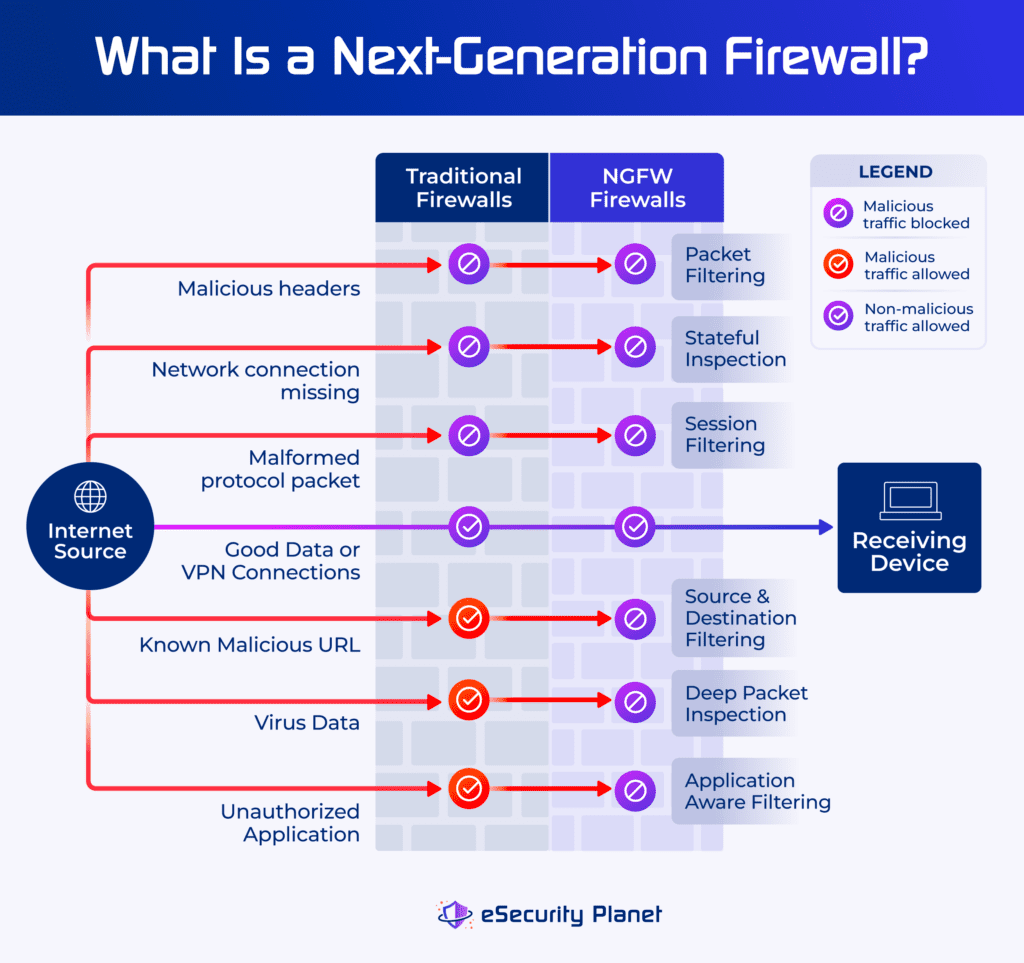
A next generation firewall (NGFW) performs deep packet inspection to check the contents of the data flowing through the firewall. Unlike more basic firewalls that only check the header of data packets, NGFWs examine and evaluate the payload data within the packet. This deep packet inspection provides the basis for the various NGFW features that improve malware blocking.
How Next-Generation Firewalls Work
Through next-generation firewalls, all information transmitted by computers through any network is broken into transmittable chunks, known as the data portion of a packet. The data is wrapped in instructions for how to deliver that data (IP address, destination port, etc.) which is known as the packet header.
Data packets add header instructions classified under either the open systems interconnection (OSI) model or one of the transmission control protocol / internet protocol (TCP/IP) models. All firewalls filter based on rules for network and transport layer information and many newer firewalls can also filter on the data link layer to block malicious IP addresses and URLs.
The table below outlines the layer instructions added to the packet header and the associated layer according to the OSI model and each of the TCP/IP models.
| OSI Layer | 4-Layer TCP/IP | 5-Layer TCP/IP | Layer Instructions for: |
|---|---|---|---|
| 7. Application | 4. Application | 4. Application | Sending and receiving application information |
| 6. Presentation | 4. Application | 4. Application | Information on usable data formats, encryption |
| 5. Session | 4. Application | 4. Application | Controlling ports and session information |
| 4. Transport | 3. Transport | 3. Transport | Transmission protocol information (TCP, UDP, etc.) |
| 3. Network | 2. Internet | 2. Network | Device address information between sending and receiving machines |
| 2. Data Link | 1. Link | 2. Data Link | Device MAC address and network format information |
| 1. Physical | 1. Link | 1. Physical | Hardware network interface card (NIC) instructions |
NGFWs remain the only class of firewalls to filter data based on application, presentation, or session layer packet information. Additionally, they can decrypt data to examine the contents of the packets themselves for malicious content.
Certain organizations are ideal candidates for a next-gen firewall, while others may prefer other types of firewalls. Factors to consider include NGFWs’ features and capabilities as well as their key advantages and disadvantages.
Who Needs a Next-Gen Firewall?
Every organization that can afford a next generation firewall solution can benefit from the extra security provided by deep packet packet inspection. NGFW vendors used to target the largest enterprises, but most firewalls now incorporate many NGFW capabilities because of the broad benefits that satisfy the firewall needs for most situations – even for small businesses and smaller IT teams.
Some organizations will possess high-speed data throughput needs that do not tolerate NGFW packet inspection delays in front of application servers, databases, etc. Yet, even these organizations will deploy NGFW elsewhere in the organization to provide general protection to users, branch offices, and applications tolerant of delays.
Who Doesn’t Benefit from NGFWs?
For companies with resource constraints or specialized needs, NGFW may cost too much, deploy with excessive options, or cause too many data throughput delays. These organizations will consider different types of firewalls that might provide a better fit.
Resource-Constrained Options
While most firewalls sold today adopt many NGFW capabilities, budget limitations may lead resource-constrained teams to seek inexpensive and reduced-feature firewalls similar in capabilities to traditional firewalls. Some organizations with IT staffing limitations may prefer to adopt a firewall-as-a-service (FWaaS) solution that enables more robust capabilities in exchange for simplified options and reduced control.
Simplified Needs
Sometimes a network needs a simple firewall for network segmentation or to perform simple packet filtering for network security. The extra features and costs of NGFW will be wasted on simple tasks and a low-cost and simplified firewall provides a more appropriate solution.
High Data Throughput Options
High data throughput needs often require multiple firewall solutions that can provide fast, packet-based filtering as a first layer of defense, followed by specialized firewalls to provide specialized defenses for cloud security, web applications, databases, or containers. These organizations may still use NGFW to protect their general networks but will find the packet inspection a performance bottleneck in front of high-speed application servers.
5 Primary Features & Capabilities of Next-Generation Firewalls
Firewalls provide protective barriers and each feature enables protection against specific threats. Next generation firewalls provide five key features:
- Traditional firewall features: Filter based on packet headers.
- Deep packet inspection: Filter based on application specifics, encrypted traffic analysis, sources and destinations, and threat intelligence feed integration.
- Network intrusion prevention: Monitor network traffic for potential signs of attack.
- User aware filtering: Tie into active directory to modify rules by users and groups.
- Network sandboxing: Test unknown files for malicious behavior in isolation.
Traditional Firewall Features
All NGFWs include the original capabilities developed for the first generations of firewalls. These packet, session, and proxy capabilities continue to provide fast filtering that free up resources for more advanced features.
Packet Filtering
Packet filtering reads the port and IP addresses in the packet header and blocks traffic based on specific firewall rules. This feature is important because it narrows the scope of potential attacks. Automatically dropping unauthorized and unwanted traffic also reduces the number of packets upon which an NGFW will need to perform deep packet inspection.
Session Filtering
Firewalls use session filtering rules to monitor established connections and block attacks using spoofed sessions. Older distributed denial of service (DDoS) attacks used malformed TCP requests to overwhelm servers and session filtering drops requests not associated with new or established sessions.
Stateful Inspection
Stateful inspection firewalls track the behavior of active network connections to detect and block potential data and traffic risks. Stateful inspection requires more memory and more time to analyze packets in the context of other data associated with specific connections.
Proxy Capabilities
Proxy capabilities allow a firewall to act as a single point of contact for sources outside of the firewall’s network and the firewall will then redirect traffic to the specific assets behind the firewall. This category of capabilities can be broken into specific sub-features such as:
- Application-level gateway (ALG): Enhance network address translation filtering for application-layer protocols such as FTP, BitTorrent, Telnet, etc.
- Circuit-level gateways (CLGs): Provide proxy services with session filtering capabilities or simply provide session filtering depending on the setup.
- Network address translation (NAT): Act as a router where only the firewall knows how to direct traffic inside the network.
- Port address translation (PAT): Use port data to reroute packets to different assets such as routing data to port 587 to the email server.
- Virtual private network (VPN): Enable encrypted tunnel connections between internal and external devices.
Deep Packet Inspection
Deep packet inspection considers the application layer information as well as the packet content itself to provide much more protection – often enhanced by artificial intelligence (AI) anomaly detection. Deep packet inspection enables and integrates filtering based on application awareness, encrypted data contents, malicious site awareness, and malware signatures.
Application Aware Filtering
Deep packet filtering can recognize the application, the activities of the application, and the data flowing between the application and the user device. For example, where a traditional firewall can either allow or block access to Facebook, an NGFW can allow Facebook, but block Facebook games. Risky applications can be blocked entirely and other applications can be allowed but blocked when attempting to access sensitive information or specific devices.
Encrypted Traffic Inspection
To enable deep packet inspection, NGFWs decrypt secure socket layer (SSL), secure shell (SSH), or other encrypted connections to inspect the encrypted data for signs of malicious behavior. For example, a user might click a link on a malicious email that attempts to establish an encrypted HTTPS connection to download malware. The NGFW will decrypt the data, detect the malicious content and block it.
Source & Destination Aware Filtering
NGFWs check the sources and destinations of each traffic connection using both the header information as well as decrypted traffic information. URL, website, or IP address filtering is applied to block known bad connections. Suspected bad or anomalous traffic can be temporarily blocked or flagged as suspicious for security teams.
Threat Intelligence Feeds
Threat intelligence feeds provide lists of malicious IP addresses, malware signatures, and other threat indicators to enable the NGFW to rapidly detect threats and prevent attacks. NGFW will typically integrate the firewall vendor’s threat intelligence feed, but some buyers will also want an NGFW that can incorporate a variety of threat feeds for enhanced detection.
Network Intrusion Prevention System (IPS)
Although typically associated with protecting data flowing between the corporate network and the outside world, NGFW also can monitor traffic flowing within the network for signs of attack. Some NGFW can challenge the capabilities of standalone IPS appliances, but before replacing IPS systems, test the NGFW capabilities under realistic threat and load conditions. Overtaxed NGFW can create bottlenecks or cause traffic delays.
User Aware Filtering
NGFW can integrate with IT user directories (EX: Active Directory) and alter firewall rules based upon users and user groups. For example, file sharing sites and applications may be permitted for the marketing department but blocked for the research and development department. While very powerful, this feature depends upon accurate group assignments in the directory.
Network Sandboxing
Some NGFW provide network or cloud sandboxes in which suspicious files may be opened and tested on an isolated virtual machine. Sandboxing often will be offered as an add-on subscription and provides a good resource to internal security teams. However, keep in mind that some malware can test for a security environment prior to executing malicious behavior so some sandbox results could be inaccurate.
Top 3 NGFW Advantages
The deep packet inspection of NGFW provides three key advantages for improving security, enhancing control, and reducing complexity.
Enhanced security results from the deep inspection of sources, destinations, and traffic. NGFW blocks known malicious sources or destinations and filters out any detected malware. While this sounds simple, malware blocking requires the execution of multiple analysis techniques and improved security will be the primary motivator for NGFW purchases.
Enhanced control stems from improved user, device, and application awareness and tracking as well as from centralized management. Enhanced firewall capabilities understand deeper contexts and normal behavior to detect and block abnormal or malicious behavior. Centralized management also enables a smaller team to maintain and monitor network security.
Reduced complexity can result when NGFWs replace other security solutions such as dedicated network IPS solutions. A single, centrally managed solution can reduce training, installation, and update requirements compared to many different security solutions.
4 Disadvantages of NGFWs
Powerful NGFWs provide valuable benefits, but also introduce tradeoffs for performance, budgets, and configuration and attack risks.
Slowed traffic results from the deep packet inspection. For each security check applied to the packet, a microsecond of delay adds on to the packet transmission speed. The robust security of a large number of inspections comes with the tradeoff of slowed data throughput.
Increased deployment costs stem from the increased NGFW capabilities. Each additional feature delivers a number of options to select and integrations to manage which will take time and expertise – which adds expense.
Increased misconfiguration risk also originates from the increased NGFW capabilities. Each option on each feature provides an opportunity for a mistake or inadvertent conflicts. The increased complexity will require increased testing to verify correct setup.
Consolidated attack risk naturally arises when NGFWs replace other security solutions. The full protection burden falls upon the NGFW solution which becomes a single point of failure. For example, the US Cybersecurity and Infrastructure Security Agency (CISA) warns that centralized encryption inspection provides a centralized target for attack and can weaken security for encrypted communication.
NGFW vs Traditional Firewalls & Other Solutions
NGFW enhances security compared to most other types of firewalls but will not be the best solution for all traffic filtering needs. Additionally, NGFW typically replaces a traditional firewall in a traditional castle-and-moat security model which may not be the best solution for the protection of modern IT infrastructure.
In general, an NGFW provides the best security option. However, here is a brief list of other technologies and when they provide a better fit:
- Traditional firewalls: Provide lower cost options for simple and fast data filtering.
- Unified threat management (UTM): Supply low-cost all-in-one security solutions.
- Web application firewalls (WAF): Deliver high-speed specialty protection for apps.
- Database firewalls: Maintain high-speed and specialized filtering for database security.
- Cloud firewalls: Preconfigure NGFW capabilities into cloud-security-optimized firewalls.
- Container firewalls: Enable code-launchable and specialized container security.
- Firewall-as-a-service (FWaaS): Provide cloud-hosted and scalable NGFW as a service.
- Secure web gateways (SWG): Enable malware protection for local and remote assets.
- Secure service edge (SSE): Extends NGFW capabilities and more to remote assets.
- Secure access service edge (SASE): Combine SSE and network operations.
- Zero trust network access (ZTNA): Add identity and access management (IAM) to NGFW capabilities for both local and remote assets.
When comparing solutions, make sure to examine the details. Some features will require add-on subscriptions and not all features will be equivalent – or necessary. For example, some NGFW support as many as 5,000 applications and others as few as 800. However, if you only need the apps within the 800, you don’t need to pay a premium to support a full 5,000 features.
Also be sure to consider automation, AI assists, and reporting features in the solution. The modern enterprise will often be resource constrained and also have many different compliance requirements. Automation and AI can help smaller teams to accomplish more and reporting can remove some compliance burdens.
Bottom Line: Effective NGFW Protection Requires Effective Rules
Next generation firewalls often provide the best option for network defense. NGFW can also provide effective cloud security, multiple branch office security, or even FWaaS capabilities when deployed as a virtual device. However, all firewalls, even NGFWs, depend upon proper setup to provide effective protection and one misconfigured or bad firewall rule can cripple even the most powerful security function.
As a first step to deploy an effective NGFW, learn about the best NGFW solutions. In the article, you’ll find their use cases, pricing, top features, and more so you can choose the best option for you.




