A circuit-level gateway (CLG) is a firewall feature that acts as a proxy and filters packets based on session information. CLGs are important because they provide specialized security filtering and prevent the discovery of IP addresses and open ports on CLG-protected devices. The best use cases stem from how CLGs work, their pros, cons, and how they function differently than other potential solutions.
Table of Contents
How Circuit-Level Gateways Work
CLGs create monitored bridges between two networks that monitor, validate, and filter communication packets without inspecting packet contents. It works at the session layer of the open systems interconnection (OSI) model and between the application and transport layers of the Transmission Control Protocol/Internet Protocol (TCP/IP) model. CLGs depend on two key features, proxy capability and stateful packet inspection, to block unsolicited communication.
Successful implementation of a circuit-level gateway defends against unrestricted communication, which can enable network probing, malware delivery, and other attacks. CLGs can be combined with threat feeds to inform security policies that block known-malicious URLs and IP addresses. An illustration of how a CLG defends networks using proxy capabilities is below and further explained under features.
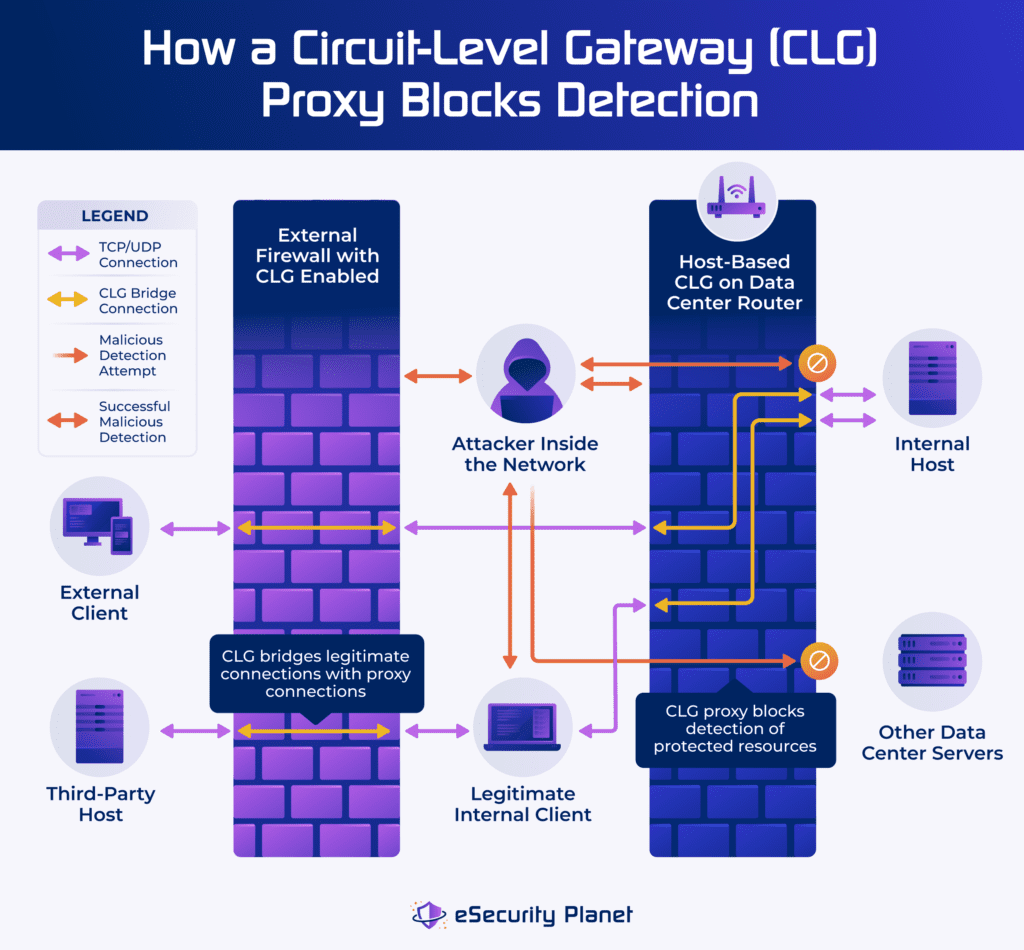
CLGs can’t detect attacks; however, they simply drop packets because they don’t match communication records. This effectively blocks many techniques used to explore networks and open ports for potential attacks. Dropped packets also defend against many different types of distributed denial of service attacks (DDoS) that attempt to consume server resources with TCP packets unrelated to established connections such as ACK-floods and SYN-floods.
Key Circuit-Level Gateway Features
Circuit-level gateways provide a very narrow network security solution to manage communication connections. This solution applies security policies to the two key features: proxy capability and stateful inspection.
Proxy Capability
The CLG receives initial requests for communication from a client on one side of the CGL to a host on the other side. The CLG checks the request against the relevant inbound or outbound communication rules and authorized requests will result in an established TCP or User Datagram Protocol (UDP) connection between the client and the CLG.
Next, the CLG acts as a proxy to contact the host on behalf of the client. It conducts the handshake process to complete authentication and authorization with the host. A successful connection will result in a second direct TCP or UDP connection between the CLG and the host bridged internally with the client connection. The CLG performs no further packet checks on this communication for its duration.
Traffic appears to originate from the CLG, so both hosts and clients can see the gateway. However, neither can explore or see past the gateway, which preserves the secrecy of the internal architecture.
Stateful Packet Inspection
CLGs maintain a record of all open communication connections, which enables stateful packet inspection. The CLG compares any arriving packet with these records and will simply drop any packet unrelated to established channels unless it’s a request to establish a new connection. The session records include protocols, port numbers, timeouts, and source and destination IP addresses and purge the information when the session terminates.
Stateful inspection ignores packet content, which enables rapid analysis and high data throughput. Unfortunately, this also means that malicious content passes freely through legitimately established communication channels.
Circuit-Level Gateway Use Cases
Use CLGs to provide focused communication security that maintains high data throughput, conceals network details, and validates legitimate traffic. Because they deliver narrow security, use cases should combine CLG features in combination with other security solutions such as packet filtering firewalls, next generation firewalls (NGFW), or zero trust network access (ZTNA) that protect against broader attacks.
Network Protection
By 1990, AT&T Bell Laboratories developed the first stateful network firewall, which they called circuit-level gateways, to protect and monitor communication sessions. Today, CLGs form a subset feature of stateful inspection adopted by many types of firewalls and should be implemented as one of many firewall features that protect local, virtual, and cloud networks.
Network Segmentation
Use the CLG feature of a host-based firewall on a router to provide extra protection and network segmentation. Such segmentation can segregate research labs, credit card processing systems, or similar regulated or high-value resources that require isolation from less sensitive network traffic.
Application Protection
Some vendors build CLG capabilities into applications to provide additional enterprise protections. For example, IBM incorporates the SOCKS protocol to provide CLG filtering and protection for the Db2 database system. Such capabilities provide strict control over high-speed communication as well as hide infrastructure details for the database (or other apps).
5 Advantages of Circuit-Level Gateways
Circuit-level gateway features deliver distinct security and operations advantages:
- Discreet connections: Implements a simple proxy for all connections that hides the IP addresses and port information of assets under protection.
- High throughput: Uses simple filtering rules based on established communication sessions to quickly allow or drop packets to maintain high speed data transmission.
- Low resource utilization: Processes packet rule decisions with low memory and processor requirements to enable low-cost deployment or multi-feature combinations.
- Selective filtering: Only tries to filter packets related to established communication and can simply and rapidly drop all unrelated packets without any rule analysis.
- Simplified operation: Requires straightforward setup with relatively simplified rules which simplifies installation, changes, maintenance, and testing.
5 Disadvantages of Circuit-Level Gateways
CLGs have five general disadvantages:
- Adds overhead: Slows data throughput with the proxy translation and session information inspection compared to more simple packet filtering rules.
- Change sensitive: Relies on established IP addresses, host names, and process names so basic CLGs can struggle to detect and keep up with network changes.
- Lacks awareness: Inspects only session information and therefore lacks insight into applications or app data to protect against attacks using established connections.
- Overly permissive: Establishes any communication request permitted by established rules without screening for known-malicious URLs or IP addresses.
- Simplistic security: Focuses narrowly on establishing connections and the related session information without any check for malicious payloads within the data packets.
Vendors don’t make standalone CLG appliances, so most CLG-capable firewalls will bundle CLG features with other security features that compensate for CLG security shortfalls.
Circuit-Level Gateways vs CLG Alternatives
Circuit-level gateways provide one of several proxy functions in firewalls and add security to network routers and other devices. Most admins use CLGs in combination with other features; here’s a brief comparison with other security and network segmentation solutions, including packet filtering, application level gateways, stateful inspection, and software-defined wide area networks (SD-WANs).
Circuit-Level Gateways vs Packet Filtering
CLGs provide specialized stateful packet filtering focused on TCP/IP inspection and filtering. Use simple packet filtering features to enable more generalized security rules that implement a broader range of security protections with minimal sacrifice to data throughput. Packet filtering rules include allow and deny lists (aka, whitelisting and blacklisting), closed ports, and disallowed protocols.
Circuit-Level Gateways vs Application Level Gateways
CLGs inspect TCP/IP communication and can block unauthorized communication, but restrict filtering specifically based on session header information. Use application layer gateways (ALGs) to enable application-layer data packet inspection that can detect and block malicious attacks and sensitive data exfiltration.
Circuit-Level Gateways vs Stateful Inspection
CLGs use specialized stateful inspection combined with proxy features to isolate the network behind the CLG and perform specialized communication inspection. When data throughput can tolerate some slowdown, implement more general stateful inspection features to protect against a broader range of malicious attacks against protocols and communication.
Circuit-Level Gateways vs SD-WAN
Some admins will use CLGs to create network segments segregated and hidden from discovery from the rest of the network. While effective, CLGs can be clumsy to manage. In a more rapidly changing environment without a packet-inspection requirement, use SD-WAN technology to centralize and automate network segmentation faster and more efficiently.
Bottom Line: Use CLGs for Speedy Security
Circuit-level gateways rapidly filter packet traffic to retain high-speed data throughput, but with limited security protection. Fortunately, these capabilities fit in nicely into a security stack of other features and solutions. Use CLGs to improve the performance of other security tools by quickly decreasing the number of packets to analyze for deeper and much slower analysis.
Learn more about how web application firewalls (WAF) provide deeper analysis and focused protection for websites and applications.







