As if to underscore the point, Gartner analyst Brian Reed unveiled the list of top security projects for 2020-2021 at Gartner’s Security & Risk Management Summit – held virtually this week a few months after the annual in-person event was canceled because of the pandemic.
Remote workforce security, Reed told attendees, “is the single greatest existential imperative for all organizations in the wake of COVID-19.”
He later added, “If you can only do one project, focusing on securing your remote workforce and going back and looking at some of those changes we might have made earlier in the year would be a really good use of time.”
Among the issues security teams should examine are whether they’re granting too much access or not enough. One sign of the latter might be users bypassing security to get their jobs done.
Other remote security considerations include job function, device type, the kind of application and data being accessed, whether in the cloud or on-premises, and the user’s location. That last consideration should also include an assessment of the company’s compliance with local labor and privacy laws.
The challenge with remote workforce security, Reed said, is to craft a zero-trust strategy that enables business while securing remote workers – and that means making sure that both managed and unmanaged devices can securely access applications.
He listed 14 vendors that can potentially help: Akamai; Cato; Cloudflare; Cisco; Cyxtera; Google Cloud; InstaSafe; Meta Networks; Microsoft; Okta; Pulse Secure; Perimeter 81; and Zscaler.
COVID-19 creates new security threats
The rapid move to telework has revealed security weaknesses in remote desktop protocol (RDP), VPN and videoconferencing solutions and forced security teams to develop new protocols for remote endpoint management and patching, said Gartner senior research director Jonathan Care.
Before the pandemic, security was designed around the notion that remote work was the exception, so when COVID-19 led to a dramatic surge in telecommuting, always-on VPNs and BYOD suddenly became urgent issues.
Rising threats because of the pandemic include coronavirus-related business email compromise (BEC) and phishing scams, including SMS phishing (“smishing”) and credential theft attacks, he said. Nation-state actors have launched advanced persistent threats (APT) against healthcare and essential services by using scan and exploit techniques and password spraying to take advantage of unpatched vulnerabilities.
Remote access security technologies
Gartner analyst Rob Smith will also discuss remote access security in a Sept. 16 presentation at the conference.
Smith says enterprises should avoid using always-on VPN unless they have to. He recommends three technologies for remote workforce security:
- CASB for SaaS applications, which can help both security and performance
- A zero-trust network architecture (ZTNA) that includes strong identity and authentication controls and the ability to control access based on device
- Virtual desktop infrastructure (VDI) for untrusted devices or users
He cautions that some information gathered via mobile device management (MDM), such as GPS data and installed apps, could violate privacy laws.
Any solution has to be scalable and be able to prioritize critical users, he said.
Top security projects and spending priorities
Last year’s list of top security projects included five holdovers from 2018, but Reed’s 2020-2021 list is largely new, with only two carryovers from 2019: Risk-based vulnerability management and cloud security posture management.
Besides security for work at home employees, the other new security projects recommended by Reed include:
- Platform approach to detection and response – a comprehensive approach spanning endpoints, the cloud and networks, similar to the XDR approaches of Palo Alto Networks and others
- Simplified cloud access controls
- DMARC email security
- Passwordless authentication
- Data classification and protection
- Workforce competencies assessment
- Automating security risk assessments, a market led by CyberSaint, Emergynt, InnoSec, Lucideus and others
Before tackling those top projects, Reed said enterprises should get the basics right – itself no short list:
- Endpoint and server protection
- IAM and administrative controls
- Log monitoring
- Backup/restore
- Patch and vulnerability management
- Perimeter security controls
- Email security controls
- End user training
- Sensitive data handling controls
- Risk assessments
Just as interesting as the top projects list was the projects Gartner analysts considered that didn’t make the list:
- Employee monitoring and surveillance technologies
- Threat attribution services
- Automated threat hunting
- Cyber-range and cyber-simulation systems
- Chatbot-based security awareness and education
- Biometric credential detection/protection
- Quantum everything
- Secure access service edge (SASE)
- Cyber-physical security — drone detection, temperature detection
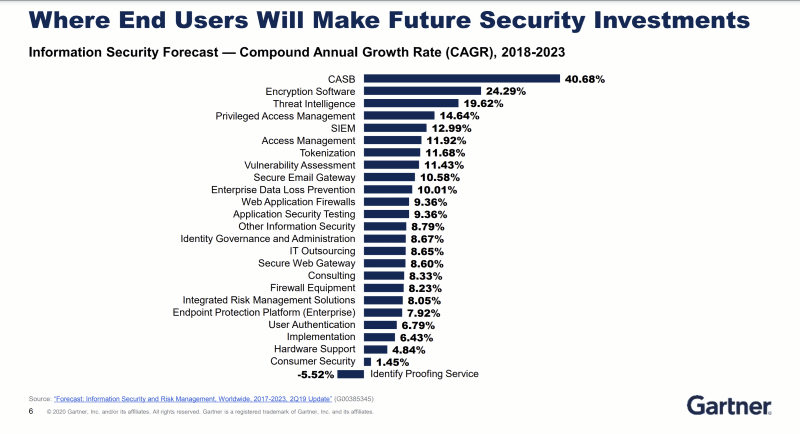
Reed also noted that IT security spending priorities (chart below) have likely changed from Gartner’s long-term forecast issued last year, which predicted that CASB, encryption, threat intelligence, access management, SIEM, tokenization, vulnerability assessment, secure email gateways, DLP and WAF would post the top growth rates in the security market through 2023.