An application gateway, also known as an application level gateway (ALG), functions as a critical firewall proxy for network security. Its filtering capability ensures that only certain network application data is transmitted, which has an impact on the security of protocols including FTP, Telnet, RTSP, and BitTorrent. Understanding ALGs involves knowing how they work, their pros and cons, and how they integrate with or differ from other types of firewalls.
How Application-Level Gateways Work in 9 Steps
ALGs enable secure communication from the start of client requests to the integration of complementary firewalls. They protect privacy by using proxy server connections and enforce security through application layer and packet inspection. They also effectively manage traffic, alter packet metadata as appropriate, dynamically assign resources, and apply dynamic policies to improve network performance and security.
Explore the setup and optimization processes that users can take for ALGs, as well as the functionalities of ALGs after proper configuration. To help you visualize the process better, we’ve also provided screenshots from Microsoft Azure’s application gateway documentation.
1. Users Set Up the Application Gateway
To create an application-level gateway, use the gateway’s interface to configure various options. Start with assigning listeners to ports, defining rules, and allocating resources to a backend pool. After configuration, test the gateway’s operation by accessing it via a browser and validating the response. Finally, when resources are no longer required, clean them up by deleting the related resource group.
2. ALG Facilitates the Client-Server Communication
When a client initiates a request, application-level gateways facilitate data transmission between the client and the server. It often involves requests for files, web pages, or other internet services. This creates the first connection for accessing server resources.
ALG supports client requests by resolving its domain name via DNS and delivering the frontend IP address to the client. It accepts incoming communication through listeners configured with frontend IP addresses and protocols. If a web application firewall (WAF) is enabled, it checks requests against WAF rules and either routes them to backends or blocks them. For valid requests, it checks routing rules and directs them to appropriate backend pools.

3. ALG Establishes Proxy Server Connection
Proxy server connections act as agents, allowing clients to communicate with main servers. Clients connect to proxy servers to manage connections behind firewalls and anonymize client IP addresses. These servers provide secure data transmission, improving privacy and security in network interactions between clients and servers.
ALGs intercept and redirect client requests to a proxy server or gateway. The proxy server then routes the requests to the correct destination, such as a backend server. ALGs can execute activities like packet inspection and modification before sending traffic to ensure security and compliance.
4. ALG Performs Application Layer & Packet Inspection
To ensure network security, application layer and packet inspection work together in a systematic manner. Initially, incoming packets are intercepted at the network interface. At OSI Layer 7, the highest layer responsible for application-level communication, the firewall checks each packet’s header to determine the protocol and destination port.
The payload is then thoroughly inspected for any irregularities or security policy violations. If a danger is discovered, an appropriate measure, such as blocking or logging, is taken in compliance with predetermined security policies. This process is repeated for outgoing packets, and all examined packets are logged for auditing and reporting, assuring ongoing network protection.
5. ALG Implements Functionality & Users Test the Backend
ALGs in the firewall recognize and process traffic for specific applications. They identify services using Layer 4 information such as TCP and UDP port numbers, then decide which ALGs to use for each type of traffic. To allow ALG capability and service identification, the firewall must be configured and the criteria for recognizing network services using Layer 4 information must be defined. Each network service should be assigned the proper ALG.
To verify the effectiveness of ALG, users must do careful testing. Fine-tune ALG parameters depending on test findings, and use monitoring tools to keep track of ALG performance and backend health. Lastly, create and enforce service identification regulations, and evaluate and update ALG settings on a regular basis.
6. ALG Manages Traffic
ALGs intercept both incoming and outgoing traffic as they travel through the firewall. They evaluate packets after they have been intercepted to determine whose application or service they belong to. Once detected, ALGs monitor communication sessions between clients and servers. ALGs manage each new session by creating a session entry and mapping it to the appropriate application or service.
7. ALG Modifies Packet Information
After managing traffic, ALGs intercept and analyze packets passing through the firewall to find modifiable information such as IP addresses or port numbers. Following preset rules or regulations, ALGs adjust this information as needed, possibly performing network address translation (NAT) processing or header manipulation.
When connecting with external networks, NAT often entails translating the private IP addresses of devices on the local network to a single public IP address allocated to the router/firewall, and vice versa. This conserves public IP addresses and increases security by concealing internal network structure from outside sources.
In some instances, ALGs may inspect and change packet payloads before reassembling them to meet protocol requirements. Quality checks ensure that modifications meet security and network requirements, and then ALGs transport the modified packets to their intended destinations, facilitating continued network communication.
8. ALG Allocates Resources & Applies Dynamic Policies
ALGs dynamically assign resources in response to changing network traffic demands by constantly monitoring and altering resource allocation, such as bandwidth and computing power. Throughout a session, ALGs monitor traffic for anomalies and enforce dynamic policies depending on traffic characteristics to ensure network security. They change resource allocation based on policy enforcement and traffic monitoring to ensure the best network performance.
ALGs release resources after a session ends, allowing them to be reallocated for future demands. They store session information, including resource allocation and policy enforcement, for auditing and reporting. This gives consumers visibility into network performance and security incidents.
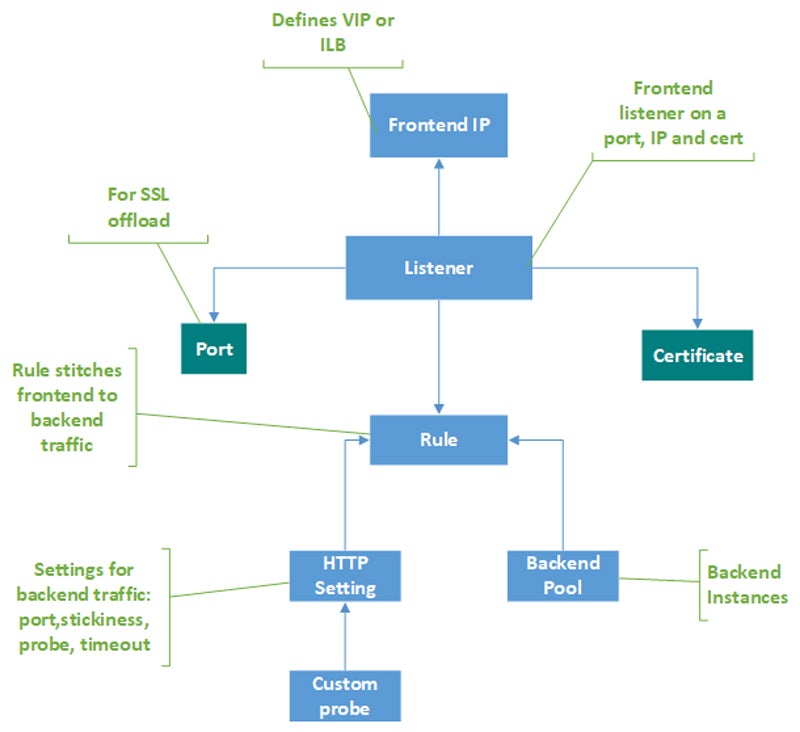
9. Users Integrate ALGs with Complementary Firewalls
To successfully integrate ALG with complementary firewalls, examine network requirements and choose appropriate solutions. Create an integration plan that outlines ALG’s position with other firewalls. Deploy and configure complementary firewalls to meet ALG standards. Set ALG settings on firewalls to support the appropriate applications. Establish communication routes between ALG and firewalls. Thoroughly test integration to ensure smooth operation.
Implement monitoring tools to track performance and ensure policy compliance. Analyze the setups and fine-tune them accordingly. Regularly evaluate and update settings to keep up with network threats and changes. These methods ensure that ALG works seamlessly with other types of firewalls, improving network security and application-level traffic control.
5 Advantages of Using ALGs
Application-level gateways boost security, manage app protocols, and offer detailed logging. Additionally, they improve network performance and protect your privacy.
Enhanced Security
ALGs boost network security by implementing strong user authentication and authorization processes. By confirming user identities and implementing access rules, ALGs prevent illegal access and secure sensitive resources. This guarantees that only authorized users may access network resources, lowering the risk of data breaches and illegal activities.
Granular Control Over Application Protocols
Administrators can specify particular rules and regulations for each application using ALGs to have granular control over application protocols. This allows for exact network traffic management while maintaining compliance with organizational policy and regulatory requirements. ALGs optimize network performance and security by controlling application access while also allowing for more efficient resource utilization.
Comprehensive Logging
ALGs offer comprehensive logging by documenting detailed information on network connections and activity. This includes statistics on user interactions, application usage, and network traffic patterns. Comprehensive logging allows administrators to conduct in-depth audits, effectively troubleshoot issues, and analyze network usage for billing or compliance purposes.
Improved Performance
ALGs increase network performance by caching frequently visited files, reducing the need for multiple retrievals from external servers. This caching reduces latency and saves bandwidth, especially for frequently utilized resources. By optimizing data transmission, ALGs increase network responsiveness and user experience and consequently enhance overall network performance and efficiency.
Ensured Privacy
ALGs strengthen privacy by acting as mediators and preventing direct external access to internal resources. This approach protects sensitive information while reducing the risk of security breaches or unauthorized access. ALGs give an additional degree of protection by separating external and internal networks.
5 Weaknesses of ALGs
Despite their security and performance advantages, ALGs face limitations with their protocol-specific configuration, UDP inefficiency, dependence on specialized knowledge for implementation, user training issues, and complex configuration.
Protocol-Specific Setup
One downside of ALG is its protocol-specific setup, necessitating individual configuration for each application protocol. Administrators must manage the complexities of numerous protocols. This consequently adds to the complexity and maintenance issues. This tailored method complicates implementation and may limit scalability, impeding efficient network administration and optimization.
Inefficient with UDP-Based Protocols
ALGs struggle with UDP-based protocols, resulting in inefficient traffic management. Their architecture fails to accommodate the stateless nature of UDP, resulting in poor performance and restricted application. This shortcoming limits their capacity to handle a wide range of network applications and may compromise network operations and responsiveness.
Knowledge-Dependent Implementation
Another drawback of ALGs is their knowledge-dependent implementation that demands a thorough understanding of each application protocol for setup. This dependency complicates implementation and needs specific skills, impeding deployment. Administrators must have in-depth knowledge to correctly configure ALGs, thus limiting accessibility and may delay adoption in businesses without the necessary competence.
User Training Challenges
Large enterprises may need user training for implementing ALGs. Educating users on ALG usage might be difficult, perhaps outweighing the benefits of deployment. This could hinder effective use and acceptance. The underutilization or misconfiguration of these tools reduces the intended security and performance benefits offered by ALGs.
Complex Configuration & Compatibility Issues
Configuring ALGs involves careful attention to network requirements and compatibility concerns. This complexity might result in configuration problems and compatibility concerns. As a result, it may prevent seamless incorporation into existing network infrastructures. Furthermore, the extensive setup process may cause delays and operational disruptions.
How ALGs Integrate into Different Firewall Architectures
Different firewall architectures like NGFWs, VPNs, integrated firewall appliances, cloud-based firewalls, UTM, and WAF, provide ALGs with a range of ways to optimize network security and performance. ALGs can improve traffic management and security procedures by seamlessly interacting with existing infrastructures, offering comprehensive protection across a wide range of network scenarios.
NGFW
ALGs integrate into next-generation firewall (NGFW) designs by providing application-level intelligence and control. NGFWs combine traditional firewall capabilities with extra functionality like intrusion prevention, SSL inspection, and application management. ALGs enhance NGFWs by performing deep packet inspection at the application layer, offering precise control over application protocols and increasing overall security posture.
VPN
Users can integrate ALGs and VPNs by setting up ALGs to inspect and manage traffic passing via the VPN tunnel at the application layer. By deploying ALGs alongside VPN gateways or concentrators, you can enforce policies and apply security measures to VPN traffic.
Integrated Firewall Appliances
Integrated firewall appliances incorporate firewall functionality with additional security technologies such as intrusion prevention, VPN, antivirus, and content filtering to provide comprehensive network solutions. ALGs collaborate with these appliances to provide application-layer intelligence and control and improve firewalls through deep packet inspection. It optimizes network performance by efficiently managing and prioritizing application traffic.
Cloud-Based Firewalls
Cloud-based firewalls protect cloud resources from cyberattacks. To properly integrate ALGs, deploy ALG functionality in the cloud or use cloud-native ALG services from your firewall provider. This includes establishing ALGs to inspect and control cloud traffic, ensuring uniform security rules across resources, and seamlessly integrating with firewall administration interfaces to enable centralized policy management and monitoring.
UTM Appliances
ALGs work with unified threat management (UTM) appliances to provide sophisticated application-level intelligence and controls. Configure ALGs within the UTM appliance in order to analyze and manage application-level traffic. This entails developing policies and regulations for individual application protocols to maximize security and network performance.
WAF
Web application firewalls (WAF) and ALGs both operate at the application layer of the network stack. ALG, through deep packet inspection and control over application protocols, complements WAF capabilities. It improves comprehension and administration of application protocols for more accurate detection and prevention of web-based attacks. ALGs can also boost WAF performance by effectively controlling and prioritizing application traffic.
ALG vs Packet Filtering vs Stateful Inspection
Here’s a comparison of application-level gateways, packet filtering, and stateful inspection based on their complexities, screening methods, and network performance impact. This also includes their network topology visibility, transparency to users, and packet inspection capabilities. Compare ALG with packet filtering and stateful inspection using this table and continue reading below for additional details.
| Features | ALG | Packet Filtering | Stateful Inspection |
|---|---|---|---|
| Complexity | Complex | Simple | Moderate |
| Screening | Based on behavior or proxies | Based on connection rules | Based on communication state/context |
| Network Performance | High impact | Low impact | Moderate impact |
| Network Topology Visibility | Can hide from attacker | Can’t hide from attacker | Can hide from attacker |
| Transparency to Users | Not transparent | Transparent | Transparent |
| Packet Inspection Visibility | Full data portion | Addresses and service protocol type | Full data portion |
ALG vs Packet Filtering
ALGs provide deep packet inspection at the application layer, giving precise control over application protocols and improving security measures. In contrast, packet filtering permits high-speed filtering using simple rules, resulting in efficient network traffic processing. While ALGs improve security by analyzing traffic at the granular level, packet filtering prioritizes sustaining data flow through simple rule implementation.
ALG vs Stateful Inspection
ALGs examine and manage traffic at the application layer, preventing unwanted access and reconnaissance attempts, whereas stateful inspection quickly detects and drops harmful or unneeded traffic. While ALGs provide tailored security measures for specific application protocols, stateful inspection conducts complete screening based on communication state and context, ensuring dynamic rule application for nuanced security policies.
Bottom Line: Deploy Application-Level Gateways For Enhanced Network Performance
While ALGs apply packet inspection and offer granular control over application protocols, they are simply one aspect of overall network defense. ALGs alone cannot handle all security issues and must be combined with other network security solutions to provide comprehensive protection. To build a strong network defense plan, integrate ALGs with other firewalls, intrusion detection systems, and other security measures.
Discover how intrusion detection and prevention systems (IDPS) and other types of firewalls complement application-level gateways for stronger network security.




