-
Cybersecurity Outlook 2022: Third-Party, Ransomware and AI Attacks Will Get Worse
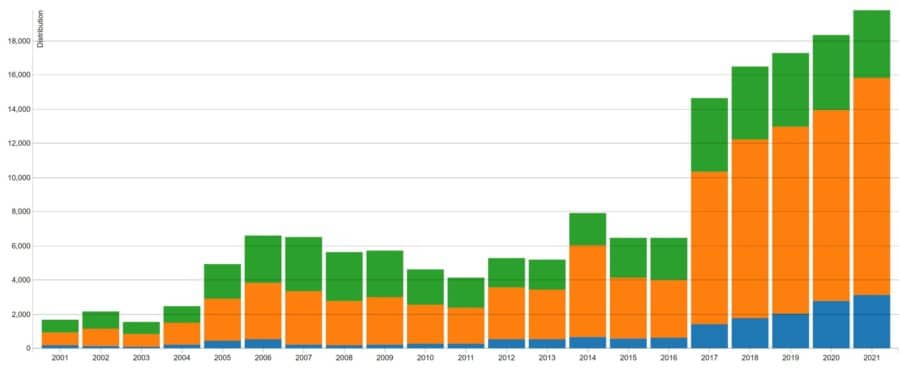
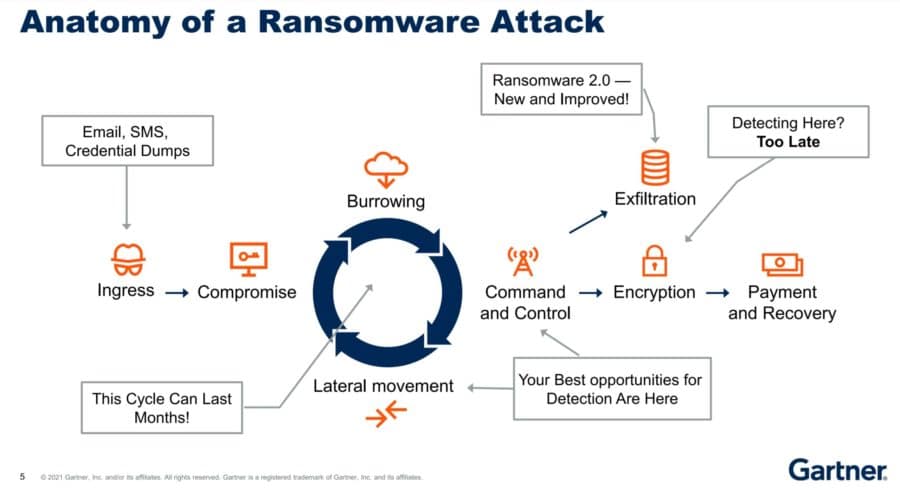
About the only consensus on cybersecurity in 2022 is that things will get uglier, but in what ways? Third-party security, ransomware, artificial intelligence (AI) and decentralized finance (DeFi) are some of the threats you can expect to see more of this year – with the potential for far worse results than we’ve seen in the […]
-
Cybersecurity Mesh, Decentralized Identity Lead Emerging Security Technology: Gartner
New cybersecurity buzzwords are always in abundance at the Gartner Security & Risk Management Summit, and the concepts that took center stage this week, like cybersecurity mesh and decentralized identity, seem well suited for new threats that have exploded onto the scene in the last year. Gartner analyst Ruggero Contu noted that security risks are […]
-
McAfee’s Consumer Business to Be Acquired by Private Equity Groups
The McAfee consumer security business, which trades on the NASDAQ under the symbol MCFE, will be going private in a deal valued at more than $14 billion. McAfee had sold its Enterprise business just a few months ago, to a private consortium led by Symphony Technology Group (STG) – and McAfee Enterprise was subsequently merged […]
-
IBM Moves Into EDR Market With ReaQta Acquisition
IBM is moving into the endpoint detection and response (EDR) market with the acquisition of ReaQta. IBM is positioning the announcement as part of its launch of an XDR product. Extended detection and response (XDR) has emerged in recent years as a unified enterprise security platform, a way for vendors to package their offerings together […]
-
CrowdStrike vs Symantec: Top EDR Solutions Compared
Buyers looking for an endpoint security solution often compare CrowdStrike and Symantec, and while both vendors made our top endpoint detection and response (EDR) product list, they’re very different security products that will likely appeal to buyers with different goals in mind. Here’s a look at both EDR products, how they compare, and their ideal […]
-
McAfee-FireEye Merger Makes STG’s Plans Clearer
Private equity firm Symphony Technology Group (STG) has been on a cybersecurity buying spree the last two years, acquiring RSA Security, McAfee’s enterprise business and Mandiant’s FireEye products business (see FireEye, Mandiant to Split in $1.2 Billion Deal). Industry analysts have speculated that STG might merge at least some of its security holdings. Yesterday that […]
-
Microsoft Makes Exchange Server Patches Less Optional
Microsoft Exchange is a frequent target of hackers, and often the attack vector is a well known vulnerability that a company just hasn’t gotten around to patching. To try to deal with that problem, Microsoft is doing what a lot of other software vendors may start doing: making applying fixes a lot less optional. In […]
-
Palo Alto Enters Small Business, Remote and Home Markets with Okyo
Palo Alto Networks (PANW) is bringing its enterprise-class security to small business and home markets with Okyo, a Wi-Fi 6 hardware device announced today. At $349 a year, the security and router system seems attractively priced for small businesses and companies looking to secure remote workers, who have surged in number since the start of […]
-
Hackers Leak 87,000 Fortinet VPN Passwords
In the latest lesson about the importance of patching, the credentials for 87,000 Fortinet FortiGate VPNs have been posted on a dark web forum by hackers. Fortinet confirmed the veracity of the hackers’ claims in a blog post today. The network security vendor said the credentials were stolen from systems that remain unpatched against a […]
-
Open Source Security: A Big Problem
Open source security has been a big focus of this week’s Black Hat conference, but no open source security initiative is bolder than the one proffered by the Open Source Security Foundation (OpenSSF). Amid discussions on the security of open source technologies like eBPF and Hadoop, OpenSSF speakers Jennifer Fernick, SVP and head of global […]
IT Security Resources
Top Cybersecurity Companies
Top 10 Cybersecurity Companies
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis