-
eSecurity Planet’s 2022 Cybersecurity Product Awards
The editors of eSecurity Planet have been giving advice to enterprise security buyers for more than a decade, and for the last five years we’ve been rating the top enterprise cybersecurity products, compiling roughly 50 lists to date on every product imaginable, from networks to endpoints and out to the cloud and beyond. This year, […]
-
Our Top Security Vendor Methodology
We gather information from a range of IT industry sources for our top security products articles. Our most frequently used sources have been analyst firms Gartner and Forrester, testing organizations MITRE and Cyber Ratings, and user review sites Gartner Peer Reviews and G2. We interview company officials and scour data sheets. We interview users and […]
-
Most Security Product Buyers Aren’t Getting Promised Results: RSA Panel
About 90% of security buyers aren’t getting the efficacy from their products that vendors claim they can deliver, according to a panel at this week’s RSA Conference that also offered some solutions to begin to fix that problem. Joe Hubback of cyber risk management startup ISTARI led both the panel and the study, which was […]
-
Latest MITRE Endpoint Security Results Show Some Familiar Names on Top
MITRE Engenuity has released the latest round of its ATT&CK endpoint security evaluations, and the results show some familiar names leading the pack with the most detections. The MITRE evaluations are unique in that they emulate advanced persistent threat (APT) and nation-state hacking techniques, making them different from tests that might look at static malware […]
-
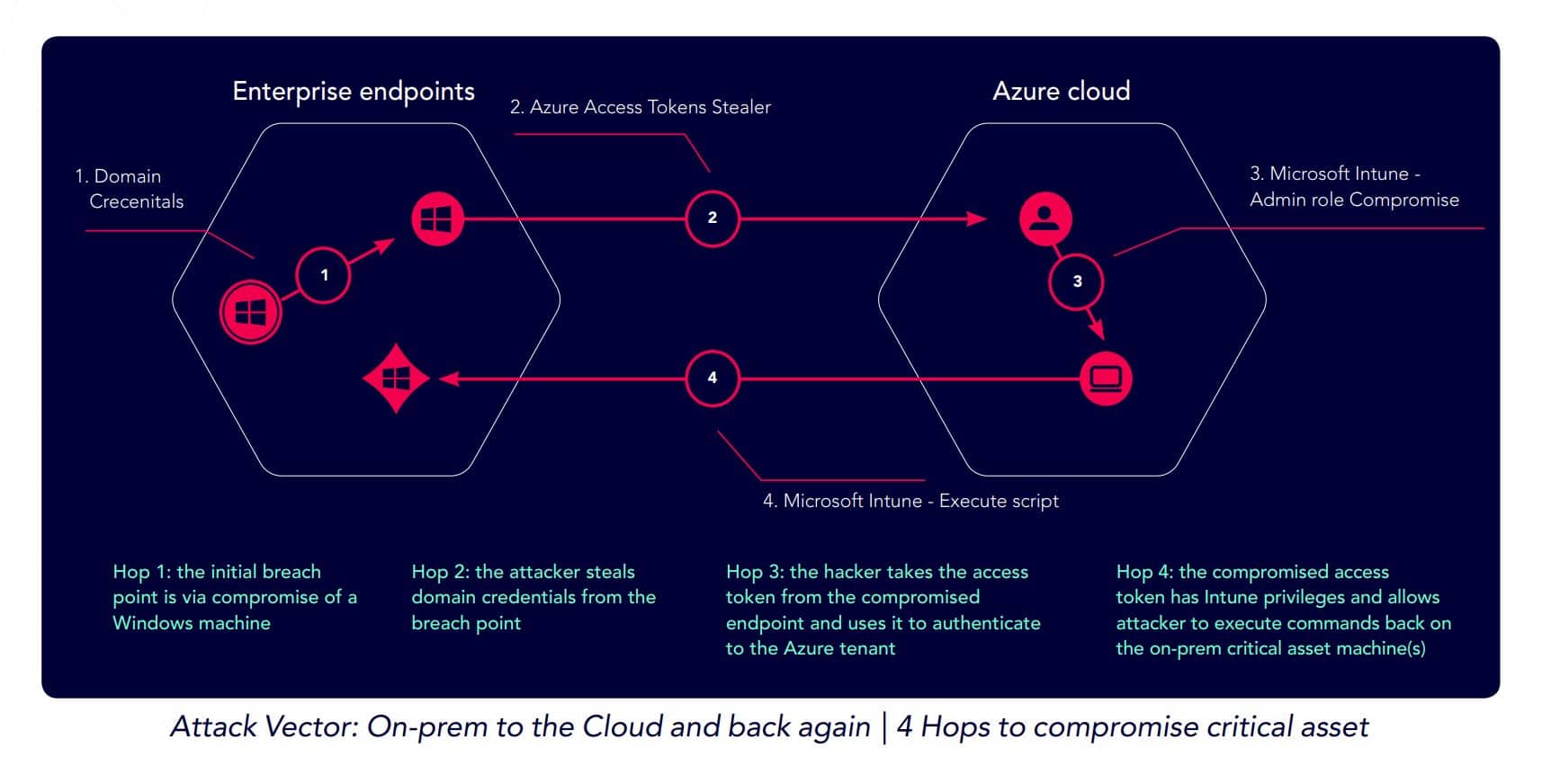
A Few Clicks from Data Disaster: The State of Enterprise Security
Once an organization has been breached, the overwhelming majority of critical assets are just a few attack techniques away from being compromised, according to a new study. The report by breach and attack simulation (BAS) vendor XM Cyber noted that 63% of critical assets are just a single “hop” away from initial breach to compromise; […]
-
McAfee Cloud Launches as Skyhigh Security
The final piece of the complicated Mandiant-FireEye split and subsequent FireEye-McAfee merger fell into place today, as McAfee’s cloud security business was officially spun off under the new name of Skyhigh Security. McAfee Enterprise and FireEye were acquired by Symphony Technology Group last year as Mandiant became a standalone company. STG also owns RSA Security, […]
-
Google to Acquire Mandiant; EDR Acquisition Next?
Google today announced that it has agreed to acquire Mandiant for roughly $5.4 billion to bolster its cloud security. Google noted that Google Cloud already offers a number of security services, including BeyondCorp Enterprise for Zero Trust, VirusTotal for malicious content and software vulnerabilities, Chronicle security analytics and automation and the Security Command Center risk […]
-
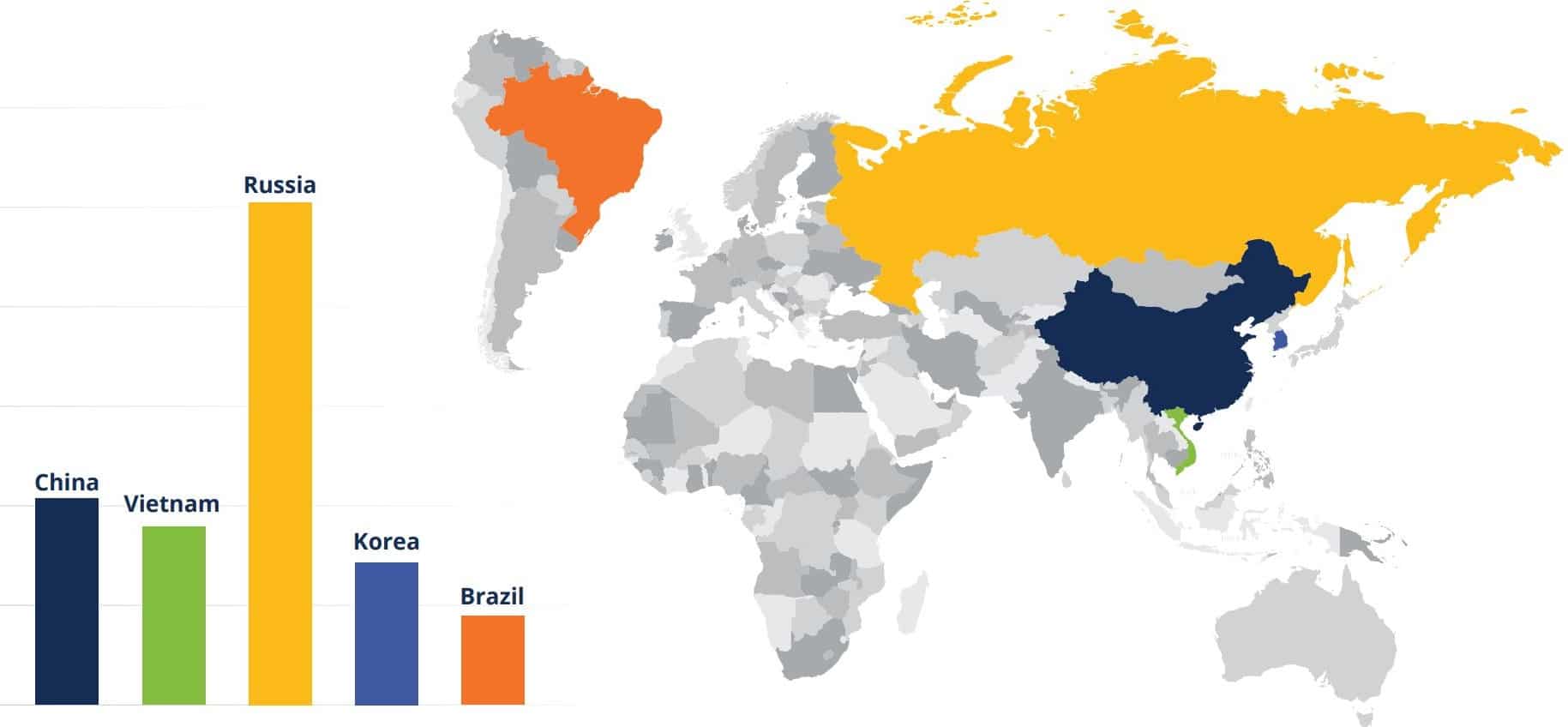
Russia, China May Be Coordinating Cyber Attacks: SaaS Security Firm
A SaaS security company says a spike in cyber attacks from Russia and China in recent weeks suggests the two countries may be coordinating their cyber efforts. SaaS Alerts, which helps managed service providers (MSPs) manage and protect customers’ SaaS apps, mentioned the finding in conjunction with the release of its annual SaaS Application Security […]
-
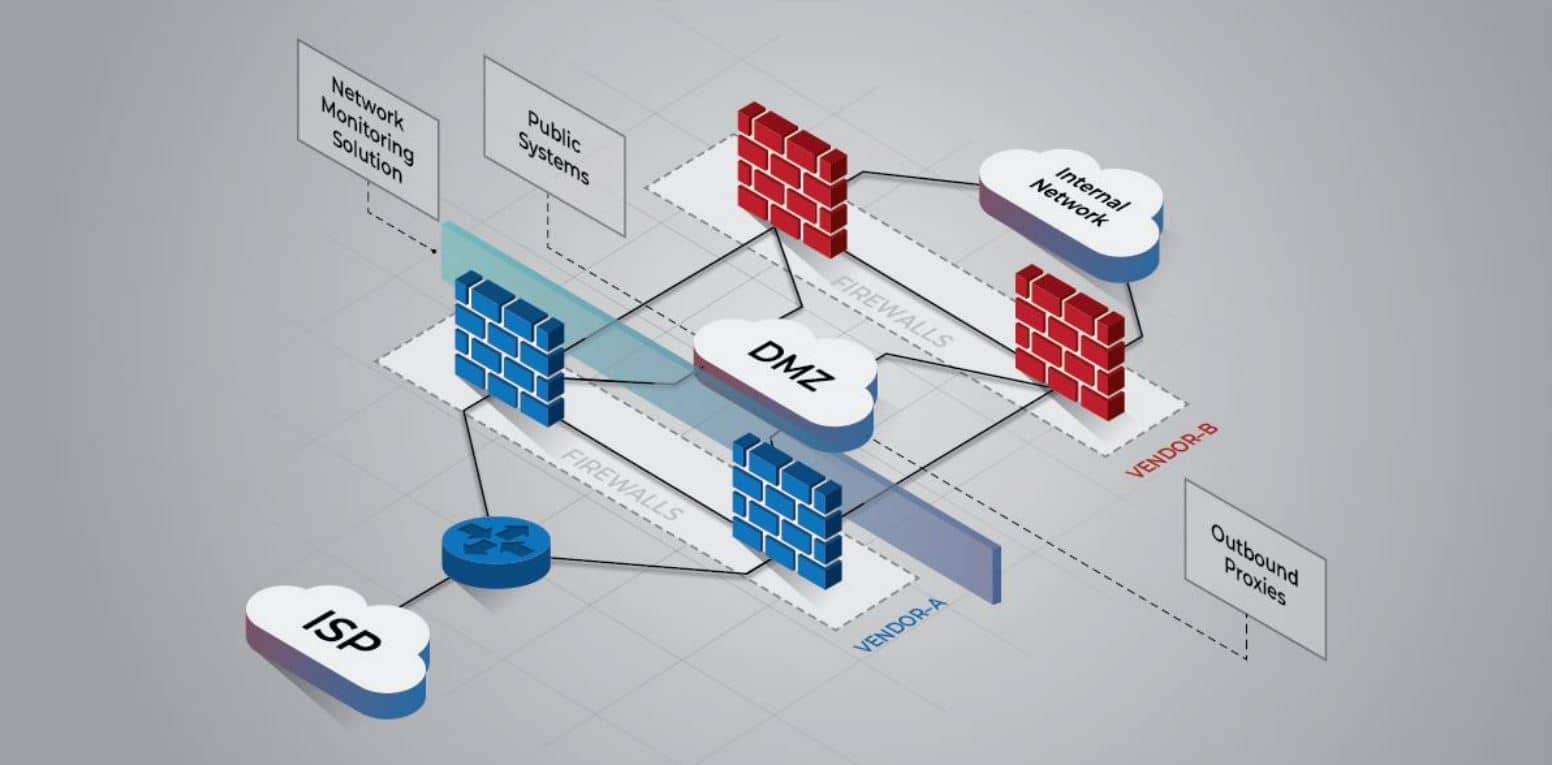
U.S. Security Agencies Release Network Security, Vulnerability Guidance
The U.S. National Security Agency (NSA) released comprehensive network security guidance on March 3, on the same day that the Cybersecurity and Infrastructure Security Agency (CISA) released its longest-ever list of exploited vulnerabilities. With organizations around the world on heightened alert in the wake of Russia’s unprovoked war against Ukraine, government agencies have stepped up […]
-
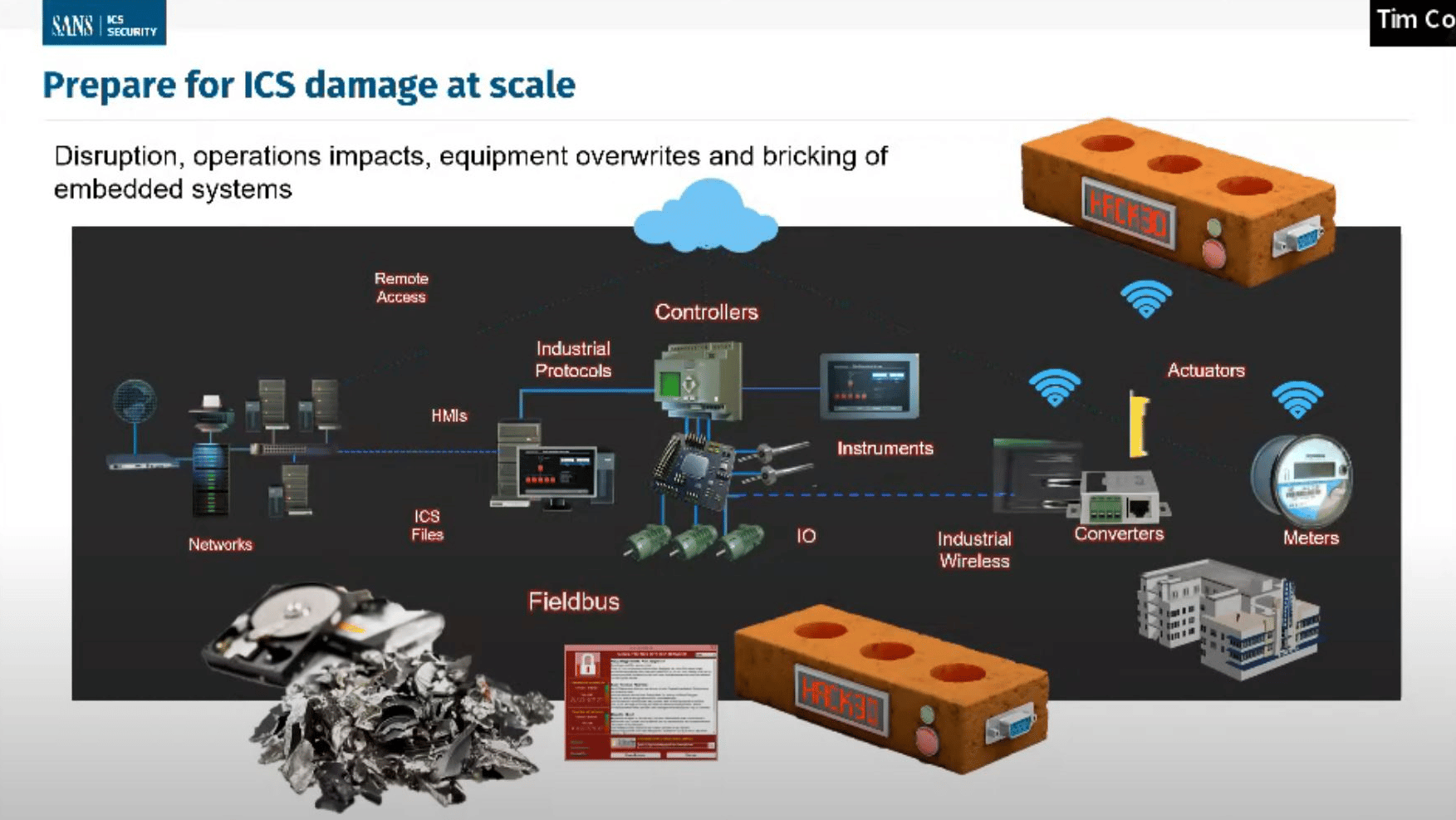
SANS Outlines Critical Infrastructure Security Steps as Russia, U.S. Trade Cyberthreats
Critical infrastructure security has moved to the forefront of cybersecurity concerns amid the Russian invasion of Ukraine – and in at least one case has led to some pretty unique cybersecurity advice. Despite Russia and the U.S. trading cyber threats – and one disputed NBC News report that outlined possible options presented to U.S. President […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis