Hacking groups linked to Russia, China and India are leveraging a novel attack technique that makes it easier for them to spread malware, steal data and evade detection, according to a report this week by security firm Proofpoint.
The advanced persistent threat (APT) groups are using a technique called rich text format (RTF) template injections, which is similar to a template injection tactic that exploits Microsoft Office files. Bad actors are using the new technique to leverage RTF text file attachments in phishing emails.
What makes the RTF template injection technique such a threat is that it’s easier for hackers to deploy – “It is trivial to alter the bytes of an existing RTF file to insert a template control word destination including a URL resource,” the Proofpoint researchers wrote in a blog post – and more difficult for antivirus and endpoint security solutions to detect.
ATP Phishing Campaigns
The researchers wrote that they have seen distinct phishing campaigns run by APT threat actors in the three countries using the RTF template injections during the second and third quarters, but added that “based on the recent rise in its usage and the triviality of its implementation, that it could soon be adopted by cybercriminals” that are more financially motivated.
Sean Nikkel, senior cyber threat intel analyst at cybersecurity firm Digital Shadows, told eSecurity Planet that the use of weaponized documents that require enabling downloads or similar connections to outside content isn’t new. However, enterprises need to understand the threat of a new technique like RTF template injections, particularly if the use of it continues to spread.
“The real fear is that we’ve seen criminal actors adopt techniques that work, especially if nation-state actors are using them with success,” Nikkel said. “Users should become aware of the risks of opening documents that require downloads of templates or other data from the internet, especially from unknown users.”
Also read: Top Secure Email Gateway Solutions
A Change from Office Files
Past template injections attacks over the years have entailed cybercriminals sending Office files like DOC and PPT to victims and later uploading the malicious payload through the template. Now they are using Windows RTF files.
According to the Proofpoint researchers, the RTF template injection is a simple tactic. An RTF file containing decoy content can be manipulated after the RTF file is opened to allow content hosted at an external URL controlled by the hackers, who can then secretly bring in a malicious payload that gets installed on the systems when the victims open the documents.
“While historically the use of embedded malicious RTF objects has been well documented as a method for delivering malware files using RTFs, this new technique is more simplistic and, in some ways, a more effective method for remote payload delivery than previously documented techniques,” the researchers wrote.
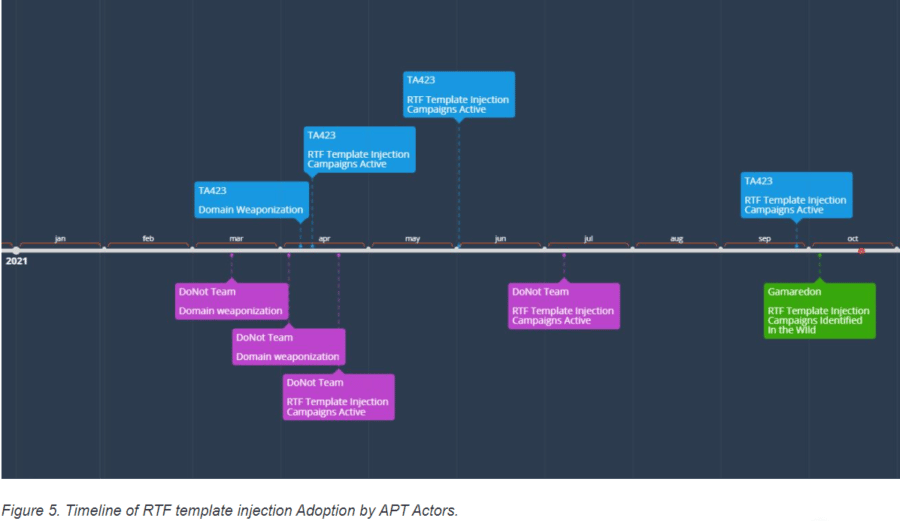
Campaigns Began in Early 2021
Proofpoint saw the RTF template injection technique being increasingly used from February through April by APT threat actors, though the researchers first picked up discussion about it in January. There were two APT groups – TA423, associated with China, and DoNot (India) – that first began using the new tactic in March, with the registration of the first domains. Multiple campaigns followed throughout April and May, they wrote.
Further campaigns attributed to the DoNot group were identified through early July, and RTF files most likely coming from TA423 were seen as late as Sept. 29, targeting organizations that have tied with Malaysian deep-water energy exploration.
Eventually, the Gamaredon ATP group – which has been linked to the Russian Federal Security Service (FSB) – was detected using RTF template injection files in campaigns in early October using documents impersonating the Ministry of Defense. That tactic is consistent with reports that have linked Gamaredon to the FSB in other parts of Ukraine, including the Republic of Crimea and the city of Sevastopol, the researchers wrote.
“The moral of the story is that adversaries will continue to evolve or modify their tactics, and that your anti-malware solution will ultimately fall short of providing confidence that at any given moment a user, asset or workload has not been compromised,” Tim Wade, technical director of the CTO team at cybersecurity vendor Vectra, told eSecurity Planet. “Managing this inevitable compromise with visibility, detection and response is the hallmark of modern enterprise security programs resilient to motivated adversaries and their legacy peers that continue to struggle with the disruption of a successful attack.”
Defending Against RTF Injections
Enterprise IT leaders need to consider what steps to take to protect themselves against these attacks, according to Digital Shadows’ Nikkel.
“Organizations may want to consider restricting the use of certain file types, such as RTF, in case security tools don’t catch suspicious signatures or behaviors that would be a giveaway for attacks like these,” he said. “An even more restrictive security stance might involve stripping inbound emails of attachments or using a sandbox to test them for malicious activity.”
Such considerations are important because the Proofpoint researchers don’t expect the template injection threat to disappear anytime soon. The viability of Office-based remote template documents has shown that the delivery mechanism is effective when paired with phishing as an initial delivery method, they wrote.
Adoption of RTF Technique will Grow
“The innovation by threat actors to bring this method to a new file type in RTFs represents an expanding surface area of threat for organizations worldwide,” the researchers wrote. “While this method currently is used by a limited number of APT actors with a range of sophistication, the technique’s effectiveness combined with its ease of use is likely to drive its adoption further across the threat landscape.”
Eventually this technique will see much wider adoption beyond phishing attacks.
“While Indian and Chinese APT actors have demonstrated an affinity for RTF file types in the past by using RTF weaponizers like the tool Royal Road, defenders eventually saw those tools and techniques become widely used by less sophisticated actors,” the researchers wrote. “This well-established trickle-down pattern may be accelerated in this case based on the minimal effort needed to weaponize RTF attachments before deploying in active phishing campaigns.”
Further reading: How DMARC Can Protect Against Ransomware







