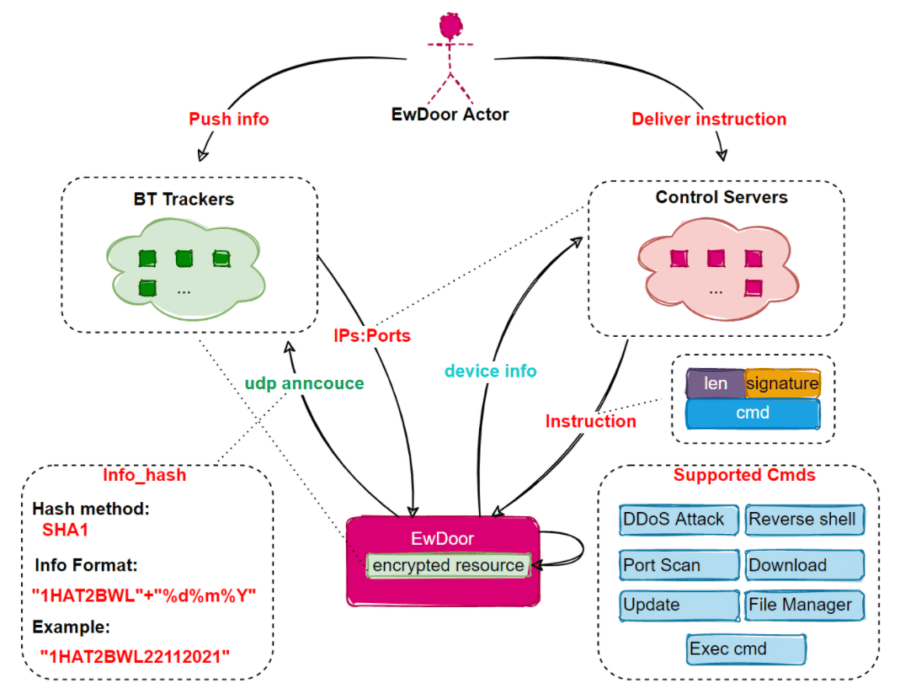
According to the Netlab researchers, the botnet exploits a hidden page in the Edgewater appliances that includes user-defined commands. The bad actors can get control of the page to execute commands. Once EwDoor is installed on the device, it can collect information and then uses a decrypted track to contact and send the device’s information to the C&C and then executes the commands.
It also uses TLS encryption to block attempts to intercept the network traffic and analysis of the malware, the researchers wrote. There are six primary functions of EwDoor: self-updating, port scanning, file management, DDoS attacks, reverse shell and executing arbitrary commands.
“In general, the function is relatively simple,” the researchers wrote. “When it runs on the infected device, it first collects device information, them performs some common things such as single instance, persistence and other functions; then decrypts the BT tracker and obtains C2 by accessing the BT tracker; finally reports the collected device information to C2 and executes the commands issued by C2.”
Also read: DDoS Attacks Skyrocket, Kaspersky Researchers Say
Threat Could Be Bigger Than Reported
The researchers also back-checked SSL certificates used by the 5,700 appliances and found there were about 100,000 IPs using the same SSL certificate as the EdgeMarc VoIP servers.
“We are not sure how many devices corresponding to these IPs could be infected, but we can speculate that as they belong to the same class of devices the possible impact is real,” they wrote.
In statements to the media, AT&T officials have confirmed the existence of the botnet and that they are taking “steps to mitigate” it. They also have said that they have “no evidence that customer data was accessed,” the carrier told Recorded Future’s The Record.
Also read: DDoS Attacks Skyrocket, Kaspersky Researchers Say
Appliances Left Unpatched
The fact that so many of these internet-facing appliances were unpatched for a vulnerability that was detected more than four years ago is troubling, according to executives in the cybersecurity space. It also reinforces the oft-repeated message to enterprises that they need to keep their systems updated.
Casey Ellis, founder and CTO at crowdsource cybersecurity vendor Bugcrowd, noted that the CVE-2017-6079 vulnerability was found in May 2017 and the patch made available about 18 months later, in December 2018. The vulnerability “is n-day [known], and one with a particularly large exposure window,” he told eSecurity Planet.
“This sort of lag in a public-facing system of privilege isn’t ideal and potentially contributed to so many of these endpoints staying unpatched and being open for exploitation by EwDoor in 2021,” Ellis said.
Bud Broomhead, CEO of cybersecurity firm Viakoo, said it’s not surprising these appliances were targeted.
“This is another example of how unpatched edge and IoT [Internet of Things] devices are highly attractive targets for threat actors,” Broomhead told eSecurity Planet. “Taking edge networking devices offline is not an option. They have to be remediated with the latest security fixes. The short timeframe that this vulnerability was shown to breach a large number of devices creates an urgency … that only remediation automation can meet.”
Also read: Best Patch Management Software
The Need for Automated Updates
Taylor Gulley, senior application security consultant at application security vendor nVisium, agreed that the EwDoor campaign illustrates the need for automated updates by default on such unmanaged devices.
“This widespread device takeover once again shows how important it is to keep your publicly-accessible devices up-to-date,” Taylor told eSecurity Planet. “It also reiterates the fact that many companies are in dire need of a patch management program. … Any successful compromises may be hard for an organization to detect if they don’t have complete logging and monitoring coverage for their edge devices, and practically impossible for a typical user to do so.”
The threat in this case is real, even though AT&T may not have found that customer data had not been accessed, Bugcrowd’s Ellis said. Any botnet that can get a foothold into an EdgeMarc ESBC could gain access to high-speed and low-latency network connections, which can be useful for DDoS attacks, and the traffic running through the routers themselves and the networks behind them.
“Enterprise network connections are likely to be considered more trustworthy by behavioral detection and bot-blocking systems, so all in all the creators of EwDoor have targeted their malware for maximum value and potential impact,” he said. “The mount system payload is quite novel and the resilience in their C2 infrastructure suggests that the operators are quite sophisticated.”
Further reading: Top IoT Security Solutions of 2021




